当前位置:网站首页>Rhcsa Notes 6
Rhcsa Notes 6
2022-07-23 18:14:00 【zyfpkp】
1.linux Type of user in
Divided into three categories :
The super user —— The user is called root, It has all permissions , Only system maintenance ( for example : Establish users, etc ) Or other necessary
Only use super user login , To avoid security problems in the system .
System users ( Dummy user )—— yes Linux Users necessary for the normal operation of the system . Mainly to meet the corresponding system process
The document is established at the request of the owner , for example :bin、daemon、adm、lp Waiting for users . System users cannot log in .
Ordinary users —— To enable users to use Linux System resources , Most of our users fall into this category .
linux Type of user group in
There are two kinds of :
Basic group ( Private group ): When establishing an account , If the group to which the account belongs is not specified , The system will create a group with the same user name , this The first group is the basic group .
Additional group ( Public group ): Can accommodate multiple users , All users in the group have the rights owned by the group .
linux Which file stores user information in ? And what do the fields mean
/etc/passwd( User account file , All accounts are accessible ) A total of 7 paragraph , The format is as follows :
user name : password :UID:GID: Account information : Account directory :Shell type

/etc/shadow( User password file ,root To access ), A total of 9 paragraph , The format is as follows :
user name : password : The number of days of the last modification time : The minimum interval between two password changes : How many days later, you need to change your password again : The number of days from issuing a warning to the official expiration of the password : The number of days that the user name is still valid before login is prohibited : The time when the user is forbidden to log in : Flag fields , meaningless

linux What is the file in which the group information is stored ? And what do the fields mean ?
/etc/group( User group file , All accounts are accessible ), A total of 4 paragraph , The format is as follows :
User group name : Set the password :GID: The group members

2. Create the following users 、 Groups and group membership :
1. Create a sysmgrs Group
2. Create user natasha At the same time specified sysmgrs As natasha Additional groups of
3. Create user harry At the same time specified sysmgrs As harry Additional groups of
4. Create user sarah Appoint shell The type is /sbin/false( You do not have access to interactive on the system shell)
It's not sysmgrs Members of

5. Set up natasha 、 harry and sarah All of your passwords are 123

6. Create user lockuser, And specify home directory as /home/lock, Then lock the user

7. Create user limituser, gid by 1555,userid by 1666, Let its password in 10 Expires in days
![]()

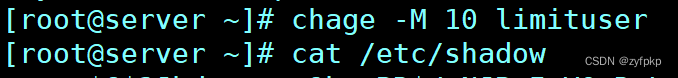

8. Unlock lockuser, And set that the password must be changed the next time you log in

9. Give Way natasha With modification harry Password permissions (sudo)![]()


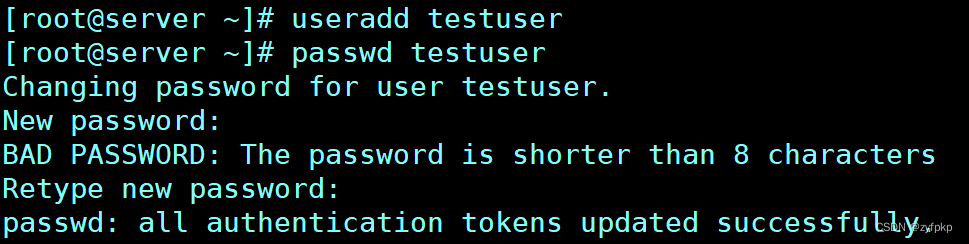
10. Create user testuser And set the password , Change the user name to normaluser


11. Delete lockuser


3. create a file , And give authority 611( Two ways , A kind of guoa, A kind of nnn)

4. Create directory , And give authority 755( Two ways , A kind of guoa, A kind of nnn)


![]()
5. create a file , And modify the owner and group of the file to other users

6. Set up suid, Set for file suid( Two ways u+s and nnnn) The way

7. Set up sgid, Set for file sgid( Two ways g+s and nnnn) The way

8. Set up sbit, Set for directory sbit( Two ways o+t and nnnn) The way

9. create a file , Query file acl
Set for file acl The user is testuser1 Permission is rwx
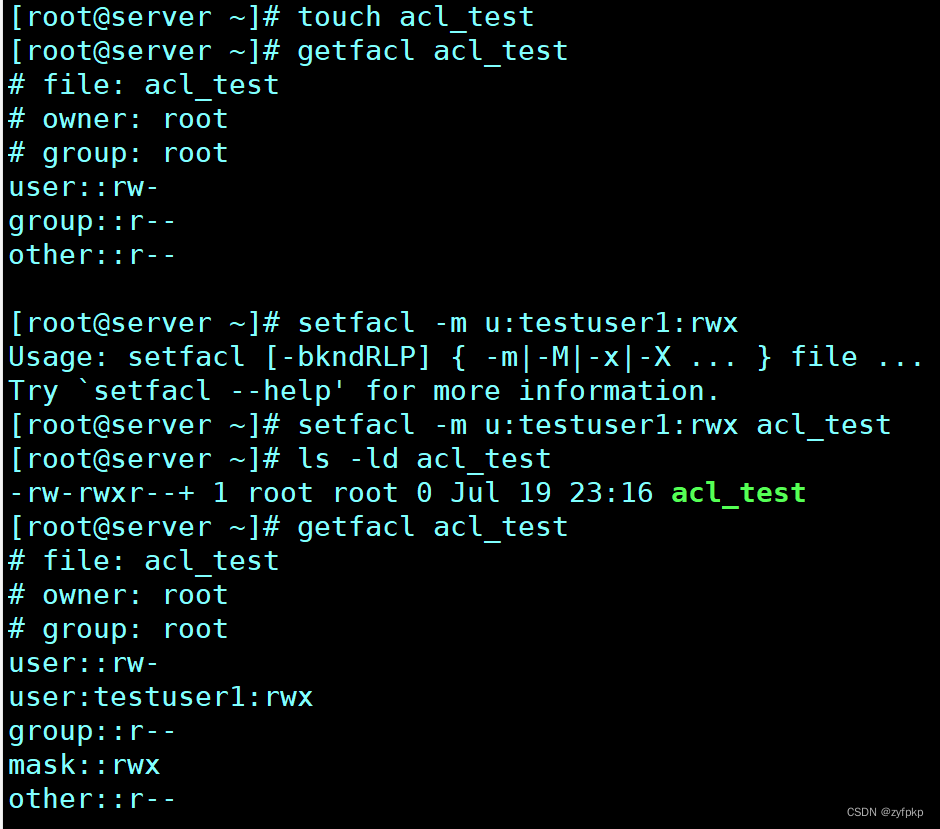
Set for file acl Of mask: Permission is r-x

边栏推荐
猜你喜欢
![Leetcode: Jianzhi offer II 115. reconstruction sequence [graph theory thinking + in degree consideration + topological sorting]](/img/cc/1438381ccc8d7fe147bb9c5e7e1742.png)
Leetcode: Jianzhi offer II 115. reconstruction sequence [graph theory thinking + in degree consideration + topological sorting]

MySQL8.0.23四次重装都失败在 'Writing configuration file'
go语言中的内存对齐是如何优化程序效率的?

(11) STM32 - IO pin multiplexing and mapping

On Monday, I asked | what constraints will take effect in the comprehensive stage of vivado?

数字安全巨头Entrust披露六月遭到勒索软件团伙攻击

Machine learning (9) - Feature Engineering (3) (supplementary)

接口测试概述

MySQL massive write problem optimization scheme MySQL parameter tuning
Detailed explanation of CO process principle in go
随机推荐
Sentinel installation diagram
几种运维工具的对比
Salary high voltage line
Type-C to OTG (USB2.0 data transmission) + PD charging protocol chip ledrui ldr6028/ldr6023ss
LDAP统一认证服务解决方案[通俗易懂]
Docker installs redis and starts it as a configuration file
Seal player IP and machine code and unlock the blocked tutorial
分组加密模式 ECB、CBC、PCBC、CFB、OFB、CTR
MySQL massive write problem optimization scheme MySQL parameter tuning
MySQL8.0.23四次重装都失败在 'Writing configuration file'
DDD:如何领用领域驱动设计来避免写流水账代码
Shell | incomplete summary of the method of viewing the process
go中高并发下的锁是如何工作的(结合源码)
MySQL uses commands to export and import in Windows
[215] Gin Framework connection to MySQL Database
Major optimization of openim - Message loading on demand, consistent cache, uniapp Publishing
物联网之Zigbee系统开发一(zigbee简介)[通俗易懂]
aspose的仓库地址
Mpu9250 sensor
Problems encountered in the project and Solutions