当前位置:网站首页>Enterprise data leakage prevention solution sharing
Enterprise data leakage prevention solution sharing
2022-06-24 23:31:00 【Cnsidna. No.1】
Enterprise data leakage prevention requirements :
With the increasing development of enterprise informatization , The competition among software manufacturers is becoming more and more intense , In addition, China does not pay enough attention to intellectual property rights 、 Rampant imitation products . Protect the source code 、 Ensure the core competitiveness of the enterprise , Become the first priority of many software R & D enterprises . So how should enterprises ensure the security of source code ? How should enterprises choose a suitable encryption software ?
Demand summary analysis
Usually , The following conditions exist in the enterprise :
Insiders can pass classified documents through U Disk and other mobile storage devices are copied out of the computer and taken away ;
Insiders can connect their own laptops to the company's Network , Then copy out the classified documents and take them away ;
Insiders can send confidential documents via email via the Internet 、QQ、MSN Wait to send it out ;
Insiders can print confidential documents 、 Take it out of the company after copying ;
Insiders can burn confidential documents on CD or take screenshots out of the company ;
Insiders can take computers or computer hard disks containing classified documents out of the company ;
Loss or repair of company computers, etc , The computer containing classified documents was lost , Maintenance and other reasons fall into the hands of external personnel , Thus causing the hidden danger of leakage ;
External visitors bring computers into the company's Network , Access the company's confidential resources, steal confidential documents and divulge secrets ;
Project developers back up a copy of their own development at home , Even the source code and development design documents of the whole system , Whether intentionally or unintentionally, it will cause the risk of code leakage ;
Project managers have complete product source code and development and design documents in their hands . These people understand development , Understand project , Understand the needs , Become a major hidden danger of source code and design document disclosure ;
Personnel who need hardware debugging , Secret related documents can be directly distributed to the hardware equipment for transfer , Cause the file to leak ;
Developed by shenxinda, an international leading technology SDC(Secret Data Cage) Confidential data security system , Adopt the world's most advanced third-generation transparent encryption technology --- Kernel level deep three-dimensional sandbox encryption technology , Is designed to solve the source code , Drawing , A set of anti disclosure system designed for the disclosure of confidential data such as documents . Today's enterprises have their own LAN , Generally, the main core confidential data is stored on the server , Some are stored on employees' computers .SDC Our secret design concept is : When employees work , Virtual an isolated encrypted sandbox on the employee's computer , The sandbox will actively authenticate and connect with the server , Then form a server - Client sandbox Such a confidential workspace , Employees work in sandboxes , thus : -- Confidential data on the server will not be stored during use , Or encryption upon landing . -- All development results on the employee's computer can only be stored on the server , Or in the local encrypted sandbox . -- The sand table is isolated from the outside world , So it won't leak . SDC Encrypted sandbox , It's a container , Everything can be loaded ; Encryption itself doesn't care what an individual is , So it has nothing to do with the process , It has nothing to do with the file format , It has nothing to do with the file size , Won't destroy the file . Unlike other encryption software , Modify the contents of the file itself .

边栏推荐
- OpenSSL SSL_read: Connection was reset, errno 10054
- Whereabouts computer desktop small arrow
- 一文理解OpenStack网络
- 基本数据类型
- HarmonyOS访问数据库实例(3)--用ORM Bee测下HarmonyOS到底有多牛
- R language dplyr package group_ By function and summarize_ The at function calculates the dataframe to calculate the number of counts and the mean value of different groups (summary data by category v
- 斐波那契
- Binary lookup array subscript
- OpenSSL SSL_ read: Connection was reset, errno 10054
- golang convert json string to map
猜你喜欢
华为机器学习服务语音识别功能,让应用绘“声”绘色

Hyperledger Fabric 2. X dynamic update smart contract
RT thread uses RT kprintf
第六章 网络学习相关技巧5(超参数验证)

idea创建模块提示已存在

中学校园IP网络广播系统解决方案-校园数字IP广播系统方案设计指南
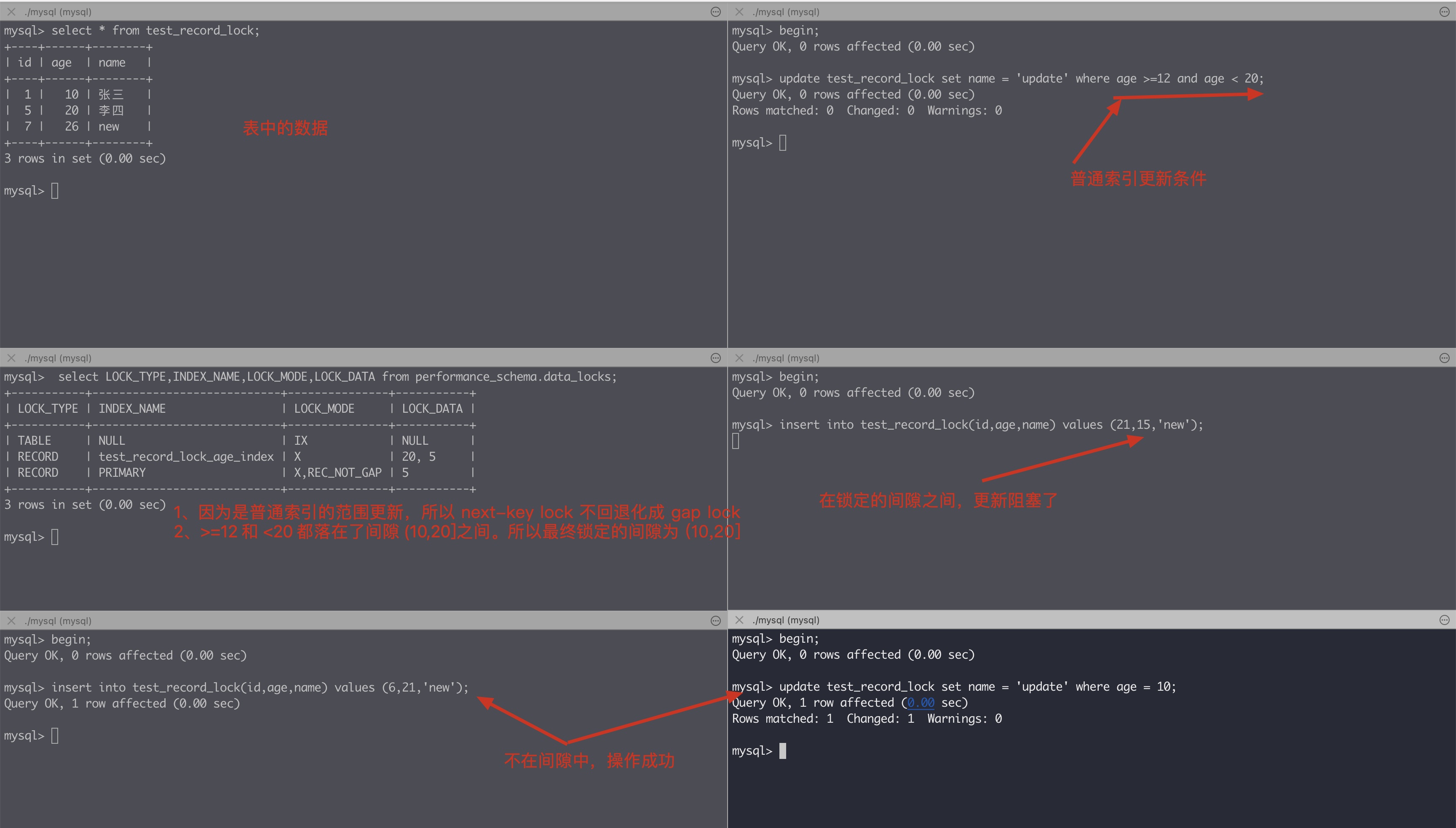
Record the range of data that MySQL update will lock
宁德时代定增450亿:高瓴认购30亿 曾毓群仍控制23%股权
Ganglia 的安装与部署
![[JS] - [array application] - learning notes](/img/8a/808fde0cc86e0ec5e1f5558ba196b4.png)
[JS] - [array application] - learning notes
随机推荐
Chapter VI skills related to e-learning 5 (super parameter verification)
379. hide and seek
Spark's wide dependence and narrow dependence yyds dry goods inventory
第六章 网络学习相关技巧5(超参数验证)
Laravel pagoda security configuration
[JS] - [array application] - learning notes
【js】-【树】-学习笔记
MySQL semi sync replication
#22Map介绍与API
Laravel user authorization
Hyperledger Fabric 2. X dynamic update smart contract
Still using simpledateformat for time formatting? Be careful of project collapse
Use of laravel verifier
OpenSSL SSL_read: Connection was reset, errno 10054
R语言使用MatchIt包进行倾向性匹配分析、使用match.data函数构建匹配后的样本集合、通过双样本t检验分析(双独立样本t检验)来判断倾向性评分匹配后样本中的所有协变量的平衡情况
Listen to the markdown file and hot update next JS page
R语言使用nnet包的multinom函数构建无序多分类logistic回归模型、使用AIC函数比较两个模型的AIC值的差异(简单模型和复杂模型)
R language uses the polR function of mass package to build an ordered multi classification logistic regression model, and uses exp function, confint function and coef function to obtain the confidence
sql -CONVERT函数
Simple use of libnum Library (hexadecimal string conversion)