当前位置:网站首页>Analysis: What makes the Nomad Bridge hack unique
Analysis: What makes the Nomad Bridge hack unique
2022-08-04 00:32:00 【chinadefi】
Analysis: What makes the Nomad Bridge hack unique

August 1, 2022, $190 million was siphoned from various assets of the Nomad Bridge.What's special about this breach is that it's the first hacking attack involving the active participation of the general public.
The Nomad Bridge hack was originally planned by a single person, but soon regular users were able to spot the bug that the original hacker exploited and exploit it by simply using Ctrl+C, Ctrl+V.
This article will delve into how this attack was made possible in the first place.
What is Nomad?
Nomad is a cross-chain bridge that allows users to transfer crypto assets between chains, but the transfer never actually happens.Nomad runs multiple smart contracts that burn assets on the original chain and mint assets on the new chain.This is why when we utilize cross-chain transfer of assets, we will have wETH instead of ETH.Wrapped Ether is a mirrored version of Ether that is compatible with other chains.
Analysis of the Nomad Hacker
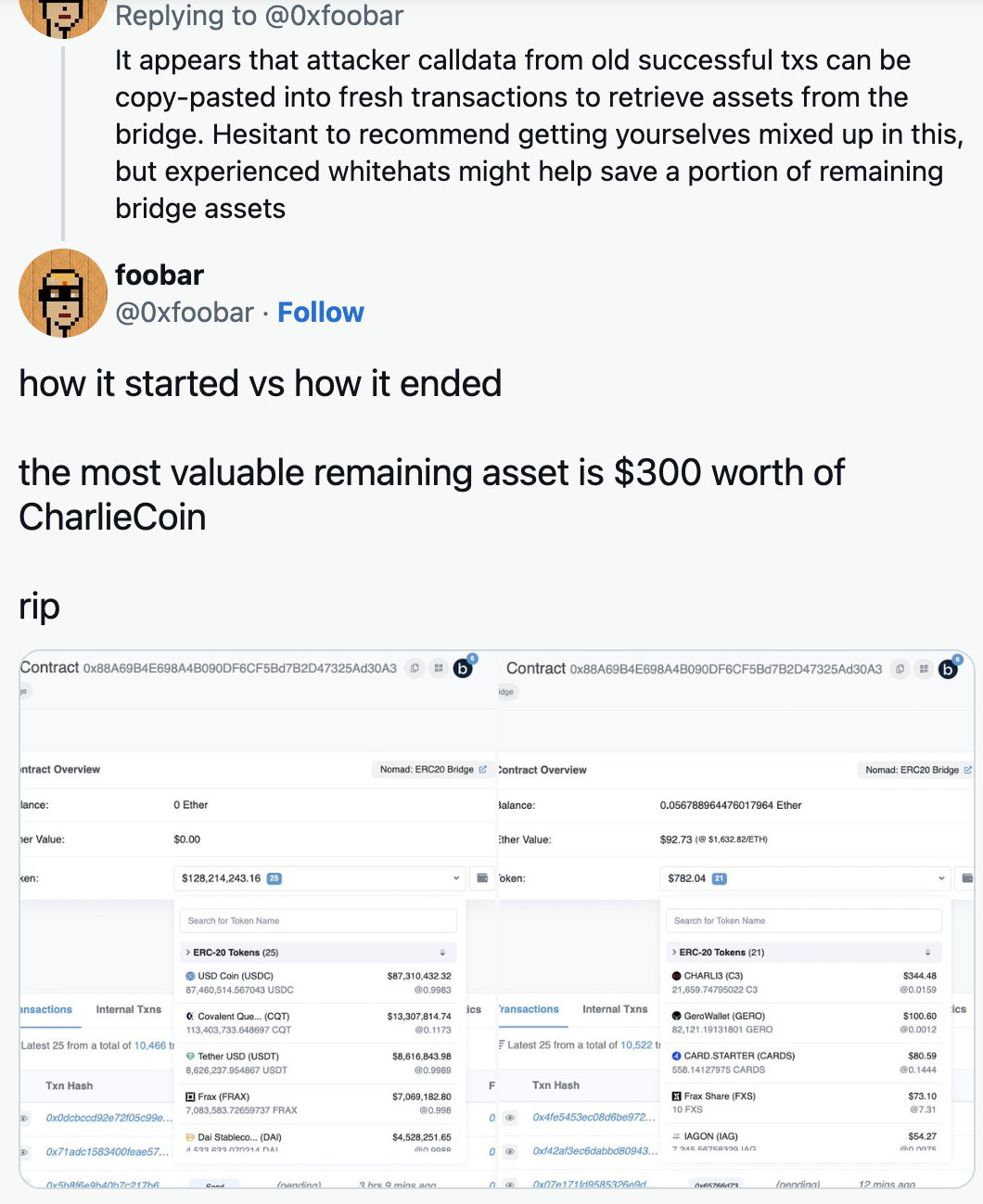
The hack happened the day before yesterday, and the attackers discovered and started exploiting a weakness.People quickly figured out what was being exploited and started copy-pasting exploits to suck assets from the Nomad bridge themselves.This effectively emptied Nomad's wallet - from $190 million to $700 in a matter of hours.
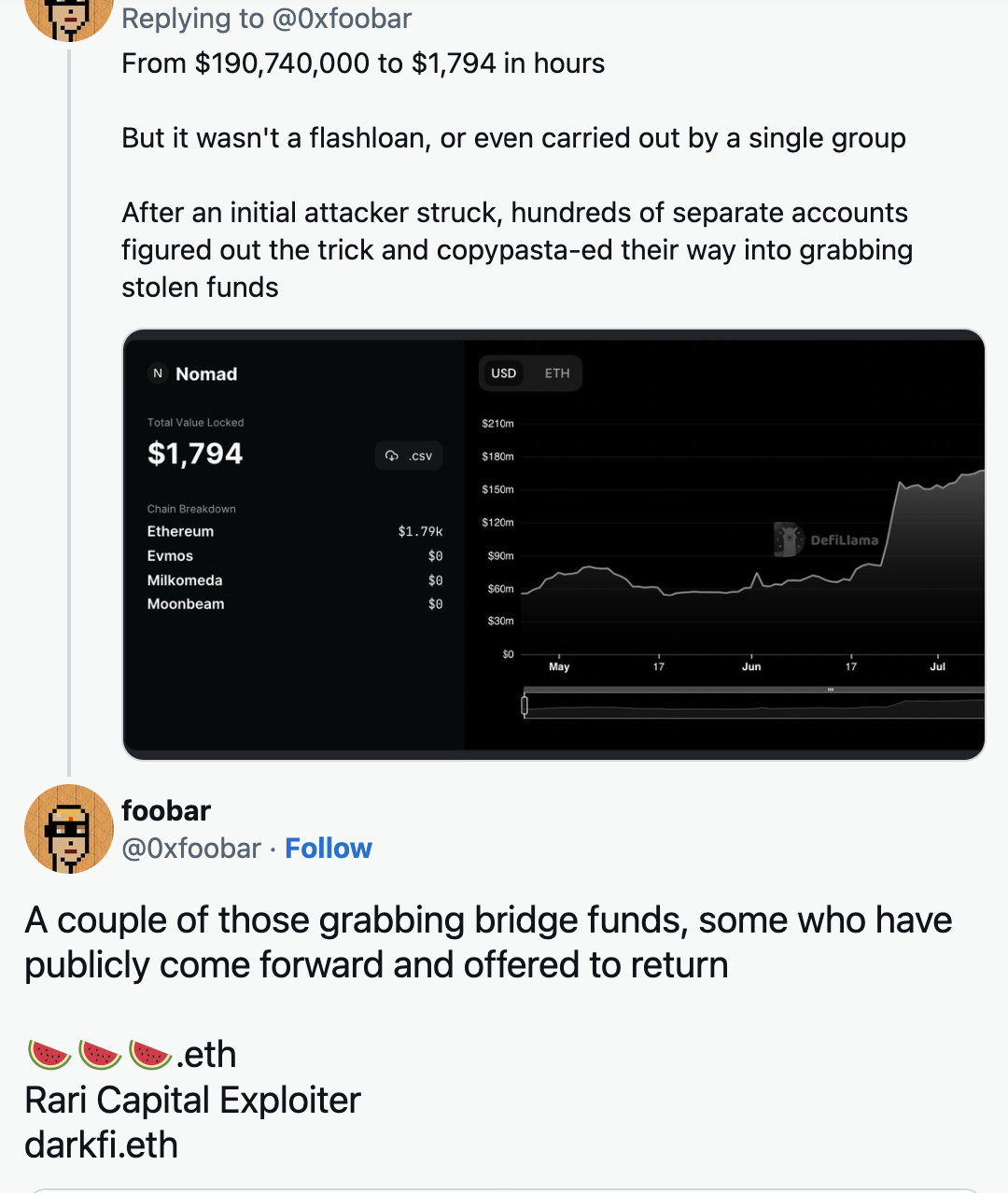
This unprecedented opportunistic attack is possible because it is so easy to replicate.To replicate the hacker, all we have to do is copy the hacker's transaction call data and replace the original address with our own.
What made the hack happen in the first place?
The vulnerability is caused by a bug in the nomad smart contract file Replica.sol.Furthermore, according to the audit report in the Nomad GitHub repository, this particular weakness has actually been flagged by the audit team and acknowledged by the team.
More specifically, the problem stems from the following process() function, on line 192 of the Replica.sol file:
require(acceptableRoot(messages[_messageHash]), "!proven");This line by itself is not inherently wrong, as it generally ensures that the request comes from a root that the smart contract considers acceptable.
require() is a built-in Solidity function that ensures that only authorized addresses can perform operations on a specific smart contract.Unfortunately, 41 days ago, the team made a mistake during the start of the contract merkle root, adding 0x00 as an acceptable root.This means that everyone's wallet address is an acceptable root for this contract and can successfully call various functions of the contract.
A poor merkle root initialization is the root cause of this problem.Once the vulnerability was discovered, it was very easy to replicate and people started siphoning money from Nomad.Some promised to return the money.
Source: https://cryptomaton.medium.com/the-great-nomad-bridge-hack-inside-the-first-decentralised-crowd-looting-event-98af2c5444f8
About
ChinaDeFi - ChinaDeFi.com is a research-driven DeFi innovation organization, and we are also a blockchain development team.Every day, from nearly 900 pieces of content from more than 500 high-quality information sources around the world, we look for more in-depth thinking and more systematic content, and synchronize to the Chinese market at the fastest speed to provide decision-making auxiliary materials.
Layer 2 Daoist - Blockchain technology enthusiasts and research analysts who are interested in Layer 2 are welcome to contact Gavin (WeChat: chinadefi) to discuss the landing opportunities brought by Layer 2.Stay tuned to our WeChat official account "Decentralized Finance Community".

边栏推荐
- The Beijing E-sports Metaverse Forum was successfully held
- XSS - Bypass for loop filtering
- C# WPF设备监控软件(经典)-下篇
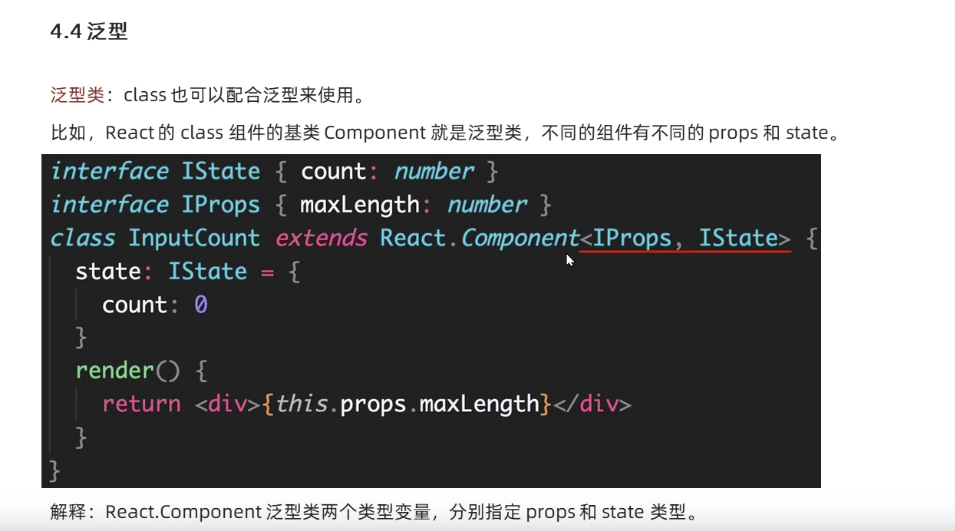
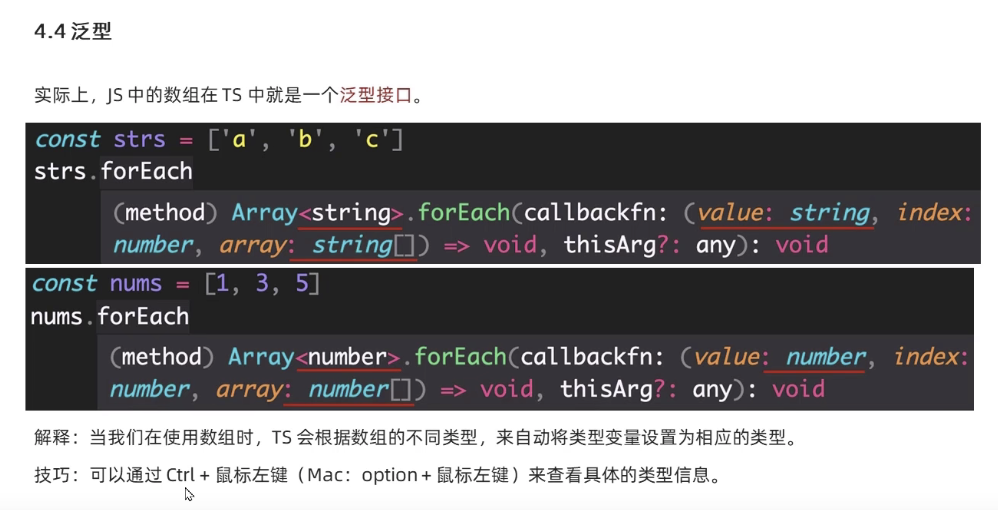
- typescript53-泛型约束
- BioVendor人Clara细胞蛋白(CC16)Elisa试剂盒检测步骤
- 智能管理PoE交换机
- 2022-08-03:以下go语言代码输出什么?A:2;B:3;C:1;D:0。 package main import “fmt“ func main() { slice := []i
- Salesforce's China business may see new changes, rumors may be closing
- 【面经】被虐了之后,我翻烂了equals源码,总结如下
- Spinnaker调用Jenkins API 返回403错误
猜你喜欢
随机推荐
【杂项】通过Excel为字符串产生条码
孙宇晨受邀参加36氪元宇宙峰会并发表主题演讲
卡尔曼滤波器KF
小身材有大作用——光模块基础知识(一)
2021年数据泄露成本报告解读
typescript55-泛型约束
免费的公共WiFi不要乱连,遭中间人攻击了吧?
小米--测试开发
nodeJs--async/await
fsdbDump用法
机器学习——库
第1章:初识数据库与MySQL----MySQL安装
YOLOv7改进之二十二:涨点神器——引入递归门控卷积(gnConv)
Sqlnet. Ora file with the connection of authentication test
轻量级网络整理及其在Yolov5上的实现
北京电竞元宇宙论坛活动顺利召开
七夕活动浪漫上线,别让网络拖慢和小姐姐的开黑时间
建木DevOps流程的快速运用
易动纷享--测试实习生视频面试
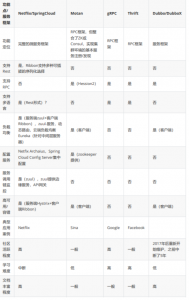
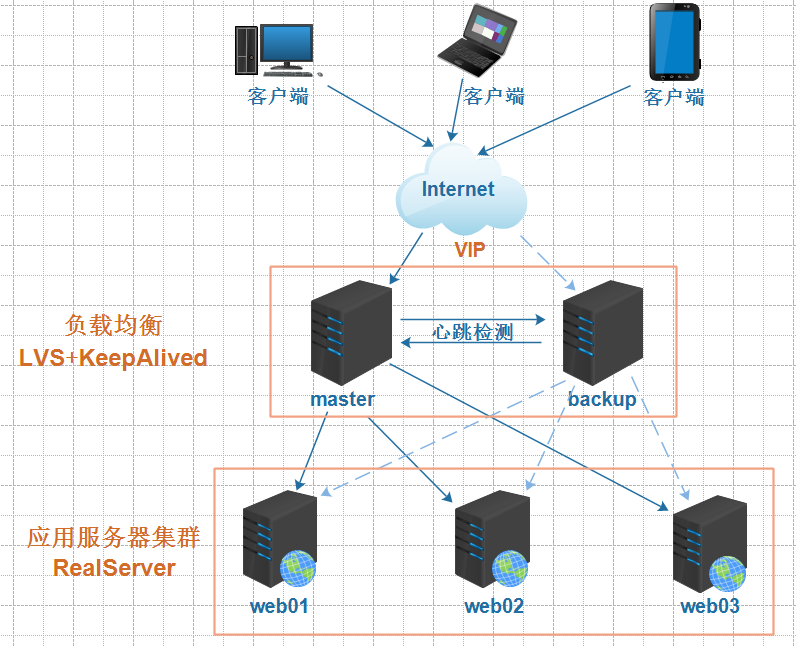
微服务的简单介绍