当前位置:网站首页>Most common usage of vim editor
Most common usage of vim editor
2022-06-24 15:38:00 【Exclusive rainy days】
Vim There is 3 Mode used in : this 3 The switching between the two modes can be illustrated by the following figure
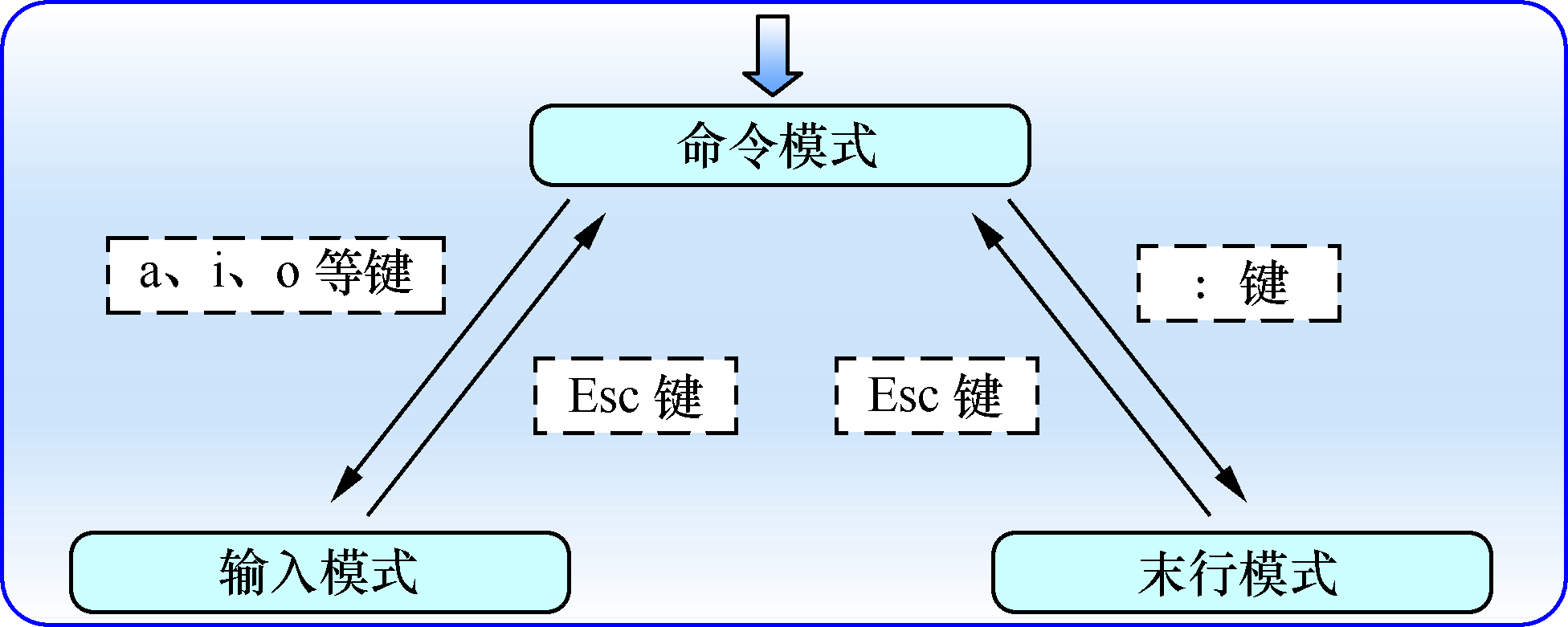
Command mode
In the use of Vim When ordered , Enter command mode by default . Command mode is usually , Do some Whole row operation . The main commands are as follows :
| command | effect |
|---|---|
| dd | Delete ( shear ) The cursor is in the whole line |
| 5dd | Delete ( shear ) Starting at the cursor 5 That's ok |
| yy | Copy the whole line where the cursor is |
| 5yy | Copy from cursor 5 That's ok |
| n | Displays the next string to which the search command navigates |
| N | Display the last string to which the search command is located |
| u | Undo the last action |
| p | Delete the previous (dd) Or copy (yy) Paste the data after the cursor |
Also commonly used is , Use G You can jump directly to the last line ,gg You can go to the first line .
Input ( edit ) Pattern
Mainly 3 Input methods :
- a(append Additional meaning ) Indicates that a bit is inserted after the current mouse
- i (Insert Meaning of insertion ) Indicates to insert... At the current position of the current mouse
- o( Another line means ) Indicates that the mouse is on the line , Insert... In the next line
Last row mode
It is mainly used for preservation or sign out file , And settings Vim Editor working environment , It also allows users to execute external Linux Command or jump to a specific number of lines in the document being written .
The most common command :
:wqSave and exit:qExit without saving ,:q!Forced exit , Discard all saves
| command | effect |
|---|---|
| :set nu | According to the line Numbers |
| :set nonu | Don't show line numbers |
| : command | Execute the command |
| : Integers | Jump to the line |
| /one/two | Move the current cursor The first one in the line one Replace with two |
| /one/two/g | Move the current cursor All in the line one Replace with two |
| :%s/one/two/g | take All in the full text one Replace with two |
| ? character string | Search the string from bottom to top in the text |
| / character string | Search the string from top to bottom in the text |
If you want to see , In all the documents , Can pass vim Order reenter , perhaps cat Output file content .
边栏推荐
- Phpcms upgrade editor method -- simple and effective
- Arrays API
- VIM common shortcut keys
- Bitmap of redis data structure
- [parameter configuration tutorial] how should the parameters in the RTMP streaming camera be configured?
- How to resolve the 35 year old crisis? Sharing of 20 years' technical experience of chief architect of Huawei cloud database
- 如何扩展aws主机上的磁盘空间
- Mongodb Getting started Practical Tutoriel: Learning Summary Table des matières
- Design of vga/lcd display controller system based on FPGA (Part 2)
- Why is the blackmail virus that shut down half of America's energy system terrible? Interpretation of authoritative reports
猜你喜欢

为什么企业实施WMS仓储管理系统很容易失败

MongoDB入门实战教程:学习总结目录
Record the range of data that MySQL update will lock

设备通过国标GB28181接入EasyCVR平台,出现断流情况该如何解决?

推荐几款超级实用的数据分析利器
Redis consistency hash and hash slot

国产最长寿的热销手机,苹果也不是对手,总算让国产手机找回面子
Wide measuring range of jishili electrometer

Do you really know the difference between H5 and applet?

FreeRTOS新建任务不执行问题解决办法
随机推荐
【Prometheus】5. Alertmanager alarm (incomplete)
Remember: never use UTF-8 in MySQL
Data stack technology sharing: how to use data stack for data collection?
How to achieve long-term development of voice social source code?
Bitmap of redis data structure
How to build a high-performance go cache Library
Easynvr has been connected to the third-party supervision platform. How to achieve local Internet access
10 hands-free idea plug-ins. These codes do not need to be written (the second bullet)
Junit5中的参数化测试(Parameterized Tests)指南
手机同花顺股票开户安全吗!
Special topic of IM code scanning login Technology (III): easy to understand. A detailed principle of IM code scanning login function is enough
Decomposition of Uber dependency injection into dig source code analysis
Step by step introduction to sqlsugar based development framework (9) -- Realizing field permission control with WinForm control
leetcode 139. Word Break 单词拆分(中等)
PHP application container deployment practice
In 2021, big companies often ask IOS interview questions -- runloop
PHP export data as excel table
Firefox browser uses plug-ins to set up proxy
Binary computing
HMM to CRF understanding and learning notes

