当前位置:网站首页>Envoy obtain the real IP address of the client
Envoy obtain the real IP address of the client
2022-06-24 22:33:00 【Mr.Cylon】
stay envoy As a front-end agent , user ip Access to information is important , Generally get ip The way . It's all through Header Medium X-Forward-For、 X-Real-IP or Remote addr And so on , But if you make sure Envoy What can be obtained ip It's a real user ip Well ? This article continues to be decrypted !
Concept description
Remote Address
yes nginx With the client TCP During connection , Get the real address of the client .Remote Address No forgery , Because of the establishment of TCP Connection requires three handshakes , If you fake the source IP, Can't create TCP Connect , There will be no back HTTP request .
In general , stay Envoy As the outermost agent , this IP For the real IP client IPX-Real-IP
Is a custom header .X-Real-Ip Usually HTTP An agent is used to indicate that it produces TCP Connected devices IP, This device may be another agent , It may also be the real requester .X-Real-Ip At present, it does not belong to any standard , Agents and Web Applications can agree to use any custom header to pass this information .X-Forwarded-For
X-Forwarded-For Is an extension header .HTTP/1.1(RFC 2616) The agreement does not define it , It started with Squid This cache agent software introduces , Used to represent HTTP The request is true IP, Now it has become the de facto standard , By the major HTTP agent 、 Forwarding services such as load balancing are widely used , And is written RFC 7239(Forwarded HTTP Extension) In the standard . Usually ,X-Forwarded-For Can be forged , And use CDN Will be rewritten
Envoy How to get the truth in IP
stay Envoy in , It involves the client IP The configuration is as follows :
use_remote_address: The default value is false, Set to true, Use the real remote address of the client connection ,false It's using x-forwarded-for
skip_xff_append: Set to true, The remote address will not be attached to x-forwarded-for in
request_headers_to_add Add request header
request_headers_to_remove Delete a request header
Experimental environment configuration preparation
admin:
access_log_path: /dev/null
address:
socket_address: {
address: 0.0.0.0, port_value: 9901 }
static_resources:
listeners:
- name: listener_80
address:
socket_address: {
address: 0.0.0.0, port_value: 80 }
access_log:
filter_chains:
- filters:
- name: envoy_http_connection_manager
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager
access_log:
- name: envoy.listener.accesslog
typed_config:
"@type": type.googleapis.com/envoy.extensions.access_loggers.file.v3.FileAccessLog
path: /var/log/envoy.log
log_format:
text_format: "[%START_TIME%] \"%REQ(:METHOD)% %REQ(X-ENVOY-ORIGINAL-PATH?:PATH)% %PROTOCOL%\" %RESPONSE_CODE% %RESPONSE_FLAGS% %BYTES_RECEIVED% %BYTES_SENT% %DURATION% %RESP(X-ENVOY-UPSTREAM-SERVICE-TIME)% \"%REQ(X-FORWARDED-FOR)%\" \"%REQ(USER-AGENT)%\" \"%REQ(X-REQUEST-ID)%\" \"%REQ(:AUTHORITY)%\" \"%UPSTREAM_HOST%\"\n"
http_filters:
- name: envoy.filters.http.router
use_remote_address: true
skip_xff_append: false
xff_num_trusted_hops: 0
stat_prefix: local_route
codec_type: AUTO
route_config:
name: local_route
#request_headers_to_remove: "X-Forwarded-For"
request_headers_to_add:
header:
key: "X-Forwarded-For"
value: "%DOWNSTREAM_REMOTE_ADDRESS_WITHOUT_PORT%"
#value: "%REQ(REMOTE_ADDR)%"
append: true
virtual_hosts:
- name: split_traffic
domains: [ "*" ]
routes:
- match:
prefix: "/"
route:
cluster: version_v1
request_mirror_policies:
cluster: version_v2
runtime_fraction:
default_value:
numerator: 10
denominator: HUNDRED
runtime_key: routing.request_mirror.version
clusters:
- name: version_v1
connect_timeout: 0.25s
type: STRICT_DNS
lb_policy: ROUND_ROBIN
load_assignment:
cluster_name: version_v1
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address: {
address: version1, port_value: 90 }
health_checks:
timeout: 3s
interval: 30s
unhealthy_threshold: 2
healthy_threshold: 2
http_health_check:
path: /ping
expected_statuses: {
start: 200, end: 201 }
- name: version_v2
connect_timeout: 0.25s
type: STRICT_DNS
lb_policy: ROUND_ROBIN
load_assignment:
cluster_name: version_v2
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address: {
address: version2, port_value: 90 }
health_checks:
timeout: 3s
interval: 30s
unhealthy_threshold: 2
healthy_threshold: 2
http_health_check:
path: /ping
expected_statuses: {
start: 200, end: 201 }
docker-compose
version: '3'
services:
envoy:
image: envoyproxy/envoy-alpine:v1.15-latest
environment:
- ENVOY_UID=0
ports:
- 80:80
- 443:443
- 82:9901
volumes:
- ./envoy.yaml:/etc/envoy/envoy.yaml
networks:
envoymesh:
aliases:
- envoy
depends_on:
- webserver1
- webserver2
- webserver3
- webserver4
webserver1:
image: cylonchau/envoy-end:latest
networks:
envoymesh:
aliases:
- version1
environment:
- VERSION=v1
- COLORFUL=blue
expose:
- 90
webserver2:
image: cylonchau/envoy-end:latest
networks:
envoymesh:
aliases:
- version1
environment:
- VERSION=v1
- COLORFUL=blue
expose:
- 90
webserver3:
image: cylonchau/envoy-end:latest
networks:
envoymesh:
aliases:
- version2
environment:
- VERSION=v2
- COLORFUL=red
expose:
- 90
webserver4:
image: cylonchau/envoy-end:latest
environment:
- VERSION=v2
- COLORFUL=red
networks:
envoymesh:
aliases:
- version2
expose:
- 90
networks:
envoymesh: {
}
The actual use Envoy The external environment when acting as an agent
Environmental Science 1: The client directly communicates with Envoy signal communication
When a normal request , The client can be obtained here IP, actually envoy What's the value X-Forwarded-For

Back end log

In forging or rewriting X-Forwarded-For After that, it is actually the obtained forged value .
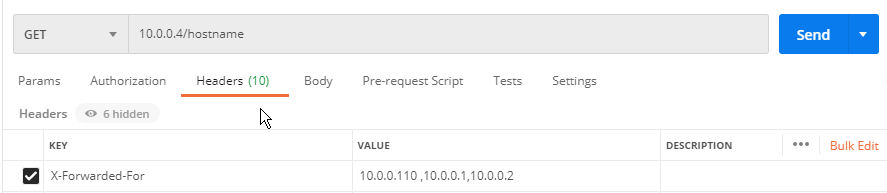


stay Envoy When acting directly as an outer agent , You can use the following parameters , No matter how fake , You can get the corresponding parameters .
name: local_route
request_headers_to_remove: "X-Forwarded-For" # fear X-Forwarded-For For forged values , You can delete this value ,
request_headers_to_add: # After deletion, you also need to pass to the back end , So you need to add this value
header:
key: "X-Forwarded-For"
value: "%DOWNSTREAM_REMOTE_ADDRESS_WITHOUT_PORT%" # obtain remote_addr, This value cannot be forged , by Envoy Variable , Express The downstream host is real IP No port , namely remote_addr No port
append: true # Whether surface values are appended or overwritten



You can see envoy What you get is real ip Not a forged request
Environmental Science 2:Envoy There are agents in the preceding paragraph ( nothing CDN)
In this environment , There are agents on the front end , Such as f5、nginx etc. . Cannot be used in this case remote_addr The data obtained in this way is the data of the front-end agent IP It's not true IP
Front end exists f5 or nginx, Can be in f5 Middle configuration irule Deliver real remote_addr, Replace with a real client IP, The front-end proxy rewrites the configuration , Customizable value .
request_headers_to_remove: "X-Forwarded-For"
request_headers_to_add:
header:
key: "X-Forwarded-For"
value: "%REQ(custom_header)%"
Environmental Science 3:Envoy There are agents in the preceding paragraph ( single CDN)
In this environment , There are agents on the front end , And used CDN, Should be for each CDN The manufacturer obtains the truth of customers IP In different ways , Here we need to find cdn Manufacturers find and get real IP Methods , Follow the steps 2 Conduct .
give an example :
Alibaba cloud cdn Get real IP Method
Accelerate music to get real IP Method
Environmental Science 4:Envoy There are agents in the preceding paragraph ( many CDN)
Because of each CDN The bandwidth of the 、 Price 、 Usage scenarios and other factors , In practice , A variety of... May be used CDN; Such as : Use under normal circumstances cdn Speed up , In case of an attack, switch to the one with high security defense CDN. Generally only accelerated CDN The price is much cheaper than the one with defense .
here Enovy To be updated , Back end applications can be based on CDN Of http Head normal acquisition IP
Environmental Science 5: The internal agent
No special requirements
边栏推荐
猜你喜欢
随机推荐
Future development of education industry of e-commerce Express
Resolving the conflict problem of the flutter Library
网上立案流程
Process communication mode
NIO、BIO、AIO
AQS source code analysis
First order model realizes photo moving (with tool code) | machine learning
DP problem set
Online filing process
Ansible basic configuration
Disk structure
DAO 中常见的投票治理方式
Shutter precautions for using typedef
60 个神级 VS Code 插件!!
代理模式详解
try-with-resources 中的一个坑,注意避让
NIO、BIO、AIO
第二批入围企业公示!年度TOP100智能网联供应商评选
Ideal L9, new trend of intelligent cockpit
Description of transparent transmission function before master and slave of kt6368a Bluetooth chip, 2.4G frequency hopping automatic connection