当前位置:网站首页>Chapter 18 request matcher serverwebexchangematcher of oauth2loginauthenticationwebfilter
Chapter 18 request matcher serverwebexchangematcher of oauth2loginauthenticationwebfilter
2022-07-25 03:37:00 【buffeer】
In the last article, we analyzed OAuth2LoginAuthentiationWebFilter The successful matching request path will be intercepted . Which request paths will be blocked 、 How to customize the request path to be intercepted . These two questions will be the theme of today .
initialization ServerWebExchageMatcher
stay ServerHttpSecurity The inner class of a class OAuth2LoginSpec Of configure() In the way ,OAuth2LoginAuthenticationWebFilter Initialize the ServerWebExchangeMather. If we don't specify ServerWebExchangeMather, Create the default ; Otherwise use the specified . The creation process is probably shown in the following source code .
protected void configure(ServerHttpSecurity http) {
// Omit other configuration
AuthenticationWebFilter authenticationFilter = new OAuth2LoginAuthenticationWebFilter(manager, authorizedClientRepository);
authenticationFilter.setRequiresAuthenticationMatcher(this.getAuthenticationMatcher());
}
private ServerWebExchangeMatcher getAuthenticationMatcher() {
// If you do not specify your own configuration , Use the default
if (this.authenticationMatcher == null) {
this.authenticationMatcher = this.createAttemptAuthenticationRequestMatcher();
}
return this.authenticationMatcher;
}
private ServerWebExchangeMatcher createAttemptAuthenticationRequestMatcher() {
return new PathPatternParserServerWebExchangeMatcher("/login/oauth2/code/{registrationId}");
}
From the source , We can observe that the default intercepted request path is :/login/oauth2/code/{registrationId}
PathPatterParserServerWebExchangeMatcher
The function of matching the request path is determined by PathPatterParserServerWebExchangeMatcher To achieve . It will intercept the request path , And extract the parameters of the request path . for example , The request path is /login/oauth2/code/google Parameters will be extracted google, And put in Map in . The core source code is shown below .
public Mono<MatchResult> matches(ServerWebExchange exchange) {
ServerHttpRequest request = exchange.getRequest();
PathContainer path = request.getPath().pathWithinApplication();
// The request method is different from the configuration method , The match is not successful
if (this.method != null && !this.method.equals(request.getMethod())) {
return MatchResult.notMatch().doOnNext((result) -> {
if (logger.isDebugEnabled()) {
logger.debug("Request '" + request.getMethod() + " " + path + "' doesn't match '" + this.method + " " + this.pattern.getPatternString() + "'");
}
});
} else {
boolean match = this.pattern.matches(path);
if (!match) {
return MatchResult.notMatch().doOnNext((result) -> {
if (logger.isDebugEnabled()) {
logger.debug("Request '" + request.getMethod() + " " + path + "' doesn't match '" + this.method + " " + this.pattern.getPatternString() + "'");
}
});
} else {
// Extract request parameters
Map<String, String> pathVariables = this.pattern.matchAndExtract(path).getUriVariables();
Map<String, Object> variables = new HashMap(pathVariables);
if (logger.isDebugEnabled()) {
logger.debug("Checking match of request : '" + path + "'; against '" + this.pattern.getPatternString() + "'");
}
// Return the result of successful matching , And put the extracted parameters into the results .
return MatchResult.match(variables);
}
}
}
Custom interception path
If you don't want to intercept the request, the default path is /login/oauth2/code/{registrationId} Request , We can configure . The configuration is as follows .
@Configuration
@EnableWebFluxSecurity
@Slf4j
public class SecurityConfig {
@Bean
public SecurityWebFilterChain securityWebFilterChain(ServerHttpSecurity http) {
return http
.csrf().disable()
.oauth2Login(oauth2Login -> oauth2Login
.authenticationMatcher(new PathPatternParserServerWebExchangeMatcher(
"/oauth2/code/{registrationId}"))
)
.build();
}
}
边栏推荐
- Execution flow control of shell
- Common methods of array
- How chemical enterprises choose digital service providers with dual prevention mechanism
- Using one stack to sort another stack
- [Flink] transform operator flatmap
- From input URL to page presentation
- MySQL select query part 2
- Secondary vocational network security skills competition P100 dcore (light CMS system) SQL injection
- Secondary vocational network security skills competition P100 vulnerability detection
- Unified return data format
猜你喜欢

Moveit2 - 8. Motion planning API
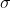
Machine learning notes - building a recommendation system (4) matrix decomposition for collaborative filtering

It took me 2 years from Foxconn assembly line to Tencent software testing post~

Direct insert sort / Hill sort
How does Jupiter notebook change themes and font sizes?

Openlayers draw circles and ellipses
![[Flink] submit the jar package to the Flink cluster and run it](/img/9b/076949a4b9fe75ee248c400ee21474.png)
[Flink] submit the jar package to the Flink cluster and run it

Question D: pruning shrubs

Fifth day of force deduction
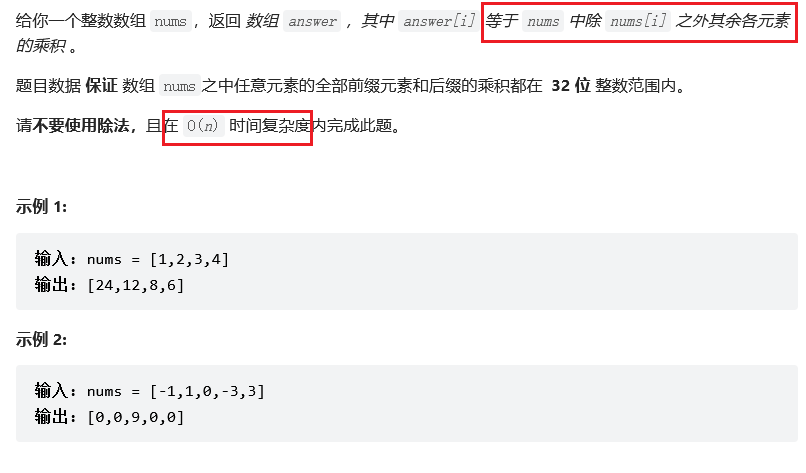
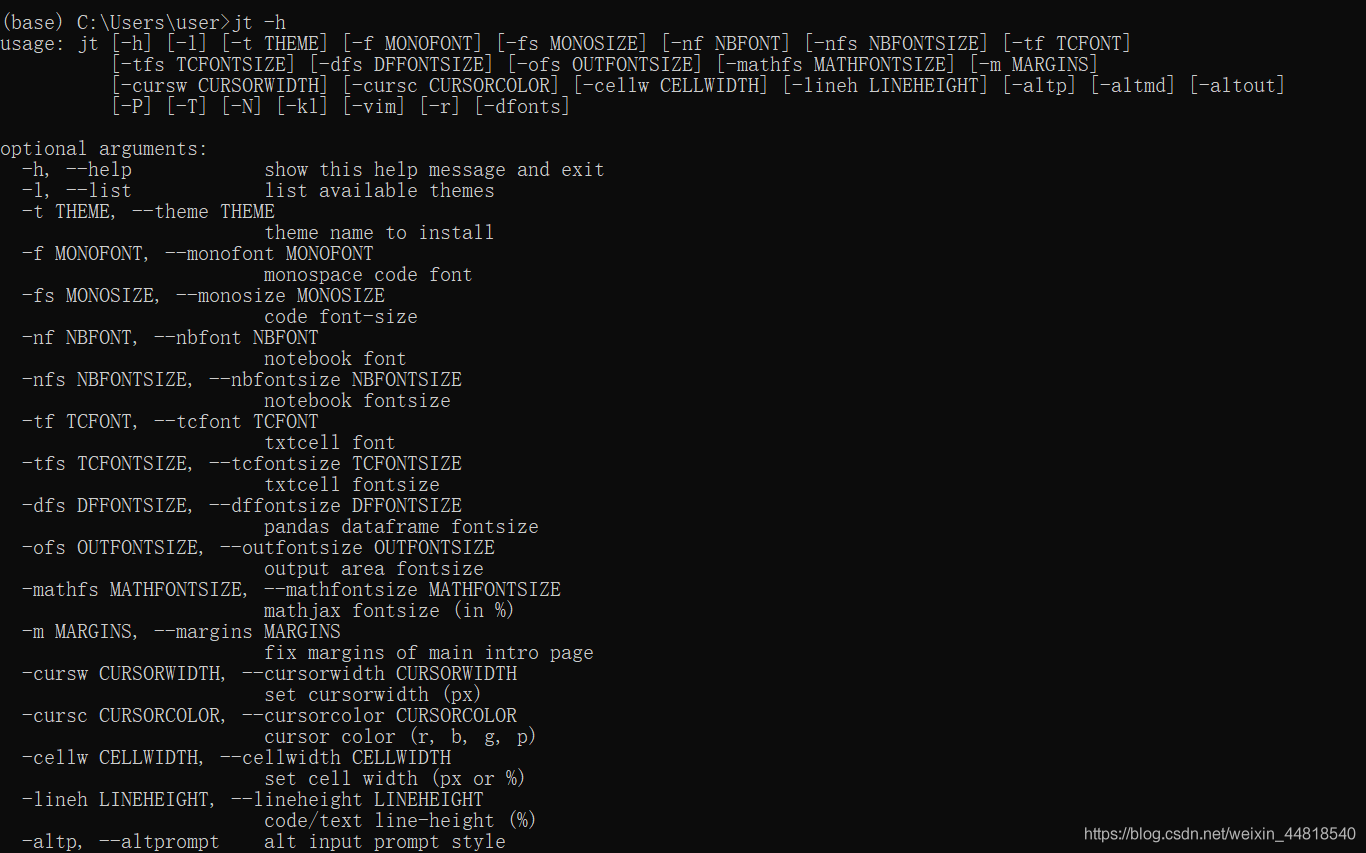
Force deduction problem 238. product of arrays other than itself
随机推荐
Day 9 (capture traffic and routing strategy)
Secondary vocational network security skills competition P100 dcore (light CMS system) SQL injection
[Flink] rich function
Skywalking distributed link tracking, related graphics, DLJD, cat
Swagger key configuration items
Servlet个人实操笔记(一)
C language writes a circular advertising lantern or changes it to a confession system
Machine learning notes - building a recommendation system (4) matrix decomposition for collaborative filtering
[leetcode medium] 34. Find the first and last positions of elements in the sorted array - array double pointer
Leetcode programming practice -- Tencent selected 50 questions (I)
B. Difference of GCDs
Merge sort / quick sort
VMware installation
C. Mark and His Unfinished Essay
Force deduction question 3
Record once C # extract audio files with ffmempeg
File permission management
Detailed explanation of three factory modes
Recursive and non recursive methods are used to realize the first order, middle order and second order traversal of binary tree respectively
Day 10: BGP border gateway protocol