当前位置:网站首页>Hcip/hcie Routing & Switching / datacom Reference Dictionary Series (19) comprehensive summary of PKI knowledge points (public key infrastructure)
Hcip/hcie Routing & Switching / datacom Reference Dictionary Series (19) comprehensive summary of PKI knowledge points (public key infrastructure)
2022-06-28 00:16:00 【skawngury】
Catalog
One 、PKI brief introduction
PKI Public Key Infrastructure Public key infrastructure

CIA Model
Confidentiality Confidentiality
Integrity integrity
Availability Usability
Two 、Confidentiality Confidential technology
Introduction to encryption technology
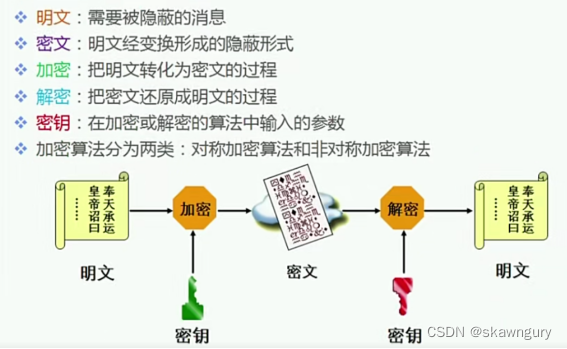
3、 ... and 、 Encryption technology classification According to the usage of the key
1 Symmetric encryption ( Shared key encryption )
Encryption and decryption use the same key
characteristic : Fast Compact ciphertext Key management is complex For the transmission of large amounts of data 


2 Asymmetric encryption ( Public key encryption )
encryption Decryption uses a different key ( Public key Private key )
characteristic : Slow speed The ciphertext is not compact Key management is simple Usually only used for digital signature

Public key encryption Private key decryption
Private key encryption Public key decryption 

Four 、 The combination of two encryption algorithms
In practical use Communication parties usually use public key cryptography to exchange key materials
Both parties finally calculate the key Using symmetric cryptography to encrypt the actual data
Combination of the two Ensure encryption speed and security
Public key cryptosystem - Asymmetric cryptosystem - Exchange key material
Slow speed The ciphertext is not compact Key management is simple Usually only used for digital signature
Shared cryptosystem - Symmetric cryptosystem - Encrypt actual data
Fast Compact ciphertext Key management is complex For the transmission of large amounts of data

A Use the key material B Public key encryption then B use B Private key decryption of Get the material
A Then encrypt the plaintext with the key material B Decrypt the plaintext with the decrypted key material
But there are still problems
A How to confirm that the public key obtained is B Of ?
How to ensure that data is not destroyed in the transmission process ?
边栏推荐
- Systematic learning + active exploration is the most comfortable way to get started!
- 安全省油环保 骆驼AGM启停电池魅力十足
- SQL reported an unusual error, which confused the new interns
- 互联网的发展为产业的变革和转型提供了新的解决方案
- Cornernet understands from simple to profound
- 零基础自学SQL课程 | CASE函数
- ASP.NET仓库进销存ERP管理系统源码 ERP小程序源码
- Golang uses Mongo driver operation -- Query (array related)
- VirtualBox extended dynamic disk size pit
- Promise是什么
猜你喜欢

智慧风电 | 图扑软件数字孪生风机设备,3D 可视化智能运维

现代编程语言:zig

Arduino UNO通过电容的直接检测实现简易触摸开关

零基础自学SQL课程 | IF函数
![[PCL self study: pclplotter] pclplotter draws data analysis chart](/img/ca/db68d5fae392c7976bfc93d2107509.png)
[PCL self study: pclplotter] pclplotter draws data analysis chart

Safe, fuel-efficient and environment-friendly camel AGM start stop battery is full of charm

【无标题】

An analysis of C language functions
本地可视化工具连接阿里云centOS服务器的redis

【论文阅读|深读】SDNE:Structural Deep Network Embedding
随机推荐
Although the TCGA database has 33 cancers
Storage structure of graph
什么是cookie,以及v-htm的安全性隐患
[try to hack] kill evaluation
Pytorch Foundation (1)
Deployment and test of crtmp live video server
A summer party
PAT乙级1013
互联网业衍生出来了新的技术,新的模式,新的产业类型
[PCL self study: pclplotter] pclplotter draws data analysis chart
炼金术(8): 开发和发布的并行
Sécurité, économie de carburant et protection de l'environnement chameau
Eliminate gaps around El image images
夏日的晚会
软件工程作业设计(1): [个人项目] 实现一个日志查看页面
Is it safe for Huatai Securities to open an account online?
Are the registered accounts of the top ten securities companies safe and risky?
Pat class B 1013
Thread pool implementation: semaphores can also be understood as small waiting queues
Smart wind power | Tupu software digital twin wind turbine equipment, 3D visual intelligent operation and maintenance