CIH Viruses
Alias Win95.CIHSpacefillerWin32.CIH PE_CIH etc. , It's a file virus , Use for Windows Of VxD Technical establishment , The main infection is Windows 95/98 The executable under , And in DOS、Windows3.2 And Windows NT Invalid in . Precisely because CIH The virus uniquely uses VxD technology , It makes this virus in Windows Spread in the environment , In fact, both timeliness and concealment are very strong , It's hard to detect the spread of this virus in the system with general anti-virus software .

Red code
“ Red code ” It's a worm virus , Be able to spread through the Internet .2001 year 7 month 13 Japan , The red code spread from web servers . It is a special attack against the network server running Microsoft Internet information service software .“ Red code ” It's also called Bady, The designer deliberately did the most damage . After being infected with it , Such information will be displayed on the network site controlled by the attacked host :“ Hello ! welcome http://wenwen.soso.com/z/UrlAlertPage.e?sp=Swww.worm.com!”. And then , The virus will take the initiative to find other vulnerable hosts for infection . This behavior lasts about 20 God , And then it's about specific IP Address initiates a denial of service attack . In less than a week , This virus has infected nearly 40 10000 servers , It is estimated that as many as 100 Ten thousand computers are infected .
SQL Slammer
SQL Slammer Also known as “ sapphire ”,2003 year 1 month 25 For the first time . It's an extraordinary worm , It has an obvious negative impact on Internet traffic . It doesn't target end computer users , It's the server . It's a single bag 、 The length is 376 Byte worm , It randomly produces IP Address , And to these IP Address sends itself . If a IP The address happens to be a Microsoft operating without patching SQL Server desktop engine software computer , It will quickly start to move towards random IP The host of the address emits a virus . It is the use of this remarkable effect of communication ,SQL
Slammer In ten minutes, I got infected 7.5 Ten thousand computers . The huge amount of data traffic makes the global router overburdened , And they were shut down one by one .
Shockwave
For businesses that rely on computers to run ,2003 It was a hard time in the summer . A wave is not flat , Wave after wave .IT During this period, the “ Shockwave ” and “ Tyrannosaurus Rex ” The double whammy of worms .“ Shockwave ” Attack first . The virus dates back to that year 8 month 11 It was detected and spread rapidly , The attack peaked in two days . Viruses spread through network connections and network traffic , Take advantage of Windows
2000/XP Attack one of the weaknesses of , After being activated , It shows computer users a malicious dialog box , The prompt system will shut down . This information is hidden in the executable file of the virus :“ mulberry , I just want to say I love you !” as well as “ bill ? gates , Why do you let this happen ? Stop making money , Fix your software !”
The virus also contains the possibility of 4 month 15 Daily direction Windows Upgrade the website to launch distributed DoS Attack code . But then ,“ Shockwave ” The damage is past its peak , It's basically under control .
Tyrannosaurus Rex
“ Shockwave ” Let's go ,“ Tyrannosaurus Rex ” Worms follow , For business and home computer users ,2003 year 8 It's a miserable month . The most destructive variant is Sobig.F, it 8 month 19 Day began to spread rapidly , In the initial 24 Within hours , It replicates itself 100 Ten thousand times , Set a historical record ( Was later Mydoom The virus breaks ). The virus is disguised as a harmless email attachment with a file name . After being activated , The worm then propagates itself to the e-mail address found in the user's local file type . The end result is a surge in Internet traffic .
Bagle
Bagle It's a classic and complex worm ,2004 year 1 month 18 First appearance on Sunday . This malicious code takes the traditional mechanism —— Email attachments infect the user system , Then go through the windows file , Find an email address to send to copy yourself .

Bagle And its 60~100 The real danger of a variety is , After the worm infected a computer , It's in it TCP Port opens a back door , Remote users and applications use this backdoor to get data on the infected system ( Any data, including financial and personal information ) Access right .Bagle.B Variants are designed to be in 2004 year 1 month 28 And then stop spreading , But so far there are plenty of other variants that continue to plague users
MyDoom
2004 year 1 month 26 A few hours a day ,MyDoom E-mail has spread on the Internet at an unprecedented rate , In an instant, the shock wave can be felt all over the world . It also has a name called Norvarg, It spreads itself in a very circuitous way : It disguises itself as a message containing an error message “ Mail processing failed ”、 It looks like an email error message, an attachment to the email , Click on this attachment , It's propagated to other addresses in the address book .MyDoom And tried to pass P2P Software Kazaa The shared folder of the user's network account to propagate .
The replication process was quite successful , Computer security experts estimate that , In the first hour of infection , One out of every ten emails carries a virus .MyDoom The virus program itself is designed to 2004 year 2 month 12 Stop spreading in the future .
Shockwave (Sasser)
“ Shockwave ” since 2004 year 8 month 30 It's starting to spread , It was so destructive that some French news agencies had to shut down satellite communications . It also led to Delta Airlines (Delta) Several flights have been cancelled , Many companies around the world have had to shut down their systems .“ Shockwave ” It's not spread by email , It doesn't require user interaction .“ Shockwave ” The virus takes advantage of non upgraded Windows
2000/XP A security vulnerability in the system . Once successfully copied , Worms actively scan other unprotected systems and spread themselves there . There's going to be constant infection and disruption of the system .
“ Shockwave ” It was written by a German high school student , He was in 18 The virus was released on your birthday . Because he was a minor at the time of writing this code , A German court found him engaged in computer sabotage , Only a suspended sentence .

The millennium bug
Computer 2000 In the problem , Also known as “2000 Virus of the year ”、“ The millennium bug ”、“ The computer millennium bug problem ” or “ Millennium virus ”. Abbreviation for “Y2K”. An intelligent system in which a computer program is used ( Including computer systems 、 Automatic control chip, etc ) in , Because the years are represented by only two decimal digits , So when the system goes ( Or involved ) Cross century date processing operation ( Such as the calculation or comparison between multiple dates ), You get the wrong result , And then lead to a variety of system dysfunction or even collapse .
Panda burning incense
Panda burning incense is a kind of malignant computer virus , It's different from the grey pigeon , It's a variety of “ worm-type virus ” variant ,2006 year 10 month 16 Day by 25 Li Jun, a native of Xinzhou District, Wuhan, Hubei Province, China , It has the function of infection transmission ,2007 year 1 At the beginning of the month , It's mainly transmitted through downloaded files , The infected machine files are carried by mistake to other computer programs 、 System damage is serious .
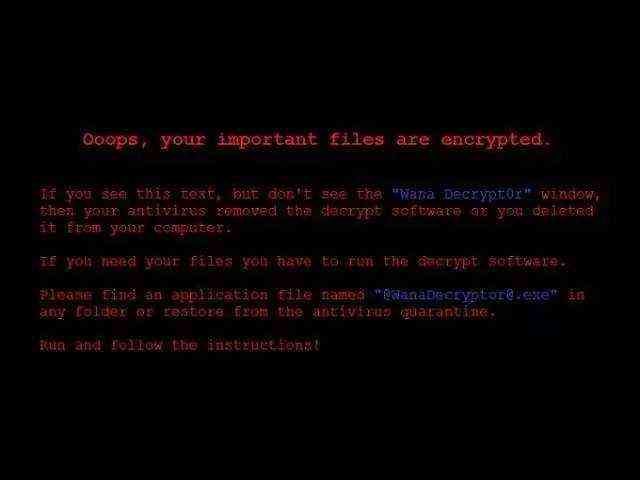
Eternal Blue
This blackmail virus mainly uses Microsoft “ window ” Loopholes in the system , To gain the ability to automatically propagate , Be able to infect all computers in a system within hours . according to 360 Statistics display of , The number of attacks per hour yesterday night reached 4000 Time .
According to the notification of Network Security Agency , The eternal blue is NSA The first example of the civilian use of the network Arsenal . It will automatically scan 445 Of the file share port Windows machine , No user action required , All disk files can be encrypted 、 Lock up , The suffix changes to .onion, And then , Hackers can control Trojans remotely , Extort from users “ Ransom ”.
“ Ransom ” You need to pay in bitcoin . The form of virtual currency payment is decentralized 、 It's hard to track , So it's very popular with hackers .

worm-type virus , Some of the viruses above are variants of it
Worm is a common computer virus . It's using the Internet to replicate and spread , The route of infection is through the Internet and email . The original definition of a worm is because it's in DOS In the environment , When the virus attacks, a bug like object appears on the screen , Gobble up the letters on the screen and reshape them . Worms are self-contained programs ( Or a program ), It can spread copies of its own functions or parts of itself to other computer systems ( Usually through a network connection ).
Worms are self-contained programs ( Or a program ), It can spread copies of its own functions or parts of it to other computer systems ( Usually through a network connection ). Please note that , Different from ordinary viruses , Worms don't need to attach themselves to the host program , There are two types of worms : Host worms and network worms . Host computer worms are completely contained in the computer on which they are running , And use a network connection to copy itself only to other computers , The host computer worm adds a copy of itself to another host , It will stop itself ( So at any given moment , Only one copy of the worm runs ), This worm is sometimes called ' Hare ', Worm viruses are usually transmitted through 1434 Port vulnerability propagation .
For example, in recent years, it has done great harm “ Nimya ” A virus is a kind of worm virus ,2007 year 1 It's popular in January “ Panda burning incense ” And its variants are also worms . The virus exploits a vulnerability in Microsoft's windows operating system , After the computer was infected with this virus , Will continue to dial the Internet automatically , And use the address information in the file or network share to spread , And ultimately destroy most of the user's important data .