当前位置:网站首页>[csrf-01] basic principle and attack and defense of Cross Site Request Forgery vulnerability
[csrf-01] basic principle and attack and defense of Cross Site Request Forgery vulnerability
2022-07-04 04:08:00 【Like the wind 9】
Catalog
1 CSRF summary
Definition :CSRF(Cross-site request forgery, Cross-site request forgery ) Also known as One Click Attack perhaps Session Riding , Commonly abbreviated as CSRF perhaps XSRF, yes An attack that deceives a victim into submitting a malicious request . It inherits the identity and privileges of the victim , Perform unintentional... On behalf of the victim 、 Malicious operation . it mandatory The end user is currently After authentication Of Web Applications On the implementation Not intended The operation of .
Place of occurrence :Web On the application , Neither system nor component .
Time of occurrence : After the end user is currently authenticated .
Occurrence form :“ mandatory ” Perform operations not intended by the user , The coercion here can also induce the user to execute .
The goal is :
The main purpose is Forge change status ( Such as changing the password 、 Transfer accounts ) Request Instead of stealing data , Because the attacker can't see the response to the fake request . With the help of some social workers ( For example, send a link via email or chat ), An attacker can trick a user into performing an operation chosen by the attacker .
CSRF The attack target is the business or function that can change the server state or data , For example, change the email address of the victim 、 Password or purchase goods . Forced query of victim data , It's useless for the supplier , Because the server response could not be obtained . therefore ,SCRF The attack is on a request that causes a state change .
Sometimes you can put CSRF Attacks are stored on vulnerable sites . These holes are called “ Stored CSRF Loophole ”. This can be done by simply accepting HTML Store... In the field of IMG or IFRAME Mark , Or through more complex cross site scripting attacks . If the attack can be stored in the site SCRF attack , The severity of the attack will be amplified . especially , The possibility of receiving an attack increases , Because victims are more likely to view pages containing attacks than a random page on the Internet .( It is universal )
And XSS contrast :
Even though CSRF Sounds like a cross site script XSS, But it has something to do with XSS Very different ,XSS Leverage trusted users within the site , and CSRF Then request a trusted website by pretending to be a trusted user . And XSS Compared to attack ,CSRF Attacks are often unpopular ( So there are few resources to guard against it ) It's hard to prevent , So it's considered a ratio XSS More dangerous .
CSRF harm
- If the victim is an ordinary user , be CSRF An attack can successfully force a user to perform a state change request , For example, send mail in the name of the target user 、 Send a message , Steal the target user's account , Even buy goods 、 Virtual currency transfer , This will reveal personal privacy and threaten the property security of the target user .
- If the victim is an administrator account ,CSRF May endanger the whole Web Applications .
- Example : You want to transfer money to a user 100 element , Then click “ Transfer accounts ” After button , Emitted HTTP The request will be made with http://www.xxbank.com/pay.php?user=xx&money=100 similar . And the attacker constructs Links http://www.xxbank.com/pay.php?user=hack&money=100, When the target user accesses the URL after , It will automatically turn to Hack Account transfer 100 element , And this only involves the operation of the target user , The attacker did not obtain the information of the target user cookie Or other information .
2 CSRF Attack process and principle
2.1 CSRF Scene example
Suppose there is a trusted website bank website , The user has logged in to the bank website and has been authenticated , The user did not exit the bank website , Visited a phishing link sent by the hacker , Making users unknowingly send a transfer request to the bank .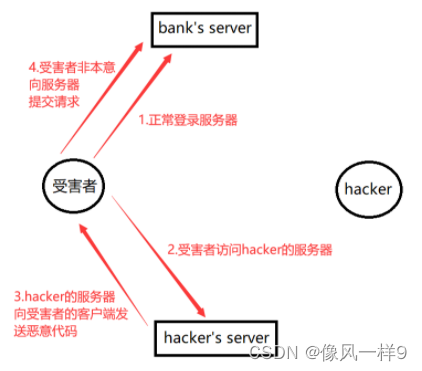
2.2 The attack process
(1) user C Browse and log in to the trusted server site A;
(2) user C land A Verification passed , In user C Generated on the browser A Of Cookie Etc ;
(3) user C Visit the attack site without logging out B;
(4) user C Attacked site B Loaded malicious code ;
(5) Load malicious code to third-party sites A Send a fake request ( The request is not an unintended request of the user ); When sending a request , user C Your browser will send the 2 What you carry in your step cookie Wait for information to be sent to the site A;
(6) Site A Indistinguishable 5 Whether the request made in is made by the user C The original intention of , Because the browser will automatically bring users C Of Cookie, therefore A Will be based on C Permission processing of 5 Request .
2.3 principle
(1) The brief answer to the principle is : The attacker exploits the identity of the target user , Perform some illegal operations in the name of the target user .
(2) For most sites , The browser requests that all credentials associated with the site be sent automatically , For example, the user's session cookie、IP Address 、Windows Domain voucher, etc . therefore , If the user has currently authenticated the site , Then the site will not be able to distinguish whether the request sent by the client is forged by the attacker or intended by the victim .
2.4 The conditions for a successful attack :
(1) The user has logged into your website A, And the local records cookie.
(2) When the user does not exit the site A Under the circumstances ( That is to say cookie In the case of the entry into force ), Visited a malicious attacker lured to dangerous sites provided B(B Site requires access site A).
(3) Site A I did not do anything CSRF defense .
3 CSRF attacks / How to trigger
(1)GET Request type :
- Use a Tags define hyperlinks . For example, in a malicious web page , Some a The source code of label statement is
<a href=" Target site page + Related parameters "> Part-time job </a>, When the victim clicks on the page , The attacker will send a forged request to the target site . - Use img Tag insert image . For example, in a malicious web page , Some img The source code of label statement is
<img src=" Target site page + Related parameters ">, When the victim swipes to the page , The attacker will send a forged request to the target site , because src Not a remote address of a picture , So there is an error in the picture display . - Others can trigger an attacker to forge URL The label of .
(2)POST Request type :
- Even if the website related operations are POST Method , Attackers can also use The way of constructing forms to forge requests , The core code is as follows : Among them the first 2~5 The line is the request and parameter forged by the attacker , By the victim clicking a Tag trigger JS Code submission forgery request .
<meta charset='utf-8'>
<form name ='csrf'
action =' Target site page '
method = 'post'>
<input type= 'hidden' name='username' vlaue=' The attacker faked '>
<input type= 'hidden' name='money' vlaue=' The attacker faked '>
</form>
<script>document.csrf.submit()</script>
<img src='./1.jpg'><br />
<a href='javascript:document.csrf.submit()'> Part-time job </a>
- And XSS Combination , The above two attack methods , Attackers need to build their own website to store web pages with malicious code , And with the XSS A combination of CSRF Cross Site Request Forgery is to store malicious code in other people's websites . such as , By studying the business process of the target website , Construct the following code , If the administrator of the target website triggers this code when logging in to the target website , Then an account will be automatically registered on the website .
<script>
xmlhttp=new XMLHttpRequest();
xmlhttp.open(\'post\',\'http:// The target site \',false);
xmlhttp.setRequestHeader("Cintent-type","application/x-www-form-urlencoderd");
xmlhttp.send(\'act=add&username=hacker&password=123456&password2=123456& The other parameters \');
</script>
5 CSRF Defense
5.1 Some ineffective defense means
(1) Use password cookie
be-all cookie, Even if it's password cookie, It will also be submitted with each request , Whether or not the end user is cheated to submit a request , All identification tokens or credentials will be submitted .
(2) Only accept POST request
Developers can develop applications to accept only for executing business logic POST request , Misconception that attackers cannot build malicious Links , So it can't be executed CSRF attack . Unfortunately , This logic is incorrect , There are many ways for an attacker to trick a victim into submitting a forged POST, For example, a simple form hosted in an attacker's website with hidden values , This form can be created by JavaScript Automatic triggering , It can also be by the victim ( Thought the form would perform other operations ) Trigger .
(3) Multi step transaction
Multi step trading is not enough to prevent CSRF, As long as an attacker can predict or infer every step of a complete transaction , Can be realized CSRF.
(4)URL rewrite
This may be seen as a useful CSRF Preventive techniques , Because the attacker cannot guess the victim's conversation ID, But the user's session ID stay URL China open , Therefore, it is not recommended to fix a security vulnerability by introducing another security vulnerability .
(5)HTTPS
HTTPS Itself cannot be lower than CSRF, however ,HTTPS Should be regarded as a prerequisite for the trustworthiness of any preventive measures . As long as the target website is not used https, Questions need to be raised on this point in the penetration test report .
5.2 Effective defense means
(1) verification Referer Field
according to HTTP agreement , stay HTTP In the head Referer, It records the time to HTTP The source address of the request . In general , The request to access a security restricted page must come from the website itself . because Referer Support client customization , Therefore, it can only be considered that the request not from the website itself is not credible , But not enough to think referer Is the website itself credible .
(2) add to Token verification
CSRF The attack was successful , It's because an attacker can fake a user's request , All user authentication information in the request exists in Cookie in , So the attacker can directly use the user's own Cookie To pass security verification . Thus we can see that , To resist CSRF The key to the attack is : In the request Add a randomly generated... In the form of a parameter token( Random string ), And establish an interceptor on the server side to verify the validity of all requests token, If not in the request token or token The content is not correct , Think it might be CSRF Attack and reject the request .
(3) Secondary verification
The second verification is in Provide the password or verification code of the current user before key operations such as transfer , This method can be used effectively CSRF attack .
(4) Users develop good internet habits
Develop good internet habits , Can greatly reduce CSRF The harm of the attack . for example , When users surf the Internet , Don't click on the Internet Forum easily 、 The chat room 、 Connections or pictures that appear in instant messaging tools or e-mail ; Exit the login account that has not been used for a long time in time , Especially system management , Try to click on links or pictures from unknown sources when logging out of the system . besides , Users also need to install appropriate security software on computers connected to the Internet , And update the feature library released by key manufacturers in time , To keep the security software tracking the latest attacks in real time .
6 summary
(1) understand CSRF The attack principle of ;
(2) Focus on mastering CSRF Three attack methods ;
(3) understand CSRF Hazards of ;
(4) Focus on mastering CSRF Our defense .
Reference article
边栏推荐
- Objective-C string class, array class
- Value transfer communication between components (parent to child, child to parent, brother component to value)
- Defensive programming skills
- Perf simple process for multithreaded profile
- functools下的reduce函数
- Introduction to asynchronous task capability of function calculation - task trigger de duplication
- Pytest multi process / multi thread execution test case
- Balance between picture performance of unity mobile game performance optimization spectrum and GPU pressure
- Msgraphmailbag - search only driveitems of file types
- 如何有效远程办公之我见 | 社区征文
猜你喜欢

I was tortured by my colleague's null pointer for a long time, and finally learned how to deal with null pointer
Two commonly used graphics can easily realize data display
指针数组和数组指针

干货!基于GAN的稀有样本生成

Storage of MySQL database

量子力学习题
02 ls 命令的具体实现

Sales management system of lightweight enterprises based on PHP
laravel admin里百度编辑器自定义路径和文件名
idea修改主体颜色
随机推荐
拼夕夕二面:说说布隆过滤器与布谷鸟过滤器?应用场景?我懵了。。
EV6 helps the product matrix, and Kia is making efforts in the high-end market. The global sales target in 2022 is 3.15 million?
Sales management system of lightweight enterprises based on PHP
[paddleseg source code reading] paddleseg calculation dice
Class summation, shortest row
Idea configuration 360zip open by default -- external tools
深入浅出对话系统——使用Transformer进行文本分类
渗透实战-SQLServer提权
I was tortured by my colleague's null pointer for a long time, and finally learned how to deal with null pointer
A review of reverse reinforcement learning at Virginia Tech (VT)
The maximum expiration time of client secret in azure ad application registration is modified to 2 years
How to dynamically cache components in Vue multi-level route nesting
用于TCP协议交互的TCPClientDemo
Typical applications of minimum spanning tree
Unity 绘制弹球和台球的运动轨迹
微信公众号网页授权
Katalon使用script实现查询List大小
基于PHP的轻量企业销售管理系统
Select sorting and bubble sorting template
Tcpclientdemo for TCP protocol interaction