当前位置:网站首页>[try to hack] windows system account security
[try to hack] windows system account security
2022-06-30 20:09:00 【Happy star】
Blog home page : Happy star The blog home page of
Series column :Try to Hack
Welcome to focus on the likes collection ️ Leaving a message.
Starting time :2022 year 6 month 30 Japan
The author's level is very limited , If an error is found , Please let me know , thank !
Do not break the law !!! The whole content of this article , All from the Internet , Only as a record of their own learning .
1、 lower than Windows10, Use command lusrmgr.msc
See if there are any new / Suspicious accounts
2、 higher than Windows10, Control panel -> The user account 
3、net user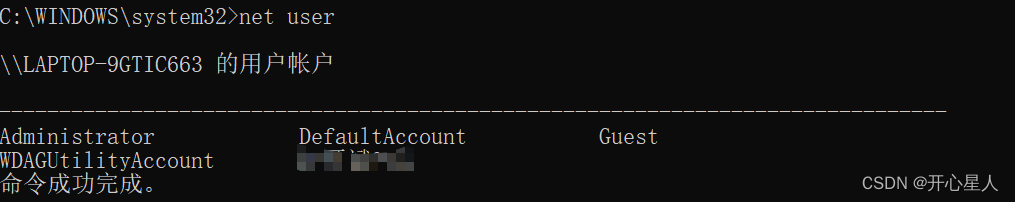
But the hidden account cannot be viewed
net user A specific user 
Pay special attention to Guest Whether the user has enabled , Because hackers may not add new users but enable Guest user 
net user hacker$ 111111 /add
The user name is $ End with hidden users ,111111 User password . The above command is to add a hidden user 
You can see it's intercepted , Allow the operation directly
net localgroup administrators hacker$ /add
Add hidden users to the administrators group , The hidden user has administrator privileges

You can see our hidden users in the control panel
4、 Is there any way to " Command prompt " and " Computer management " And hide the account
Yes , Through the registry
function ->regedit
HKEY_LOCAL_MACHINE\SAM\SAM\Domains\Account\Users\Name
You can see our hidden users 
administrator The items corresponding to the account are "000001F4"
We will hacker$ Export to hacker.reg. At the same time "000003F3" and "000001F4" Term F The key values are exported as user.reg,admin.reg
use " Notepad " open admin.reg, Will the "F" Copy the content after the value , Replace user.reg Medium "F" Value content , Save when done .
net user hacker$ /del
Delete hidden users
take hacker.reg and user.reg Import registry , The hidden user is finished 
We can still use it normally hacker$ This hidden user 
But at this point , Administrators can still delete our hidden users through the registry , How to hide ?
Came to "HKEY_LOCAL_MACHINE\SAM\SAM" It's about , Set up "SAM" Permissions for the item , take "administrators" You can cancel all the permissions you have .

In this way, the administrator cannot delete it
5、D shield
Use D Shield to check the security of the system account 
It's still very effective , The alarm went off immediately
But the discovery cannot be deleted .
How to delete , To be studied
6、 Combined with log analysis
View administrator login time 、 Whether the user name is abnormal
function ->eventvwr.msc
Log Parser
Download address :https://www.microsoft.com/en-us/download/confirmation.aspx?id=24659
Download to by default C:\Program Files (x86)\Log Parser 2.2
1、 Query the event of successful login
All events of successful login
LogParser.exe -i:EVT –o:DATAGRID "SELECT * FROM c:Security.evtx where EventID=4624"
Events that specify the login time range :
LogParser.exe -i:EVT –o:DATAGRID "SELECT * FROM c:Security.evtx where TimeGenerated>'2018-06-19 23:32:11' and TimeGenerated<'2018-06-20 23:34:00' and EventID=4624"
Extract the user name and password of successful login IP:
LogParser.exe -i:EVT –o:DATAGRID "SELECT EXTRACT_TOKEN(Message,13,' ') as EventType,TimeGenerated as LoginTime,EXTRACT_TOKEN(Strings,5,'|') as Username,EXTRACT_TOKEN(Message,38,' ') as Loginip FROM c:Security.evtx where EventID=4624"
2、 Query the event of login failure
All events of login failure :
LogParser.exe -i:EVT –o:DATAGRID "SELECT * FROM c:Security.evtx where EventID=4625"
Extract login failed user names for aggregation statistics :
LogParser.exe -i:EVT "SELECT EXTRACT_TOKEN(Message,13,' ') as EventType,EXTRACT_TOKEN(Message,19,' ') as user,count(EXTRACT_TOKEN(Message,19,' ')) as Times,EXTRACT_TOKEN(Message,39,' ') as Loginip FROM c:Security.evtx where EventID=4625 GROUP BY Message"
3、 System history switch on record :
LogParser.exe -i:EVT –o:DATAGRID "SELECT TimeGenerated,EventID,Message FROM c:System.evtx where EventID=6005 or EventID=6006"
.\LogParser.exe -i:EVT –o:DATAGRID "SELECT EXTRACT_TOKEN(Message,13,' ') as EventType,TimeGenerated as LoginTime,EXTRACT_TOKEN(Strings,5,'|') as Username,EXTRACT_TOKEN(Message,38,' ') as Loginip FROM E:\onedrive\ desktop \11.evtx where EventID=4624"
边栏推荐
猜你喜欢

文件包含&条件竞争
Solution to rollback of MySQL database by mistake deletion

线上线下双结合,VR全景是家具线上转型好方法!

Primary school, session 3 - afternoon: Web_ xxe

VR云展厅如何给线下实体带来活力?有哪些功能?

How unity pulls one of multiple components

Advanced skills of testers: a guide to the application of unit test reports

超视频时代的音视频架构建设|Science和英特尔联袂推出“架构师成长计划”第二季

太湖 “中国健康农产品·手机直播万里行”走进太湖

线下门店为什么要做新零售?
随机推荐
FH6908A负极关断同步整流模拟低压降二极管控制IC芯片TSOT23-6超低功耗整流器 1w功耗 <100uA静态 替代MP6908
Convert seconds to * * hours * * minutes
传输层 使用滑动窗口实现流量控制
Tensorflow2.4实现RepVGG
mysql统计账单信息(上):mysql安装及客户端DBeaver连接使用
VR全景拍摄为什么要加盟?巧借资源实现共赢
Why should offline stores do new retail?
如何做好测试用例设计
Inventory the six second level capabilities of Huawei cloud gaussdb (for redis)
【LeetCode】【SQL】刷题笔记
Primary school, session 3 - afternoon: Web_ xxe
[iccv 2019] characteristics precise supervision of feature super resolution for small object detection
Why must we move from Devops to bizdevops?
为什么一定要从DevOps走向BizDevOps?
解决arm_release_ver of this libmali is ‘g2p0-01eac0‘,rk_so_ver is ‘4‘,libgl1-mesa-dev不会被安装,存在未满足的依赖关系
exness:流动性系列-流动性清洗和反转、决策区间
Audio and video architecture construction in the super video era | science and Intel jointly launched the second season of "architect growth plan"
Summary of operating system interview questions (updated from time to time)
Cartoon | has Oracle been abandoned by the new era?
漏洞扫描工具大全,妈妈再也不用担心我挖不到漏洞了
