当前位置:网站首页>How to encrypt your own program with dongle
How to encrypt your own program with dongle
2022-07-24 19:20:00 【senseshield】
Using dongle to encrypt and protect programs is a very mature encryption scheme . At present, encryption locks are common in the market : Thoughtful elite 5, Wei Bu ,safenet. The more established encryption lock companies in China are pondering , Thoughtful lock from elite 4, Up to now, the elite 5, Are relatively good products , High encryption security , Good experience , High cost performance , I recommend this one .
How to encrypt program flow with dongle
- Get encryption SDK package .
- Shell the program directly with the shell tool provided by the dongle .
- Use the control lock and write lock tools to make the matching user lock .
- Send the encrypted program and supporting user lock to the user .
Encryption lock authorization management
Elite 5 Series of encryption locks can realize software authorization management 、 Remote upgrade and other functions .
- Time and time limit function . Software is sold by subscription , When the subscription expires, the software license can be upgraded by remote upgrade .
- Network lock function . Realize a lock on the server in the LAN , Other computers under the same LAN can also use software .
- Limited function module . Limit the sales of different functional modules of the software .

The shelling tool encrypts the program flow
Directly transfer the program with encryption exe perhaps dll Drag directly into the shelling tool , Select the function to encrypt , At the same time, choose the protection mode .Virbox Protector There are four ways for shell tools to protect functions : Code virtualization / Code obfuscation / Code fragmentation / Code encryption .

Code fragmentation is the latest technology to reflect on independent intellectual property rights : be based on LLVM and ARM Virtual machine technology , Automatically extract massive code and move in SS Kernel mode module , It greatly reduces the use threshold , There is no need to manually migrate algorithms , Portable algorithms have grown from a limited number to almost unlimited , The supported languages are no longer limited to C, This is a comprehensive application of encryption technology , The effect is similar to breaking up the execution of the software , Let the cracker have no way to start . High security 、 It is recommended to call key functions or encryption lock methods ; Using too much will affect efficiency .
Code encryption , Take code blocks as data , Store with permissive encryption function , When the program executes this function, verify the license and solve The secret , The entire block of code is not exposed in memory .
Code virtualization : in the light of X86 Code : It refers to translating machine code into a string of pseudo code byte streams that are unrecognizable to both machines and people ; In the specific implementation, we will translate and explain these pseudo codes one by one , Gradually restore to the original code and execute . This subroutine used to translate pseudo code and be responsible for specific execution is called virtual machine VM( Like an abstract CPU). It exists as a function , The parameter of the function is the memory address of the bytecode . Due to virtual machine code and virtual machine CPU The implementation of can achieve random design and random execution every time And the code can change randomly every time , Including some logical equivalent changes, you can refer to the hardware N A NAND gate NOT-AND Realize various logic gates , Algorithm and changes in the form of accessing memory , Including non equivalent changes in Mathematics , The code volume can almost expand to 100 To 10000 times , The machine cannot restore the algorithm to the original logic . Code virtualization is characterized by : Medium safety 、 It doesn't affect efficiency .
边栏推荐
- Taokeeper environment setup
- matplotlib
- Detailed explanation of DHCP distribution address of routing / layer 3 switch [Huawei ENSP]
- SATA protocol OOB essay
- Hucang integrated release of full data value, sequoiadb V5.2 online conference heavy attack
- Techempower web framework performance test 21st round results release --asp Net core continue to move forward
- Jedi survive and eat chicken F12 screenshot save path reference
- Getaverse,走向Web3的远方桥梁
- Mysql数据库,去重,连接篇
- Nftscan and port3 have reached strategic cooperation in the field of NFT data
猜你喜欢

Literature reading: gopose 3D human pose estimation using WiFi

Tcl/tk file operation

Typora user manual
What are the benefits of knowledge management in enterprises?
【JVM学习04】JMM内存模型

Convolutional neural network CNN

Database index: index is not a panacea

OPENGL学习(二)OPENGL渲染管线
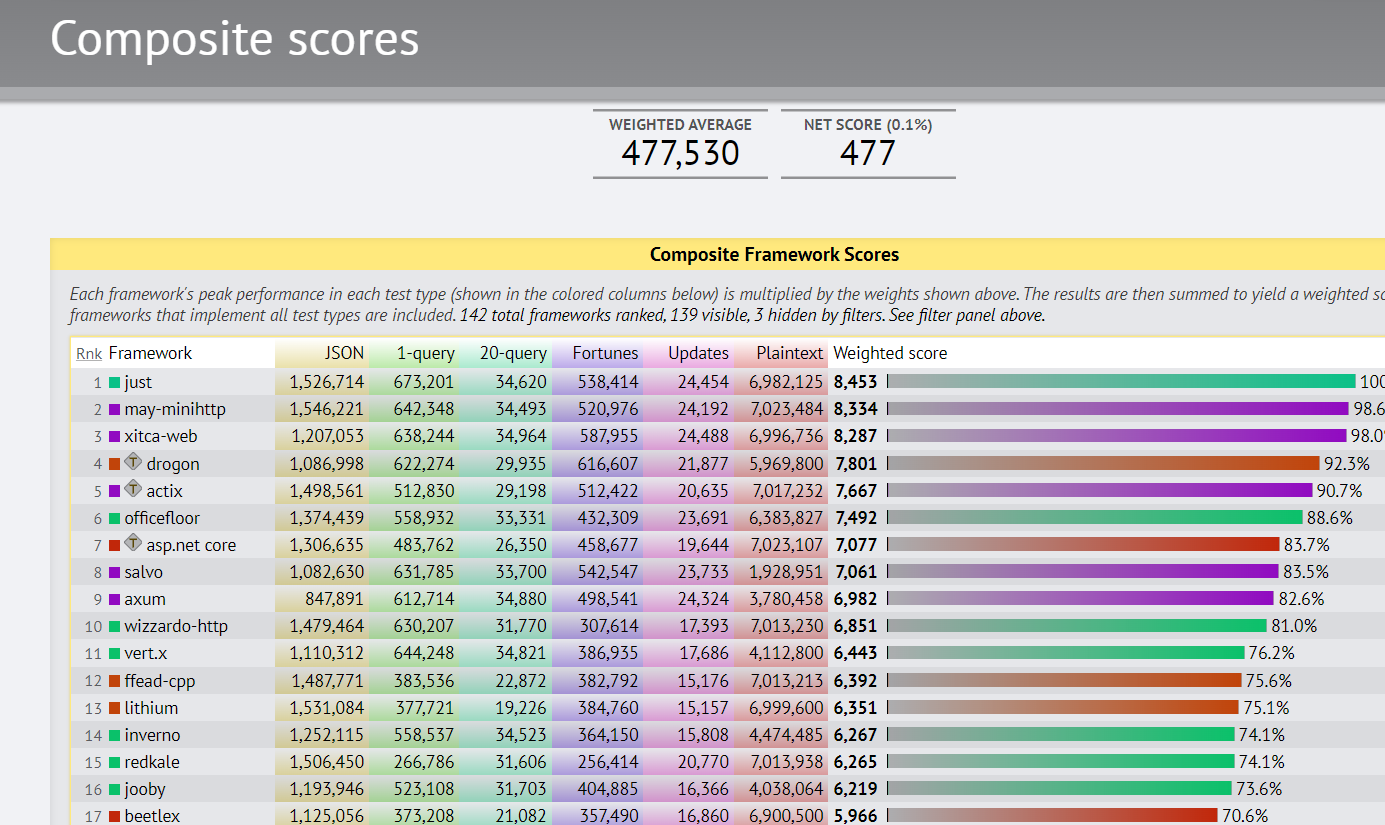
Techempower web framework performance test 21st round results release --asp Net core continue to move forward

Pay close attention! List of the latest agenda of 2022 open atom open source Summit
随机推荐
Siyuan notes V2.1.2 synchronization problem
原反补及大小端
Analysis of dropout principle in deep learning
FPGA 20 routines: 9. DDR3 memory particle initialization write and read through RS232 (Part 1)
2022暑期杭电多校第一场1012Alice and Bob(博弈论)
In the spring of domestic databases
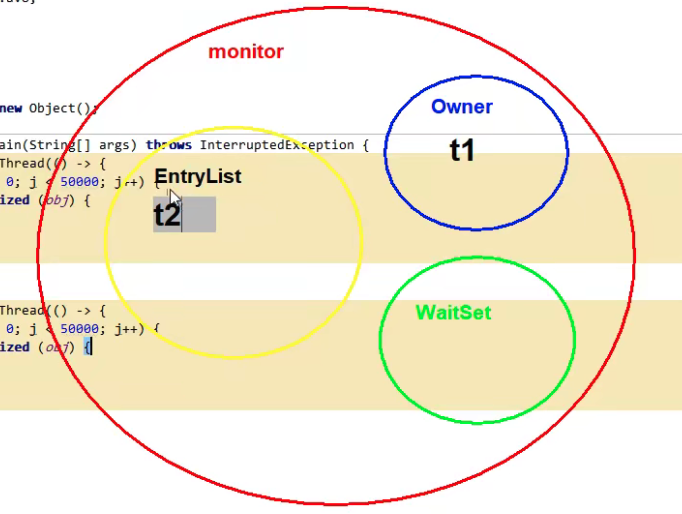
【JVM学习04】JMM内存模型
Summer Niuke multi school 1:i chiitoitsu (expectation DP, inverse yuan)
OPENGL学习(二)OPENGL渲染管线
Data model subclassing reference
Getaverse,走向Web3的远方桥梁
Solve the problem of disconnection due to long idle time after SSH login
MySQL1
Cyberpanel free open source panel - high speed lscache free SSL Certificate - self built DNS and enterprise post office
LTSpice software power settings
MySQL final chapter
Feature extraction tool transformer Bert
2022 Hangzhou Electric Multi school first Dragon Slayer (dfs+ state compression)
High speed ASIC packaging trends: integration, SKU and 25g+
He has been in charge of the British Society of engineering and technology for 13 years, and van nugget officially retired
