当前位置:网站首页>Terminal identification technology and management technology
Terminal identification technology and management technology
2022-07-01 13:13:00 【Bad bad -5】
Anti sharing requirement background
- Sharing Internet access means that multiple terminals share the source address to access the Internet
- Demand background
- Private connection WiFi It is easy to expose the intranet , Avoid shared access users bypassing corporate access control and online behavior monitoring
- The operator undertakes to build the campus network of colleges and universities , The wireless sharing network in the dormitory will affect the broadband account opening rate and income of operators
Anti sharing identification and control technology
- Share the Internet scene
- Configure the router NAT agent , Realize multiple PC Share the Internet through the router
- PC Agent to others through agent software PC Share the Internet
- PC adopt 360WiFi And other software sharing hot spots to share the Internet
Traditional anti sharing technology
- ID Trajectory detection
- Only aim at Windows host , adopt Windows When the network protocol stack is implemented ,ID The value of the field will be sent with IP The number of messages increases
- PC After power on , Will randomly generate a ID value , after PC Will increase this regularly ID value , Generally different hosts ID The initial value of will be different
- By monitoring ID Value of field , You can find out whether there is sharing Internet
- advantage
- It can accurately judge whether it is a shared Internet user
- You can determine the number of network hosts on the online share
- Completely passive monitoring , There is no need to send detection information
- shortcoming
- It takes a period of observation , Usually more than two days . Because it takes a long time to observe , And users' online time will not last for two days
- For time-sharing Internet and Proxy The detection effect of is not obvious . Because of staggering online time , You can't detect different ID value
- DHCP In this case, the effect is poor . Because after the lease expires ,IP The address may change
- Always offset detection
- Different hosts always have different physical offsets , There is a corresponding relationship between the network protocol stack clock and the physical clock
- There is a statistical correspondence between the message frequency sent by different hosts and the clock
- You can use a specific spectrum analysis algorithm , Find different network clock offsets to determine different hosts
- advantage
- It can accurately determine whether it is a shared Internet user
- It can accurately determine the number of shared Internet hosts
- shortcoming
- Complex calculation methods are needed for processing and analysis , Consumption of resources
- It takes a period of observation , Usually more than two days
- DHCP In this case, the effect is poor
- Other traditional anti sharing technologies
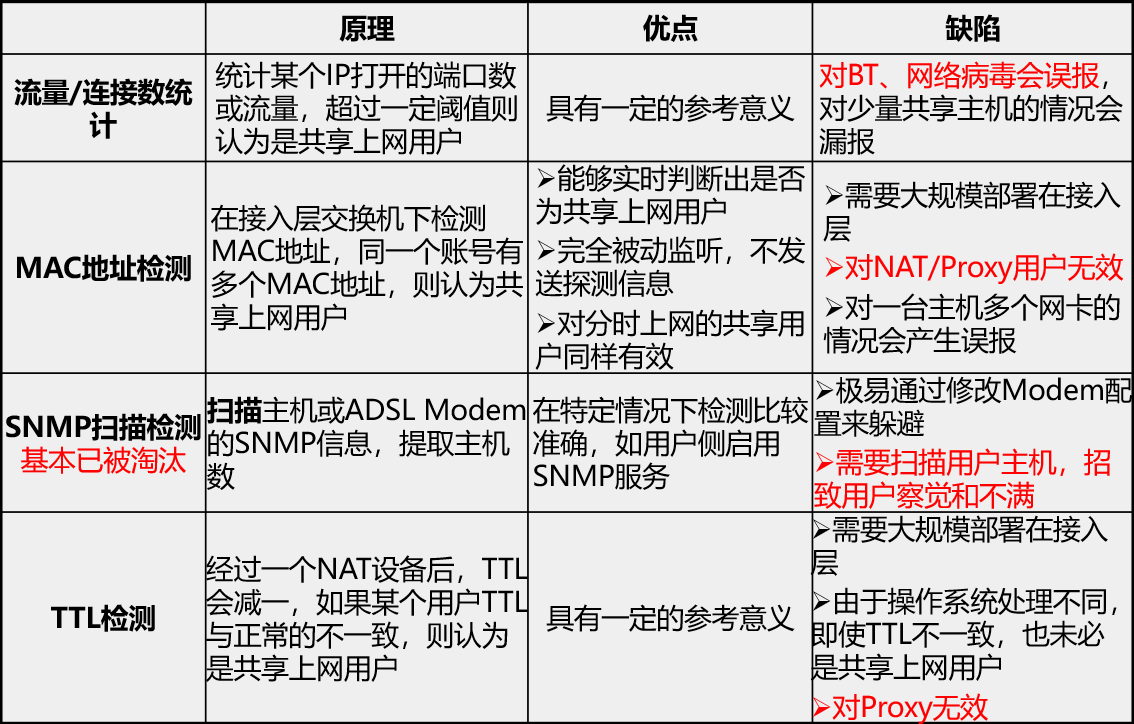
Convinced DPI Detection technology
PC And PC Detection technology between
- QQ Detect anti sharing technology
- QQ At the time of landing , The sent packet will contain its own reality IP Address , Through the gateway device NAT After the transformation , Will not change the inner data information ,AC After receiving the packet , To test , Discover the source in the packet IP Different , Then it can be determined that there is sharing Internet behavior
- Deeply convinced by font detection technology
- In the shared PC visit HTTP Website , When playing video ( Need to install Flash plug-in unit ),AC Request tampering PC request , send PC Report the system font information to AC, If shared PC Use different Fonts , Then you can identify the sharing online behavior
- Deeply convinced of auxiliary detection technology
- URL testing
- By analyzing the data package of common application software , You can find some HTTP In request ,URL There will be some feature strings , These feature strings will have some information related to PC Strongly related . That is, the same one PC The characteristic information string sent is the same , Different PC It's different .AC Then we can get the shared Internet based on the number of different feature strings PC The number of
- Wechat features ID testing
- By analyzing the wechat client when sending messages , At the fixed offset position of the packet , The offset position of the same wechat client is the same , Different clients have different offset positions .AC You can extract the number of offset positions , Get the number of shared Internet devices
- By analyzing the wechat client when sending messages , At the fixed offset position of the packet , The offset position of the same wechat client is the same , Different clients have different offset positions .AC You can extract the number of offset positions , Get the number of shared Internet devices
- URL testing
Detection technology between mobile terminals
- URL Detection technology
- And PC Between the URL The detection technology is the same
- Apply rule detection technology
- Through the built-in rule library of the device , Different mobile terminals can be analyzed from the application
- UA Detection technology
- User-Agent It contains the identification information of the browser ( operating system 、 Encryption level 、 Browser language and other information ), Different terminals can be identified from this information
- User-Agent It contains the identification information of the browser ( operating system 、 Encryption level 、 Browser language and other information ), Different terminals can be identified from this information
PC And mobile terminal detection technology
- URL Detection technology
- Apply rule detection technology
Background of mobile terminal management requirements
- Private connection WiFi It will bring hidden dangers to the intranet
- cheap WiFi Tools will reduce private access WiFi Difficulty and cost
- The popularity of rubbing network cards makes it difficult to find and trace the source of violations
Mobile terminal identification and control technology
- Exclude trust IP And the user
- For legal AP Access , Default release , For illegal access AP Or the user , Then it needs to be controlled
- Manage illegally accessed mobile terminals
- For illegally accessed mobile terminals , You can configure to reject this mobile terminal device , No internet access , And after this IP All access to will be denied
- Identify mobile terminals
- URL Detection technology
- Apply rule detection technology
- UA Detection technology
- Recognition is not supported for the following three scenarios
- Cell phone through USB Data line to access the Internet , share PC Network of
- PC Virtual machine installed in ,AC Different operating systems will be detected
- The mobile terminal simulator is installed on the computer ,AC Will be detected PC And two kinds of traffic packets of mobile terminals
- Mobile terminals find trends
- For recent 7、30 God ,AC Make trend statistics on the number of mobile terminals found every day , It is convenient for administrators to find the effectiveness of management
【AC Terminal identification and control experiment 】
All of the above are original , If unknown or wrong , Please point out .
边栏推荐
- Detailed explanation of parallel replication examples in MySQL replication
- Flinkcdc should extract Oracle in real time. What should be configured for oracle?
- Huawei HMS core joins hands with hypergraph to inject new momentum into 3D GIS
- 逆向调试入门-PE结构-输入表输出表05/07
- MySQL Replication中的并行复制示例详解
- PG基础篇--逻辑结构管理(触发器)
- Have you ever encountered the problem that flynk monitors the PostgreSQL database and checkpoints cannot be used
- 启动solr报错The stack size specified is too small,Specify at least 328k
- VM virtual machine configuration dynamic IP and static IP access
- 不同的测试技术区分
猜你喜欢

图灵奖得主Judea Pearl:最近值得一读的19篇因果推断论文

leetcode:241. 为运算表达式设计优先级【dfs + eval】

波浪动画彩色五角星loader加载js特效
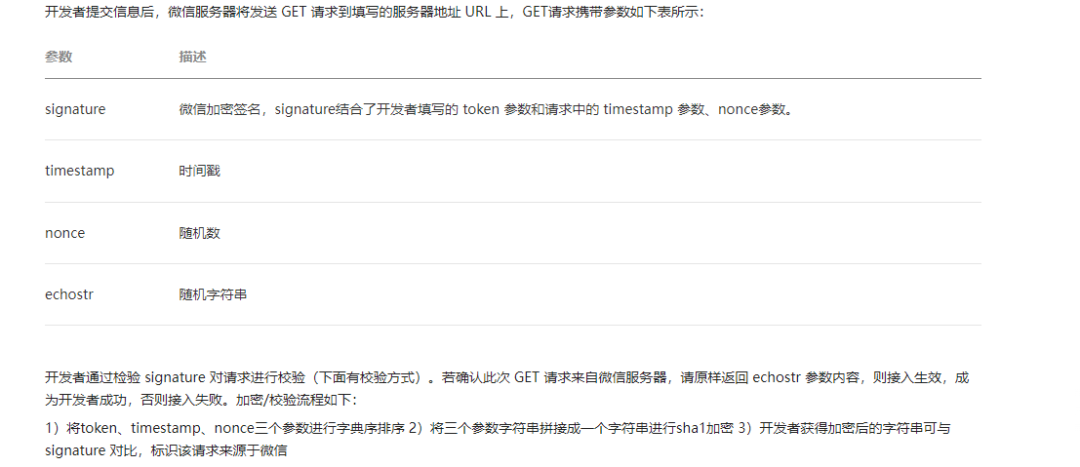
Use Net core access wechat official account development

I spent tens of thousands of dollars to learn and bring goods: I earned 3 yuan in three days, and the transaction depends on the bill

1553B environment construction
学历、长相、家境普通的人,未来的发展方向是什么?00后的职业规划都已经整得明明白白......

Vs code setting Click to open a new file window without overwriting the previous window

【开发大杀器】之Idea

【大型电商项目开发】性能压测-压力测试基本概念&JMeter-38
随机推荐
Judea pearl, Turing prize winner: 19 causal inference papers worth reading recently
终端识别技术和管理技术
图灵奖得主Judea Pearl:最近值得一读的19篇因果推断论文
Ustime wrote a bug
MHA high availability cluster deployment and failover of database
Function test process in software testing
MySQL报错1040Too many connections的原因以及解决方案
Huawei HMS core joins hands with hypergraph to inject new momentum into 3D GIS
There are still many things to be done in the second half of the year
SVG钻石样式代码
Google Earth Engine(GEE)——全球人类居住区网格数据 1975-1990-2000-2014 (P2016)
How can genetic testing help patients fight disease?
Will it affect the original MySQL database to read the data of a MySQL table in full by flick MySQL CDC
[development of large e-commerce projects] performance pressure test - basic concept of pressure test & jmeter-38
C language learning
La taille de la pile spécifiée est petite, spécifiée à la sortie 328k
shell脚本导入存储过程到数据库
请问flink mysql cdc 全量读取mysql某个表数据,对原始的mysql数据库有影响吗
How to count the status of network sockets?
Redis exploration: cache breakdown, cache avalanche, cache penetration