当前位置:网站首页>Why is the blackmail virus that shut down half of America's energy system terrible? Interpretation of authoritative reports
Why is the blackmail virus that shut down half of America's energy system terrible? Interpretation of authoritative reports
2022-06-24 15:34:00 【Tencent security】
The largest product pipeline operator in the United States Colonial Pipeline At local time 5 month 7 Was attacked by blackmail software on the th , Forced to shut down its key fuel network supplying oil to the eastern coastal states of the United States .
Colonial Of 5500 Miles of pipelines carry fuel from refineries along the Gulf coast to customers in the southern and eastern United States , It was transported 45% East Coast fuel , covers 5000 Ten thousand Americans .
distance 2017 year 5 month 12 Japanese extortion virus WannaCry The first outbreak has passed 4 Years. , A lot of people were impressed by the “ one 's sabre-rattling is getting louder and the smell of gunpowder thicker ” Still fresh in my memory , But this is just the beginning , The next few years , Blackmail virus has increasingly become a tried and true means of attack , And more and more varieties have been developed , Only in the last few months , foxconn 、 Acer 、 Kia and other well-known enterprises are still receiving extortion virus attacks , The ransom has set new records again and again .
This time, Colonial Pipeline event , The blackmail virus directly damaged a national energy system , The harm is evident .
Extortion virus is still almost unsolved , It's almost impossible to decrypt once you get caught , Fortunately, some technical means can also be used to enhance the immunity to extortion virus . Tencent security united with Southern Metropolis Daily to summarize the attack methods of blackmail virus 、 Attack the target 、 Attack path 、 Prevention methods and other information , Compiled 《2021 Blackmail virus trend report and protection scheme suggestions in the first half of the year 》, For institutions and enterprises to extort virus “ Enemy and know yourself ”, Try to avoid being attacked .
meanwhile , Tencent Security Alliance Nanfang Metropolis Daily 、 Watch the snow forum , Invite three senior safety experts , They were in Windows System kernel security 、 Years of experience in the field of anti-virus and Threat Intelligence , Decrypt all aspects of blackmail virus for you .
Sweep yards attention Tencent security video Number
Or direct video number search “ Tencent security ”
Follow and make an appointment for live broadcast
5 month 11 On Tuesday night 19:00
Be there or be square
边栏推荐
- 股票开户要找谁?在线开户安全么?
- Very exciting! 12000 words summarized the theory of network technology, reviewing the old and learning the new
- Logstash introduction and simple case
- Kubernetes practical tips: using ksniff to capture packets
- Bert whitening vector dimension reduction and its application
- Record the range of data that MySQL update will lock
- Tencent cloud native intelligent data Lake Conference will be held, revealing the panoramic matrix of Tencent cloud data Lake products for the first time
- 刚刚阿里面软件测试回来,3+1面任职阿里P7,年薪28*15薪
- Network engineers must know the network essence knowledge!
- Method after charging the idea plug-in material theme UI
猜你喜欢

From pair to unordered_ Map, theory +leetcode topic practice
Brief discussion on the implementation framework of enterprise power Bi CI /cd

A common defect management tool - Zen, which teaches you from installation to using the handle

How to generate assembly code using clang in Intel syntax- How to generate assembly code with clang in Intel syntax?
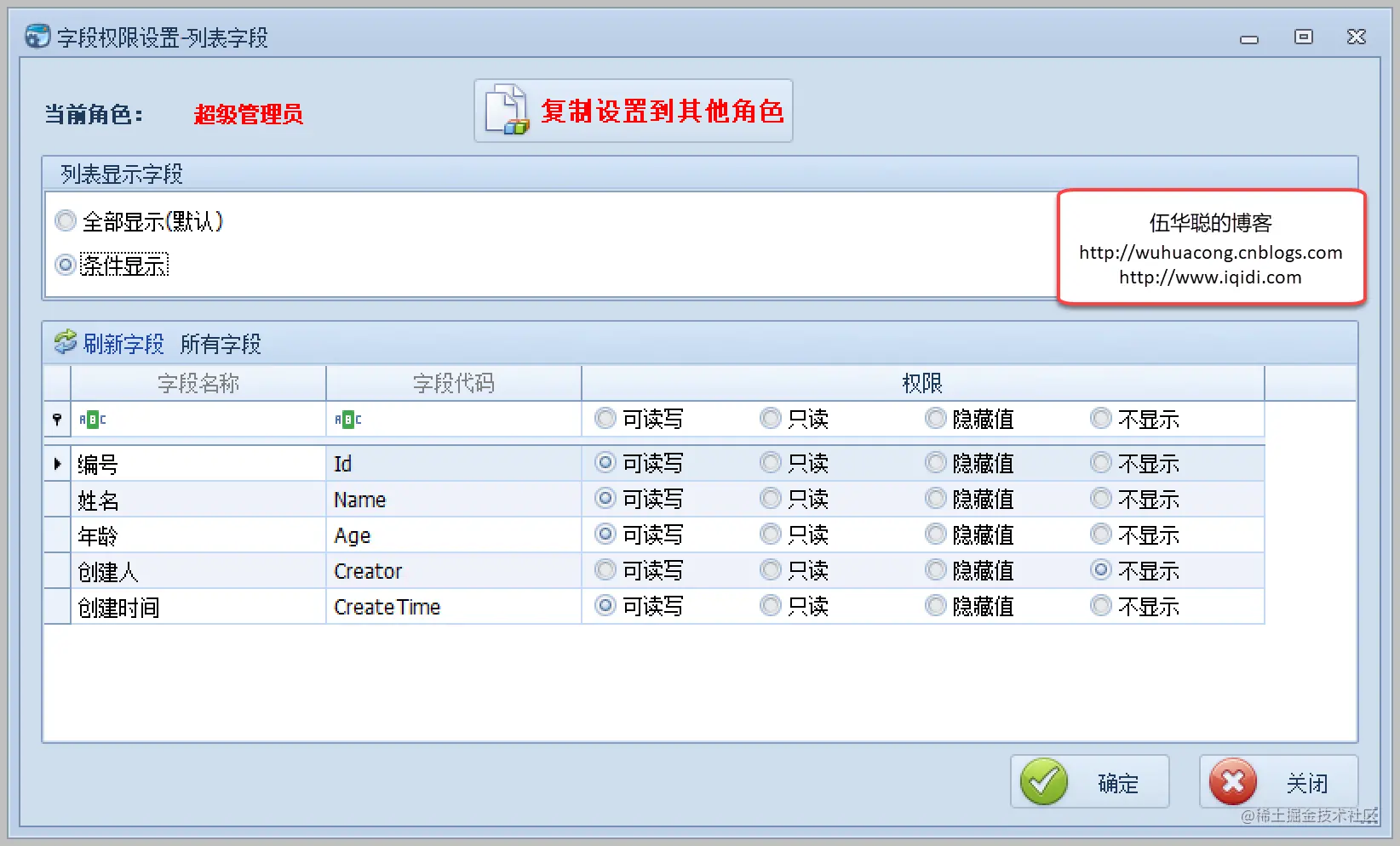
Step by step introduction to sqlsugar based development framework (9) -- Realizing field permission control with WinForm control

Bert whitening vector dimension reduction and its application

熬夜整理出的软件测试【高频】面试题大全(2022最新)

Left hand code, right hand open source, part of the open source road

Mots clés pour la cartographie es; Ajouter une requête par mot - clé à la requête term; Changer le type de mot - clé de cartographie

ES mapping之keyword;term查詢添加keyword查詢;更改mapping keyword類型
随机推荐
Task priority motion planning of floating base
【Kubernetes】1
Analysis of dompurify
Differential privacy
The security market has entered a trillion era, and the security B2B online mall system has been accurately connected to deepen the enterprise development path
Design of CAN bus controller based on FPGA (Part 2)
Stm32f1 and stm32cubeide programming examples -ws2812b full color LED driver (based on spi+dma)
Multimeter resistance measurement diagram and precautions
How do individuals open accounts for stock speculation? Is it safe to open accounts for stock speculation
"Industry outlook" analysis of five major trends in China's security video surveillance industry
update+catroot+c000021a+critical service failed+drivers+intelide+viaide+000000f
Step by step introduction to sqlsugar based development framework (9) -- Realizing field permission control with WinForm control
一个简单而功能强大的开发者工具箱Box3.cc
Service visibility and observability
Istio FAQ: 431 request header fields too large
Data sharing between laravel lower views
Redis consistency hash and hash slot
Sequential representation and implementation of linear table (refer to YanWeiMin version)
Attacked! Cloud development monitoring alarm practice
安防市场进入万亿时代,安防B2B网上商城系统精准对接深化企业发展路径