当前位置:网站首页>How the WordPress administrator user name was leaked
How the WordPress administrator user name was leaked
2022-06-10 14:31:00 【fmz2222】
WordPress Your administrator account is easy to access , Although I got the administrator account , It's not very useful , But it does not rule out that some white passwords are simple digital passwords . The attacker blew up or hit the library successfully , So as to obtain the background administrator account .
that . How the attacker got you Wordpress 【 Administrator user name 】 Of , And how to protect your administrator account from being obtained , This article will talk about !!!
obtain
1、 First, let's talk about how the administrator's account is leaked
An attacker or an attacker program constructs :https://www.5uapk.com/wp-json/wp/v2/users/ Of URL Conduct GET, such 99% Will return a string of information , It contains your administrator account . as follows :
- [{"id":1,"name":"daniao","url":"","description":"","link":"https:\/\/daniao.com\/author\/daniao","slug":"daniao","avatar_urls":{"24":"https:\/\/cn.gravatar.com\/avatar\/28f745cefb1ad2da1747cdcfccc0ddfa?s=24&d=mm&r=g","48":"https:\/\/cn.gravatar.com\/avatar\/28f745cefb1ad2da1747cdcfccc0ddfa?s=48&d=mm&r=g","96":"https:\/\/cn.gravatar.com\/avatar\/28f745cefb1ad2da1747cdcfccc0ddfa?s=96&d=mm&r=g"},"meta":[],"_links":{"self":[{"href":"https:\/\/daniao.com\/wp-json\/wp\/v2\/users\/1"}],"collection":[{"href":"https:\/\/daniao.com\/wp-json\/wp\/v2\/users"}]}}]
The above information can be found :daniao The administrator account , The truth has been hidden , This is just for demonstration .
2、 Confirm whether it is used wordpress Program
In fact, the above code has almost confirmed that you are using wp Procedure , Let me mention here :
An attacker or an attacker program constructs https://www.5uapk.com//wp-includes/wlwmanifest.xml Of URL Conduct GET, To determine if you used Wordpress Program . And your background login address ! You will get such feedback after typing . So it is very important to modify the background login address .
- <manifest xmlns="http://schemas.microsoft.com/wlw/manifest/weblog">
- <options>
- <clientType>WordPress</clientType>
- <supportsKeywords>Yes</supportsKeywords>
- <supportsGetTags>Yes</supportsGetTags>
- </options>
- <weblog>
- <serviceName>WordPress</serviceName>
- <imageUrl>images/wlw/wp-icon.png</imageUrl>
- <watermarkImageUrl>images/wlw/wp-watermark.png</watermarkImageUrl>
- <homepageLinkText>View site</homepageLinkText>
- <adminLinkText>Dashboard</adminLinkText>
- <adminUrl>
- <![CDATA[ {blog-postapi-url}/../wp-admin/ ]]>
- </adminUrl>
- <postEditingUrl>
- <![CDATA[ {blog-postapi-url}/../wp-admin/post.php?action=edit&post={post-id} ]]>
- </postEditingUrl>
- </weblog>
- <buttons>
- <button>
- <id>0</id>
- <text>Manage Comments</text>
- <imageUrl>images/wlw/wp-comments.png</imageUrl>
- <clickUrl>
- <![CDATA[ {blog-postapi-url}/../wp-admin/edit-comments.php ]]>
- </clickUrl>
- </button>
- </buttons>
- </manifest>
3、 Confirm your users id
Attackers can also construct < https://www.5uapk.com?author=1 //?author=2 //?author=3> To confirm that your Administrator id, To match the above .
Protect
Now that I know , So how to protect , Keep looking down .
4、 Set access rights
1) Blocking access /wp-json/wp/v2/users/, If it's a pagoda , You can set the following code in the website configuration or pseudo static .
Here's the hidden content !
Comment and refresh , To view
4) effect
Visit the above page at this time , Will be shielded . Pictured :


5、 If you are a pagoda and have a professional firewall installed , You can also set it like this
Where access is prohibited url Add the following rule to :
- /wp-json/wp/v2/users
- /wp-includes/wlwmanifest.xml
Visit at this time , The prompt of firewall interception will appear .

6、 Last
This is not a loophole , So don't be nervous , In fact, the little friend who paid a little attention to security had already modified a very strong password , Hidden login background , Disabled xmlrpc.php.
1) If you want to Ban xmlrpc.php, You can use nginx, The code is as follows , The placement is the same as above , Put in pseudo static settings .
- location ^~ /xmlrpc.php { return 403; }
Whether to disable it according to your own needs , If an upgrade error occurs , Then you can delete or disable the code .
2) In fact, the administrator accounts of some topics are displayed in the article , It feels like this really is ……, We can do it in wp Set a nickname in the background , In this way, the article will show the nickname in the article .
3) You can pass the above URL Test your Wordpress Site . See if you can get sensitive information . If you are particularly sensitive , Just set the permissions .
Reprinted address :http://www.5uapk.com/game/3047.html
边栏推荐
- LeetCode_ 21 (merge two ordered linked lists)
- 22.6.7 successfully use doc2vec model to generate embedded vectors
- Adding, deleting, modifying and querying databases with JDBC
- Gin blog 总结1
- Singleton pattern and special class design
- C#多线程学习笔记三
- 在启牛开户安全么
- 这个牛逼的低代码生成器,现在开源了!
- 一次主从表集成流程开发过程
- 2022危险化学品经营单位主要负责人考试题库及在线模拟考试
猜你喜欢

C multithreading learning note 3

Gin blog 总结1
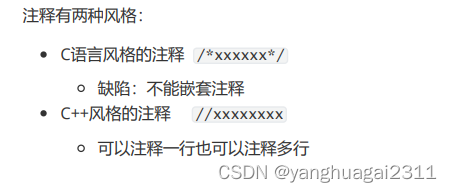
初试c语言之第二次笔记

超强实操!手把手教学Kinect深度图与RGB摄像头的标定与配准

JMeter 中如何实现接口之间的关联?
北京/上海内推 | 微软亚洲研究院系统与网络组招聘全职实习生

Leetcode 2293. Minimax game (yes. One pass)

2022山东省安全员C证复训题库及在线模拟考试

Design tools and skills for beginners to build their own blog

Flyter page Jump to transfer parameters, tabbar learning summary 5
随机推荐
初试c语言之第二次笔记
what‘t the meaning of “de facto“
[Discrete Mathematical period Review Series] Second and first order Logic (precate Logic)
博主自白
SIGIR 2022 | HKU and Wuhan University put forward kgcl: a recommendation system based on knowledge map comparative learning
2022广东省安全员A证第三批(主要负责人)考试练习题及在线模拟考试
2022山东省安全员C证复训题库及在线模拟考试
KaTeX问题 —— csdn编辑时中打出等号对齐的样式
[logodetection data set processing] (2) draw the label box of the training set picture
CG collision testing
Singleton pattern and special class design
Cell asynchronously invokes method change records
KAtex problem - the style of equal sign alignment in CSDN editing
为doc2vec生成训练向量的数据集
焱融看|混合云环境下,如何实现数据湖最优存储解决方案
How to implement the association between interfaces in JMeter?
Flyter page Jump to transfer parameters, tabbar learning summary 5
一次主从表集成流程开发过程
CG碰撞检测 Collision Testing
【离散数学期复习系列】六、树