当前位置:网站首页>Find out the invisible assets -- use hosts collision to break through the boundary
Find out the invisible assets -- use hosts collision to break through the boundary
2022-06-24 16:08:00 【Bypass】
Sort out the assets from the perspective of the attacker , Use full port scanning + How subdomain names are collected , Identify all corporate asset exposures . But even so , It is often caused by incorrect configuration or untimely recycling , There are still some hidden assets .
01、 Business scenario
In general , Using a domain name to access a web site requires two steps , One is DNS Domain name resolution to server ip Address , The second is to bind the domain name to the server IP Address , Most of the time, we will forbid the passage IP Go directly to the website , Thus, malicious parsing and ip Scanning detection , Ensure that users can only access the business system through the correct domain name .
Take an enterprise deployment architecture as an example , Use Lvs+Nginx Build high availability web framework . In this mode , Just bind a public network ip, All service ports of the Intranet can pass through nginx The unique port of the agent is mapped to the external network environment .
Based on this enterprise deployment architecture , There are two typical vulnerability scenarios :
(1) Test environment or pre production environment , Clear the domain name resolution of the public network , however Nginx The configuration was not cleared in time , Bind correct host To access .
(2) For security reasons , Extranet Nginx And the Internet Nginx It is necessary to make a strict distinction , But there is no distinction between internal and external networks . Use the same Nginx Complete the configuration of Intranet and Internet services , Resolve to the public network through the public network domain name , Intranet DNS Resolve to intranet . This is the time , Bind correct host You can access the intranet system .
02、Hosts Collision Technology
Based on the above scenario , The domain name record cannot be found in the domain name resolution record , adopt IP Port can not access the website , Only to check nginx Configuration situation , Will discover the security problems that may be caused by improper configuration .
that , From the attacker's point of view , How to find these invisible assets ?
Here is a technology to share , It's called Hosts Collision Technology , By combining the domain name with IP Conduct binding collision , Once it matches the domain name binding configuration on the back-end proxy server , You can access the corresponding business system , To discover hidden assets .
Of course , In addition to being able to find hidden assets , We can also use this method to find the real business system IP, To bypass the cloud WAF Safety protection of .
03、 Automated scanning tools
hostscan: automation Host Collision tool
https://github.com/cckuailong/hostscanHosts_scan: be used for IP And domain name collision match access python Script
https://github.com/fofapro/Hosts_scan边栏推荐
- 2021-04-24: handwriting Code: topology sorting.
- 【应用推荐】最近大火的Apifox & Apipost 上手体验与选型建议
- Most common usage of vim editor
- Istio FAQ: region awareness does not take effect
- HMM to CRF understanding and learning notes
- C. Three displays codeforces round 485 (Div. 2)
- [application recommendation] the hands-on experience and model selection suggestions of apifox & apipost in the recent fire
- Two problems of qtreewidget returning as DLL in singleton mode
- April 23, 2021: there are n cities in the TSP problem, and there is a distance between any two cities
- 实现领域驱动设计 - 使用ABP框架 - 领域逻辑 & 应用逻辑
猜你喜欢

MySQL binlog

60 个神级 VS Code 插件!!

构建Go命令行程序工具链
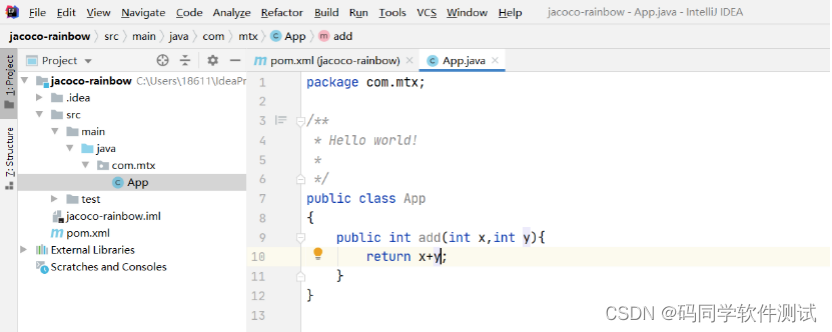
Still worried about missing measurements? Let's use Jacobo to calculate the code coverage
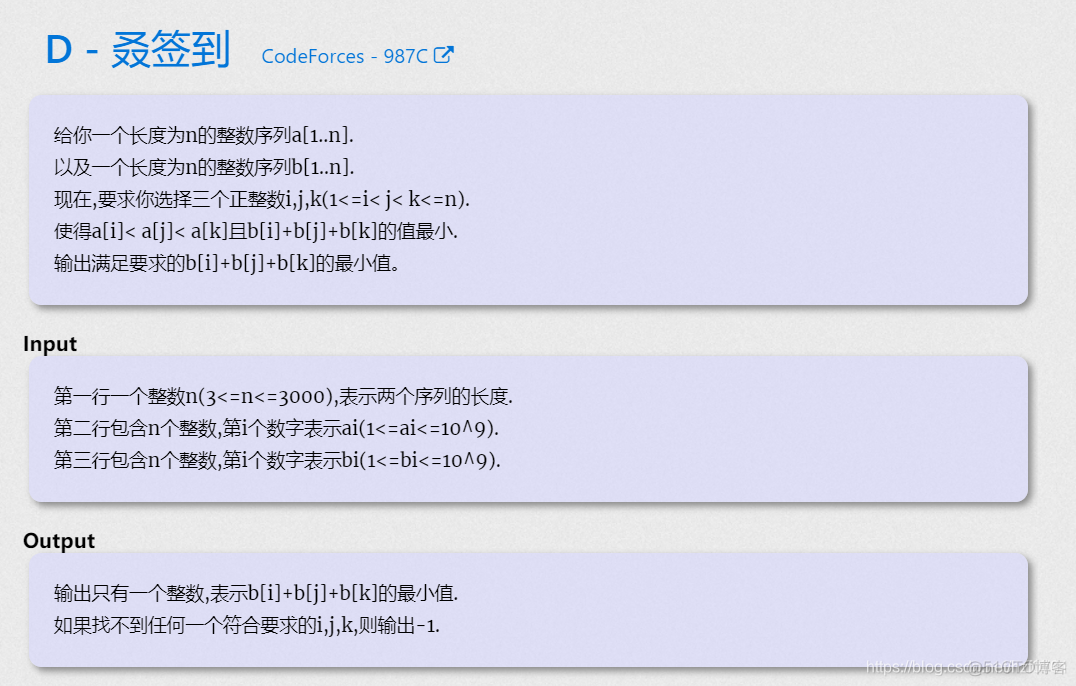
C. Three displays codeforces round 485 (Div. 2)

实现领域驱动设计 - 使用ABP框架 - 领域逻辑 & 应用逻辑

The catch-up of domestic chips has scared Qualcomm, the leader of mobile phone chips in the United States, and made moves to cope with the competition
nifi从入门到实战(保姆级教程)——环境篇

用 Oasis 开发一个跳一跳(一)—— 场景搭建
MySQL Advanced Series: locks - locks in InnoDB
随机推荐
Install the imagemagick7.1 library and the imageick extension for PHP
Logging is not as simple as you think
Easy installation of Jenkins
How to implement SQLSERVER database migration in container
Why is it easy for enterprises to fail in implementing WMS warehouse management system
How does the effective date of SAP PP ECM affect the work order?
Ascinema with asciicast2gif for efficient command line terminal recording
[cloud native | kubernetes chapter] Introduction to kubernetes Foundation (III)
leetcode 139. Word Break 單詞拆分(中等)
Siggraph 2022 | truly restore the hand muscles. This time, the digital human hands have bones, muscles and skin
Nature刊登量子计算重大进展:有史以来第一个量子集成电路实现
MySQL Advanced Series: locks - locks in InnoDB
How to open a futures account safely? Which futures companies are more reliable?
Detailed explanation of estab of Stata regression table output
用 Oasis 开发一个跳一跳(一)—— 场景搭建
The decline of China's product managers: starting from the nostalgia for jobs
2021-05-02: given the path of a file directory, write a function
MySQL InnoDB and MyISAM
Efficient tools commonly used by individuals
期货怎么开户安全些?哪些期货公司靠谱些?
