当前位置:网站首页>SQL injection vulnerability (type chapter)
SQL injection vulnerability (type chapter)
2022-06-25 11:28:00 【errorr0】
Don't go the way hackers go , Never know what they did , Knowing does not necessarily mean understanding . But if you experience it personally, you will have a different understanding , You will also have a deeper understanding of the injection of some parameters . I've talked about it before SQL Principle of injection , So I won't go over it here , Let's go straight to the dry goods .( The following vulnerability descriptions are based on MYSQL Database language as an example )
SQL Inject There are several categories , Let's get to know :
SQL Injection classification
For parameters SQL Inject There is Character injection 、 Digital injection .
Character injection : Parameters are wrapped in some other symbols , Like single quotes 、 Double quotes 、 Parentheses, etc .
Digital injection : Parameter has no package , It can be injected directly , This is the most dangerous , The closing step is omitted .
Press submission Classification exists :GET Inject 、POST Inject 、COOKIE Inject 、HTTP Request header Injection (User-Agent Inject 、XFF Head injection 、Referer Inject ). Strictly speaking COOKIE Inject It is HTTP Request header Injection A kind of .
GET Inject : Usually in url Direct manual injection on the (url Link to a web page ).
POST Inject :POST The submission is usually in the submission box of some accounts and passwords ( Of course, it could be other areas ), Attack injection points need to be utilized hackbar Tool submission POST Or directly to them http In the agreement POST Submit data for injection .
COOKIE Inject :COOKIE Can be modified directly with F12 View the existing in the application COOKIE, It can be modified and injected .
HTTP Request header Injection : This needs to be right HTTP Re contract the modification package for the requested data .
according to Method of injection There are : Joint injection 、 An error injection 、 Bull's blind note 、 Time blind note 、 Stack Injection 、 Wide byte Injection 、 The secondary injection 、DNSlog Inject .
Joint injection
That's one SQL sentence Combine the data of two tables , If the data query of the first table is wrong, the data of the second table will be echoed to the page .
The basic sentence is :1' union select 1,2,group_concat(schema_name) from information_schema.schemata-- The point is that union And select, If it is filtered, it has to find another way , Find some ways to bypass , That kind of thing is sql Inject advanced learning .
An error injection
There are several functions available :extractvalue()、updatexml()、exp()、floor() wait .
updatexml()
Let me briefly introduce updatexml() Error reporting injection principle of , See the following example :
UpdateXML(xml_target, xpath_expr, new_xml)
xml_target:: Operation required xml fragment
xpath_expr: Need to be updated xml route (Xpath Format )
new_xml: Updated content
This function updatexml() There are three parameters , The first one and the third one won't say , Look directly at the second parameter , The second parameter type required by the function is XML(XPATH), If XPATH The path is not XML Or when there is a syntax error , You're going to report a mistake , Error content contains wrong path content , Because this is also a sentence sql sentence , So it will put sql sentence Error reporting after execution , Finally, the queried data is brought out . If you are interested, you can learn about it extractvalue(), It is associated with updatexml() The principle of error reporting is similar .

exp()
exp() Originally it was for e Of x The function of the power ,x That is, the parameter in brackets , But some masters with big brain holes have found that

stay 709 Errors will be reported later , The value obtained from the negation of this query statement is particularly large
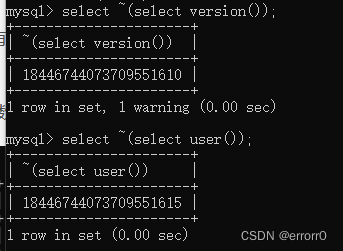
So here comes the interesting one , If we put a layer on the outside exp(), Because this value is greater than 709 Of , If an error is reported, the result of our query will be carried out . But pay attention to the use of this hole MySQL The version is >=5.5.5, If my version is too low, there will be no screenshot of the test results , Let's get a general idea of the process .
floor()
be supposed to floor() The error reporting injection is a bit one-sided , It's actually floor() coordination group by And rand() Joint operation will lead to the generation of errors . So why are errors reported ?
First, let's briefly talk about the functions of these three gadgets :
floor(): Take the largest integer not greater than this number , I.e. round down ;
group by x: take x As a primary key , Create a temporary table , if x If it does not exist in the table, create a new , If there are coun(*), be count() The count is self increasing 1;
rand(): Randomly generate one 0 To 1 Number of numbers .
Just these instructions can An error injection ? The answer is yes . And its error report is also very interesting , Let's start with two sentences sql Instructions

select count(*),Host from user group by concat(database(),floor(rand(0)*2));
select count(*),Host from user group by concat(database(),floor(rand(1)*2));The test of this result is uncertain , Because it's a random number . So why rand() The results are not the same with different seeds ? In fact, I am not very clear about the underlying principle here , But according to other masters' articles and my own guess , We can think of it this way ( If you have any questions, please correct them ):
First group by The following data is the primary key in the temporary table , Whether the temporary table exists or not ,rand() Will be executed twice , Which two times ? The first is group by To determine if there is database()floor(rand(0)*2) This primary key value , The second time it was deposited, it was executed again floor(rand(0)*2), So here comes the question , If database()1 There is , And for the first time group by Judge floor(rand(0)*2) by 0, If the temporary table does not exist database()0, Then we need to generate database()floor(rand(0)*2) This primary key , But we did it once when we deposited floor(rand(0)*2), And if this time floor(rand(0)*2) No 0 It is 1 了 , Then there would have been database()1, And because rand() Why , Force to insert the same primary key , The primary key names in the known database are not the same , So it will report a mistake , And its error report is to concat() The data in .
So we can inject this into the case of the above example , It can also explain why different seeds appear in different situations , This is about probability , So if no error is reported , You need to test several times with different seed numbers .
Bull's blind note
bool type There are only two values ----1 and 0. That is right and wrong , The database name or table name or other data content we query will not be displayed , There is only one true or false echo that is not found , So we use the truncation of the found string into a single character to judge ASCII The value of the code , Use Boolean judgment to extract its string step by step .
There are three specific methods , Manual injection ( Especially troublesome )、 Brute force 、 Write a script to run ( Easiest ).
Manual injection : utilize substring Truncate the string, and then one character by one ASCII Using the value of >、=、<, Judge , Using the mean value theorem , as follows :
1'and ascii(substring(database(),1,1))=100--+Brute force : On the basis of manual injection , For its ASCII code Value brute force cracking ( More than a hundred times ), The final result is one character , With such a brute force crack, we can get a complete string .
Write the script : The general idea is similar to that of manual work , If the judgment of a string is correct, the normal interface will be returned , Make a comparison between the interface data and some unique ones to determine whether they are correct , Run down in turn .
By the way , The first two methods need to start with length() Get the database name or the length of other data .
Time blind note
That is, no error will be reported , There will be no right or wrong echo , Time blind injection is to create an environment to query whether the result is right or wrong , You can use if() coordination sleep(), When we execute a query against a statement sleep() wait for , We can guess that this is the correct statement , Otherwise, it is the wrong statement , This idea and Bull's blind note It's kind of similar . The difference between them is , Bull's blind note It is injected through page echo , Time blind note It is injected through response time , But the thinking is the same , Right and wrong sql Statements get different results .
Time blind note Another function is benchmark(), It is also used for delay , Don't explain too much , Those who are interested can learn about it .
Stack Injection
One SQL Inquire about The statement ends with a semicolon , If you do not limit the number of queries , One semicolon executes one sql Inquire about , Then you can execute more than one statement at a time sql Inquire about .
therefore Stack Injection The principle of is another sql Inquire about , Through another sql Query the sensitive information you want to find .
Wide byte Injection
To prevent conflicts with closed characters from causing errors , Therefore, the program design has escaped some special characters that have to be input , That is, the backslash is added before the sensitive character , If we enter a single quotation mark, it will actually be \' such .
The way around this escape is called Wide byte Injection . Known characters occupy one byte , Chinese characters occupy two bytes , So in GBK code If you happen to encounter two characters by chance GBK code , And it happens to be a Chinese character , The code is also GBK Format . Then the original two characters become a Chinese character , This is the same. Wide byte Injection Principle , We'll try to put something in front of the single quotation marks , Make it relate to The backslash Can be combined into one character , Finally, the annexation The backslash The function of . Look at an example ,

You can see what we entered Single quotation marks It's escaped , So try to get around this The backslash , After inquiry, we know that The backslash Of GBK code by %5C

Then the interesting ones will come , Yes GBK Encoding table We know that , More than a few %DE、%DF、%E0 Will 5C Merge into one Chinese character .

The secondary injection
Insert... For the first time SQL sentence There is no special function and echo of the data , But the injection problem occurred during the operation of the program .sqli-labs There is a question in this article that it already exists admin user , Now create a admin'# user , But after warehousing, use this account to log in and change the password admin The administrator's password has been changed , That is, the result of secondary injection .
This injection attack belongs to the type of lingering long-term attack , And hard to detect .
DNSLOG Don't say , A little bit more , Write a separate introduction later .
Reference resources : About floor() An error injection , Do you really understand ? - FreeBuf Network security industry portal
Wrong type sql Injection principle analysis - Programmer base
Principle analysis of error reporting injection - JavaShuo
mysql Of floor() Error injection method detailed analysis ( Reprint )_Vap0R The blog of -CSDN Blog
边栏推荐
- 牛客网:分糖果问题
- Hangzhou / Beijing neitui Ali Dharma academy recruits academic interns in visual generation (talent plan)
- Démarrer avec Apache shenyu
- How to realize the rich text editor function of mobile terminal
- 反应c语言程序结构特点的程序
- 金仓数据库 KingbaseES 插件dbms_session
- 金仓数据库 KingbaseES 插件force_view
- Ladder Side-Tuning:预训练模型的“过墙梯”
- Handler、Message、Looper、MessageQueue
- Remove the problem of orange border on the desktop control in WebView
猜你喜欢
Upload and modify the use of avatars

牛客网:分糖果问题

SQL注入漏洞(繞過篇)
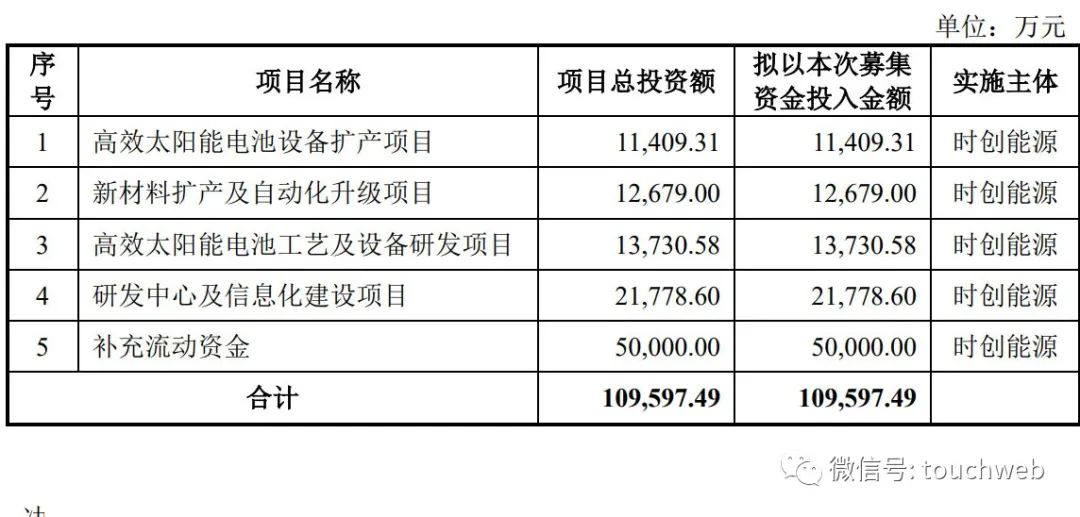
Shichuang Energy sprint Technology Innovation Board: le chiffre d'affaires annuel prévu de 1,1 milliard de RMB est de 0,7 milliard de RMB, en baisse de 36%

Geographic location system based on openstreetmap+postgis paper documents + reference papers + project source code and database files

Shichuang energy rushes to the scientific innovation board: it plans to raise 1.1 billion yuan, with an annual revenue of 700million yuan and a 36% decrease in net profit

翌圣生物冲刺科创板:25%收入来自新冠产品销售 拟募资11亿

scrapy+scrapyd+gerapy 爬虫调度框架

基于C语言的图书信息管理系统 课程论文+代码及可执行exe文件

中國信通院沈瀅:字體開源協議——OFL V1.1介紹及合規要點分析
随机推荐
数据库系列:MySQL索引优化总结(综合版)
Leetcode 1249. 移除无效的括号(牛逼,终于做出来了)
Very important very important very important very important very important very important very important very important very important
金仓数据库 KingbaseES 插件DBMS_OUTPUT
scrapy+scrapyd+gerapy 爬虫调度框架
金仓数据库 KingbaseES 插件dbms_session
GCC related
[shangyun boutique] energy saving and efficiency improvement! Accelerating the transformation of "intelligent manufacturing" in the textile industry
GaussDB 集群维护案例集-sql执行慢
建造者模式
Arrays. asList()
SystemVerilog (XIII) - enumerate data types
Spark history server performance improvement (I) -- Application List
Use of three-level linkage plug-ins selected by provinces and cities
贝叶斯
Gaussdb others scenarios with high memory
仿真与烧录程序有哪几种方式?(包含常用工具与使用方式)
16 enterprise architecture strategies
Tidb applicable scenarios
Jincang KFS data cascade scenario deployment