当前位置:网站首页>The essence of attack and defense strategy behind the noun of network security
The essence of attack and defense strategy behind the noun of network security
2022-07-26 09:03:00 【Domestic giant panda】
I think the attack and defense confrontation of network security is a confrontation on the cross coordinate
1) The attacker is concerned about source -> sink In the process of data flow , Whether there is an opportunity to attack , When attacking bypass The point is sanitize Is it tight enough
2) The corresponding protective personnel need to build protective measures at multiple levels , Whether it's the network layer 、 application layer 、 The host layer is erected tightly enough sanitize

3) As shown in the figure above , If we take blue in the figure as the coordinate system , Red 1 2 3 Think of it as three functions , The grey content is regarded as the dangerous threshold of function input
3.1) The danger threshold of function input parameter exceeds the green line , Then the safety personnel should receive the alarm , If the danger threshold exceeds the red line, the function call should be blocked directly
3.2) The order of function calls ( for example 1 2 3 Is a common buffer overflow attack chain ), Alarm or intercept if certain rules are met
3.3) Function input parameters and function order of function call ( for example 1 2 3 Is a common buffer overflow attack chain also The risk threshold of participation reaches the green line or even the red line ), Alarm or intercept if certain rules are met

summary : The security protection strategy is mainly aimed at the input parameter verification ( Ordinate )、 Logical chain check ( Abscissa ) And the double check of the input parameter combination logic chain ( Horizontal ordinate )
We bring this idea into practice :
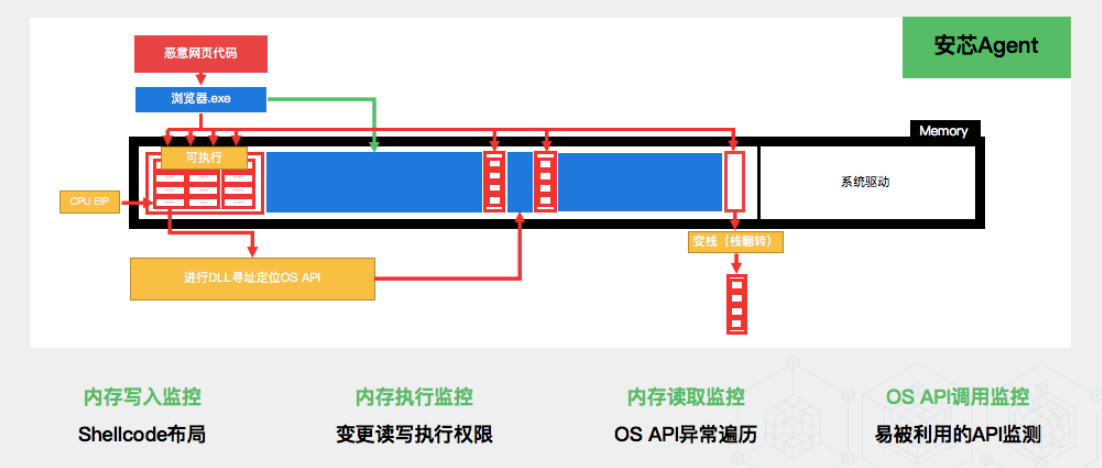
4)edr、hids、 Why do products such as situational awareness say their names are different , But the essence is the same ? Because they use the same protection theory
4.1) The danger threshold of function input parameter reaches the threshold , Corresponding to the implementation of a certain safety behavior ( Alarm or intercept )
4.2) The call order of the function has reached the threshold , Corresponding to the implementation of a certain safety behavior ( Alarm or intercept )
4.3) The input participating function call has reached the threshold , Corresponding to the implementation of a certain safety behavior ( Alarm or intercept )
Refer to the following figure :

5) Further, let's take a look at application protection RASP product , The underlying logic is exactly the same
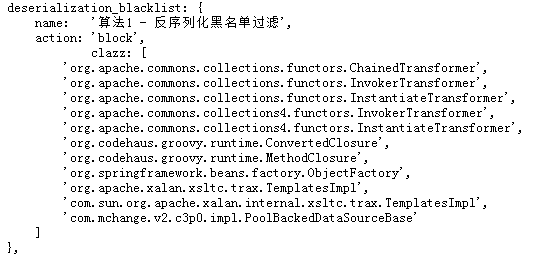
5.1) The danger threshold of function input parameters reaches a certain standard , Corresponding to the implementation of a certain safety behavior ( Alarm or intercept )
Take part in the picture below , Use the blacklist to intercept the call input parameters :
5.2) The calling sequence of functions meets a certain standard , Corresponding to the implementation of a certain safety behavior ( Alarm or intercept )
5.3) The input participating function call has reached the threshold , Corresponding to the implementation of a certain safety behavior ( Alarm or intercept )
Take part in the picture below , Verify the context logic and input parameters of the call stack :

6) As for the flow level, it is also completely consistent , But the real-time traffic is too high , It is difficult to do something similar to the application side 、 The host side can guarantee logical context verification , So at present, there is only one case basically covered by the flow side
6.1) The danger threshold of function input parameters reaches a certain standard , Corresponding to the implementation of a certain safety behavior ( Alarm or intercept )
7) Finally, let's talk about the so-called pseudo defense , Please look at the picture below first :

If you put XY Section formed by coordinates , As the coverage of a security policy .
Then the essence of pseudo defense is to compare and verify the integrity of each coverage using different logical implementation methods .
All network security protection is maintained : confidentiality 、 integrity 、 Usability
And the logic behind it can use one XYZ Coordinates explain , So please don't reinvent words , Please concentrate on improving the hard power of the industry .
Reference address :
https://mp.weixin.qq.com/s/cIJTyjusZbM5ndSTMjECUg
https://github.com/baidu/openrasp
Prohibited reproduced thank you
边栏推荐
- Learn more about the difference between B-tree and b+tree
- Qtcreator reports an error: you need to set an executable in the custom run configuration
- unity简易消息机制
- 垂直搜索
- Codeworks DP collection
- day06 作业--技能题2
- Probability model in machine learning
- Web overview and b/s architecture
- day06 作业---技能题7
- Database operation topic 2
猜你喜欢

第6天总结&数据库作业
2022流动式起重机司机考试题模拟考试题库模拟考试平台操作

Qtcreator reports an error: you need to set an executable in the custom run configuration

李沐d2l(五)---多层感知机
巴比特 | 元宇宙每日必读:元宇宙的未来是属于大型科技公司,还是属于分散的Web3世界?...

Database operation topic 1

Database operation topic 2

Study notes of automatic control principle --- stability analysis of control system

day06 作业---技能题7
![[eslint] Failed to load parser ‘@typescript-eslint/parser‘ declared in ‘package. json » eslint-confi](/img/39/135d29dae23b55497728233f31aa6a.png)
[eslint] Failed to load parser ‘@typescript-eslint/parser‘ declared in ‘package. json » eslint-confi
随机推荐
Flask project learning (I) -- sayhello
Learning notes of automatic control principle --- linear discrete system
PAT 甲级 A1076 Forwards on Weibo
[encryption weekly] has the encryption market recovered? The cold winter still hasn't thawed out. Take stock of the major events that occurred in the encryption market last week
day06 作业--技能题6
垂直搜索
idea快捷键 alt实现整列操作
Database operation topic 2
深度学习常用激活函数总结
day06 作业---技能题7
187. Repeated DNA sequence
网络安全漫山遍野的高大上名词之后的攻防策略本质
day06 作业--技能题2
Laravel框架日志文件存放在哪里?怎么用?
Horizontal comparison of the data of the top ten blue chip NFTs in the past half year
Okaleido launched the fusion mining mode, which is the only way for Oka to verify the current output
day06 作业--技能题1
Advanced mathematics | Takeshi's "classic series" daily question train of thought and summary of error prone points
Node-v download and application, ES6 module import and export
Hegong sky team vision training Day6 - traditional vision, image processing