当前位置:网站首页>05. Security of blog project
05. Security of blog project
2022-07-06 05:22:00 【John is orange】
Security of blog project
SQL Inject : Steal database content
XSS attack : Steal the front end cookie Content
Password encryption : Protect the information security of users
Add
- server There are many ways to attack the client , In case there are many means
- This article talks about common 、 Can pass web server (nodejs) Level preventive
- Some attacks require hardware and services to support ( need OP Support ), Such as DDOS
1. SQL Inject
- The most primitive 、 The simplest attack , Since then web2.0 And then there is SQL Injection attack
- attacks : Enter a SQL fragment , Finally spliced into a piece of attack code
- Preventive measures : Use MySQL Of escape Function handles the input
For example, login verification now , It is executed after string splicing SQL Statement to achieve :
const {
exec } = require("../db/mysql");
const login = (username, password) => {
const sql = ` select username, realname from users where username = '${
username}' and password = '${
password}'; `;
return exec(sql).then((rows) => {
return rows[0] || {
};
});
};
module.exports = {
login,
};
SQL Statements such as :
select username, realname from users where username = 'zhangsan' and password = '123456';
Password free user
But if the user name entered is zhangsan ' -- , Then annotate the following statement , Even if the password is wrong, you can use zhangsan Login to .
select username, realname from users where username = 'zhangsan' -- ' and password = '123456';
Delete library
If someone's user name is zhangsan';delect from users; -- , The consequences are more serious , The direct database is completely deleted .
select username, realname from users where username = 'zhangsan';delect from users; -- ' and password = '123456';
resolvent
Use escape characters . Escaping sensitive symbols can avoid this problem .mysql The library provides mysql.escape Method , Used to escape content :
// controller/user.js
const {
exec, escape } = require("../db/mysql");
const login = (username, password) => {
username = escape(username);
password = escape(password);
const sql = ` select username, realname from users where username = ${
username} and password = ${
password}; `;
console.log(sql);
return exec(sql).then((rows) => {
return rows[0] || {
};
});
};
module.exports = {
login,
};
After the escape SQL The statement is as follows :
select username, realname from users where username = 'zhangsan \' --' and password = '123';
username The whole sheet is wrapped in quotation marks , The single quotation mark inside will be escaped , Therefore, it will not affect the query .
2. XSS attack
The most familiar attack method on the front end , but server The end should master
attacks : Mix js Code , To get web information
Preventive measures : Transformation generation js Special characters for
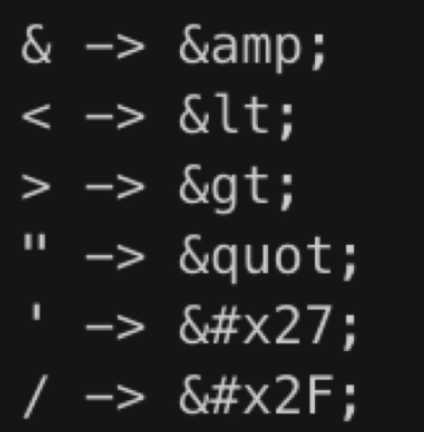
2.1 XSS Attack Demo
When I publish my blog, I enter the following content :
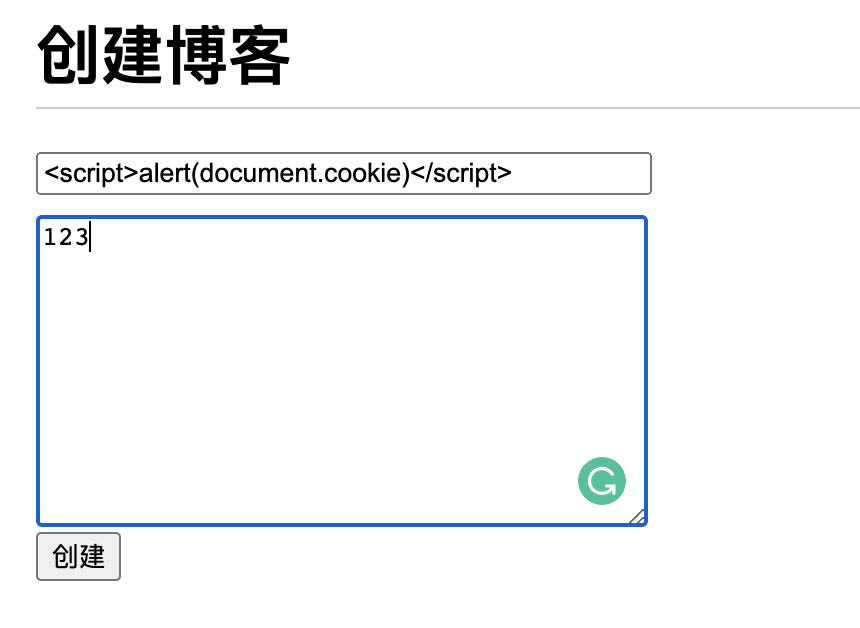
After successful creation, jump to the management center , because HTML Directly embedded in script Script , So will execute alert(document.cookie). So the transfer will generate script Script symbols are an effective way .
2.2 The prevention of XSS attack
Install third party libraries :
yarn add xss
Usage and the above escape Escape is very similar , Just wrap the string that needs to be escaped .
// controller/blog.js
const newBlog = (blogData = {
}) => {
// blogData Is a blog object , contain title、content、author attribute
blogData = {
...blogData,
createTime: Date.now(),
id: 3, // Indicates a new blog , Inserted into the data table id
};
const {
title, content, author, createTime } = blogData;
const sql = ` insert into blogs (title, content, createTime, author) values ('${
xss(title)}', '${
xss(content)}', ${
createTime}, '${
author}');`;
return exec(sql).then((insertData) => {
// promise Returns the inserted value corresponding to id
return {
id: insertData.insertId,
};
});
};
Realization effect :
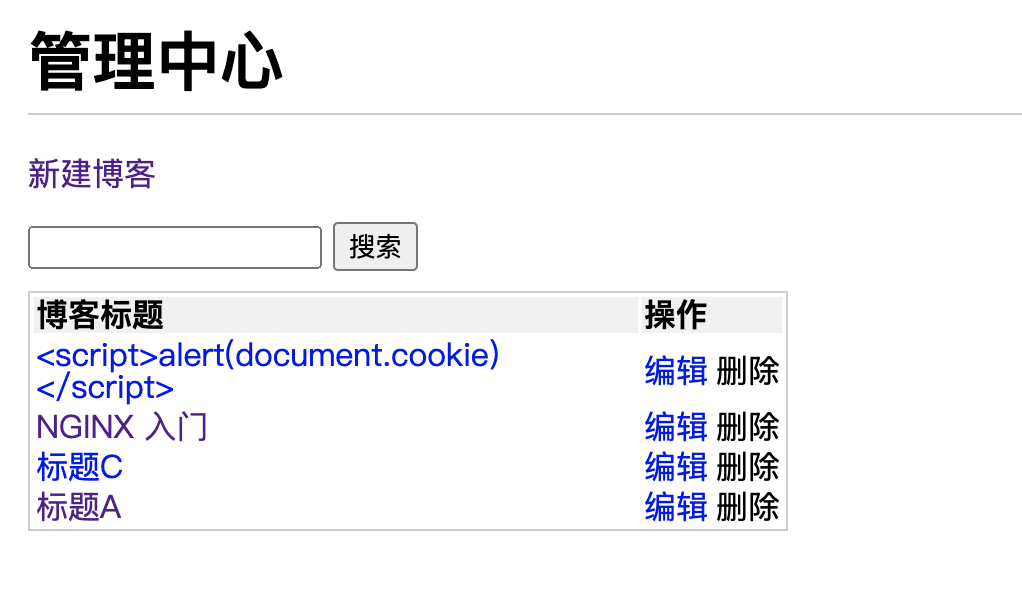
After the escape SQL The statement is as follows :
insert into blogs (title, content, createTime, author)
values
('<script>alert(document.cookie)</script>', '123', 1655309413840, 'zhangsan');
But in some places, the escape symbol may not escape , For example, the article details page :
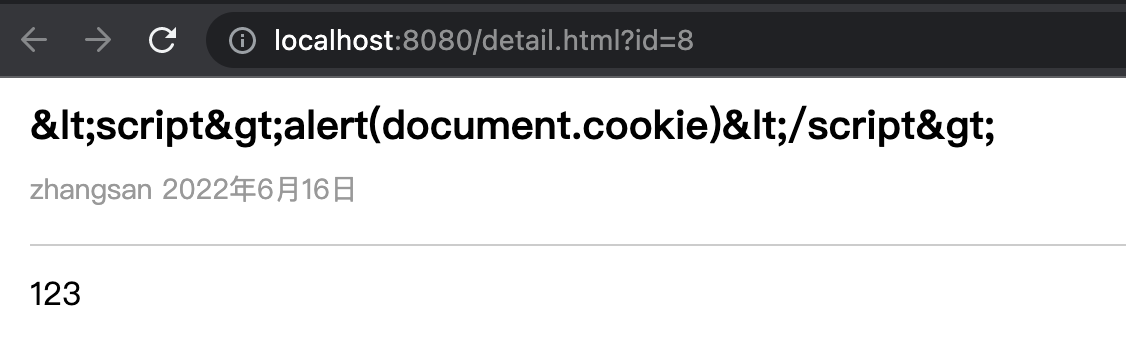
This kind of content needs to be handled by the front end rather than the back end .
3. Password encryption
- In case the database is broken by users , The last thing you should disclose is user information
- attacks : Get user name and password , Try logging into other systems
- Preventive measures : Encrypt the password , Even if you get the password, you don't know the plaintext
Encryption process :
First introduced node Self contained
cryptomodularconst crypto = require("crypto");stay utils New file in folder , Write the relevant logic of password encryption , Then get the encrypted content through this method , Then modify the original plaintext password in the database .
Of course, this step is unreasonable , But without the function of registration and password modification, there is no way .
const crypto = require("crypto"); // secret key const SECRET_KEY = "kfdsjl_742938#"; // md5 Encrypted content const md5 = (content) => { // The output becomes 16 Base number return crypto.createHash("md5").update(content).digest("hex"); }; // Encryption function const genPassword = (password) => { const str = `password=${ password}&key=${ SECRET_KEY}`; return md5(str); }; module.exports = { genPassword, };When logging in, the password is encrypted and queried , Because now the encrypted content is stored in the database .
// controller/user.js const { exec, escape } = require("../db/mysql"); const { genPassword } = require("../utils/cryp"); const login = (username, password) => { username = escape(username); // Generate encrypted password password = genPassword(password); password = escape(password); const sql = ` select username, realname from users where username = ${ username} and password = ${ password}; `; return exec(sql).then((rows) => { return rows[0] || { }; }); }; module.exports = { login, };
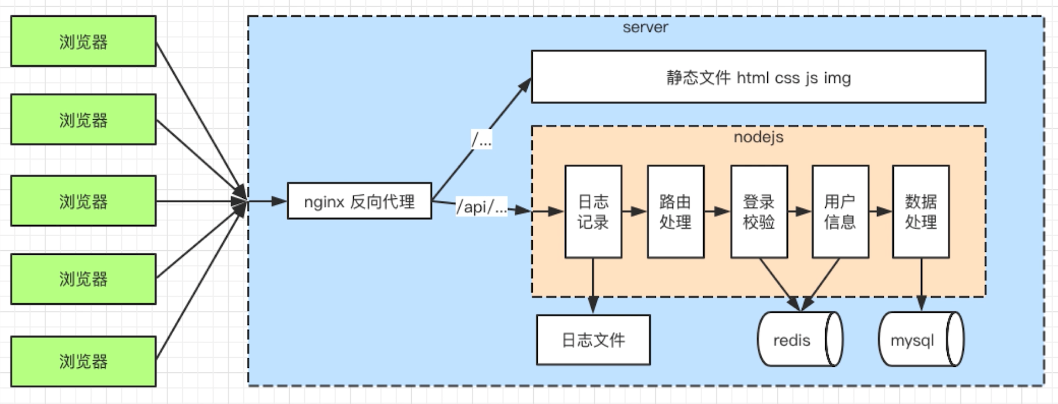
4. flow chart
- Handle http Interface
- Connect to database
- To realize the login
- Security
- journal
- go online
边栏推荐
- 算法-- 爬楼梯(Kotlin)
- The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
- Nacos - TC Construction of High available seata (02)
- Modbus protocol communication exception
- Oracle query table index, unique constraint, field
- Codeforces Round #804 (Div. 2) Editorial(A-B)
- [noip2009 popularization group] score line delimitation
- Safe mode on Windows
- 备忘一下jvxetable的各种数据集获取方法
- Class inheritance in yyds dry inventory C
猜你喜欢
【云原生】3.1 Kubernetes平台安装KubeSpher
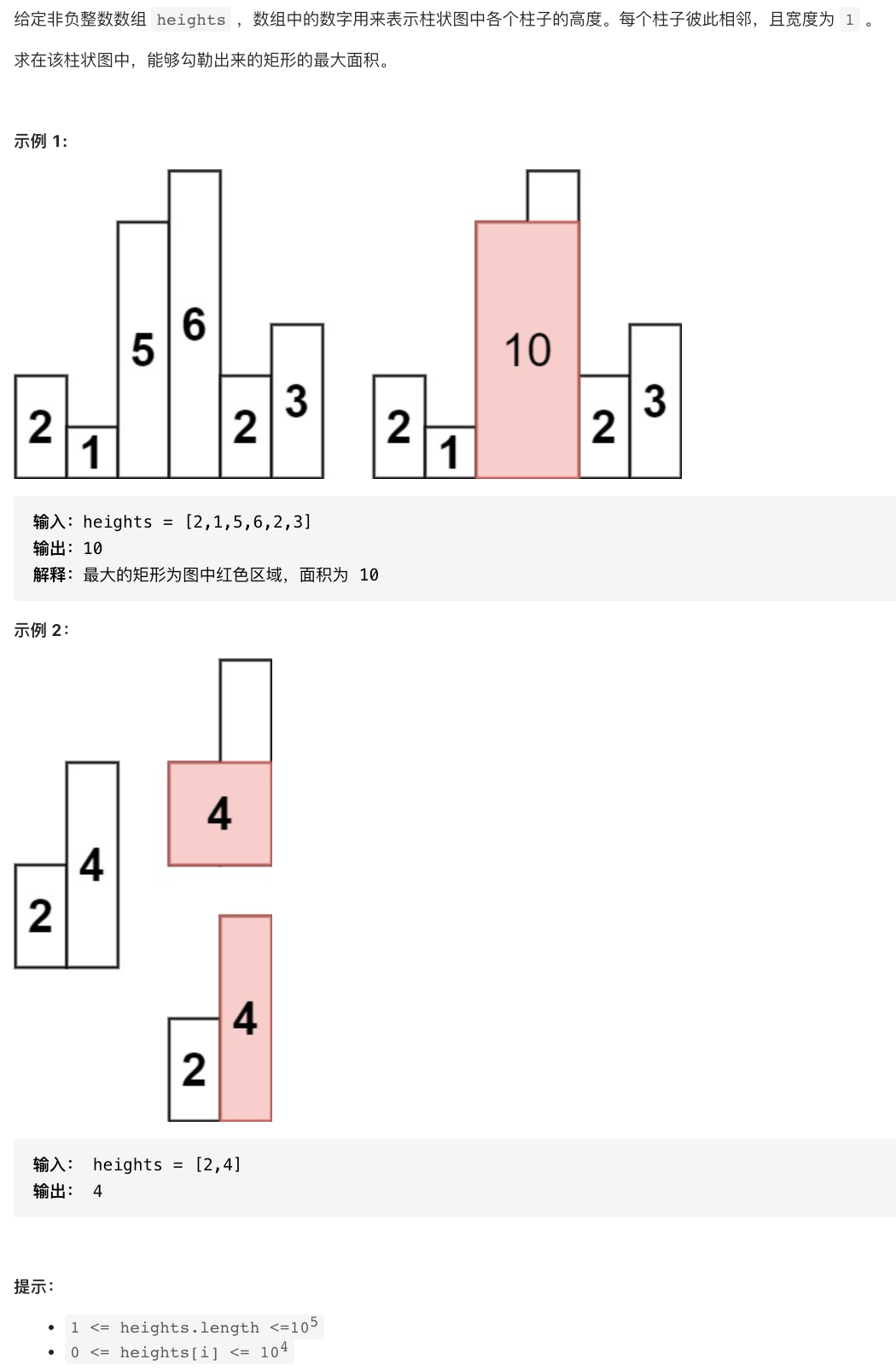
剑指 Offer II 039. 直方图最大矩形面积

Huawei equipment is configured with OSPF and BFD linkage

C进阶-数据的存储(上)
flutter 实现一个有加载动画的按钮(loadingButton)
Rce code and Command Execution Vulnerability
Nacos TC setup of highly available Seata (02)
自建DNS服务器,客户端打开网页慢,解决办法
Summary of deep learning tuning tricks
![[leetcode daily question] number of enclaves](/img/6e/1da0fa5c7d1489ba555e4791e2ac97.jpg)
[leetcode daily question] number of enclaves
随机推荐
03. 开发博客项目之登录
[noip2009 popularization group] score line delimitation
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
Cuda11.1 online installation
Vulhub vulnerability recurrence 69_ Tiki Wiki
Postman manage test cases
Imperial cms7.5 imitation "D9 download station" software application download website source code
Simple understanding of interpreters and compilers
Pix2pix: image to image conversion using conditional countermeasure networks
Promotion hung up! The leader said it wasn't my poor skills
Three.js学习-光照和阴影(了解向)
Compilation and connection of shader in games202 webgl (learn from)
集合详解之 Collection + 面试题
JS quick start (II)
js Array 列表 实战使用总结
February 12 relativelayout
Building intelligent gray-scale data system from 0 to 1: Taking vivo game center as an example
Driver development - hellowdm driver
UCF (2022 summer team competition I)
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower