当前位置:网站首页>Firewall foundation Huawei H3C firewall web page login
Firewall foundation Huawei H3C firewall web page login
2022-06-27 13:09:00 【51CTO】
Huawei H3C firewall login web page
Principle overview :
A firewall ( English :Firewall) Technology is through the organic combination of all kinds of software and hardware equipment for safety management and screening , Help the computer network in it 、 Build a relatively isolated protective barrier between the external networks , A technology to protect user data and information security .
The function of firewall technology is to discover and deal with the possible security risks when the computer network is running 、 Data transmission and so on , The treatment measures include isolation and protection , At the same time, it can record and test all operations in computer network security , To ensure the security of computer network operation , Guarantee the integrity of user data and information , Better for users 、 More secure computer network experience .
So-called “ A firewall ” It refers to an intranet and public access network ( Such as Internet) The way of separation , It is actually an applied security technology based on modern communication network technology and information security technology , Isolation technology . It is more and more used in the interconnection environment of private network and public network , Especially with access Internet The Internet is the most important .
Firewall is a protective barrier between the internal and external network environment with the help of hardware and software , So as to block the unsafe network factors of the computer . Only with the consent of the firewall , Users can enter the computer , If you don't agree, you'll be blocked out , The alarm function of firewall technology is very powerful , When an external user wants to enter the computer , The firewall will quickly send out the corresponding alarm , And remind users of their behavior , And make self judgment to decide whether to allow external users to enter the interior , As long as the user is in the network environment , This kind of firewall can carry out effective query , At the same time, the information found will be displayed to the user , Then users need to implement corresponding settings for the firewall according to their own needs , Block the disallowed user behavior . Through the firewall, you can also effectively view the traffic of information data , And it can also master the speed of uploading and downloading data information , It is convenient for users to have good control judgment on the use of computers , The internal situation of the computer can also be viewed through this firewall , It also has the function of starting and closing the program , And the internal log function of the computer system , In fact, it is also a summary of the real-time situation of the firewall and the internal security of the computer system .
Firewall is a kind of access control scale which is executed when two networks communicate , It can prevent hackers from accessing your network to the maximum extent . It's set up on different networks ( Such as trusted intranet and untrusted public network ) Or a combination of components between network security domains . It is the only access to information between different networks or network security domains , Be able to control according to the safety policy of the enterprise ( allow 、 Refuse 、 monitoring ) Information flow in and out of the network , And it has strong anti attack ability . It's about providing information security services , Infrastructure for network and information security . Logically , The firewall is a separator , A limiter , It's also an analyzer , Effectively monitored the intranet and Internet Any activity between , Ensure the security of the internal network .
The firewall scans its network traffic , This will filter out some attacks , In case it is executed on the target computer . Firewalls can also shut down unused ports . And it can also disable outgoing traffic on specific ports , Block the Trojan horse . Last , It can disable access from special sites , To prevent all communications from unknown intruders .
The barrier of network security
A firewall ( As a blocking point 、 The control points ) It can greatly improve the security of an internal network , And reduce risk by filtering unsafe Services . Because only carefully selected application protocols can pass through the firewall , So the network environment becomes more secure . For example, firewalls can prohibit such as well-known unsafe NFS Protocol access to protected network , In this way, it is impossible for external attackers to use these fragile protocols to attack the internal network . Firewalls can also protect the network from routing based attacks , Such as IP Source routing attacks and ICMP Redirection path in redirection . The firewall should be able to reject all messages of the above types of attacks and notify the firewall administrator .
Strengthen network security strategy
Configure through a firewall centric security scheme , All security software ( Like a password 、 encryption 、 Identity Authentication 、 Audit, etc ) Configure on the firewall . Compared with dispersing network security issues to various hosts , Centralized security management of firewall is more economical . For example, during network access , The one-time password system and other identity authentication systems do not have to be scattered on each host , And focus on the firewall .
Monitoring audit
If all access passes through the firewall , that , The firewall can record these accesses and log them , At the same time, it can also provide statistical data of network usage . When something suspicious happens , The firewall can give appropriate alarm , And provide detailed information on whether the network is monitored and attacked . in addition , It is also very important to collect the usage and misuse of a network . The first reason is to know whether the firewall can resist the detection and attack of attackers , And know whether the control of firewall is sufficient . Network usage statistics are also very important for network demand analysis and threat analysis .
Prevent the leakage of internal information
By using firewall to divide the internal network , It can realize the isolation of key network segments of intranet , Thus, the impact of local key or sensitive network security issues on the global network is limited . also , Privacy is an issue of great concern to the intranet , An unnoticed detail in an internal network may contain clues about security and attract the interest of external attackers , Some security vulnerabilities of the internal network have even been exposed . Using a firewall, you can hide those internal details, such as Finger,DNS Etc .Finger Displays the registered names of all users of the host 、 real name , Last login time and use shell Type, etc . however Finger The information displayed is very easy for attackers to learn . An attacker can know how often a system is used , Whether there are users connecting to the Internet in this system , Whether the system is noticed when being attacked, etc . Firewalls can also block information about internal networks DNS Information , The domain name of such a host and IP The address will not be known to the outside world . In addition to safety , The firewall also supports Internet Service enterprise internal network technology system VPN( Virtual private network ).
Logging and event notification
All data entering and leaving the network must pass through the firewall , The firewall records it through logs , It can provide detailed statistical information of network use . When a suspicious event occurs , The firewall can alarm and notify according to the mechanism , Provide information on whether the network is threatened .
Huasan firewall login web page :
The topology :

Realization effect :
Enter url https://192.168.56.10
Click Advanced

Get into H3C A firewall web page :
user name :admin
password :admin

Login successful

Configuration command :
login: admin
Password:
<H3C>sy
System View: return to User View with Ctrl+Z.
[H3C]sy FW1
[FW1]dis th
#
sysname FW1
#
telnet server enable
#
irf mac-address persistent timer
irf auto-update enable
undo irf link-delay
irf member 1 priority 1
#
xbar load-single
password-recovery enable
lpu-type f-series
#
scheduler logfile size 16
#
aaa session-limit ftp 16
aaa session-limit telnet 16
aaa session-limit ssh 16
domain default enable system
#
ip http enable
ip https enable
#
return
[FW1]un in en
Information center is disabled.
[FW1]int g1/0/1
[FW1-GigabitEthernet1/0/1]ip add 192.168.56.10 24
[FW1-GigabitEthernet1/0/1]dis th
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address 192.168.56.10 255.255.255.0
#
return
[FW1]security-zone name Trust
[FW1-security-zone-Trust]import interface g1/0/1
[FW1]object-policy ip manage
[FW1-object-policy-ip-manage]rule pass
[FW1]zone-pair security source trust destination local
[FW1-zone-pair-security-Trust-Local]object-policyapply ip manage
[FW1]local-user admin class manage
[FW1-luser-manage-admin]password simple admin
[FW1-luser-manage-admin]service-type http https
[FW1-luser-manage-admin]authorization-attribute user-role n etwork-admin
[FW1-luser-manage-admin]dis th
#
local-user admin class manage
password hash $h$6$hx47TNXzNgS9ICF2$6sUbrnLZ6TCw1fJ9ZidCMf J3O1N6kW5eLoDAFlZdfjJzbn/P1NKL1QuagnGVU24SCO/iVh++eamPVOXos ueNNQ==
service-type telnet terminal http https
authorization-attribute user-role level-3
authorization-attribute user-role network-admin
authorization-attribute user-role network-operator
#
return
[FW1-luser-manage-admin]
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.
- 36.
- 37.
- 38.
- 39.
- 40.
- 41.
- 42.
- 43.
- 44.
- 45.
- 46.
- 47.
- 48.
- 49.
- 50.
- 51.
- 52.
- 53.
- 54.
- 55.
- 56.
- 57.
- 58.
- 59.
- 60.
- 61.
- 62.
- 63.
- 64.
Grooming command :
[FW1]int g1/0/1
[FW1-GigabitEthernet1/0/1]ip add 192.168.56.10 24 // Configure login address
[FW1]security-zone name Trust
[FW1-security-zone-Trust]import interface g1/0/1 take G1/0/1 Add to trust Area
[FW1]object-policy ip manage
[FW1-object-policy-ip-manage]rule pass // Rule release
[FW1]zone-pair security source trust destination local //
[FW1-zone-pair-security-Trust-Local]object-policy apply ip manage
[FW1]local-user admin class manage
[FW1-luser-manage-admin]password simple admin
[FW1-luser-manage-admin]service-type http https
[FW1-luser-manage-admin]authorization-attribute user-role n etwork-admin
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.

Huawei firewall login web page :
The topology :
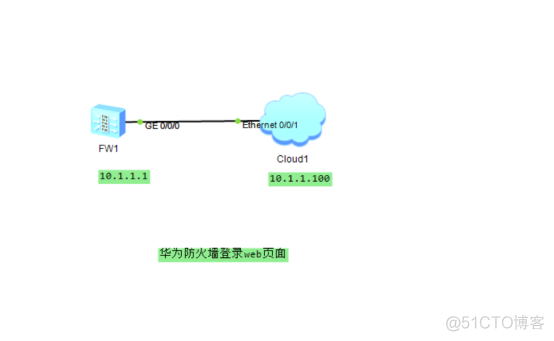
Experimental results :


Huawei firewall defaults to
user name :admin
password :[email protected]
Username:admin
Password:
The password needs to be changed. Change now? [Y/N]: y
Please enter old password:
Please enter new password:
Please confirm new password:
Info: Your password has been changed. Save the change to survive a reboot.
*************************************************************************
* Copyright (C) 2014-2018 Huawei Technologies Co., Ltd. *
* All rights reserved. *
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
*************************************************************************
<USG6000V1>sy
Enter system view, return user view with Ctrl+Z.
[USG6000V1]sy FW1
[FW1]un in en
Info: Saving log files...
Info: Information center is disabled.
[FW1]int g0/0/0
[FW1-GigabitEthernet0/0/0]ip add 10.1.1.1 24
[FW1-GigabitEthernet0/0/0]se
[FW1-GigabitEthernet0/0/0]service-manag
[FW1-GigabitEthernet0/0/0]service-manage a
[FW1-GigabitEthernet0/0/0]service-manage all pe
[FW1-GigabitEthernet0/0/0]service-manage all permit
[FW1-GigabitEthernet0/0/0]dis th
2022-06-26 04:04:45.140
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 10.1.1.1 255.255.255.0
alias GE0/METH
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
return
[FW1-GigabitEthernet0/0/0]
<FW1>sy
Enter system view, return user view with Ctrl+Z.
[FW1]web
[FW1]web-ma
[FW1]web-manager en
[FW1]web-manager enable
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.
- 36.
- 37.
- 38.
- 39.
- 40.
- 41.
- 42.
- 43.
- 44.
- 45.
- 46.
- 47.
- 48.
- 49.
- 50.
- 51.
- 52.
To configure web Page login completed , Direct login :
user name :admin
password :[email protected]
Grooming command :
End of experiment ;
remarks : If there is a mistake , Please understand !
This article is my study notes , For reference only ! If there is a repetition !!! Please contact me
边栏推荐
猜你喜欢

AI for Science: scientific research paradigm, open source platform and industrial form

基于SSM实现招聘网站

Esp32s3 iperf routine test esp32s3 throughput test

Daily question brushing record (6)
Record number of visits yesterday

Summary of redis master-slave replication principle

Cloud native (30) | kubernetes' app store Helm

让学指针变得更简单(二)

今日睡眠质量记录78分

【医学分割】unet3+
随机推荐
Good luck today
PLM还能怎么用?
云原生(三十) | Kubernetes篇之应用商店-Helm
今天运气不错
[fans' welfare] today, I'd like to introduce a method to collect money for nothing - convertible bonds. I personally verified that each person can earn 1500 yuan a year
Esp32s3 iperf routine test esp32s3 throughput test
如何下载带有超链接的图片
二叉树的三种遍历方式
Nmcli team bridge basic configuration
Privacy computing fat offline prediction
栈的计算(入栈出栈顺序是否合法)-代码
SSH workflow and principle
Viewpager2 usage record
执行 npm 指令失败,提示ssh: ... Permission denied
Quanzhi A13 tossing memo
数字化新星何为低代码?何为无代码
JSON. Stringify usage
Clear self orientation
PyCharm汉化
How to choose LAN instant messaging software