当前位置:网站首页>Call system function security scheme
Call system function security scheme
2022-06-25 02:30:00 【Hua Weiyun】
1. Directly call the function of the system
Reasons why it is not recommended to use : We are in the process of coding , There are many functional systems that have provided functional interfaces , Generally, we call system functions directly to realize functions . But you know what ? It's not safe for you to call system functions directly in some scenarios , When your program is being studied by security reverse , You can import the table directly through the program , And the system functions called by disassembly , So we just need to check the function of the system function , Then you can know the general function points , And just one hook (HOOK technology ) Functions on the system , Then the function of the system function you call will fail .
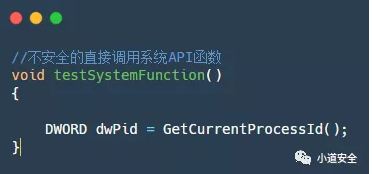
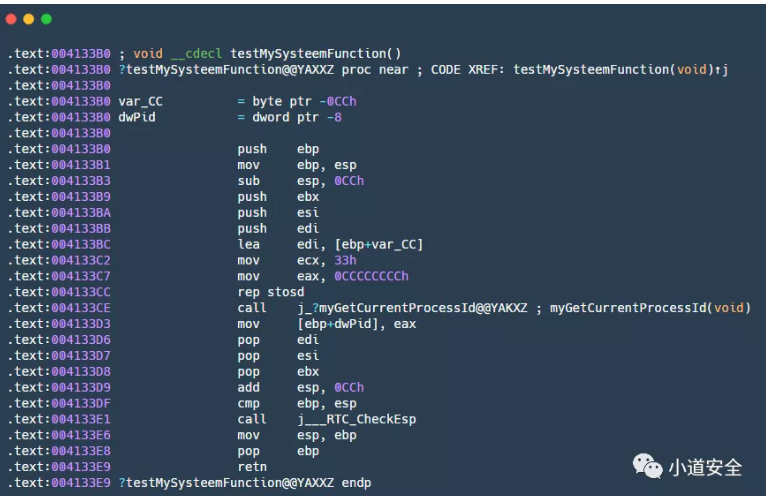
The following figure shows the assembly code realized by calling the system function . You can analyze the function directly through the system function shown .
2. Customize the implementation function and then call the function
Recommended reasons for use : For the key functions, we suggest to implement the functions by ourselves , Then call , This can make it more difficult for the program to be analyzed directly , So as to strengthen the security of the program .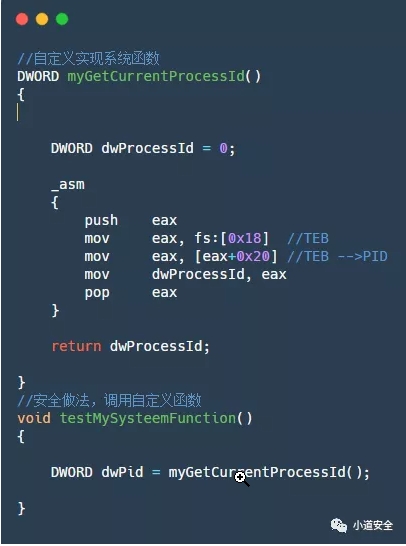
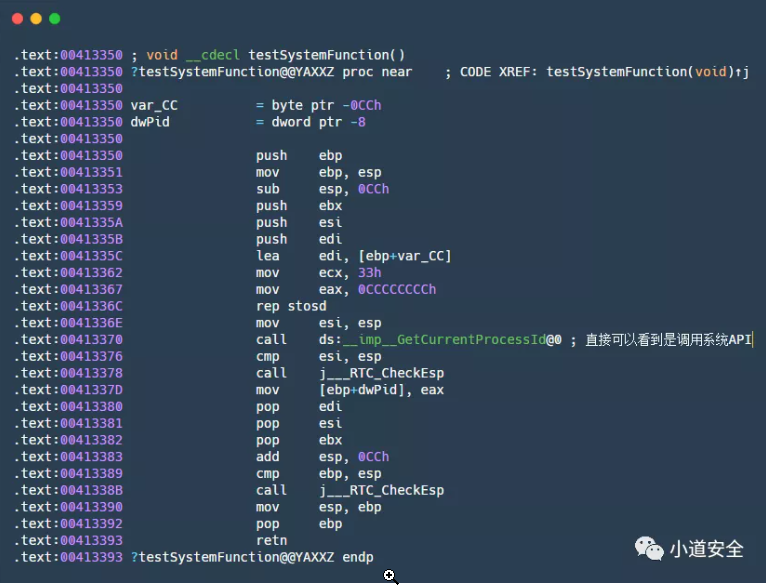
The following figure is the assembly code for custom function calls , You can see from the assembly code below that the key functions are implemented by yourself , To understand the function of this function, you need to go inside the function for analysis . This enhances the relative safety of key function functions .
边栏推荐
- MCN机构遍地开花:博主和作者要谨慎签约、行业水很深
- Left hand dreams right hand responsibilities GAC Honda not only pays attention to sales but also children's safety
- Is the compass reliable? Is it safe to open a securities account?
- 3 years of testing experience. I don't even understand what I really need on my resume. I need 20K to open my mouth?
- NPM package publishing tutorial
- The Oracle 11g RAC cluster database cannot be started due to directory permission errors
- 2022年云计算应用关键威胁调查
- 算力服务网络:一场多元融合的系统革命
- 背了八股文,六月赢麻了……
- 【FPGA】串口以命令控制温度采集
猜你喜欢
随机推荐
[mobile terminal] design size of mobile phone interface
把 Oracle 数据库从 Windows 系统迁移到 Linux Oracle Rac 集群环境(1)——迁移数据到节点1
02 common codes for Epicor secondary development
Is it out of reach to enter Ali as a tester? Here may be the answer you want
罗德与施瓦茨与中关村泛联院合作开展6G技术研究与早期验证
测试/开发程序员,30而立,你是否觉得迷茫?又当何去何从......
Viewing MySQL password on Linux_ MySQL forgets password "suggestions collection" under Linux
探索C语言程序奥秘——C语言程序编译与预处理
内网学习笔记(6)
Hashcat 的使用
华为、阿里等大厂程序员真的好找对象吗?
数据库系统概论必背知识
Network planning | [four network layers] knowledge points and examples
js正则匹配数字、大小写字母、下划线、中线和点[通俗易懂]
把 Oracle 数据库从 Windows 系统迁移到 Linux Oracle Rac 集群环境(3)—— 把数据库设置为归档模式
mysql命令备份
[day 26] given the ascending array nums of n elements, find a function to find the subscript of target in nums | learn binary search
入坑机器学习:一,绪论
Migrate Oracle database from windows system to Linux Oracle RAC cluster environment (3) -- set the database to archive mode
The role of software security testing, how to find a software security testing company to issue a report?