当前位置:网站首页>Quick introduction to PKI system
Quick introduction to PKI system
2022-07-23 14:38:00 【Test notes of biting and crying apples】
This is the collection and collation of some knowledge points encountered in the current work .
One 、 What is? PKI
First ,PKI(Public Key Infrastructure) It's a system .
A public key infrastructure is one that includes hardware 、 Software 、 personnel 、 A collection of policies and procedures , It is used to realize the generation of key and certificate based on public key cryptosystem 、 management 、 Storage 、 Functions such as distribution and cancellation .
PKI The system is computer software and hardware 、 Combination of authority and application system . It is for the implementation of e-commerce 、 E-government 、 Office automation provides basic security services , So that users who don't know each other or are far away can communicate safely through the trust chain .
— Baidu Encyclopedia
To put it bluntly ,PKI Or provide mutual identification services , Ensure the safety of communication .
Next , Open Baidu's website , Learn more PKI Various roles in the system .
1. digital certificate
I'll talk to you , If you confirm that each other is the person you want to talk to ? Then we can show each other our ID cards , To prove each other's identity is reliable .
that , In network communication , Such media is also needed , That's digital certificate .
Click the small lock icon on the left of Baidu website , The browser will display the following , Tell you that this connection is secure .
The reason why the browser can confirm Baidu's identity , Because of digital certificate . Click this button , You can further see the certificate related information .

Information can be roughly divided into 3 class :
1.1 Users
- User information , If it is an enterprise, here is the domain name , The example is baidu.com….
- Public key information , Here is the user's public key in asymmetric encryption , Anyone can see .、
- The period of validity
1.2 Issued by the
- Issued by the : Who issued the certificate , there GlobalSign Organization Validation.
- Signature of the issuer : The issuer digitally signs all the information of this certificate , It shows that he is responsible for the authenticity of this certificate .
1.3 Other information about the certificate
Other information about certificates
Based on this , When a browser accesses https The website of , Will check the validity of the certificate , Use the information in the certificate after passing ( Mainly public key ) Communicate with the website .
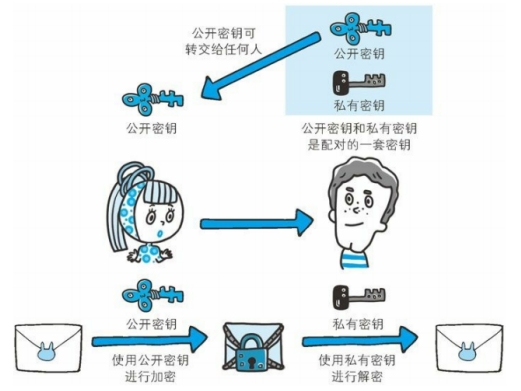
2. Public key encryption ( Asymmetric encryption )
The key of digital certificate is public key , That is, asymmetric encryption algorithm . It has 2 A character :
- Private key (private key): The private key can't be known to anyone else .
- public key (public key): The public key can be released at will , Anyone can get .
The interaction process is like this ( Send ciphertext to A, The receiving party B):
- A Use B Public key for encryption .
- A Send encrypted information to B.
- B After receiving the encrypted message , Decrypt with your own private key .
In this way , You don't need to send a private key to decrypt , So you don't have to worry about the key being stolen by the attacker .
in addition , Even if you know the public key and ciphertext , It's extremely difficult to get back to the original information . Because the decryption process is to evaluate the discrete logarithm , It's not easy to do .
Let's go one step further , If we can factorize a very large integer quickly , There is hope for password cracking . But in terms of current technology, it's not realistic .
3. PKI On stage
The above public key encryption method still has a problem :
- It cannot be proved that the public key itself is a genuine public key .
such as ,A Preparing and B The server establishes the communication under the public key encryption mode ,A And I did receive the public key . however A I don't know if this public key really comes from B, Maybe in transit , The real public key has been replaced by the attacker .
therefore , A mechanism is also needed to prove that these contents in the process are reliable , Here we need to mention at the beginning PKI System , Its core is the generation and distribution level of certificates .
The generation of certificates comes from an important role : Digital certificate authority (CA,Certificate Authority).
There are about dozens of roots in the world CA(Certificate Authority), These will be preset on the computer CA The digital certificate of . such as Amazon、Verisign such , They have a whole set of mechanisms to ensure that they are credible . Based on this , They have their own digital certificates , And the matching private key .
If the website wants to get its own certificate , You can find a piece CA, Fill in the information and pay the annual fee , You can get the certificate . When the browser visits the website , I see that you have the certificate issued by the authority in the industry , I will trust you unconditionally after I check that there is no problem .

ad locum ,PKI The system must provide users with safe and transparent services , Users do not have to consider PKI How to generate certificates in the system 、 to update 、 Revoked and restored , How are keys managed , As long as users can easily obtain digital signatures .
Two 、PKI Applications in the automotive industry
PKI The system is widely used in the automotive industry , Such as remote vehicle control 、 Near field vehicle control 、 Safe start 、Ethernet Communication security and so on . Here is the one with the highest priority “ Remote vehicle control ” Example .
1. Build your own PKI system
Enterprises should first establish their own PKI system , That is to introduce a PKI supplier , Issue the certificate 、 apply 、 Revocation and other public modules are established . Next , On top of it , Establish the process of each application .

2. Each end is connected PKI system
Mobile terminal 、 Cloud and car Tbox, Both generate their own private keys locally , And apply for your certificate in the cloud . This also requires the development of corresponding business processes .
All three terminals need to keep their private keys properly , The mobile terminal can store the private key in TEE in , There are many choices that can be stored in the cloud , The car end can be stored in HSM or TEE in . Without the storage mode of these hardware , You can use the white box encryption method of the software , Security is also guaranteed . White box encryption means that even if you encounter a white box attack , Its key is also difficult to crack .
3. Start business
After everyone has the certificate and private key , The business process becomes quite simple .

- There are many interactions between cloud and vehicle , It is recommended that both ends exchange through two-way authentication “ session key ”( Symmetric key ). Because symmetric encryption is thousands of times faster than asymmetric encryption , It will change slightly according to the length of the key . The process of exchanging session keys can be referred to TLS Two way authentication handshake process .
- The mobile terminal sends the vehicle instructions to the cloud , And sign with your private key . After receiving it in the cloud , Using mobile phone A The digital certificate of , Conduct signature verification .
- The cloud uses the negotiated vehicle control instructions “ session key ” After encryption , Send it to the vehicle end . After vehicle end verification , It can be executed internally .
therefore , be based on PKI The scheme of the system is more reliable .
Reference article :
https://zhuanlan.zhihu.com/p/237155609
https://www.cnblogs.com/pingguo-softwaretesting/p/14970453.html
https://zhuanlan.zhihu.com/p/377562137
边栏推荐
- 固定资产管理系统哪家好?固定资产管理平台有哪些?
- 【 langage c】 devinez jeux numériques + applet d'arrêt
- How can manual testing turn to automated testing? Byte 5 years of automation experience talk about
- Drag and drop----
- 链下数据互操作
- Work notes: one time bag grabbing
- 股票炒股开户风险性大吗,安全吗?
- 云呐|公司固定资产如何管理?公司固定资产如何管理比较好?
- C language implementation of classroom random roll call system
- Optimisation du serveur Cloud Huawei avec connexion clé
猜你喜欢
随机推荐
Which is a good fixed asset management system? What are the fixed asset management platforms?
剑指 Offer 46. 把数字翻译成字符串
【FLink】FLink Hash collision on user-specified ID “opt“. Most likely cause is a non-unique ID
动态规划-- 背包问题
AI acceleration gesture recognition experience based on efr32mg24
Solve a series of problems in using Bert encoder
After using vscode to format the code, save and find that the code is messy again. What should I do? Vs remove formatting
Canvas from getting started to persuading friends to give up (graphic version)
Find the maximum area of the island -- depth first search (staining method)
[WinForm] desktop program implementation scheme for screenshot recognition and calculation
(heavy chain dissection) Magic Tree
基于EFR32MG24的AI 加速度姿势识别体验
Consensys Quorum Benchmark Test
几种点云(网格)孔洞填充方法(1)
wacom固件更新错误123,数位板驱动更新不了
How can manual testing turn to automated testing? Byte 5 years of automation experience talk about
初识并查集
力扣142题:环形链表2
【我可以做你的第一个项目吗?】GZIP的细节简介和模拟实现
Ffmpeg 1 - Overview / installation



![寻找峰值[抽象二分练习]](/img/99/122e79784f0f07120680d2cbcf89da.png)