当前位置:网站首页>Substr and substring function usage in SQL
Substr and substring function usage in SQL
2022-07-24 19:51:00 【Total dusk】
sql in substr And substring The usage function
Their functions are similar , Can intercept strings
Grammar introduction 1 :
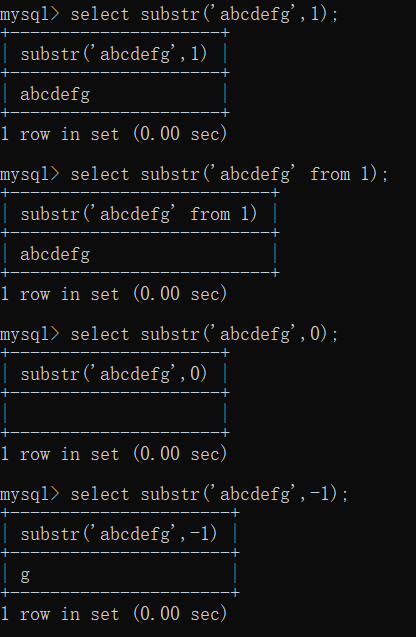
SUBSTR(str,pos) amount to SUBSTR(str FROM pos)
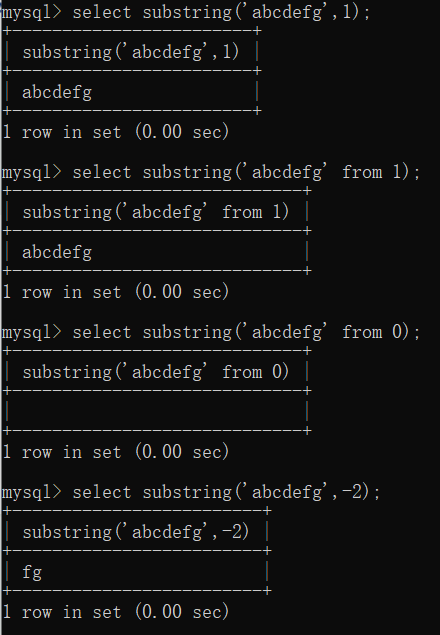
SUBSTRING(str,pos) amount to SUBSTRING(str FROM pos)
Parameter Introduction
str: The string to be intercepted
pos: The starting position is the number of characters you want to intercept
Be careful :
- The character count of the string is from 1 At the beginning , No 0, If pos Write the value as 0, Will return an empty
- The starting position can be negative , Negative numbers are reciprocal , The last character is -1
- The value returned is from pos Start to finish Substring of
Case study
substr:
substring:
Grammar introduction II :
SUBSTR(str,pos,len) amount to SUBSTR(str FROM pos FOR len)
SUBSTRING(str,pos,len) amount to SUBSTRING(str FROM pos FOR len)
Parameter Introduction
str: The string to be intercepted
pos: The starting position is the number of characters you want to intercept ( The points of attention are the same as above )
len: The length of characters you want to intercept ( Be careful : If this len<1, The result will return null )
result : Return from pos Start , The length is len Substring of
Case study
substr

substring

边栏推荐
- Getting started with COM programming 1- creating projects and writing interfaces
- 2019 Hangdian multi school first 6581 vacation [thinking]
- Wechat applet -that.setdata ({}) set complex field data
- Getaverse,走向Web3的远方桥梁
- Siyuan notes V2.1.2 synchronization problem
- Meshlab&PCL ISS关键点
- Techempower web framework performance test 21st round results release --asp Net core continue to move forward
- "Six pillars of self esteem" self esteem comes from one's own feelings
- Batch download files from the server to the local
- 【校招面经】8道指针面试真题,快来检测自己掌握了几道。
猜你喜欢

Look at the interface control devaxpress WinForms - how to customize auxiliary function properties (Part 2)
Redis basic knowledge, application scenarios, cluster installation

【JVM学习03】类加载与字节码技术

Clion configuring WSL tool chain

Read the registry through the ATL library clegkey (simple and convenient)

How to export map files tutorial

How to encrypt your own program with dongle
Meshlab&PCL ISS关键点

从码农转型大音乐家,你只差这些音乐处理工具

Analysis of the basic concept of digital warehouse
随机推荐
Codeforces round 580 (Div. 2) c- almost equal [Law]
【JVM学习04】JMM内存模型
Duilib actual combat 1- imitate Baidu online disk login interface
Batch download files from the server to the local
How to select software dongle
Hucang integrated release of full data value, sequoiadb V5.2 online conference heavy attack
Day 10 (inheritance, rewriting and use of super)
Techempower web framework performance test 21st round results release --asp Net core continue to move forward
Sword finger offer 53 - I. find the number I in the sorted array
Stop using UUID indiscriminately. Have you tested the performance gap between self incrementing ID and UUID?
Leetcode402 remove K digits
Read the registry through the ATL library clegkey (simple and convenient)
Pyhanlp installation tutorial
Detailed explanation of ELF format (I)
strlen函数剖析和模拟实现
从码农转型大音乐家,你只差这些音乐处理工具
【德味】安全:如何为行人提供更多保护
Leetcode652 finding duplicate subtrees
Description of large and small end mode
Summary of articles in 2020