当前位置:网站首页>TCP sliding window, singleton mode (lazy and hungry) double checked locking / double checked locking (DCL)
TCP sliding window, singleton mode (lazy and hungry) double checked locking / double checked locking (DCL)
2022-07-24 20:00:00 【It's seventh uncle】
TCP Sliding window of
Zhihu Video Explanation : Network transmission principle : What is? TCP The sliding window 
Sliding window of network programming (TCP flow control )
The singleton pattern ( Lazy and hungry )
In traditional textbooks, there are two kinds of single case mode , It's a hungry man style , A lazy style . The corresponding code is as follows :
Explain in detail the dual hungry man mode and the lazy man mode : Lazy mode in singleton mode , Starving model , Double check lock / Double check lock
Hungry Chinese style
public class Singleton {
private static Singleton instance = new Singleton(); // It will be instantiated when the class is loaded
private Singleton (){
}
public static Singleton getInstance() {
return instance;
}
}
Hungry Chinese instantiates when the class is loaded , Call directly when using getInstance() Method. This mode is thread safe , In multi-threaded concurrency mode, objects will not be instantiated repeatedly .
advantage : Efficient shortcoming : Premature object instantiation , Waste memory resources
The sluggard model
public class Singleton {
private static Singleton singleton;
private Singleton() {
}
public static Singleton getInstance() {
if (singleton == null) {
singleton = new Singleton();
}
return singleton;
}
}
This mode does not instantiate objects at load time , It's calling getInstance() Method to instantiate the object, Lazy is used to avoid premature instantiation , Reduce the waste of memory resources .
advantage : The first call initializes , Avoid memory waste . shortcoming : Only suitable for single thread , Thread unsafe
Reference resources : Use singleton mode to talk about thread safety
Double check lock / Double check lock (DCL, namely double-checked locking)
Reference resources : Double check lock / Double check lock (DCL, namely double-checked locking) Detailed analysis
public class Singleton {
private volatile static Singleton instance;
private Singleton() {
}
public static Singleton getInstance() {
if (instance == null) {
synchronized (Singleton.class) {
if (instance == null) {
instance = new Singleton();//erro
}
}
}
return instance;
}
public static void main(String[] args) {
Singleton.getInstance();
}
}
Why double check
public static Singleton getInstance() {
if (instance == null) {
// Threads 1,2 Arrive at the same time , All pass (instance == null) Judge .
// Threads 1 Enter the following synchronization block , Threads 2 Blocked
synchronized (Singleton.class) {
if (instance == null) {
// Threads 1 Perform discovery instance by null, After initializing an instance , Release the lock .
// Threads 2 Go into sync block , this instance Has been initialized . Unable to get if Conditions , Avoid repeated initialization .
instance = new Singleton();
}
}
}
return instance;
}
Double check is performed because , If multiple threads pass the first detection , At this time because synchronized, One of the threads will first pass the second detection and instantiate the object , The remaining threads will not instantiate the object repeatedly . such , In addition to locking during initialization , Subsequent calls return directly , It solves the redundant performance consumption .
Why use volatile Double lock
if (instance == null) {
instance = new Singleton();//erro
}
If not used volatile keyword , The hidden trouble comes from the comments in the above code erro A line , This line of code has roughly the following three steps :
- Open up the space required for objects in the heap , Allocation address
- Initialize according to the initialization order of class loading
- Return the memory address to the reference variable in the stack
because Java The memory model allows “ Unordered write ”, Some compilers for performance reasons , It is possible to 2 and 3 Reorder , The order becomes
- Open up the space required for objects in the heap , Allocation address
- Return the memory address to the reference variable in the stack ( At this time, the variable is no longer null, But variables are not initialized )
- Initialize according to the initialization order of class loading

Reference resources : The double check lock implements the singleton mode
边栏推荐
- Original reverse compensation and size end
- Safe way -- Analysis of single pipe reverse connection back door
- clip:learning transferable visual models from natural language supervision
- 英文翻译中文常见脏话
- Ask a question: is there an error msg = ora-04036: instance usage when using CDC to monitor oracle
- Convolutional neural network CNN
- strlen函数剖析和模拟实现
- Sword finger offer 45. arrange the array into the smallest number
- Valdo2021 - vascular space segmentation in vascular disease detection challenge (I)
- Browser local storage webstroage
猜你喜欢
![[face to face experience of school recruitment] 8 real questions of pointer interview. Come and test how many you have mastered.](/img/2c/e687b224285aeee66dacace6331161.png)
[face to face experience of school recruitment] 8 real questions of pointer interview. Come and test how many you have mastered.

聊下自己转型测试开发的历程
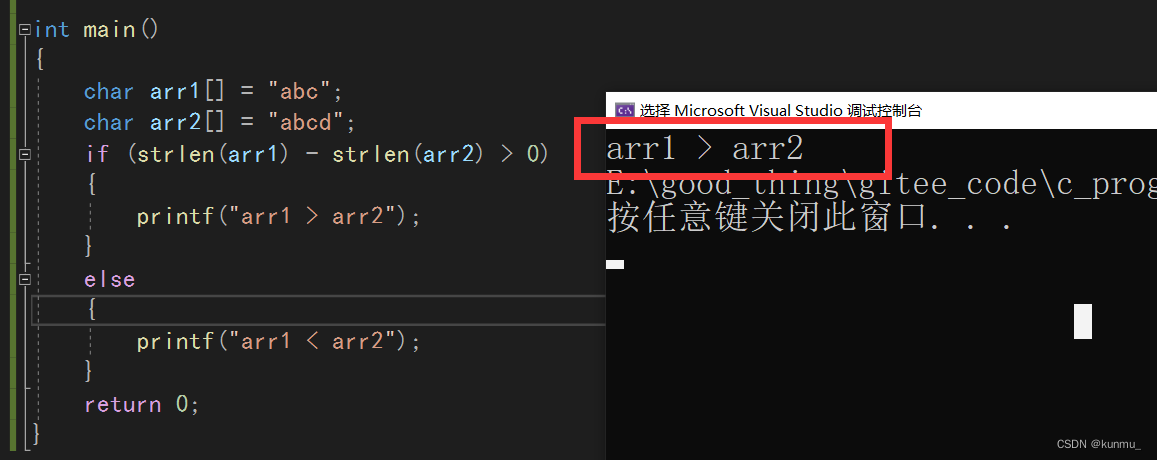
Analysis and Simulation of strlen function

Are network security and data security indistinguishable? Why is data security important?

Unity2d~ game practice of decrypting Zhou mu (completed in three days)

Usage and introduction of MySQL binlog

01 | 开篇词:手把手教你搭建一个博客网站

Flink window & time principle

Choose the appropriate container runtime for kubernetes

How to export map files tutorial
随机推荐
Unity3d eventsystem (event)
Sword finger offer 50. the first character that appears only once
Prevent static decompilation, dynamic debugging and plug-in
Setting up a dual machine debugging environment for drive development (vs2017)
微服务架构 | 服务监控与隔离 - [Sentinel] TBC...
Basic idea of regularization
Please ask a question. Follow the quick start method. After creating the table, the Flink SQL queries and displays the table structure, but there is an error when it exceeds the limit. What should we
从码农转型大音乐家,你只差这些音乐处理工具
Unity2d~ game practice of decrypting Zhou mu (completed in three days)
How to view the execution plan of a stored procedure in Youxuan database
6.0 holes stepped by fragment request permission in the system
01 | 开篇词:手把手教你搭建一个博客网站
Look at the interface control devaxpress WinForms - how to customize auxiliary function properties (Part 2)
Siyuan notes V2.1.2 synchronization problem
Choose the appropriate container runtime for kubernetes
Work notes - some problems encountered when using jest
Is the incremental update of SQL Server database identified according to the where clause? Can't do stream update? Each table should
湖仓一体释放全量数据价值,SequoiaDB v5.2线上发布会重磅来袭
Conversion between VC string and timestamp
Redisgraph graphic database multi activity design scheme