当前位置:网站首页>TCP.IP
TCP.IP
2022-07-28 20:32:00 【Operation and maintenance log of Panax notoginseng】
HTTP
Hypertext transfer protocol , It is the most widely used network protocol on the Internet
The request message consists of three parts :
a、 Request line : Include request method 、URI、HTTP Version information
b、 Request first field
c、 Request content entity
The response message consists of three parts :
a、 Status line : contain HTTP edition 、 Status code 、 Reason phrase for status code
b、 Response first field
c、 Response content entity
Network status code
- 2XX: success
- 3XX: Further operation , Redirect etc.
- 4XX: Request error
- 5XX: Service processing error
- 301: Jump forever
- 403: Blocking access , Not enough permissions
- 404: The page requested by the client could not be found
- 502: Bad gateway
- 504: gateway timeout
New version features :
a、 Default persistent connections save traffic , As long as either end of the client server does not explicitly propose to disconnect TCP Connect , Just keep connected , Can send multiple times HTTP request
b、 Pipelining , The client can send multiple HTTP request , Instead of waiting for a response one by one
c、 Breakpoint continuation principle
HTTPS
HTTP Security version , stay HTTP Lower join SSL layer ,HTTPS The safety basis of SSL, So the details of encryption need to be SSL agreement
Communication process
- Client initiated url request
- The server returns the public key
- The client verifies the public key , Correct is the next step , Errors are warnings
- The client generates random values , Use public key encryption
- Send to server , The server decrypts the random value with the private key
- Random values are used as secret keys for symmetric encryption
- Send to client , Decrypt with random values
common problem :
Q:HTTP And HTTPS difference ?
A: 1.HTTPS Need to apply to buy CA certificate , HTTP Unwanted
2.HTTP It's plaintext transmission , unsafe , HTTPS Is in HTTP On the basis of SSL layer , More secure
3.HTTPS Low efficiency ,HTTP Efficient
Q:HTTPS Transmission process ?
A: Client initiated HTTPS request , The server returns the certificate , Client verifies certificate , After the verification, the random number used to modify the symmetric encryption algorithm is generated locally , The random number is encrypted and transmitted to the server through the public key in the certificate , After receiving it, the server decrypts it through the private key to get the random number , After the data interaction through symmetric encryption algorithm encryption and decryption .
Q: Why certificates are needed ?
A: To prevent attacks by intermediaries , Verify the identity of the server
Q: How to prevent tampering ?
A: The certificate is public , Although the middleman can get the certificate , But the private key cannot be obtained , The public key cannot infer the private key , Therefore, private key encryption cannot be used after tampering , Forced encryption customers can not decrypt , Forcibly modify the content , This will cause the certificate content to not match the fingerprint in the signature
TCP/IP
TCP/IP Protocol set includes application layer , Transport layer , The network layer , Network access layer
TCP/UDP
TCP Connection oriented , Reliable transmission , Occupy more system resources , Slow speed , Low efficiency , Use when there are requirements for network quality
UDP It's disconnected , Transmission is unreliable , Less system resources , Fast , Efficient , There are no special requirements for data security
About detecting network connections
Statistics 80 Number of port connections
netstat -nat|grep -i “80”|wc -l
Statistics httpd Number of protocol connections
ps -ef|grep httpd|wc -l
Find out which IP Maximum address connections
netstat -na|grep ESTABLISHED|awk {print $5}|awk -F: {print $1}|sort|uniq -c|sort -r +0n
see nginx Current concurrent accesses :
netstat -apn|grep 'nginx: worker'|wc -l
see apache Current concurrent accesses :
netstat -an | grep ESTABLISHED | wc -l
see http How many processes are there :
ps aux|grep httpd|wc -l
For connected IP Sort by number of connections :
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n
see TCP Connection status :
netstat -nat |awk '{print $6}'|sort|uniq -c|sort -rn
netstat -n | awk '/^tcp/ {++S[$NF]};END {for(a in S) print a, S[a]}'
netstat -n | awk '/^tcp/ {++state[$NF]}; END {for(key in state) print key,"\t",state[key]}'
netstat -n | awk '/^tcp/ {++arr[$NF]};END {for(k in arr) print k,"\t",arr[k]}'
netstat -n |awk '/^tcp/ {print $NF}'|sort|uniq -c|sort -rn
netstat -ant | awk '{print $NF}' | grep -v '[a-z]' | sort | uniq -c
see 80 The most port connections 20 individual IP:
netstat -anlp|grep 80|grep tcp|awk '{print $5}'|awk -F: '{print $1}'|sort|uniq -c|sort -nr|head -n20
netstat -ant |awk '/:80/{split($5,ip,":");++A[ip[1]]}END{for(i in A) print A,i}' |sort -rn|head -n20
use tcpdump Sniffing 80 Port access to see who is the highest :
tcpdump -i eth0 -tnn dst port 80 -c 1000 | awk -F"." '{print $1"."$2"."$3"."$4}' | sort | uniq -c | sort -nr |head -20
Find more time_wait Connect :
netstat -n|grep TIME_WAIT|awk '{print $5}'|sort|uniq -c|sort -rn|head -n20
Find out more SYN Connect :
netstat -an | grep SYN | awk '{print $5}' | awk -F: '{print $1}' | sort | uniq -c | sort -nr | more
Three handshakes
key word
SYN Set up a connection sign
ACK Confirm the connection identification
Seq Sequence number , Randomly generate numbers , Prevent interception
ack Confirmation number
FIN end

Why not four times, not two times, three times
Because four times before , The server will send a syn And a ack To the client , But the two packets are almost synchronized , So merge into one package
Not twice because , The client should confirm the server , The server should also confirm the client before establishing a two-way connection
Four waves
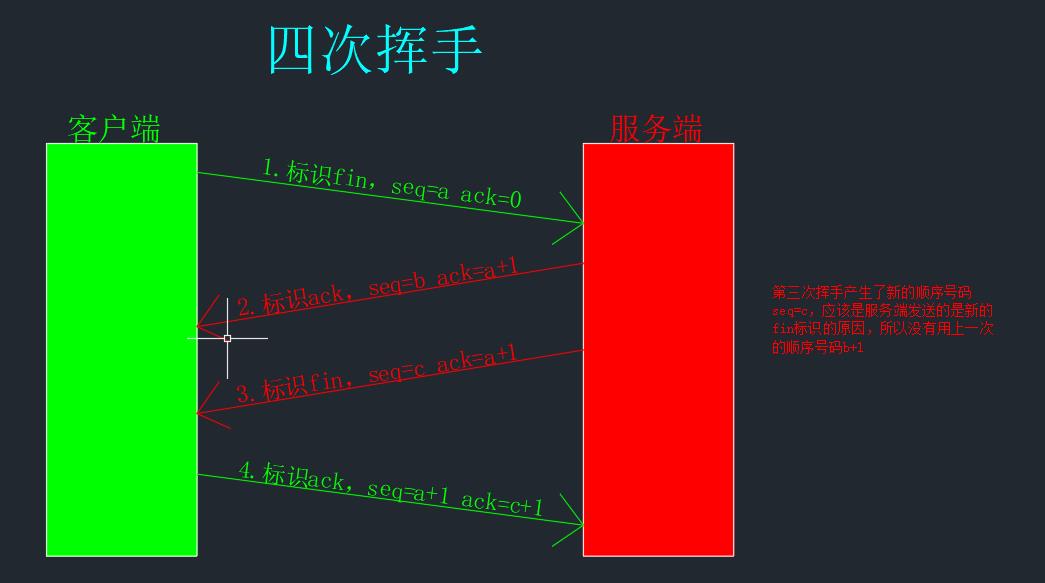
Why four waves, not three
Theoretically speaking, you can wave your hand three times ,2 and 3 And merge into a packet and send it to the client , But there are some problems , Because data transmission may be unidirectional ,2 and 3 And merge into a packet, that is, the confirmation and end connection identification must be sent together , Suppose the server is transmitting data to the client , The client can end the one-way connection, but the server cannot end the connection , At this moment, if the confirmation and end connection packets are sent together , It will cause the transmission of the server to be terminated
OSI Seven layer and four layer models
Detailed seven layer model
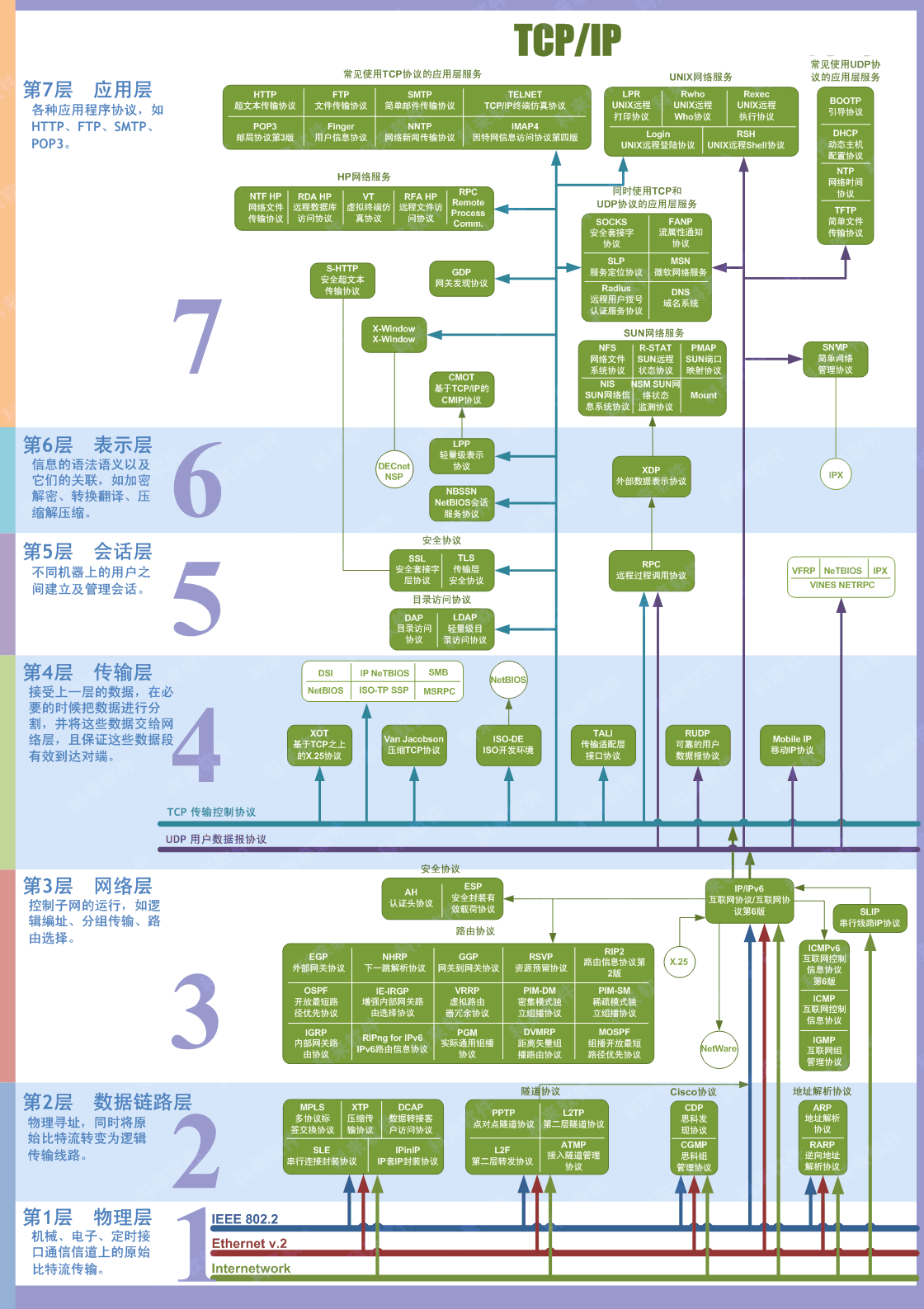
This picture is reproduced , I don't remember the address , Reprint , Invasion and deletion
Simplify the seven tier and four tier models
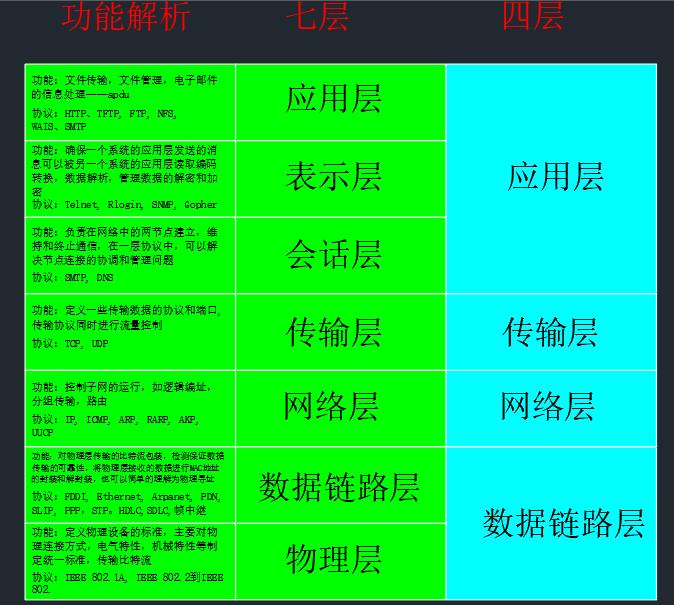
Forced to terminate
OSI Seven layer and four layer models
Detailed seven layer model
[ Outside the chain picture transfer in …(img-BS6q9Mr9-1656486883776)]
This picture is reproduced , I don't remember the address , Reprint , Invasion and deletion
Simplify the seven tier and four tier models
[ Outside the chain picture transfer in …(img-MsXp1Upm-1656486883776)]
边栏推荐
- CM4 development cross compilation tool chain production
- Wust-ctf2021-re school match WP
- 7. Functions of C language, function definitions and the order of function calls, how to declare functions, prime examples, formal parameters and arguments, and how to write a function well
- 一碰撞就自燃,谁来关心电池安全?上汽通用有话说
- Nocturnal simulator settings agent cannot be saved
- Scene thread allocation in MMO real-time combat games
- LVS deployment Dr cluster
- 产品经理访谈 | 第五代验证码的创新与背景
- 【实验分享】CCIE—BGP反射器实验
- Related concepts of multitasking programming
猜你喜欢
关于链接到其他页面的标题

Linux Installation MySQL (pit filling version)

Multi-Modal Knowledge Graph Construction and Application: A Survey

树行表达方式
![[task03: complex query methods - views, subqueries, functions, etc.]](/img/83/2cad48016199b079aca0251b7b4ee8.png)
[task03: complex query methods - views, subqueries, functions, etc.]

C language data 3 (2)

Other IPS cannot connect to the local redis problem solving and redis installation

Shanghai Jiaotong University joined hands with Taobao to set up a media computing laboratory: promoting the development of key technologies such as video super score

JVM (24) -- performance monitoring and tuning (5) -- Analyzing GC logs

What is the variance?
随机推荐
Item exception handling in SSM
How to automatically store email attachments in SharePoint
【CodeForces】Educational Codeforces Round 132 (Rated for Div. 2)
File lookup and file permissions
Gru neural network
DSACTF7月re
Mysql报错:Specified key was too long; max key length is 767 bytes
Related concepts of multitasking programming
CNN convolution neural network learning process (weight update)
关于链接到其他页面的标题
Commands related to obtaining administrator permissions
DOS common commands
【实验分享】CCIE—BGP反射器实验
Shanghai Jiaotong University joined hands with Taobao to set up a media computing laboratory: promoting the development of key technologies such as video super score
Method number problem for solving sum of numbers (knapsack problem)
Leetcode-297 serialization and deserialization of binary tree
Storage of C language data in memory (1)
C语言数据 3(1)
私有化部署的即时通讯平台,为企业移动业务安全保驾护航
WPF -- implement websocket server
