当前位置:网站首页>node. JS architecture optimization: reverse proxy and cache service
node. JS architecture optimization: reverse proxy and cache service
2022-06-25 12:35:00 【Velly_ zheng】
// The following notes are all notes from the learning video , Make it easy to remember
// Video address :https://time.geekbang.org/course/intro/232
app.js file
const app = new (require('koa'))
const cacheRedis = require('redis')('cache')
const backupRedis = require('redis')('backup')
//koa The middle bond of the onion conforms to an onion model
app.use(async(ctx,next) => {
const result = await cacheRedis(ctx.url); // RPC Asynchronous invocation of , from redis Extract a cached file from the
// The request url As key, from redis Take out a copy of the results , Assign a value to result
if(result){ // If there is a result , Directly return the result ; Hit cache
ctx.body = result;
return;
}
await next() // If you miss the cache , Then execute the following middle key
if(ctx.status == 200){ // Judge whether the request result is normal
cacheRedis.set(ctx.url,ctx.body, {expire: 200}); // Write request results to cache , Set expiration time
backupRedis.set(ctx.url,ctx.body, {expire: 200}); // Write the request results to the backup cache , Set expiration time
}
if(ctx.status != 200){
const result = await backupRedis(ctx.url); // From backup redis Take out the results
ctx.status = 200;
ctx.body = result;
}
})
边栏推荐
- The R language uses the follow up The plot function visualizes the longitudinal follow-up map of multiple ID (case) monitoring indicators, and uses stress The type parameter specifies the line type of
- Thinkphp3 count ` *'problem
- sudo: ulimit: command not found
- Huile optimization system -- sharing of secondary development source code of huile optimization app system
- The difference between this and super and their respective functions
- Fun pocket mall -- sharing the development source code of fun pocket app system
- The network traceroute command is used to determine the path through which IP packets access the destination address.
- Zhangxiaobai's road of penetration (IV) -- detailed explanation of XSS cross site script vulnerabilities
- MySQL common interview questions
- The first techo day Tencent technology open day in 2022 will be held online on June 28
猜你喜欢

Dark horse shopping mall ---1 Project introduction - environment construction

Navicat premium view password scheme
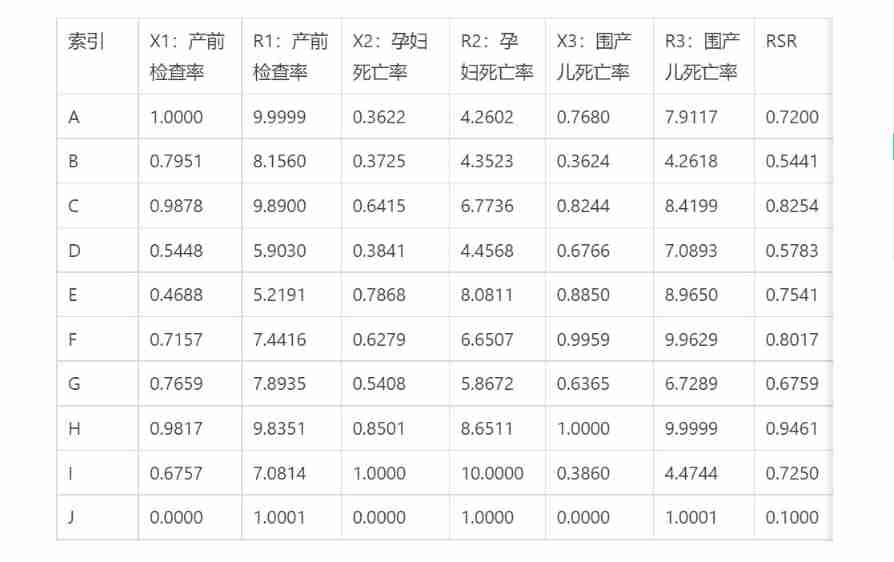
Rank sum ratio comprehensive evaluation method for common models in mathematical modeling

devsecops与devops的理解与建设

Flutter common commands and problems

How to use ARIMA model for prediction?

How do super rookies get started with data analysis?
Explanation of ideas and sharing of pre-processing procedures for 2021 US game D (with pre-processing data code)

A commonly used statistical modeling method -- difference analysis
![[论]Learning Dynamic and Hierarchical Traffic Spatiotemporal Features with Transformer](/img/58/d68112a3d019de66150e2f5102f436.png)
[论]Learning Dynamic and Hierarchical Traffic Spatiotemporal Features with Transformer
随机推荐
Renrenyue -- renrenyue system development source code sharing
揭秘GaussDB(for Redis):全面對比Codis
The dist function of R language calculates the distance between two samples in dataframe data, returns the distance matrix between samples, and specifies the distance calculation method through the me
Understanding and construction of devsecops and Devops
ECSHOP video list_ ECSHOP uploading video, video classification, video list playing video function
Concise H5 error page
ECSHOP commodity wholesale multi attribute multi specification multi inventory batch purchase ECSHOP wholesale plug-in ECSHOP multi attribute order
Micro engine remote attachment 7 Niu cloud upload
Heyangdao store management system -- share the development source code of heyangdao system
Network | indicators and test methods to measure the quality of the network
Array reorder based on a field
When MySQL queries fields in JSON format, it takes a property value of JSON data
Zhangxiaobai's way of penetration (III) -- detailed explanation of SQL injection vulnerability principle (SQL Server)
SDN system method | 9 Access network
Arm V7 continuous load / store
K8s, docker compose install MySQL 8.0.18
Uncover gaussdb (for redis): comprehensive comparison of CODIS
Today, I will explain to you what is DFI and its development prospects
thinkphp3.2.5 GIF. class. php for php7.4
Ubuntu uninstalling PHP