当前位置:网站首页>On the exploitation of a horizontal ultra vires vulnerability
On the exploitation of a horizontal ultra vires vulnerability
2022-06-13 10:18:00 【Bright moon and clear wind~~】
Link to the original text :https://www.freebuf.com/articles/web/334522.html
Remember the exploitation of a horizontal ultra vires vulnerability
shit xiong 2022-06-07 10:42:17
62551
List of articles
0x00 Preface
This paper records the whole process of a horizontal ultra vires , The following happened roughly :
- modify post Parameters , Cause unauthorized viewing and deletion ;
- Modify the path (REST Style parameter ), Result in ultra vires modification ;
- modify cookie Field , Bypass login for unauthorized access ;
- Ultra vires editors implant xssPayload, Get complete cookie.
Okay , Start making up .
0x01 Ultra vires view and delete
Register and log in to the personal center , A random test , It is found that you can view or modify any user data beyond your authority by modifying parameters . Let's take the educational experience as a demonstration .
1、 First create , Revise .
2、 Packet capture, interception and replay , adopt infoId To reference objects , Return user information , And enter the editing state .

3、 The request package passes infoId Parameter reference object ,sql Inject fruitless , Try to modify infoId value , Reference object succeeded , Return other user information . Modify when deleting post The parameter value can also delete any user information beyond authority .
4、 Continue to edit your self-assessment , Click save . Find out the front infoId The value of ran into the path , Also try to modify ( Note that this involves changes to , Don't modify it at will , You can try to modify the content of another test account ).
5、 Return to modified successfully ( Go to the target account to refresh , It was found that the data had indeed been modified ).
6、 Why can paths also be used as parameter test points , Because what's used here is REST Style parameter .
Reference link :https://blog.csdn.net/weixin_44750790/article/details/118195473
0x02 Bypass login unauthorized access
The previous operation , I haven't been able to get sensitive information such as mobile phone number and email , It is found that the editing of these basic information does not use the same set of processes , In order to get it out , Then there is the following .
1、 Below is a request for preview materials , I can't see get/post Parameters , Nature does not exist “ Unsafe direct object reference ” Such ultra vires loopholes .
Obviously through cookie Discriminative , So many fields , Generally, I don't consider overstepping my authority ( The head is not strong enough ), But at first glance cookie The field values in all seem to be base64 code . It's all base64 Coded , this !
2、 Control variable method , Field by field deletion , Find valid fields ( Delete a field , No change on the page indicates that this field is invalid , I believe everyone knows this skill ).
A delete operation , Leaving only career_id This field . Replay returns the profile , Modifying or deleting this field will cause an exception , This indicates that the server only verifies this field .
Verify only one field , It seems easy to use base64 code , Good good !
3、 Decoding ,5160397 It is estimated that this user id 了 .
4、 adopt Burpsuite Of Intruder Module traversal career_id Field , Catch someone else id have a look .

5、 Use this id, Successfully unauthorized access to the user's resume information .
6、 Next , Copy this cookie Replace the in your browser cookie, Successfully bypassed login , Unauthorized access to other users' personal Center , And it can edit and delete data .
0x03 utilize “self-xss“ Get more permissions
Seriously overstepping one's authority to the top is almost over , The following is the use of “ Crooked ways ” 了 .
1、 Further exploration and discovery , In fact, the access credentials of the personal center are only verified career_id This field , Other pages also verify more cookie Field , Only after passing the verification can you access more pages to view the position information 、 Delivering resumes, etc .
2、 In fact! , There is also a storage type for editing data XSS. Storage type of resume editing page xss, It's basically a self-xss No doubt , Generally, who can access my resume editing page .
3、 I can even edit other people's resumes beyond my authority , Can we embed in other people's resumes when editing them xssPayload, A set of “ Ultra vires + self_xss” Combined boxing .
in addition , It is not difficult to see from the previous request package , These data editing operations , There must be CSRF Loopholes . that , Another set “CSRF + self\_xss” Combined boxing .
Of course ,CSRF Certainly not as safe as our ultra vires editors .
Next, wait for the target to visit ......
Here is a brief analysis of the train of thought , I won't do the demonstration .
0x04 summary
Summarize the basic idea of testing level ultra vires :
- Control variable method to delete parameters or cookie Field , Found a valid parameter or cookie Field ;
- As far as possible for parameters or cookie Field defuzzification , Further test ;
- Modify the parameter value or cookie Field , Carry out ultra vires test on operations such as adding, deleting, modifying and checking ;
- Ultra vires combined with other vulnerabilities to improve the hazard level .
Ultra vires loopholes can also be combined with Authz This kind of burp Plug in to test , However, it is generally limited to the ultra vires of viewing operations .
The author of this article : shit xiong, Please quote from FreeBuf.COM
边栏推荐
- MySQL中redo日志和undo日志简述
- 实战模拟│企业微信机器人实时报错预警
- Install Kubernetes 1.24
- 等个有“源”人|OpenHarmony 成长计划学生挑战赛报名启动
- Apple zoom! It's done so well
- Node-RED系列(二七):扩展节点之s7节点的使用说明
- 一篇文章读懂:Spark运行模式
- Thingsboard tutorial (20): filtering telemetry data using regular chains
- It was so simple to implement system call
- Information document management and configuration management
猜你喜欢

Matplotlib 学习笔记
![[51nod p3047] displacement operation [bit operation]](/img/89/065e59382d3596868002466e3951d9.jpg)
[51nod p3047] displacement operation [bit operation]

逐向双碳:东数西算中的绿色需求与竞争焦点

Node red series (25): integrate Gaode map and realize 3D map and track playback

A hot MySQL training topic, making you a master of SQL
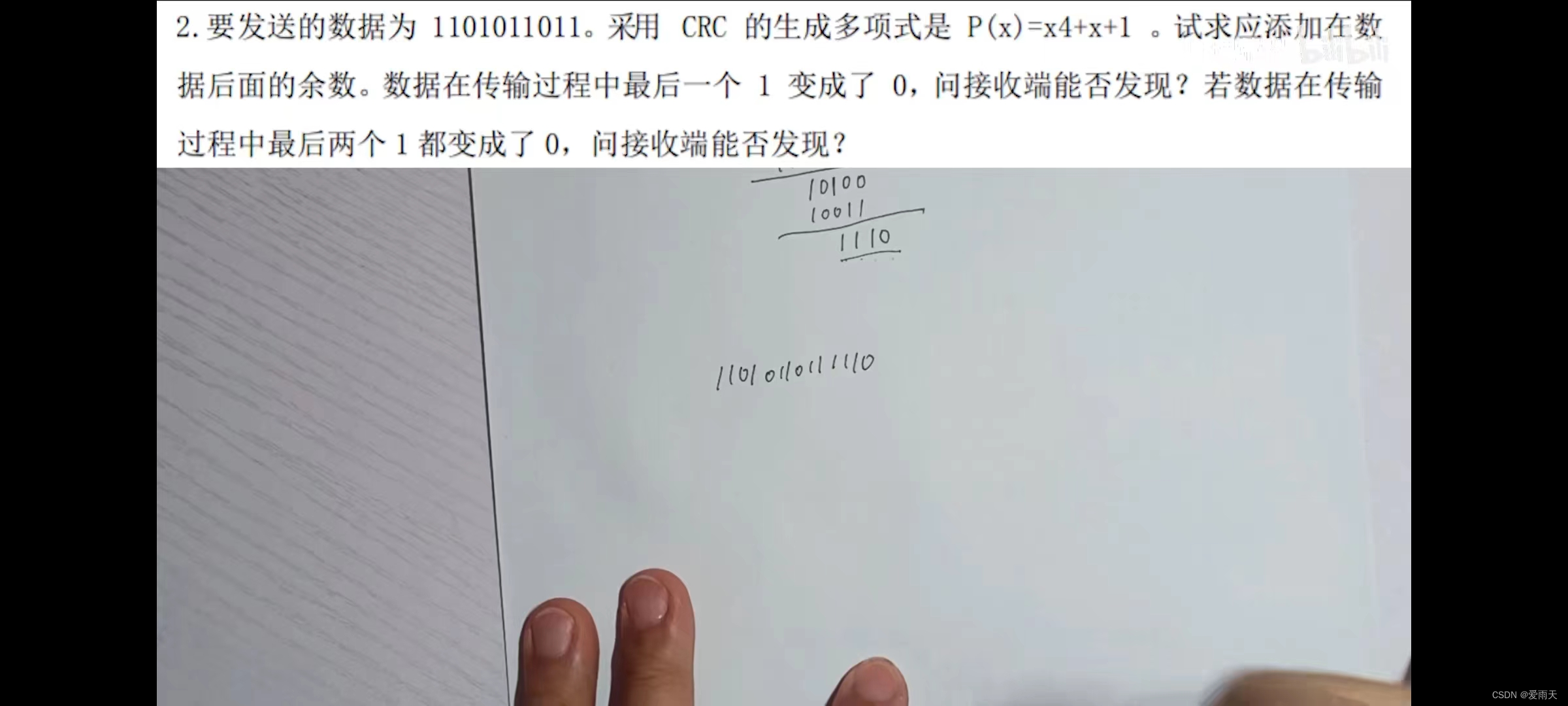
Test redundancy code for error problem type solution - excerpt

vivo大规模 Kubernetes 集群自动化运维实践
![[51nod p2673] shortest path [heap optimization Dijk]](/img/08/5e68466fe8ff8458f736bc50d897da.jpg)
[51nod p2673] shortest path [heap optimization Dijk]
![[51nod p2106] an odd number of times [bit operation]](/img/f4/600395cd0ecb44235c65805f379bd4.jpg)
[51nod p2106] an odd number of times [bit operation]

云计算企业崛起 甲骨文数据库市场主导地位动摇
随机推荐
[51nod p3111] xiaoming'ai intercepts [Las]
[51nod p2527] or and sum [bit operation]
Matlab hub motor analysis fuzzy PID control vertical vibration analysis
记一次水平越权漏洞的利用
MySQL中redo日志和undo日志简述
递归想法和实现介绍,消除递归
[image denoising] image denoising based on MATLAB Gaussian + mean + median + bilateral filtering [including Matlab source code 1872]
Interrupt handling mechanism
[51nod p2102] or subtraction and [bit operation]
隐私计算FATE-核心概念与单机部署
架构师必备:系统容量现状checklist
电解电容、钽电容、普通电容
五分钟内编写Pytorch模型
36氪首发|打造国产精算预测引擎等产品,「深轻科技」连续完成三轮融资
Chapter I Section I
Node red series (24): use MySQL nodes in node red to add, delete, modify and query databases
修饰模式和代理模式的异同
Introduction to knowledge map
[51nod p3058] Xiao ming'ai set [set]
[51nod 2493] sum of binary distances [bit operation]