当前位置:网站首页>What you don't know about traifik
What you don't know about traifik
2022-06-24 01:24:00 【Luga Lee】
In the previous post , We briefly introduced about Traefik Related concepts and component principle mechanism , For details, please refer to : Why choose Traefik Ingress ?
As an innovative edge router , signify Traefik It is the guardian of the whole application platform , Intercept and route every access request : Based on the set logic and rules , To determine which services handle the corresponding request . About Traefik Model portrait of , For details, please refer to the following :
Of course , In addition to the service proxy characteristics , Traefik Also have “ Service discovery ” Functional mechanism , It dynamically detects back-end service status information and updates routing rules in real time , So as to achieve the effect of service governance .
We use Docker Provider The scene serves as a reference model for Traefik A brief analysis of Ecology , So that we can understand Traefik Related features .
In the following scenario , We are based on the latest version of Traefik v2.5.2 Image as an example , Deploy and run related instances , The details are as follows :
[[email protected] ~] % vi docker-compose.yaml version: '3' services: reverse-proxy: image: traefik:latest # Turn on web UI also Traefik monitor Docker command: --api.insecure=true --providers.docker ports: # HTTP port - "80:80" # Web UI port ( adopt --api.insecure=true Enable ) - "8080:8080" volumes: # Traefik monitor Docker event - /var/run/docker.sock:/var/run/docker.sock
then , We run this instance , As follows :
[[email protected] ~] % docker-compose up -d reverse-proxy
[[email protected] ~] % curl -i http://192.168.56.114:8080/api/rawdata?jsonHTTP/1.1 200 OKContent-Type: application/jsonDate: Thu, 09 Sep 2021 02:05:08 GMTContent-Length: 1361 HTTP/1.1 200 OK Content-Type: application/json Date: Thu, 09 Sep 2021 02:05:08 GMT Content-Length: 1361 {"routers":{"[email protected]":{"entryPoints":["traefik"],"service":"[email protected]","rule":"PathPrefix(`/api`)","priority":2147483646,"status":"enabled","using":["traefik"]},"[email protected]":{"entryPoints":["traefik"],"middlewares":["[email protected]","[email protected]"],"service":"[email protected]","rule":"PathPrefix(`/`)","priority":2147483645,"status":"enabled","using":["traefik"]},"[email protected]":{"entryPoints":["http"],"service":"reverse-proxy-traefik","rule":"Host(`reverse-proxy-traefik`)","status":"enabled","using":["http"]}},"middlewares":{"[email protected]":{"redirectRegex":{"regex":"^(http:\\/\\/(\\[[\\w:.]+\\]|[\\w\\._-]+)(:\\d+)?)\\/$","replacement":"${1}/dashboard/","permanent":true},"status":"enabled","usedBy":["[email protected]"]},"[email protected]":{"stripPrefix":{"prefixes":["/dashboard/","/dashboard"]},"status":"enabled","usedBy":["[email protected]"]}},"services":{"[email protected]":{"status":"enabled","usedBy":["[email protected]"]},"[email protected]":{"status":"enabled","usedBy":["[email protected]"]},"[email protected]":{"status":"enabled"},"[email protected]":{"loadBalancer":{"servers":[{"url":"http://172.20.0.2:80"}],"passHostHeader":true},"status":"enabled","usedBy":["[email protected]"],"serverStatus":{"http://172.20.0.2:80":"UP"}}}}
here , We can also access... Through the browser http://192.168.56.114:8080/api/rawdata Interface to view Traefik Of API Raw data .
Next , We deploy a Demo service , be based on Traefik Create a route , The details are as follows :
version: '3'
services:
reverse-proxy:
# Official Traefik 2.0 Docker Mirror image
image: traefik:latest
# Turn on web UI And tell Traefik monitor Docker
command: --api.insecure=true --providers.docker
ports:
# HTTP port
- "80:80"
# Web UI port ( adopt --api.insecure=true Enable )
- "8080:8080"
volumes:
# such Traefik Can monitor Docker event
- /var/run/docker.sock:/var/run/docker.sock
whoami:
# One passes API Expose it IP Address container
image: containous/whoami
labels:
- "traefik.http.routers.whoami.rule=Host(`whoami.docker.localhost`)"Based on the above Yaml In file , We defined A name is whoami ordinary web service , This service will print information about the deployed machine (IP Address 、 Host and so on ). Then we use the following command to start whoami service , Specifically :
[[email protected] ~] % docker-compose up -d whoami
here , We ask again Api Interface , The results are shown below :
[[email protected] ~] % curl -i http://192.168.56.114:8080/api/rawdata?jsonHTTP/1.1 200 OKContent-Type: application/jsonDate: Thu, 09 Sep 2021 02:09:25 GMTContent-Length: 1705 HTTP/1.1 200 OK Content-Type: application/json Date: Thu, 09 Sep 2021 02:09:25 GMT Content-Length: 1705 {"routers":{"[email protected]":{"entryPoints":["traefik"],"service":"[email protected]","rule":"PathPrefix(`/api`)","priority":2147483646,"status":"enabled","using":["traefik"]},"[email protected]":{"entryPoints":["traefik"],"middlewares":["[email protected]","[email protected]"],"service":"[email protected]","rule":"PathPrefix(`/`)","priority":2147483645,"status":"enabled","using":["traefik"]},"[email protected]":{"entryPoints":["http"],"service":"reverse-proxy-traefik","rule":"Host(`reverse-proxy-traefik`)","status":"enabled","using":["http"]},"[email protected]":{"entryPoints":["http"],"service":"whoami-traefik","rule":"Host(`whoami.docker.localhost`)","status":"enabled","using":["http"]}},"middlewares":{"[email protected]":{"redirectRegex":{"regex":"^(http:\\/\\/(\\[[\\w:.]+\\]|[\\w\\._-]+)(:\\d+)?)\\/$","replacement":"${1}/dashboard/","permanent":true},"status":"enabled","usedBy":["[email protected]"]},"[email protected]":{"stripPrefix":{"prefixes":["/dashboard/","/dashboard"]},"status":"enabled","usedBy":["[email protected]"]}},"services":{"[email protected]":{"status":"enabled","usedBy":["[email protected]"]},"[email protected]":{"status":"enabled","usedBy":["[email protected]"]},"[email protected]":{"status":"enabled"},"[email protected]":{"loadBalancer":{"servers":[{"url":"http://172.20.0.2:80"}],"passHostHeader":true},"status":"enabled","usedBy":["[email protected]"],"serverStatus":{"http://172.20.0.2:80":"UP"}},"[email protected]":{"loadBalancer":{"servers":[{"url":"http://172.20.0.3:80"}],"passHostHeader":true},"status":"enabled","usedBy":["[email protected]"],"serverStatus":{"http://172.20.0.3:80":"UP"}}}}
By looking at /api/rawdata The data returned by the interface , We found that Traefik The new container has been automatically detected and the corresponding configuration has been updated . I'm going to introduce Traefik When , We said , When Traefik When a new service is detected , It will automatically create the corresponding route , Then we can access the corresponding route . here , We use Curl Tools to verify , The details are as follows :
[[email protected] ~] % curl -H Host:whoami.docker.localhost http://127.0.0.1 Hostname: d1078dbb0332 IP: 127.0.0.1 IP: 172.20.0.3 RemoteAddr: 172.20.0.2:37580 GET / HTTP/1.1 Host: whoami.docker.localhost User-Agent: curl/7.29.0 Accept: */* Accept-Encoding: gzip X-Forwarded-For: 172.20.0.1 X-Forwarded-Host: whoami.docker.localhost X-Forwarded-Port: 80 X-Forwarded-Proto: http X-Forwarded-Server: 814dfa472b98 X-Real-Ip: 172.20.0.1
Next , We are right. whoami Service expansion , To verify Traefik Load balancing function of , The specific operation is shown below :
[[email protected] ~] % docker-compose up -d --scale whoami=4 traefik_reverse-proxy_1 is up-to-date Creating traefik_whoami_2 ... done Creating traefik_whoami_3 ... done Creating traefik_whoami_4 ... done
here , Let's take a look at the container status of our current service after the expansion , As shown below :
[[email protected] ~] % docker-compose ps Name Command State Ports --------------------------------------------------------------------------------------------------------------------------------------------- traefik_reverse-proxy_1 /entrypoint.sh --api.insec ... Up 0.0.0.0:80->80/tcp,:::80->80/tcp, 0.0.0.0:8080->8080/tcp,:::8080->8080/tcp traefik_whoami_1 /whoami Up 80/tcp traefik_whoami_2 /whoami Up 80/tcp traefik_whoami_3 /whoami Up 80/tcp traefik_whoami_4 /whoami Up 80/tc
[[email protected] ~] % curl -i http://192.168.56.114:8080/api/rawdata?json HTTP/1.1 200 OK Content-Type: application/json Date: Thu, 09 Sep 2021 02:28:35 GMT Content-Length: 1882 {"routers":{"[email protected]":{"entryPoints":["traefik"],"service":"[email protected]","rule":"PathPrefix(`/api`)","priority":2147483646,"status":"enabled","using":["traefik"]},"[email protected]":{"entryPoints":["traefik"],"middlewares":["[email protected]","[email protected]"],"service":"[email protected]","rule":"PathPrefix(`/`)","priority":2147483645,"status":"enabled","using":["traefik"]},"[email protected]":{"entryPoints":["http"],"service":"reverse-proxy-traefik","rule":"Host(`reverse-proxy-traefik`)","status":"enabled","using":["http"]},"[email protected]":{"entryPoints":["http"],"service":"whoami-traefik","rule":"Host(`whoami.docker.localhost`)","status":"enabled","using":["http"]}},"middlewares":{"[email protected]":{"redirectRegex":{"regex":"^(http:\\/\\/(\\[[\\w:.]+\\]|[\\w\\._-]+)(:\\d+)?)\\/$","replacement":"${1}/dashboard/","permanent":true},"status":"enabled","usedBy":["[email protected]"]},"[email protected]":{"stripPrefix":{"prefixes":["/dashboard/","/dashboard"]},"status":"enabled","usedBy":["[email protected]"]}},"services":{"[email protected]":{"status":"enabled","usedBy":["[email protected]"]},"[email protected]":{"status":"enabled","usedBy":["[email protected]"]},"[email protected]":{"status":"enabled"},"[email protected]":{"loadBalancer":{"servers":[{"url":"http://172.20.0.2:80"}],"passHostHeader":true},"status":"enabled","usedBy":["[email protected]"],"serverStatus":{"http://172.20.0.2:80":"UP"}},"[email protected]":{"loadBalancer":{"servers":[{"url":"http://172.20.0.4:80"},{"url":"http://172.20.0.5:80"},{"url":"http://172.20.0.3:80"},{"url":"http://172.20.0.6:80"}],"passHostHeader":true},"status":"enabled","usedBy":["[email protected]"],"serverStatus":{"http://172.20.0.3:80":"UP","http://172.20.0.4:80":"UP","http://172.20.0.5:80":"UP","http://172.20.0.6:80":"UP"}}}}
here , We request 4 Time , To see Traefik Load balancing between four instances , The specific order is as follows :
[[email protected] ~] % curl -H Host:whoami.docker.localhost http://127.0.0.1 # for the first time Hostname: 50f70b1ccace IP: 127.0.0.1 IP: 172.20.0.4 RemoteAddr: 172.20.0.2:40000 ... # The second time Hostname: 8c2204231f98 IP: 127.0.0.1 IP: 172.20.0.5 RemoteAddr: 172.20.0.2:39660 ... # third time Hostname: d1078dbb0332 IP: 127.0.0.1 IP: 172.20.0.3 RemoteAddr: 172.20.0.2:37600 ... # The fourth time Hostname: f1cf5b632fde IP: 127.0.0.1 IP: 172.20.0.6 RemoteAddr: 172.20.0.2:50384 ...
Based on this , We go through http://192.168.56.114:8080/dashboard/#/ visit Traefik Web UI To observe different routing requests 、 service 、 Middleware and other related information . The details are as follows :
On the whole front page , We can see Traefik Requests for different protocols supported 、 Service type , involve HTTP、TCP as well as UDP etc. . meanwhile , Show different types of Providers Information , involve Docker、K8S And other relevant information . be based on HTTP agreement , You can see the 4 Routing rules ,5 A service and 2 A custom middleware . With Middlewares For example , We click based on HTTP Agreed “Middlewares ” Of the forum “Explore” link , You can see the link topology call chain formed by the currently deployed applications , The details are as follows :
in the light of Traefik Middlewares Custom development practices for , If you are interested , Refer to the previous article :Traefik Middleware Plug in practice , So that everyone can understand Traefik The rich functions of .
Custom renewal for certificates , It's also Traefik One of the powerful functions of component , Based on this , We will be based on HTTP and DNS Two aspects are briefly described .
Based on the above scenario , Its brief activity flow is analyzed as :
Traefik Use ACME( A protocol ( Precisely agreed means of communication ), Used to negotiate from LE Certificate . It is Traefik Part of ) towards LE(Let's Encrypt, A service that provides free certificates ) Request a certificate for a specific domain , Such as ,example.com.LE Answer with some randomly generated text ,Traefik Put this text in a specific location on the server .LE Then ask DNS Internet The server , for example .com, The server points to a IP Address .LE Through the port 80/443 View the... Of the file containing the random text IP Address .
If there is , So this proves that the person requesting the certificate controls both the server and the domain , Because it shows the right DNS Control of records . Certificate issued , Valid for 3 Months , The surplus is not enough 30 days ,Traefik Will automatically attempt to renew .
be based on HttpChallenge The advantage of is the ability to obtain wildcard certificates . These are validation of all subdomains *.example.com In addition , There is no need to open any ports . The related file configurations are as follows :
## STATIC CONFIGURATION
log:
level: INFO
api:
insecure: true
dashboard: true
entryPoints:
web:
address: ":80"
websecure:
address: ":443"
providers:
docker:
endpoint: "unix:///var/run/docker.sock"
exposedByDefault: false
certificatesResolvers:
lets-encr:
acme:
#caServer: https://acme-staging-v02.api.letsencrypt.org/directory
storage: acme.json
email: [email protected]
httpChallenge:
entryPoint: web
Based on this scenario ,Traefik Use ACME towards LE Request a certificate for a specific domain , Such as example.com.LE Answer some randomly generated text ,Traefik As a new DNS TXT Record . then ,LE Check example.com DNS Record to see if the text exists .
If it exists , So this proves that the person requesting the certificate controls the domain , The certificate is valid for 3 Months .Traefik Will be less than... In the remaining time 30 Day time automatically tries to renew .
Comparison based on HttpChallenge ,Traefik Need to be able to DNS Records are automatically updated , So any management DNS People on the site support this . That's why you use Cloudflare. The related file configurations are as follows :
## STATIC CONFIGURATION
log:
level: INFO
api:
insecure: true
dashboard: true
entryPoints:
web:
address: ":80"
websecure:
address: ":443"
providers:
docker:
endpoint: "unix:///var/run/docker.sock"
exposedByDefault: false
certificatesResolvers:
lets-encr:
acme:
#caServer: https://acme-staging-v02.api.letsencrypt.org/directory
storage: acme.json
email: [email protected]
httpChallenge:
entryPoint: web
In addition to the above characteristics , stay Traefik V2.3.x And in subsequent versions , Introduced a range of new features , Include Traefik Plug in system 、 And Traefik Pilot Integration of 、 Yes Amazon ECS Support, etc , Make Traefik Ecological components are becoming more and more functional , More and more application scenarios .
In addition to the examples shown above 、 The alarm 、 In addition to the monitoring information function ,Traefik Pilot It also supports customization “ plug-in unit ” Development function , It provides a wealth of plug-in types , Adaptive assembly can be carried out in combination with actual business scenarios , The details are as follows :
in summary , As a cloud native edge router ,Traefik The function has been able to meet most business scenarios , meanwhile , It has also been applied in many industries . Maybe , In the next version , We will usher in a stronger Traefik ecology , Including the latest launch of the Google team Kubernetes Service API Support for , And for Traefik Mesh Chinese support mTLS The function of . In addition to the above , Other potential features will emerge as the market changes , Last , Let's wait and see ~
# Reference material
- https://github.com/DoTheEvo/
This article is from WeChat official account. - Framework post station (priest-arc)
边栏推荐
- [log service CLS] experience of troubleshooting abnormal scenarios with tke event log
- What is the website domain name trademark registration process? What is the use of a website domain name trademark?
- Sockfwd a data forwarding gadget
- 机器学习中 TP FP TN FN的概念
- Map design
- Textplus - reverse engineering of textplus
- Icml'22 | progcl: rethinking difficult sample mining in graph contrast learning
- Devops culture: Amazon leadership principles
- Selenium crawls stocks in practice
- How does the fixed assets management software reduce costs and increase efficiency for enterprises?
猜你喜欢
Installation and use of winscp and putty

GNN上分利器!与其绞尽脑汁炼丹,不如给你的GNN撒点trick吧

GNN upper edge distributor! Instead of trying to refine pills, you might as well give your GNN some tricks
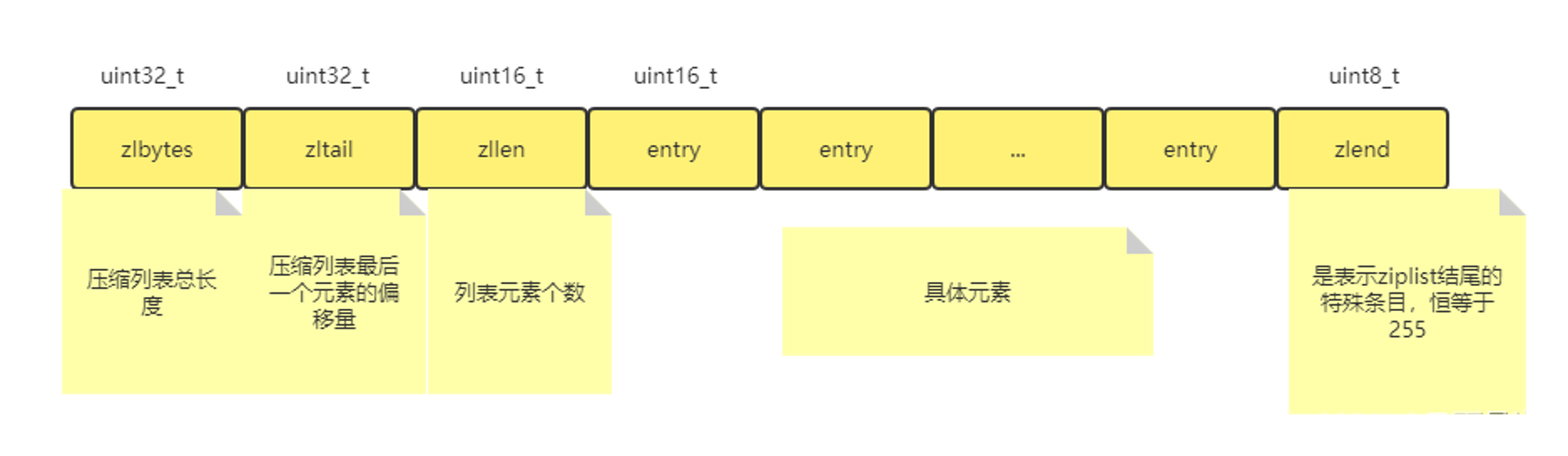
【Redis进阶之ZipList】如果再有人问你什么是压缩列表?请把这篇文章直接甩给他。

Niu Xuechang's anniversary celebration: software promotion, limited time and free registration code!
Shengdun technology joined dragon lizard community to build a new open source ecosystem

ShardingSphere-proxy-5.0.0容量范围分片的实现(五)

Installation and use of winscp and putty

Shardingsphere-proxy-5.0.0 implementation of capacity range partition (V)
13 `bs_duixiang.tag标签`得到一个tag对象
随机推荐
S2b2c e-commerce platform in the pharmaceutical and medical industry enables enterprises to grasp differentiated competitive advantages and improve supply chain efficiency
Output type SPED trigger inbound delivery after PGI for inter-company STO's outb
7 tips for preventing DDoS Attacks
Solve the problem that Base64 compressed files are extracted with spaces after post request
Echo framework: implementing timeout Middleware
Feasibility of importing UE4 using gltf with instances
4 most common automated test challenges and Countermeasures
What is memory out of order access?
If you want to open an account for stock trading, is it safe to open an account online-
Echo framework: automatically add requestid
Graduation project - thesis writing notes [design topic type, thesis writing details, design materials]
[redis advanced ziplist] if someone asks you what is a compressed list? Please dump this article directly to him.
WinSCP和PuTTY的安装和使用
Is the domain name available for trademark registration? How long is the trademark registration cycle?
Intelligent + fault-tolerant server is the best partner in the edge computing scenario
[technology planting grass] skillfully use cloud function to create wechat web page authorization public service
实时计算框架:Spark集群搭建与入门案例
Architecture solutions
js输入输出语句,变量
[technical grass planting] take you to Tencent cloud's private cloud disk in ten minutes
