当前位置:网站首页>[hcie TAC] question 5-2
[hcie TAC] question 5-2
2022-06-29 08:15:00 【Heterogenesis】

Misplaced restore :
#AR30:
acl 2000
rule 5 deny 10.5.1.32 0
int g0/0/0
traffic-filter outbound acl 2000
One 、 Fault root cause judgment
AR32 Of loopback0 cannot access AR34 Of loopback 0 and g0/0/0 Address of the interface , The root cause is that AR30 Of g0/0/0 The outgoing direction of the interface is targeted at AR32loopback 0 Traffic filtering strategy of interface address .
Two 、 Fault analysis
2.1、 The fault phenomenon reappears , stay AR32 On the implementation ping -a 10.5.1.32 x.x.x.x ( among x.x.x.x yes ISIS All addresses of the zone ) command , It is found that some addresses are inaccessible , The inaccessible addresses are as follows :
<AR32>ping -a 10.5.1.32 10.5.1.34
PING 10.5.1.34: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
--- 10.5.1.34 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
------------------------------------------------------------------------------------
<AR32>ping -a 10.5.1.32 10.5.34.34
PING 10.5.34.34: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
--- 10.5.34.34 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
……
Omit can ping My address
From the output results , unable ping The address of Tong is AR34 Of loopback0 and g0/0/0 Interface ,IP The addresses are 10.5.1.34、10.5.34.34, Need to view AR32 Whether there is corresponding routing information in the routing table of .
2.2、 stay AR32 On the implementation display ip routing-table command , see AR32 Routing table information for , The output is as follows :
<AR32>display ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 21 Routes : 21
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.5.1.27/32 OSPF 10 2 D 10.5.239.28 GigabitEthernet0/0/0
10.5.1.28/32 OSPF 10 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.1.29/32 OSPF 10 2 D 10.5.239.28 GigabitEthernet0/0/0
10.5.1.30/32 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.1.31/32 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.1.32/32 Direct 0 0 D 127.0.0.1 LoopBack0
10.5.1.33/32 OSPF 10 3 D 10.5.239.28 GigabitEthernet0/0/0
10.5.1.34/32 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.14.0/24 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.34.0/24 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.40.0/24 OSPF 10 3 D 10.5.239.28 GigabitEthernet0/0/0
10.5.128.0/24 OSPF 10 2 D 10.5.239.28 GigabitEthernet0/0/0
10.5.129.0/24 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.130.0/24 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.239.0/24 Direct 0 0 D 10.5.239.32 GigabitEthernet0/0/0
10.5.239.32/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/0
10.5.239.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/0
From the output results ,AR32 In the routing table of ISIS All routes of the zone , explain AR28 Admiral ISIS The process is introduced into OSPF In progress . Need to view ISIS Whether the routing table of the area device exists OSPF Area routing , To judge AR28 On OSPF Whether the process is introduced into ISIS In progress .
2.3、 stay AR31 and AR34 On the implementation display ip routing-table command , see AR31 and AR34 Routing table information for , The output is as follows :
<AR31>dis ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 23 Routes : 23
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.5.1.27/32 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.1.28/32 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.1.29/32 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.1.30/32 ISIS-L1 15 20 D 10.5.14.34 GigabitEthernet0/0/1
10.5.1.31/32 Direct 0 0 D 127.0.0.1 LoopBack0
10.5.1.32/32 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.1.33/32 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.1.34/32 ISIS-L1 15 10 D 10.5.14.34 GigabitEthernet0/0/1
10.5.14.0/24 Direct 0 0 D 10.5.14.31 GigabitEthernet0/0/1
10.5.14.31/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/1
10.5.14.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/1
10.5.34.0/24 ISIS-L1 15 20 D 10.5.14.34 GigabitEthernet0/0/1
10.5.40.0/24 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.128.0/24 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.129.0/24 ISIS-L1 15 30 D 10.5.14.34 GigabitEthernet0/0/1
10.5.130.0/24 Direct 0 0 D 10.5.130.31 GigabitEthernet0/0/2
10.5.130.31/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/2
10.5.130.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/2
10.5.239.0/24 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
=====================================================================
<AR34>display ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 16 Routes : 17
Destination/Mask Proto Pre Cost Flags NextHop Interface
0.0.0.0/0 ISIS-L1 15 10 D 10.5.14.31 GigabitEthernet0/0/1
ISIS-L1 15 10 D 10.5.34.30 GigabitEthernet0/0/0
10.5.1.30/32 ISIS-L1 15 10 D 10.5.34.30 GigabitEthernet0/0/0
10.5.1.31/32 ISIS-L1 15 10 D 10.5.14.31 GigabitEthernet0/0/1
10.5.1.34/32 Direct 0 0 D 127.0.0.1 LoopBack0
10.5.14.0/24 Direct 0 0 D 10.5.14.34 GigabitEthernet0/0/1
10.5.14.34/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/1
10.5.14.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/1
10.5.34.0/24 Direct 0 0 D 10.5.34.34 GigabitEthernet0/0/0
10.5.34.34/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/0
10.5.34.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/0
10.5.129.0/24 ISIS-L1 15 20 D 10.5.34.30 GigabitEthernet0/0/0
10.5.130.0/24 ISIS-L1 15 20 D 10.5.14.31 GigabitEthernet0/0/1
From the output results ,AR31 In the routing table of OSPF All routes of the zone ,AR34 There are two default routes on , The next jump points to AR30 and AR31 , explain AR28 Admiral OSPF The process is introduced into ISIS In progress . Both processes have all the routes in the other region , It indicates that the whole network route can reach , There is no route filtering policy . The preliminary judgment may be AR28、AR30、AR31、AR32、AR34 There is a traffic filtering policy on , because AR28 and AR30 Login permission exists and cannot be accessed , So check out AR31、AR32、AR34 Whether there is a traffic filtering policy on .
2.4、 stay AR31、AR32、AR34 On the implementation of separate display acl all、display traffic-filter applied-record、display traffic-policy applied-record command , Check to see if there are any filtering strategies that can lead to failure , The output is as follows
……
Omit the output
From the output results ,AR31、AR32、AR34 There is no traffic filtering strategy that can cause this fault phenomenon . The judgment may be AR28 or AR31 There is a traffic filtering policy on . Due to the problem of login permission , So you need to be in AR32 Upper use tracert Command to test indirectly .
2.5、 stay AR32 On the implementation tracert -a 10.5.1.32 10.5.1.34 and tracert 10.5.1.34 command , Test whether there is a traffic filtering strategy on the delivery path of traffic , The output is as follows :
<AR32>tracert -a 10.5.1.32 10.5.1.34
traceroute to 10.5.1.34(10.5.1.34), max hops: 30 ,packet length: 40,press CTRL_C to break
1 10.5.239.28 30 ms 20 ms 10 ms
2 10.5.130.31 40 ms 10.5.129.30 30 ms 10.5.130.31 30 ms
3 * 10.5.14.34 70 ms *
============================================================================================
<AR32>tracert 10.5.1.34
traceroute to 10.5.1.34(10.5.1.34), max hops: 30 ,packet length: 40,press CTRL_C to break
1 10.5.239.28 30 ms 20 ms 10 ms
2 10.5.130.31 50 ms 10.5.129.30 20 ms 10.5.130.31 1 ms
3 10.5.34.34 40 ms 10.5.14.34 20 ms 10.5.34.34 20 ms
From the output results , stay AR32 In order to loopback0 The interface address is the source address tracert When testing , The flow can pass normally AR28, But through AR30 Packet loss occurs after , The traffic can not arrive smoothly AR34. stay AR32 Do not carry the source address on the tracert When testing , The traffic can arrive smoothly AR34, No packet loss . explain AR30 Of g 0/0/0 There is a traffic filtering policy on the interface , But it is impossible to judge the direction of policy application , Need to be used in the opposite direction tracert Command to determine the direction of policy application .
2.6、 stay AR34 On the implementation tracert -a 10.5.1.34 10.5.1.32 and tracert -a 10.5.34.34 10.5.1.32 command , Determine the direction of policy application , The output is as follows :
<AR34>tracert -a 10.5.1.34 10.5.1.32
traceroute to 10.5.1.32(10.5.1.32), max hops: 30 ,packet length: 40,press CTRL_C to break
1 10.5.34.30 60 ms 20 ms 20 ms
2 10.5.129.28 10 ms 30 ms 10.5.130.28 20 ms
3 10.5.239.32 40 ms 20 ms 20 ms
=====================================================================
<AR34>tracert -a 10.5.34.34 10.5.1.32
traceroute to 10.5.1.32(10.5.1.32), max hops: 30 ,packet length: 40,press CTRL_C to break
1 10.5.34.30 60 ms 20 ms 20 ms
2 10.5.129.28 10 ms 30 ms 10.5.130.28 20 ms
3 10.5.239.32 40 ms 20 ms 20 ms
From the output results ,AR34 With loopbck0 and g0/0/0 The interface address is reversed to the source address tracert When testing , The traffic can arrive smoothly AR32, No packet loss , explain AR34 To AR32 There is no traffic filtering strategy in the direction of .
in summary :AR32 In order to loopback0 For the source tracert When testing , The packet can pass smoothly AR28 But through AR30 Packet loss occurs after , explain AR30 There is a target on AR32loopback0 Traffic filtering strategy of interface address . stay AR34 With loopback0 and g0/0/0 The interface address is reversed for the source tracert When testing , Packets can arrive smoothly AR32, Description in AR34 To AR32 There is no traffic filtering on the path of .
Conclusion :AR32loopback 0 The interface address cannot be accessed AR34 loopback 0 Interface address The root cause is that AR30 Of g0/0/0 There is a problem in the outgoing direction of the interface AR32 loopback 0 Traffic filtering strategy of interface address .
3、 ... and 、 Fault handling
3.1、AR30 Of g0/0/0 There is a traffic filtering strategy in the outgoing direction of the interface , The following commands need to be executed :
display traffic-filter applied-record # View traffic filtering
display traffic-policy applied-record # View traffic policy
system-view # Enter the system view
int g0/0/0 # Enter the interface view
undo traffic-filter outbound # Delete traffic filtering
undo traffic-policy outbound # Delete traffic policy
After the execution of the above order AR32 Execute the following command on to test whether the fault has been resolved :
ping -a 10.51.32 10.5.1.34 # test AR32 and AR34 loopback0 Connectivity of interfaces
ping -a 10.1.32 10.5.34.34 # test AR32 loopback0 and AR34 g0/0/0 Connectivity of interfaces
3.2、 Other high possibilities ——AR30 I made advanced ACL Filter , Need to be in AR30 Execute the following command on :
display acll all # View all ACL
system-view # Enter the system view
undo acl { senior ACL Serial number } # Delete ACL
After the execution of the above order AR32 Execute the following command on to test whether the fault has been resolved :
ping -a 10.51.32 10.5.1.34 # test AR32 and AR34 loopback0 Connectivity of interfaces
ping -a 10.1.32 10.5.34.34 # test AR32 loopback0 and AR34 g0/0/0 Connectivity of interfaces
3.3、quit # Push to system view
save # Save configuration
If after executing the above command , The problem is still unresolved , It is necessary to send front-line engineers to the site for troubleshooting , Or provide complete equipment configuration , And call Huawei 400 Hotline , Ask Huawei experts for remote assistance .
边栏推荐
- A review of visual SLAM methods for autonomous driving vehicles
- Mongodb- connect to the database using the mongo/mongosh command line
- 笔记本电脑快速连接手机热点的方法
- 关于SQL语句的大小写
- 《动手学深度学习》(一)-- 线性神经网络
- AC automata
- Basic syntax - bit operation
- Simulation time and bag operation in ROS
- 马赛克笔记
- Django - installing mysqlclient error: mysqlclient 1.4.0 or newer is required; you have 0.9.3
猜你喜欢
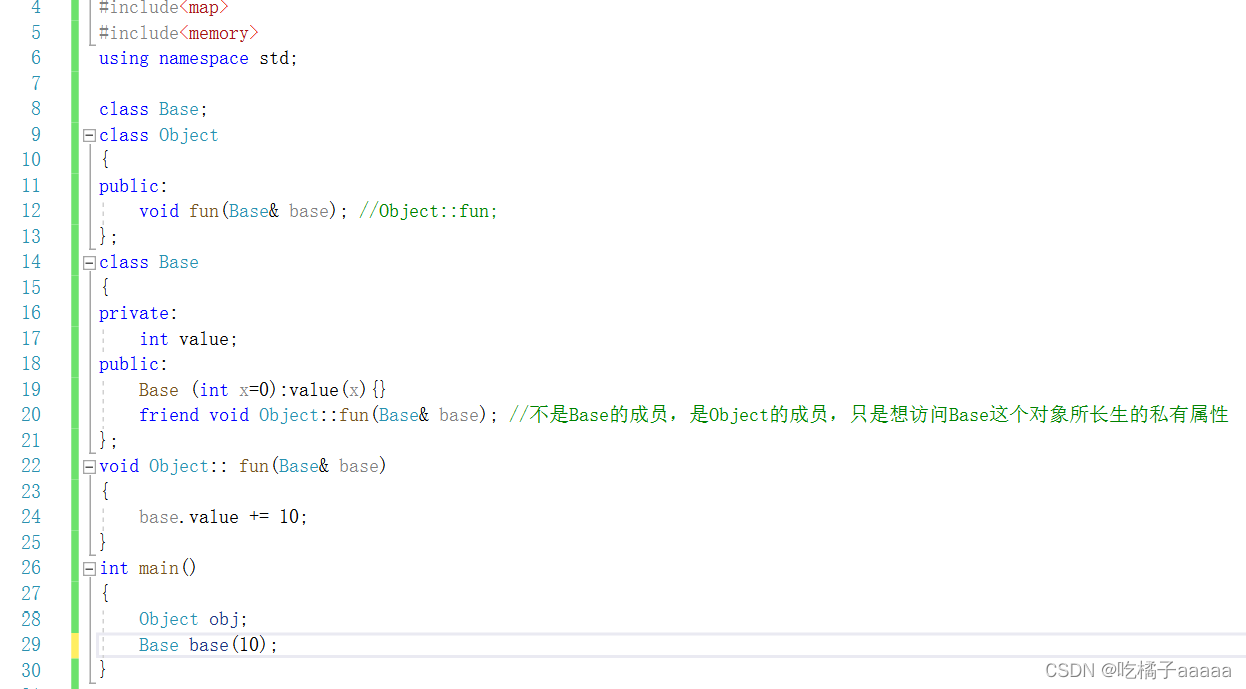
Friends, static keywords, static methods, and relationships between objects

Introduction to taro

AC automata
产品经理应该学习墨刀还是Axure?

蓝图基础
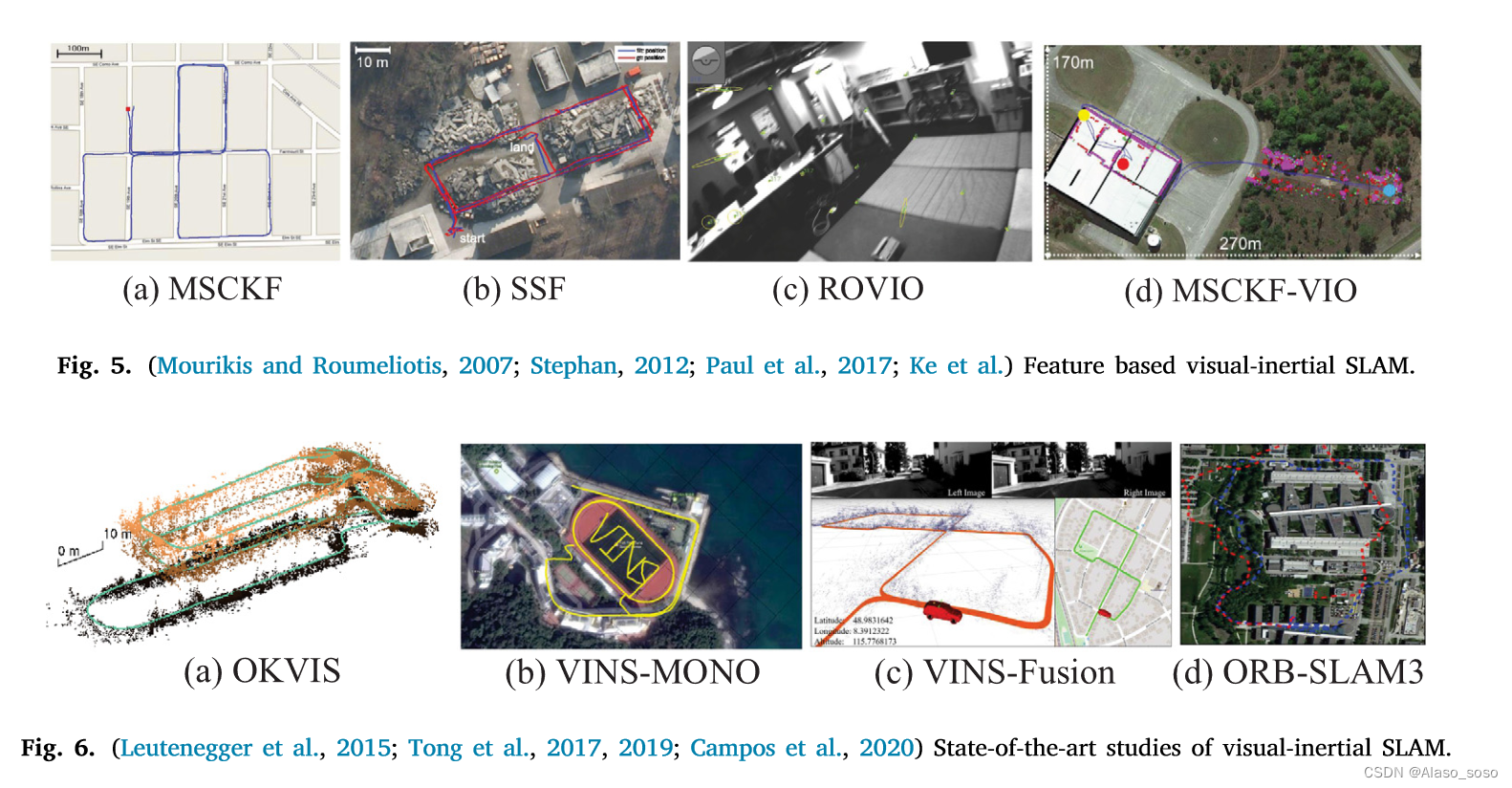
A review of visual SLAM methods for autonomous driving vehicles
Un voyage profond d'IA dans Huawei Cloud

Code:: blocks code formatting shortcuts

【修复收藏功能、更新登录接口】知识付费小程序、博客小程序、完整版开源源码、资源变现小程序,带299整站资源数据

Taro 介绍
随机推荐
How to share the virtual environment of pycharm to jupyter Lab
消息中间件:pulsar
SizeBalanceTree
MySQL statistics by day / week / month / quarter / half year / year
Line features & surface features of vSLAM features
What are the constraints in MySQL? (instance verification)
jsp学习部分
Protobuf binary file learning and parsing
华为云的AI深潜之旅
Indextree and Application
VSLAM特征之线特征&面特征
蓝图基础
IndexTree以及应用
SQL Server enable CDC
Improvement direction of programming ability
[eye of depth Wu Enda's fourth operation class] summary of multiple linear regression with multiple variables
Blueprint basis
Hook 简介
Why are two SQL statements that execute very fast, especially after the Union
AI and the meta universe sparked a spark: human beings lost only shackles and gained all-round liberation