当前位置:网站首页>Cache penetration and bloom filter
Cache penetration and bloom filter
2022-07-03 12:50:00 【Mcc_ mingchao】
What is cache penetration ?
Cache penetration is simply A lot of Requested key It doesn't exist in the cache at all , Causes the request to go directly to the database , There's no caching at all . for instance : Some hacker deliberately creates something that doesn't exist in our cache key Make a lot of requests , Causes a large number of requests to fall to the database .

We usually use bloom filter to solve cache penetration , Store the values of all possible requests in the bloom filter , When the user requests to come , First judge whether the value of the request from the user exists in the bloom filter . If it doesn't exist , Directly return the request parameter error information to the client , If there is one, the following process will be followed .

( Add bloom filter )
- You can actually think of it as a binary vector ( Or bit array ) And a series of random mapping functions ( hash function ) Two part data structure .
- Its advantage is that the spatial efficiency and query time are much better than the general algorithm , The disadvantage is that it has certain error recognition rate and deletion difficulty .

As shown in the figure , When adding elements to the bloom filter , This element first generates different hash values by multiple hash functions , Then the elements in the following table of the corresponding digit group are set to 1( When the bit array is initialized , All positions are 0). When the same string is stored the second time , Because the previous corresponding position has been set to 1, So it's easy to know that this value already exists .
If we need to judge whether an element is in the bloom filter , Just do the same hash again for the given string , After getting the value, judge the Every element Is it all for 1, If the value is 1, So this value is in the bloom filter , If there is a value that is not 1, Indicates that the element is not in the bloom filter .
Different strings may be hashed out in the same place , In this case, we can increase the number group size or adjust our hash function .
therefore , The bloom filter says that an element exists , A small probability will miscalculate ,( Like in the picture d, Although the positions obtained by three hash functions are 1, When they are all put in by different elements before ) The bloom filter says that an element is not there , Then this element must not be in .
The following is a very simple analog bloom filter I wrote , For the convenience of understanding , I acquiesce key It's all numbers , But in reality, more often than not, strings
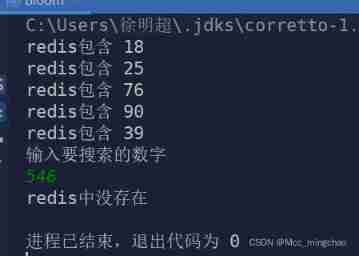
import java.util.HashSet; import java.util.Random; import java.util.Scanner; import java.util.Set; public class Bloom { static public int hash1(int x){ return x%7; } static public int hash2(int x){ return x%17; } static public int hash3(int x){ return x%27; } public static void main(String[] args) { boolean arr[]=new boolean[27]; Set set=new HashSet(); for(int i=0;i<5;i++){ Random random=new Random(); int r=random.nextInt(100); System.out.println("redis contain "+r); set.add(r); arr[hash1(r)]=true; arr[hash2(r)]=true; arr[hash3(r)]=true; } int x=0; System.out.println(" Enter the number to search "); Scanner sc=new Scanner(System.in); x=sc.nextInt(); if (arr[hash1(x)] == true &&arr[hash2(x)] == true&&arr[hash3(x)] == true){ if(set.contains(x)){ System.out.println(" eureka ");; } else{ System.out.println(" misjudged "); set.remove(x); } } else{ System.out.println("redis Does not exist in "); } } }
The effect is as shown in the picture
边栏推荐
- 【数据挖掘复习题】
- idea将web项目打包成war包并部署到服务器上运行
- Detailed explanation of the most complete constraintlayout in history
- Use bloc to build a page instance of shutter
- Approve iPad, which wants to use your icloud account
- 电压环对 PFC 系统性能影响分析
- Sword finger offer06 Print linked list from end to end
- 剑指Offer10- I. 斐波那契数列
- 【习题五】【数据库原理】
- Record your vulnhub breakthrough record
猜你喜欢
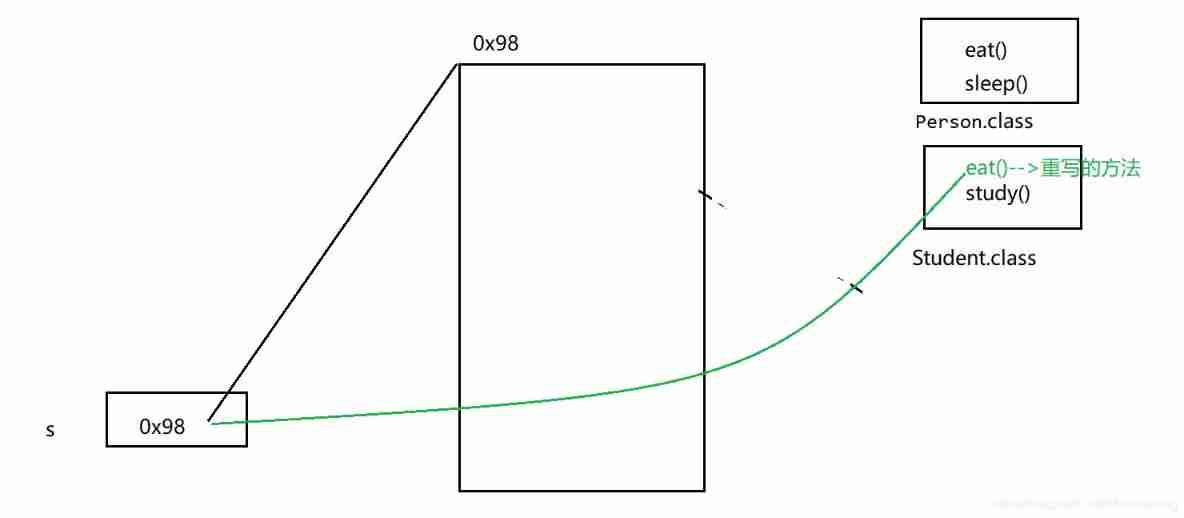
Method overloading and rewriting

The latest version of blind box mall thinkphp+uniapp

T430 toss and install OS majave 10.14
【ArcGIS自定义脚本工具】矢量文件生成扩大矩形面要素
2021 autumn Information Security Experiment 1 (password and hiding technology)

并网-低电压穿越与孤岛并存分析
记录自己vulnhub闯关记录

剑指Offer10- I. 斐波那契数列

ncnn神经网络计算框架在香橙派OrangePi 3 LTS开发板中的使用介绍

Solve the problem of VI opening files with ^m at the end
随机推荐
[ArcGIS user defined script tool] vector file generates expanded rectangular face elements
Approve iPad, which wants to use your icloud account
What is more elegant for flutter to log out and confirm again?
社交社区论坛APP超高颜值UI界面
【习题七】【数据库原理】
自抗扰控制器七-二阶 LADRC-PLL 结构设计
Application of ncnn Neural Network Computing Framework in Orange Pi 3 Lts Development Board
Application of ncnn neural network computing framework in orange school orangepi 3 lts development board
剑指Offer04. 二维数组中的查找【中等】
Day 1 of kotlin learning: simple built-in types of kotlin
Keep learning swift
Enter the length of three sides of the triangle through the user, and calculate the area of the triangle, where the length is a real number
剑指Offer07. 重建二叉树
Ali & ant self developed IDE
ncnn神经网络计算框架在香橙派OrangePi 3 LTS开发板中的使用介绍
基于同步坐标变换的谐波电流检测
Pytext training times error: typeerror:__ init__ () got an unexpected keyword argument 'serialized_ options'
Simple use and precautions of kotlin's array array and set list
ORM use of node -serialize
Sword finger offer07 Rebuild binary tree