当前位置:网站首页>[GNN report] Li Jia, Hong Kong University of science and technology: Rethinking graph anomaly detection - what kind of graph neural network do we need?
[GNN report] Li Jia, Hong Kong University of science and technology: Rethinking graph anomaly detection - what kind of graph neural network do we need?
2022-07-23 08:38:00 【Quietly like big white】
Catalog
2、Rethinking Graph Neural Networks for Anomaly Detection
Anomaly detection of existing drawings
1、 brief introduction
Guest speaker : Li Jia ( Hong Kong University of science and technology )

Report title : Figure rethinking of anomaly detection — What kind of graph neural network do we need ?
Summary of the report :
Figure neural network (GNN) It is widely used in anomaly detection of structured data , For example, malicious account detection on social networks 、 Financial transaction fraud detection, etc . For the first time, we analyze the possible impact of abnormal data from the perspective of spectral domain . The core findings are : Abnormal data will lead to spectral energy “ Move right ” The phenomenon , That is, the spectrum energy distribution moves from low frequency to high frequency . Based on this discovery , We put forward again Beta Wavelet neural network (BWGNN). It has several band-pass filters with local properties , Better capture “ Move right ” High frequency abnormal information generated . On four large-scale graph anomaly detection data sets ,BWGNN The performance of the model is better than that of the existing models .
About the reporter :
Li Jia , Hong Kong University of science and technology Department of computer science and Hong Kong University of science and Technology ( Guangzhou ) Data science and analysis assistant professor ,2021 He graduated from the Chinese University of Hong Kong . Dr. Li Jia has many years of abnormal detection experience in industry , Worked for Google And Tencent . At present, its research mainly focuses on the anomaly detection of graph data , Reversible graph neural network and drug generation and medical health based on graph data .
reference
1.Rethinking Graph Neural Networks for Anomaly Detection
2.https://github.com/squareRoot3/Rethinking-Anomaly-Detection
2、Rethinking Graph Neural Networks for Anomaly Detection
background



learning model


Anomaly detection of existing drawings
 motivation
motivation

Start with finding the right filter
Background knowledge

Graph Laplacian 
Spectral decomposition ( External environment information )

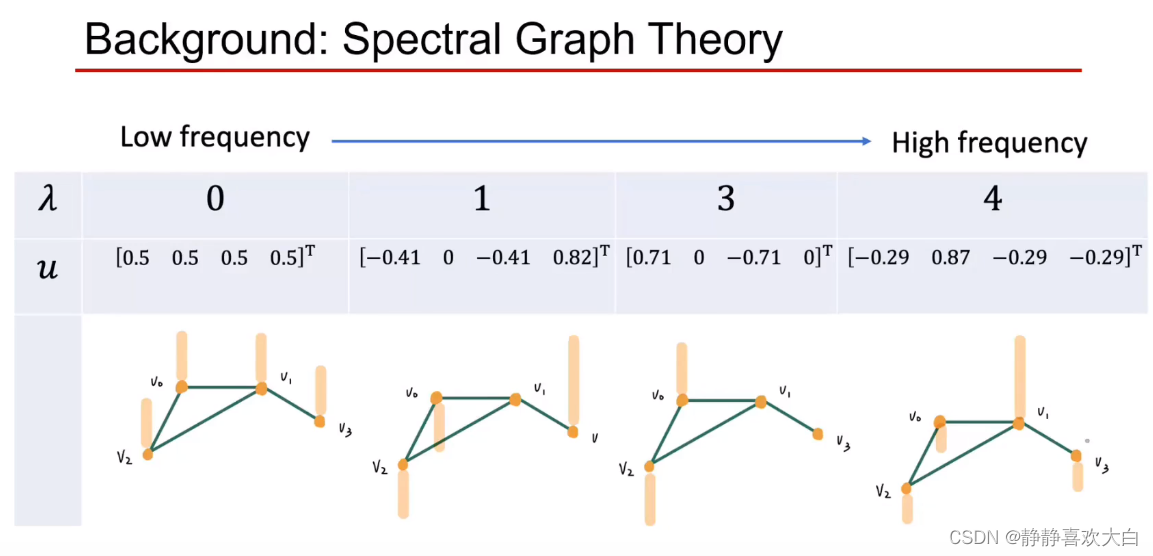
Spectral clustering 

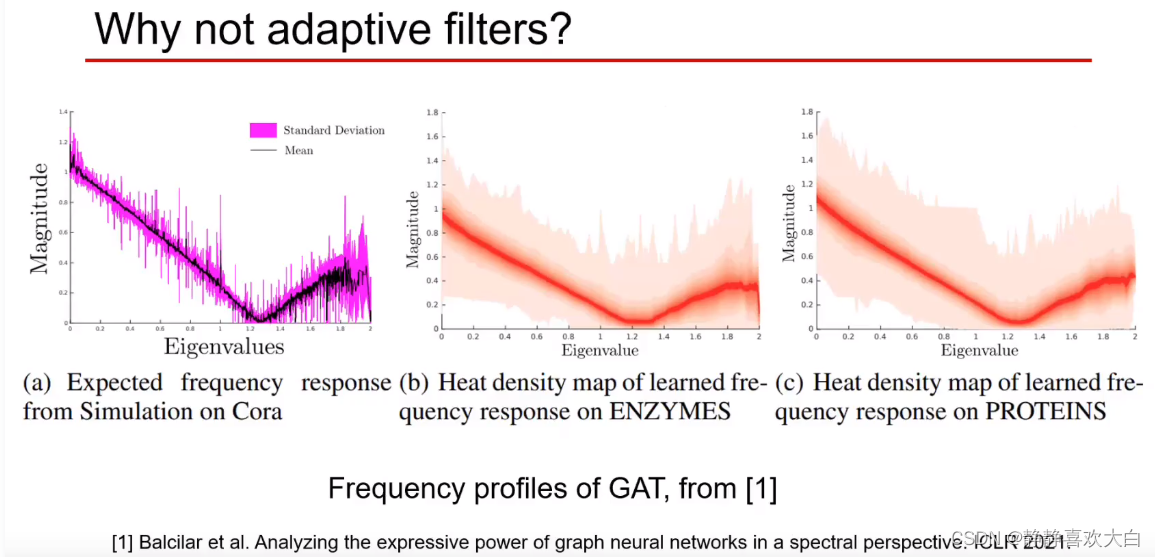
When the features become more and more , Low frequency energy is transferred to high frequency
Definition of low frequency energy
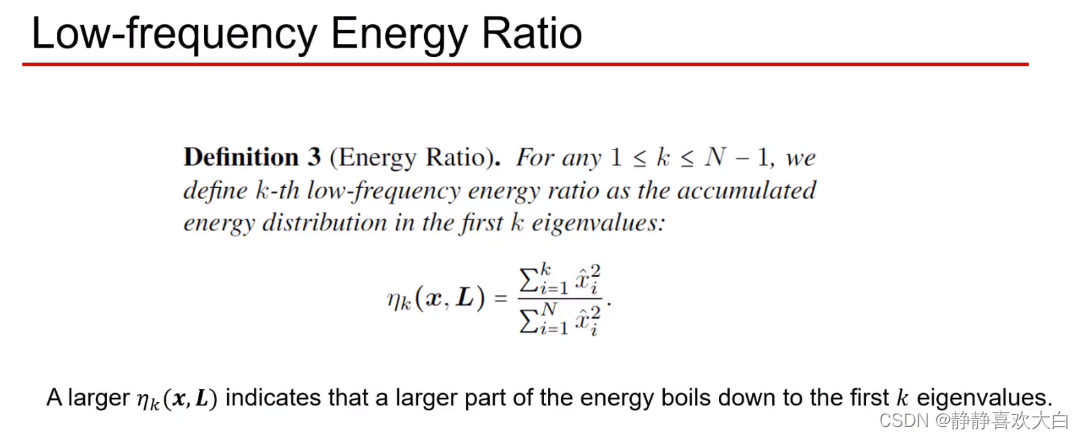
Conclusion
When there is an anomaly in the graph or when the anomaly in the graph gradually becomes larger , The energy distribution after spectral decomposition is gradually transferred from the low-frequency part to the high-frequency part
Verify the conclusion through hypothesis

If the low-frequency characteristic component becomes larger, the low-frequency energy becomes smaller

Verify the conjecture : On a synthetic dataset 
Verify the conjecture : On real data sets

Verification on big data sets is difficult , Propose new concepts
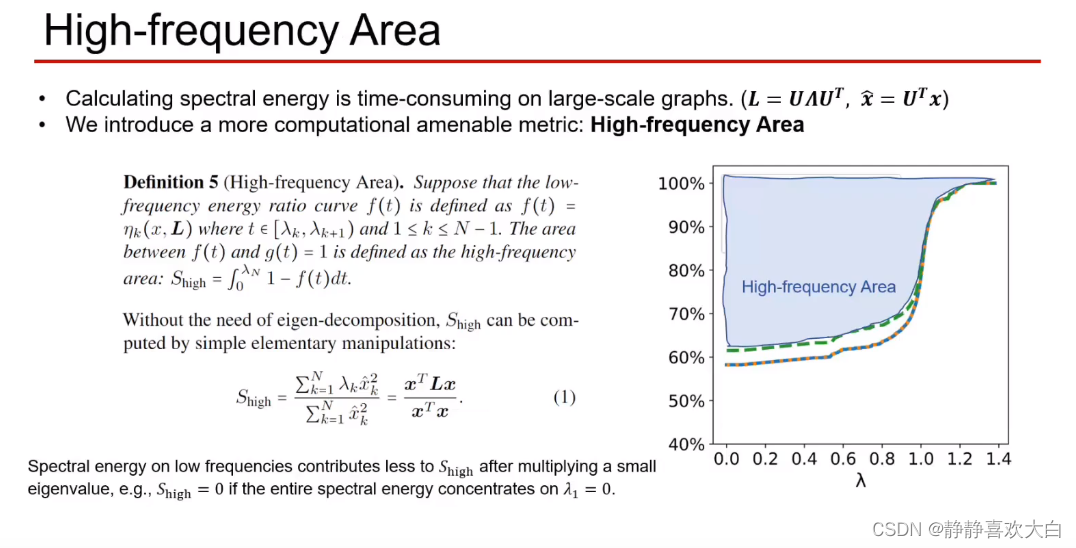 verification
verification
Abnormal decrease is found , Low frequency energy rises ( The green dotted line is higher than the yellow dotted line )
Through the data value result verification

Method

It is found that wavelet transform is low-pass filtering


Discover wavelet GNN True coincidence , At the same time, determine to use beta kernal Of intuition


go back to GNN On the design of , Still follow MPNN normal form

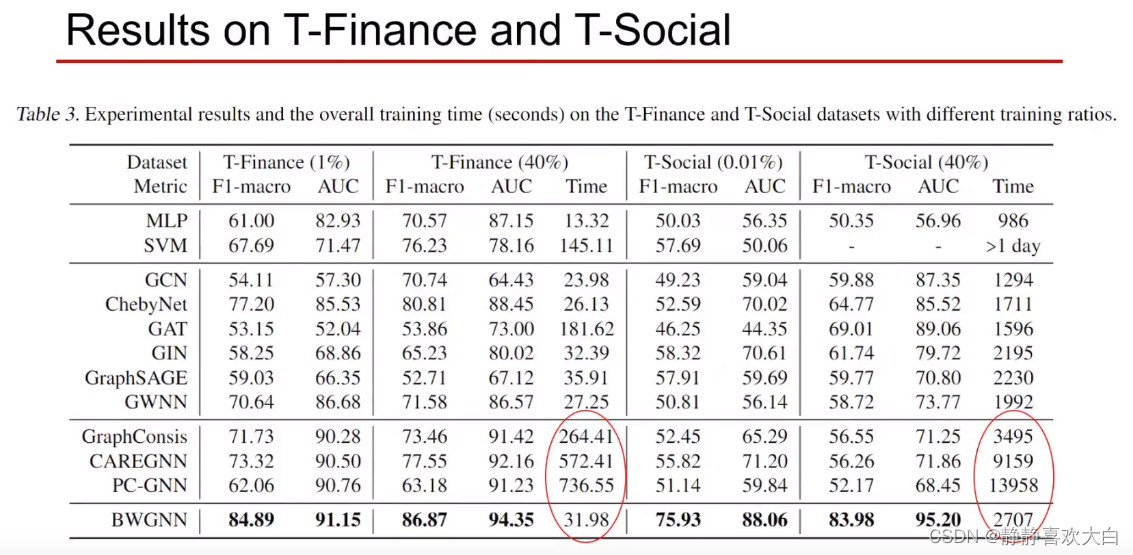
experiment
Framed is a big data set


summary

3、 Reference resources
边栏推荐
猜你喜欢
第三章 栈

一文读懂Elephant Swap的LaaS方案的优势之处
Mria + RLOG 新架构下的 EMQX 5.0 如何实现 1 亿 MQTT 连接

What if Alibaba cloud international forgets its member name or login password?
Let's talk about the charm of code language

获取一个控件宽度

数据分析与隐私安全成 Web3.0 成败关键因素,企业如何布局?

浅谈——网络安全架构设计(四)

Intel raid simulator Download

程序员可能还是程序员,码农可能只能是码农了
随机推荐
How to realize synchronized
Swift - 标红的修饰词
Data analysis and privacy security become the key factors for the success or failure of Web3.0. How do enterprises layout?
Lc: sword finger offer 39. numbers that appear more than half of the time in the array
「疯狂食客」的元宇宙新布局「原始立方」,收藏价值几何?
【wepy2.0】的安装
Vue组件切换时缓存组件状态即动态组件keep-alive 动态组件与异步组件
Initializing, cleaning up and const decorating member functions of constructors
Shell variables, system predefined variables $home, $pwd, $shell, $user, custom variables, special variables $n, $, $*, [email protected],
On the stability of common sorting
Qgraicsview implementation palette
odbc excel--2022-07-21
图的遍历 ~
What's the use of volatile
Flick enables mapstate to implement keyedstate
What level of futures company is founder metaphase? Is the account opening safe and reliable?
BufferedInputStream缓冲区填充问题
svn: E000022: Can‘t convert string from ‘UTF-8‘ to native encoding 问题解决
物联网安装调试员丨让“智慧”生活早日来临
QgrapicsView实现画板


