当前位置:网站首页>Common rendering pipeline grooming
Common rendering pipeline grooming
2022-06-12 22:25:00 【ZEKEGU1997】
Forward Rendering
Most common rendering , So called forward rendering , Is to string objects into a queue , Render one by one . The main cycle can be light source or object .
The disadvantage is that the efficiency is low when there are many objects or light sources , And there will be many repeated calculations .
Deferred Rendering
Divide rendering into two stages , The first stage deals with the data needed for lighting calculation , And store them in GBuffer in , These data include the location of slices 、 Diffuse map , Normal map , Specular reflection intensity diagram, etc .
The utility model has the advantages of high efficiency when there are many objects and light sources , The disadvantage is that the required bandwidth is large , Do not apply MSAA, Difficult to handle transparent blending .
Tiled Deferred Shading
Due to bandwidth constraints , It is difficult for mobile terminal to implement conventional delayed rendering , One solution is to divide the screen into areas , Render separately .
Tiled Fowrad Rendering
Divide the screen space into blocks , Calculate the range it can cover for each light source , If there is no effect on a certain screen area, it will be removed .
Clustered Forward Rendering
Forward+ Is divided in the screen space Tile Filter the light source to reduce the consumption , This division is in XY 2D Plane , and Clustered Forward Rendering Is to go further on this basis , stay Depth The direction is also divided once , Further reduce the influence range of light , Reduce the waste of lighting calculation . Because the result of the division is 3D Of Frustum, Every Frustum Called a Cluster, This is it. Cluster The origin of .
边栏推荐
- The interface testing tool apipos3.0 is applicable to process testing and reference parameter variables
- SQL query list all views in SQL Server 2005 database - SQL query to list all views in an SQL Server 2005 database
- 接口测试工具apipost3.0版本对于流程测试和引用参数变量
- [C language] data type occupation
- Generate the chrysanthemum code of the applet (generate the chrysanthemum code, change the middle logo, change the image size, and add text)
- 【LeetCode】103. Zigzag sequence traversal of binary tree
- 认识的几位清华同学都离职了……
- Shardingsphere-proxy-5.0.0 deployment table implementation (I)
- JS fighting on...
- Jin AI her power | impact tech, she can
猜你喜欢

数据库每日一题---第10天:组合两个表
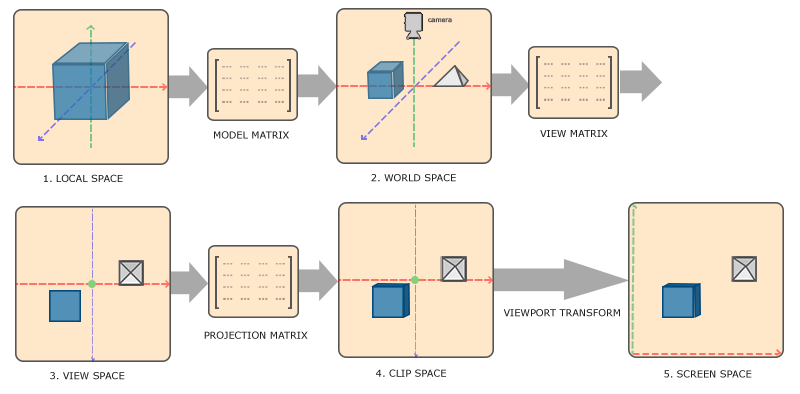
管线中的坐标变换

NoSQL - redis configuration and optimization (II) high availability, persistence and performance management

How to specify your webpage's language so Google Chrome doesn't offer to translate it

C语言:如何给全局变量起一个别名?

JVM Basics - > how GC determines that an object can be recycled

设计消息队列存储消息数据的 MySQL 表格

Implementation of master-slave replication and master-master replication for MySQL and MariaDB databases
![[Part VI] source code analysis and application details of countdownlatch [key]](/img/6e/085e257c938a8c7b88c12c36df83e1.jpg)
[Part VI] source code analysis and application details of countdownlatch [key]

Ansible playbook and variable (II)
随机推荐
IPhone: save Boolean into core data - iphone: save Boolean into core data
C # reading table data in word
Mysql concat_ WS, concat function use
[leetcode] sword finger offer II 020 Number of palindrome substrings
【LeetCode】53.最大子数组和
How to perform disaster recovery and recovery for kubernetes cluster? (22)
JVM Basics - > how GC determines that an object can be recycled
Audio and video technology development weekly 𞓜 234
Mysql concat_ws、concat函数使用
C language: how to give an alias to a global variable?
C语言:如何给全局变量起一个别名?
Have you really learned the common ancestor problem recently?
China Aquatic Fitness equipment market trend report, technical innovation and market forecast
Mr. Sun's version of JDBC (21:34:25, June 12, 2022)
JVM Basics - > how to troubleshoot JVM problems in your project
生成小程序菊花码(生成菊花码、更换中间logo、更改图片尺寸,加文字)
[890. find and replace mode]
[sword finger offer] sword finger offer 35 Replication of complex linked list
One article to quickly understand whether there are security risks in your network
Database daily question --- day 10: combine two tables