当前位置:网站首页>Explain JMM in detail
Explain JMM in detail
2022-07-01 22:55:00 【Keyboard singer】
One 、 Computer hardware storage system
CPU Run is not a direct operation of memory, but first read the data in memory to the cache , And memory read and write operations will cause inconsistencies .JVM An attempt was made in the specification to define a Java Memory model (java Memory Model, abbreviation JMM) To screen out the memory access differences between various hardware and operating systems , In order to make Java The program can achieve consistent memory access effect under various platforms .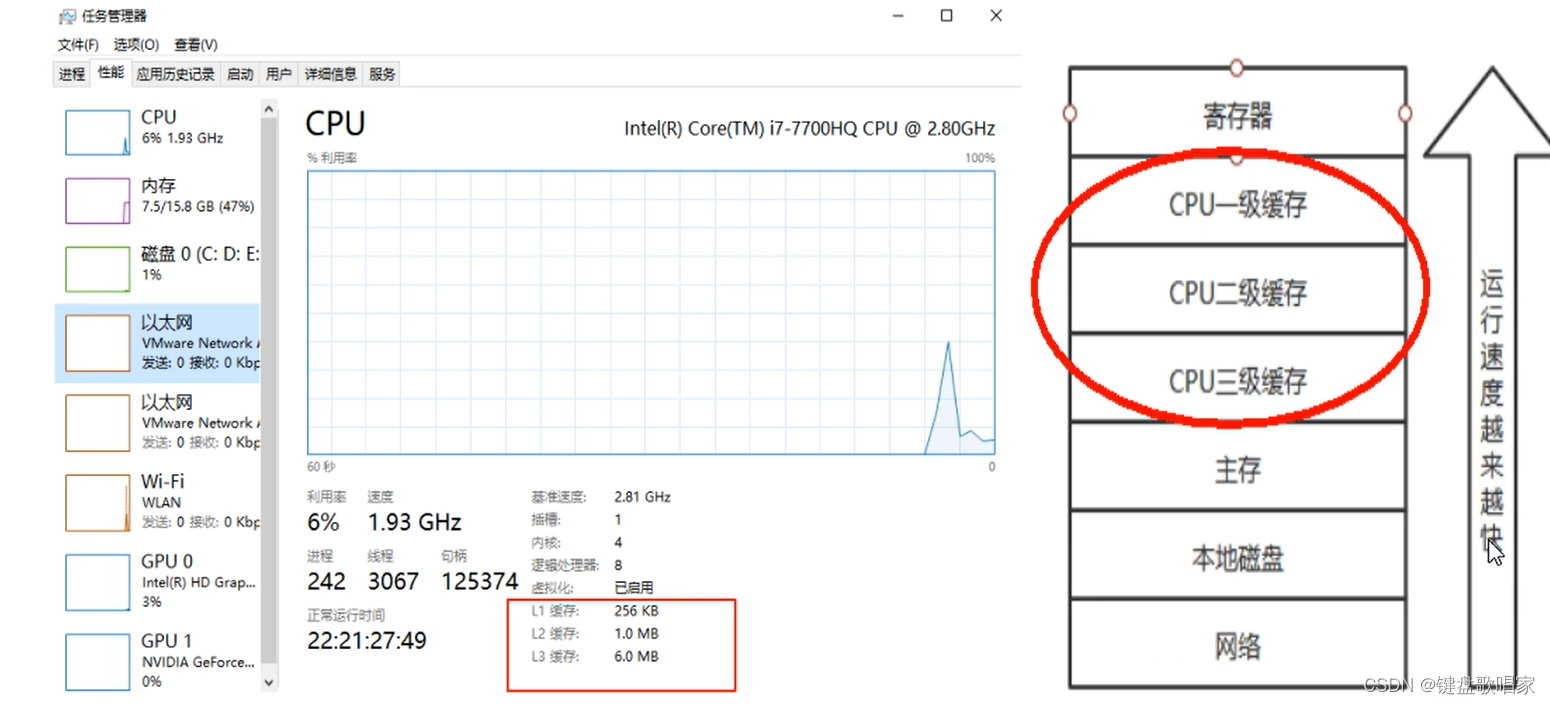
Two 、 brief introduction
1.JMM brief introduction
JMM(Java Memory model Java Memory Model, abbreviation JMM) It is an abstract concept and does not really exist. It only describes a set of conventions or specifications , Through this set of specifications, the... In the program is defined ( Especially multithreading ) The read-write access mode of each variable and determines when and how a thread's writing to a shared variable becomes visible to another thread , The key technical points are around the atomicity of multithreading 、 Visibility and order unfold .
principle :JMM The key technology points are all around the atomicity of multithreading 、 Visibility and order unfold . It works as follows :
1. adopt JMM To realize the abstract relationship between thread and main memory .
2. Shield the memory access differences of various hardware platforms and operating systems to achieve Java The program can achieve consistent memory access effect under various platforms .
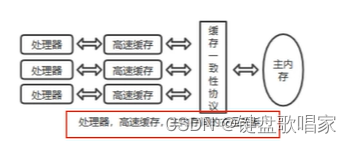
2. The concept of cache rows
A multi-core cpu Each core of has its own L2 cache , All cores share a L3 cache . When the data in the main memory is written to the cache , It will also write in the nearby data by the way . This write range is called a cache row ( size 64 byte &#
边栏推荐
- SAP GUI 里的收藏夹事务码管理工具
- Explain kubernetes network model in detail
- 业务可视化-让你的流程图'Run'起来
- Cutefishos system~
- ECMAScript 2022 正式发布,有你了解过的吗?
- el-input文本域字数限制,超过显示变红并禁止输入
- twenty million two hundred and twenty thousand seven hundred and one
- 友善串口助手使用教程_友善串口调试助手怎么进行配置-友善串口调试助手使用教程…
- LC501. Mode in binary search tree
- Genicam gentl standard ver1.5 (4) Chapter 5 acquisition engine
猜你喜欢
转--原来gdb的底层调试原理这么简单

每日刷题记录 (十)

SAP GUI 里的收藏夹事务码管理工具

“信任机器”为发展赋能

Appium automated testing foundation - Supplement: introduction to desired capabilities parameters

Intelligent computing architecture design of Internet

Demo program implementation of QT version Huarui camera

思科考试--路由的概念和配置考试
Deadlock handling strategies - prevent deadlock, avoid deadlock, detect and remove deadlock

internal field separator
随机推荐
转--原来gdb的底层调试原理这么简单
SAP 智能机器人流程自动化(iRPA)解决方案分享
104. SAP UI5 表格控件的支持复选(Multi-Select)以及如何用代码一次选中多个表格行项目
Friendly serial assistant tutorial_ How to configure friendly serial port debugging assistant - tutorial on using friendly serial port debugging assistant
El input text field word limit, beyond which the display turns red and input is prohibited
分享一个一年经历两次裁员的程序员的一些感触
The fixed assets management subsystem reports are divided into what categories and which accounts are included
Vsphere+ and vsan+ are coming! VMware hybrid cloud focus: native, fast migration, mixed load
SAP GUI 里的收藏夹事务码管理工具
友善串口助手使用教程_友善串口调试助手怎么进行配置-友善串口调试助手使用教程…
Selection of all-optical technology in the park - Part 2
Pytorch nn.functional.unfold()的简单理解与用法
阿洛迷茫后的思考
【扫盲】机器学习图像处理中的深层/浅层、局部/全局特征
下班前几分钟,我弄清了v-model与.sync的区别
447-哔哩哔哩面经1
The principle, testing and Countermeasures of malicious software reverse closing EDR
Operation category read is not supported in state standby
MySQL view exercise
What class loading mechanisms does the JVM have?