当前位置:网站首页>Research Notes (8) Deep Learning and Its Application in WiFi Human Perception (Part 2)
Research Notes (8) Deep Learning and Its Application in WiFi Human Perception (Part 2)
2022-08-02 05:22:00 【CS research GO】
论文题目:Deep Learning and Its Applications to WiFi Human Sensing: A Benchmark and A Tutorial
论文作者:Jianfei Yang, Xinyan Chen, Dazhuo Wang, Han Zou, Chris Xiaoxuan Lu, Sumei Sun, Fellow, IEEE and Lihua Xie, Fellow, IEEE
工作单位:新加坡南洋理工大学,University of Edinburgh, UK, etc
发表刊物:arxiv, pp. 1-17,2022
II. PRELIMINARIES OF WIFI SENSING
A. CSI简介
在WiFi通信中,CSI(信道状态信息)It reflects the diffraction of the wireless signal、Propagation in the physical environment after reflection and scattering,The channel characteristics of the communication link are described.For a pair of transmitter and receiver antennas,CSIMultipath phase shift and amplitude attenuation on each subcarrier are described.与RSS(接收信号强度)相比,CSIThe data has better sensing resolution,在WiFiIt can be regarded as the environment in which the signal propagates“WiFi图像”.在WiFi感知中,CSIThe recording function is provided by a dedicated tool[1]、[2]实现.CSIThe estimate can be expressed as :
H i = ∥ H i ∥ e j ∠ H i H_i=\parallel H_i \parallel e^{j\angle H_i} Hi=∥Hi∥ej∠Hi
其中 ∥ H i ∥ \parallel H_i \parallel ∥Hi∥和 ∠ H i \angle H_i ∠Hi分别代表第 i i iThe magnitude and phase of the subcarriers.
B. CSI工具
| CSI工具 | 带宽 | 子载波数量 | 设备 |
|---|---|---|---|
| Intel 5300 CSI Tool | 20MHz | 30 | Intel 5300 NIC |
| Atheros CSI Tool | 20/40MHz | 56/114 | Atheros NIC |
| Nexmon CSI Tool | 80MHz | 256 | 智能手机&树莓派 |
C. CSIData transformation and cleaning
- Q:如何处理CSIData makes it applicableWiFi感知?
- A1:只使用CSIAmplitude data as input.
- A2:在基于模型的方法中,between the antennasCSIPhase difference as input.
- A3: Use processedCSIDoppler said,例如,提出BVP(Human coordinate velocity profile)to simulate the Doppler features that reflect human motion[31].
D.CSIThe impact of data on the human body
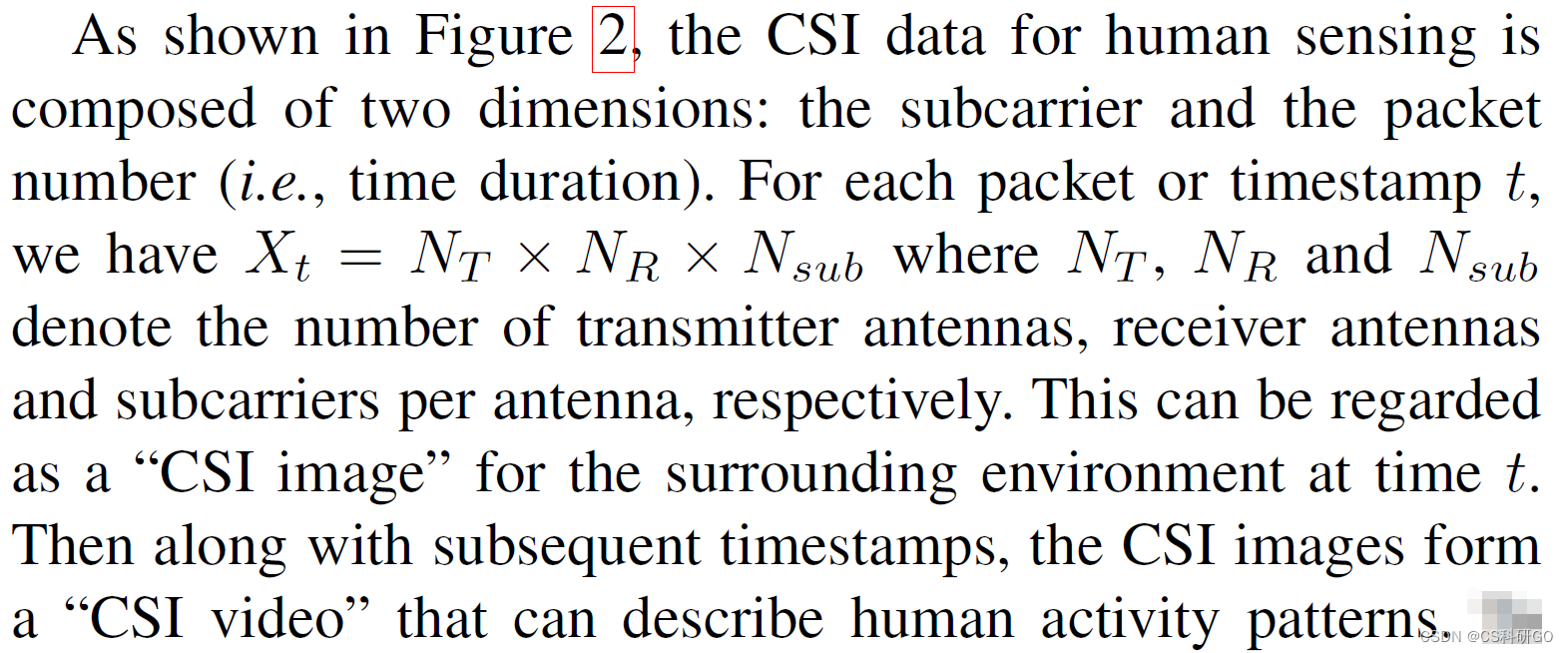
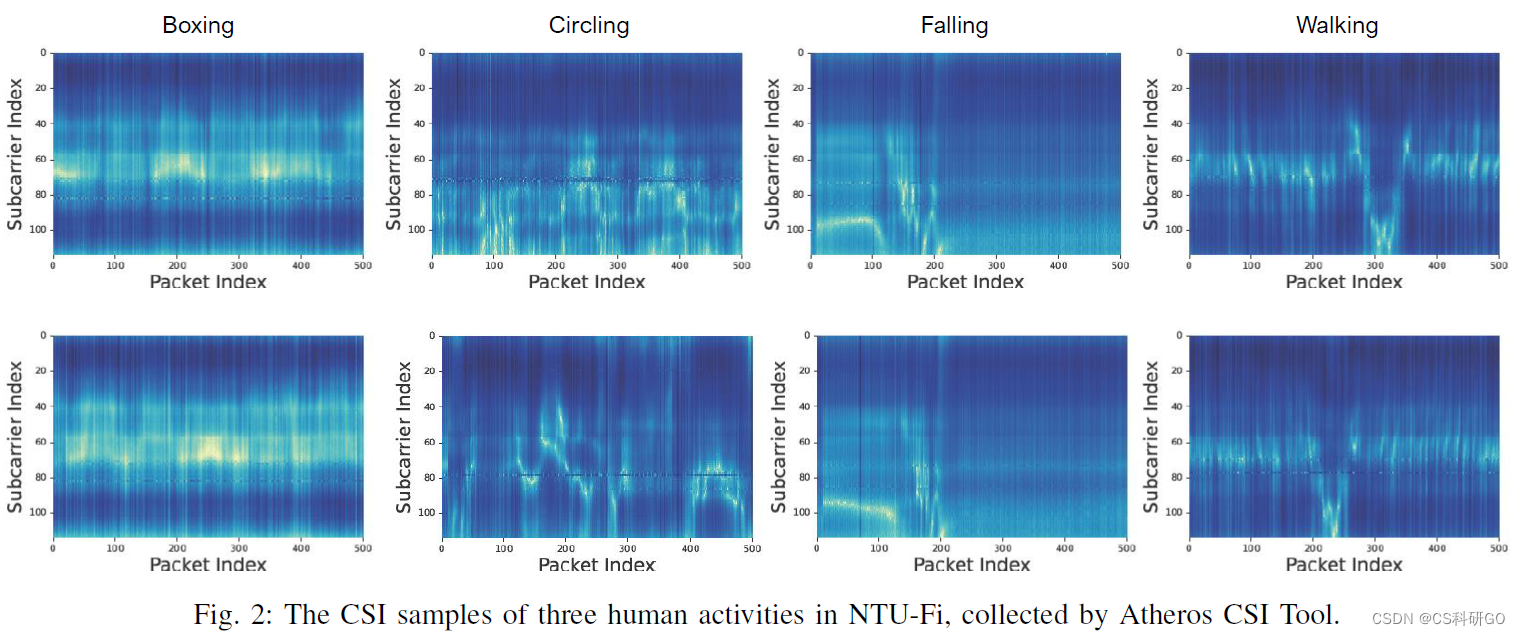
为了将CSIData is combined with deep learning models,This article summarizes what contributes to a better understanding of deep model designCSI数据属性:
- Subcarrier dimension—空间特征
- 时间维度(consecutive packets)----时间特征
- Antenna Dimensions—Resolution and channel characteristics
III. DEEP LEARNING MODELS FOR WIFI SENSING
A.用于WiFiPerceptual deep learning models(2017-2022)

B.WiFiFundamentals of commonly used deep learning models in the field of perception
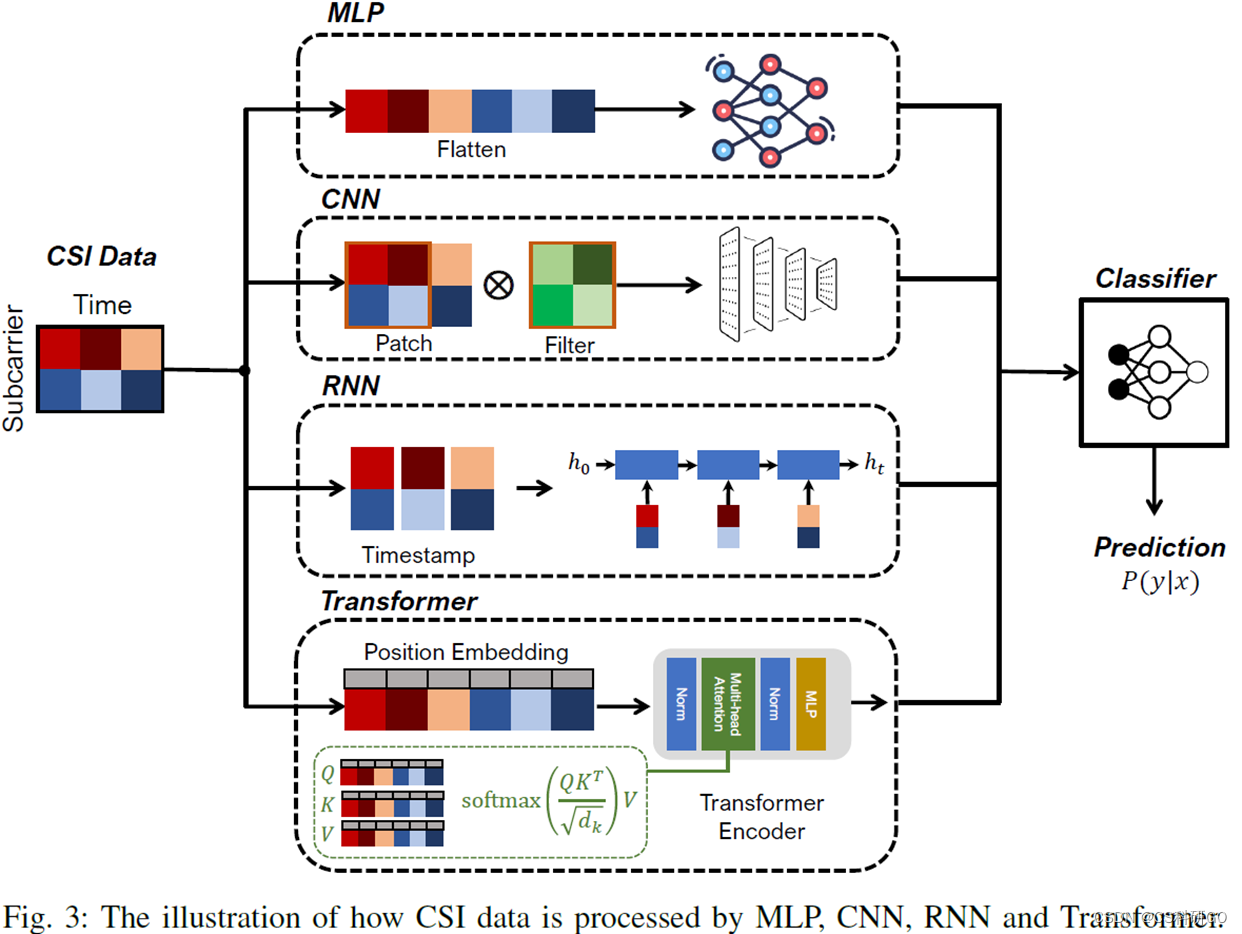
C.WiFiEvaluation of commonly used deep learning models in the field of perception
- MLP:参数多,收敛速度慢,计算开销大;
- CNN:卷积层过多(>20),The vanishing gradient problem leads to performance degradation;
- RNN:There is a vanishing gradient problem when backpropagating,无法捕获CSI的长期依赖关系;
- LSTM:克服了Vanilla RNN存在的问题;
- Transformer:参数多,训练成本高,And it is difficult to collect a large number of labeled onesCSI数据.
IV. LEARNING METHODS FOR DEEP WIFI SENSING MODELS
- 监督学习:Traditional deep model training relies on supervised learning with large amounts of labeled data,But data collection and labeling is a realityWiFiPerceive application bottlenecks.
- 少样本学习:Since only a small number of samples are required,因此在实际应用中,Few-shot learning helps based on WiFigesture recognition and human body recognition.
- 迁移学习:在WiFiperceive the scene,由于CSIData is highly dependent on the environment,Therefore, cross-domain scenarios are very common.Transfer learning is used to solve cross-domain problems.
- 无监督学习:The model can be strengthened,获得更好的泛化能力.
- 集成学习:Can improve model classification performance,But the computational overhead also grows exponentially.

V. EMPIRICAL STUDIES OF DEEP LEARNING IN WIFI SENSING: A BENCHMARK
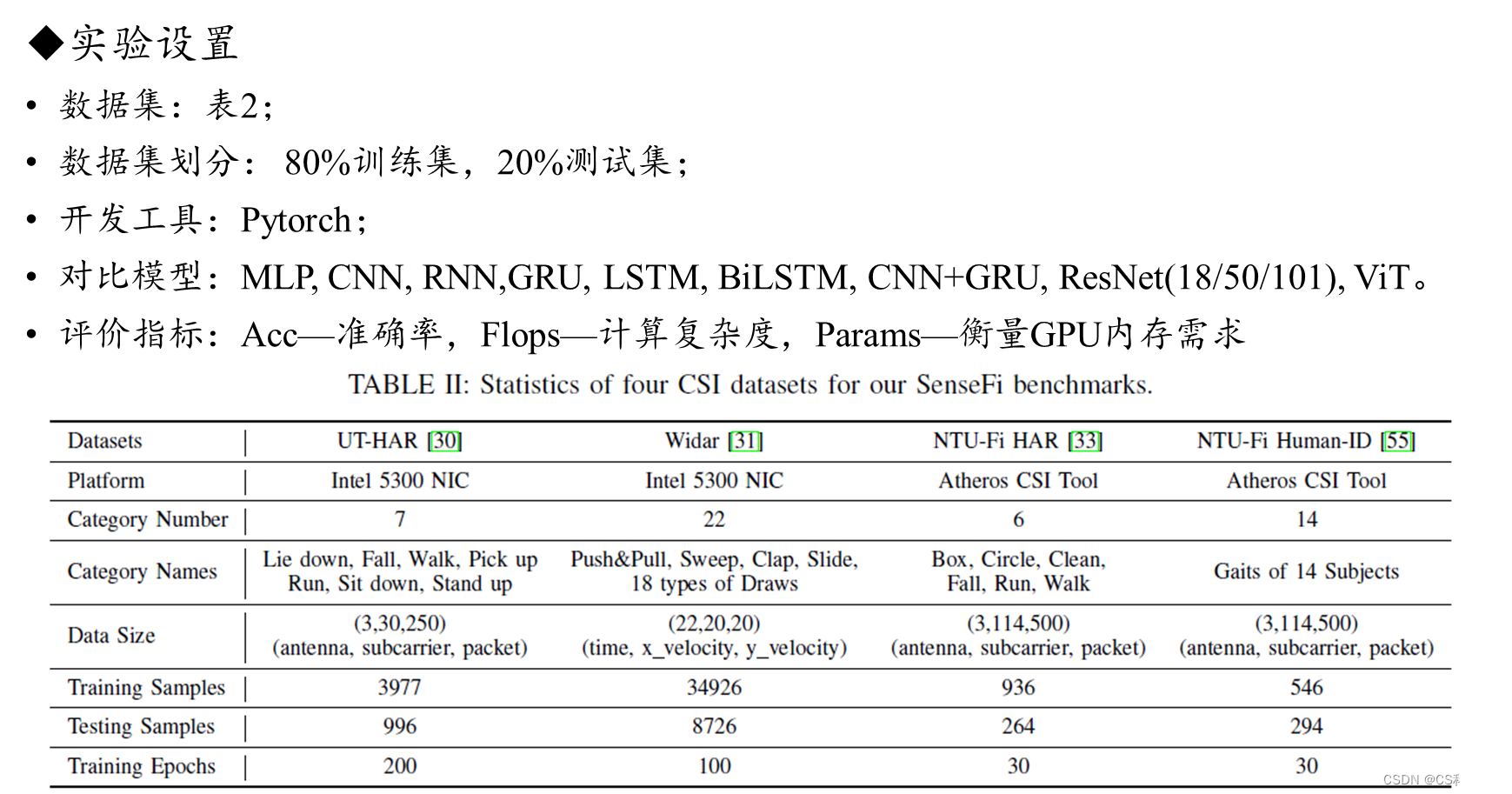
A. 实验设置
B. Deep Model Evaluation

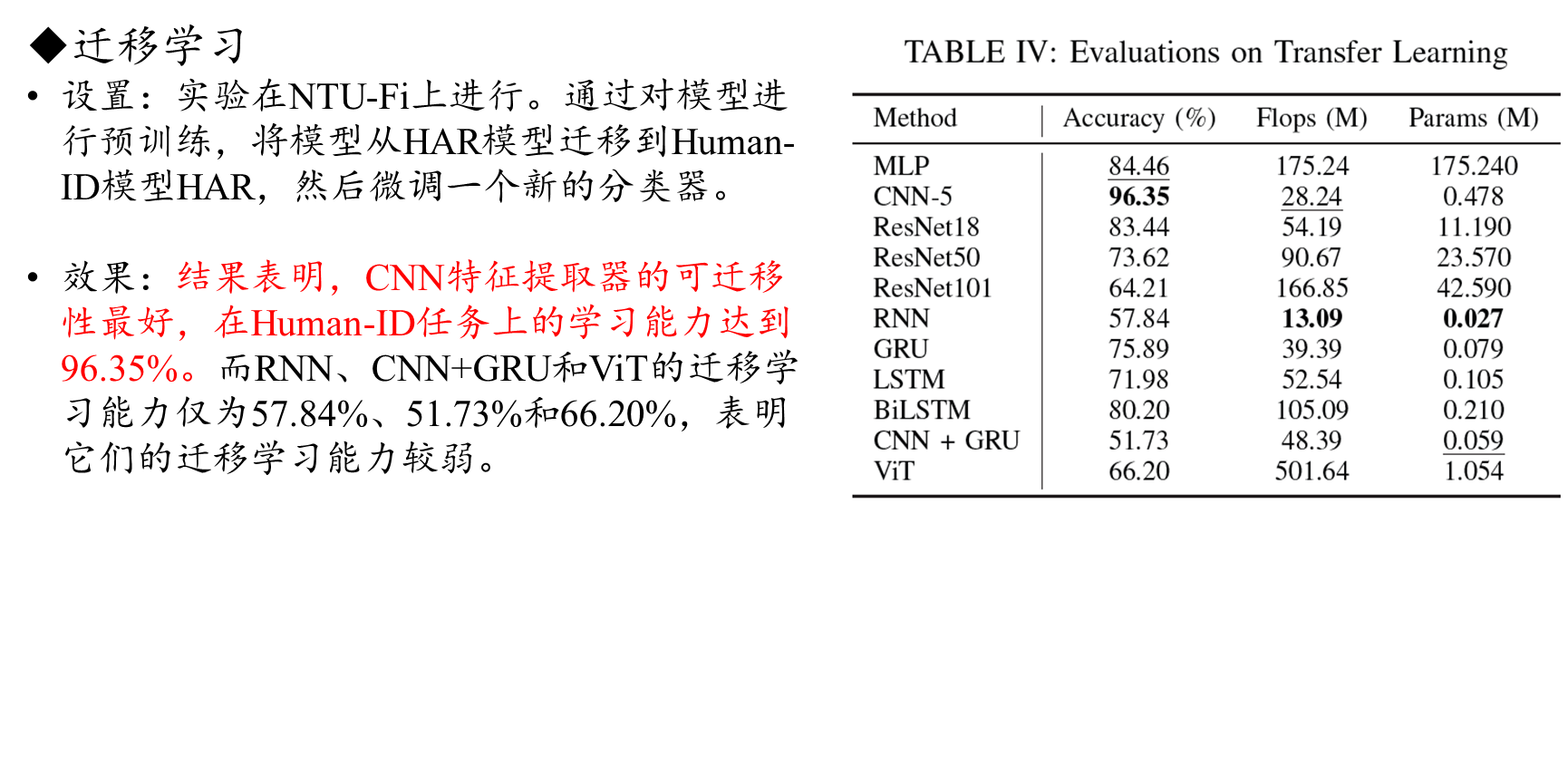
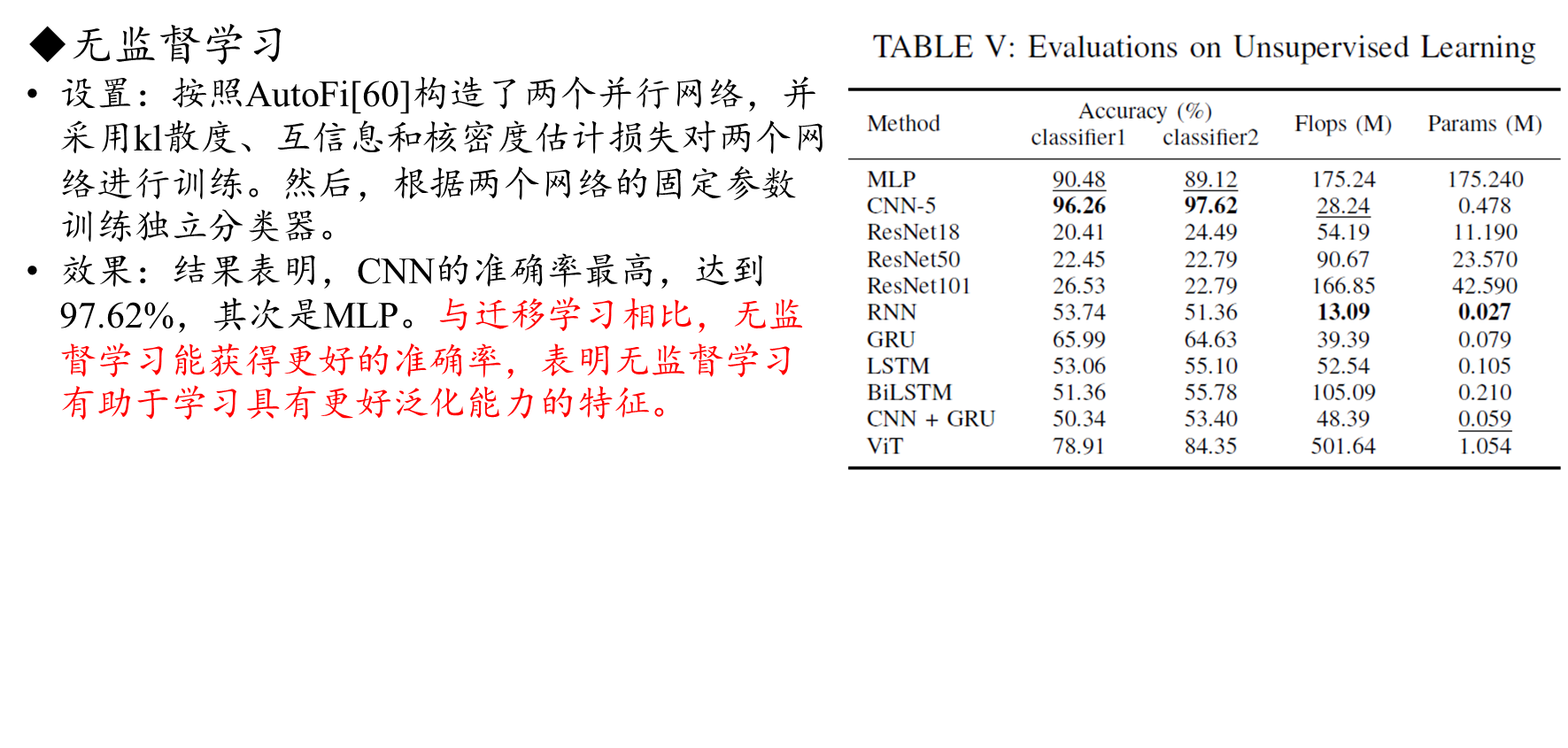
C. Learning strategy assessment
VI. DISCUSSIONS AND SUMMARY


PS:Since the paper was published in axvir上的,There are inevitably some omissions in the text.比如图2The three human activities mentioned in the subheading,The actual image involves four activities,And the image source of the upper and lower lines is not given a detailed introduction.
边栏推荐
- BCS演讲实录 | 未来智安CTO陈毓端精讲《XDR扩展威胁检测响应探索与实践》
- Your device is corrupt. It cant‘t be trusted and may not work propely.
- PHP5.6安装ssh2扩展用与执行远程命令
- jmeter之数据库连接JDBC安装与使用
- Win8.1下QT4.8集成开发环境的搭建
- 企业级的dns服务器的搭建
- 《2022年中国网络安全市场全景图》
- VisibleDeprecationWarning: Creating an ndarray from ragged nested sequences (which is a list-or-tupl
- ES6中变量的使用及结构赋值
- Transfer of UKlog.dat and QQ, WeChat files
猜你喜欢
随机推荐
想低成本保障软件安全?5大安全任务值得考虑
4个不可不知的“安全左移”的理由
flasgger手写phpwind接口文档
arr的扩展方法、数组的遍历及其他方法
未来智安入围《2022年中国数字安全百强报告》,威胁检测与响应领域唯一XDR厂商
Liunx服务环境部署
h264转flv
3个最佳实践助力企业改善供应链安全
字典基本操作方法
ftp服务的部署和优化
MongoDB相关记录
The CCF brush topic tour - the first topic
MySQL5.7的安装编译及报错的解决方法
STM32/TMS320F2812+W5500硬软件调试总结
[Win11] PowerShell无法激活Conda虚拟环境
深蓝学院-手写VIO作业-第一章
怎样写测试用例?
Your device is corrupt. It cant‘t be trusted and may not work propely.
其他语法和模块的导出导入
深蓝学院-视觉SLAM十四讲-第七章作业