当前位置:网站首页>Endanger the safety of common Internet attacks have?
Endanger the safety of common Internet attacks have?
2022-08-02 20:45:00 【Software testing network】
Technology is now developing,The size of the Internet of things and application number also in the rapidly expanding.到2022年底,The global Internet market scale is expected to grow18%,物联网设备数量将达到144亿台.

Despite the global supply chain problems due to outbreak of the new champions league(包括芯片短缺),但预计到2025年,Global Internet devices will continue to grow2700万台.
Although the growth excited enterprises and users,But to understand how these devices are vulnerable to cyber attacks are also important.
因此,以下介绍7Kinds of common Internet attack that endangers safety,And understand the definition、示例、Common method of iot attack and prevent them from.
什么是物联网?
So how do you define the Internet of things?The Internet of things is a technology phenomenon,Refers to such as thermostat、汽车、冰箱、门锁、相机、健身追踪器、WiFiRouters connected to the Internet or other wireless communications networks and other daily equipment.
基本上,The Internet of things includes using sensors、软件、网络、, such as the Internet connection and data exchange of all physical devices or things.
The wireless connection is the Internet of things can help enterprises to the way.Through the Internet of things application,Enterprises can simplify the process of each operation in the field of,Including the manufacturing、供应链、销售、营销等.
Smart sensors can track assets,The Internet of things application can control the machine,The Internet of things intelligent device can collect data,The use case endless,Helps to reduce waste、Optimization process and reduce the cost.
物联网应用示例
Here are some real-life applications,Can help to understand what the Internet of things.
(1)智能音箱
Intelligent sound box is a typical application of the Internet of things,Because it is relatively easy to carry.Amazon EchoIs one of the typical example of Internet equipment,It is a compact intelligent speaker,Can broadcast news and music、Through the Internet to answer the question、设置警报、开/关灯等.
(2)智能穿戴
The function of the intelligent wearable device such as a watch is not just tell time,还可以发送消息、接听电话、播放音乐、计算步数、View the social interaction and so on.智能戒指、Smart helmet and smart headphones is the use of the Internet of things technology equipment more examples of.
(3)智慧城市
Iot also addressed with traffic jams、道路安全、卫生、街道照明、盗窃、Pollution and so on related issues.
(4)联网车辆
Internet of vehicles can be connected via wireless network and equipment.In addition to remotely lock/解锁车门、Open the skylight or start/Stop engine functions such as,These cars also provides carWiFi连接.If the driver is over the boundary of the set,Geographical fence function will remind the owner.It is also useful for taxi and commercial truck drivers.
What makes the Internet of things become weak?
Typical of the Internet of things devices in addition to set default passwords without any security features.The security measures might let ranged attackers by using not mend loopholes to control the whole system.
The more iot devices can connect way,Cyber criminals use the more chance.因此,Loopholes in the Internet of things include the loopholes in the Internet,For example in bluetooth devices found a loophole in the.
Iot device is considered to be the weakest element in the wireless system,Hackers are allowed to enter the network、控制计算机,Even spreading malware.以下是几个原因:
- The lack of security software:Most of the Internet of things devices don't have the ability to integrate antivirus or firewall protection.因此,They are easy to be used.
- 缺乏网络安全意识:当今时代,More and more industries turn to digital.但是,Inherent vulnerable to rely on the Internet of things device itself is a major network security holes,Many enterprises have ignored this loophole,And threatened use of.
- Attack surface increase:Wireless connection between the Internet of things devices represents a broader attack surface,Hackers can remote access to countless entry point.
Common Internet attack
Because most of the Internet of things devices are built for simple task,So they didn't use the strong security program.Malicious actions using the weak safety standards to try one of the following common Internet of things.
(1)窃听
Hacking victims through iot equipment monitoring network,And secretly collecting sensitive data,Including bank details and login credentials.They can even sit close to the location of the hearing room ongoing dialogue.例如,People may not realize that someone in the nearby coffee shop,By using the support of the Internet of things in the room intelligent device to monitor the dialogue.
This is run through the use of such equipment unsafe or weaker network to implement safety.
(2)权限提升攻击
To know everything about the Internet of things is very important,Because professional hackers can also attack the operating system.They use the Internet of things devices are not to repair the weaknesses or zero-day vulnerabilities that would increase the permissions to administrator level and complete control of the system.
(3)暴力攻击
几乎84%Organizations use iot devices,但只有50%Organization deployed appropriate security measures,Include regular change password.默认、Has not changed and weak passwords allow network attacker attempts to violence.They are using trial and error method to crack all possible combinations of password and enter the system、Account or network.
因此,The weak or the old password,The network attacker the easier it is to crack.
(4)A malicious node injection
Cyber criminals between legal node inject malicious script,To access the data exchanged between link node.这通常是可能的,Because no one could have been monitoring the Internet of things device.
(5)The firmware was hijacked
There are so many things networking equipment、品牌和产品,Firmware hijacking is a major problem.Bad actors send victims with a damaged links of false update notification.These links to redirect the user to a malicious web site,Asked to submit detailed personal information or by malicious software system.
(6)分布式拒绝服务
最近,Distributed denial of service orDDoSThe number of attacks significantly soar.The goal is through multiple device access a single server.Hackers use botnet malware trying through infected or“僵尸化”The Internet of things devicesDDoS攻击.
(7)物理篡改
From the external access iot equipment such as car,Because in the open environment,Unable to control who can contact with them.因此,Network attackers targeted attacks by physical tampering with equipment.
To minimize the risk of Internet equipment
In the understanding of the Internet of things or what is the Internet of things,Enterprises should employees on the following preventive measures of education.
(1)Consider security as soon as possible
Design and manufacture of iot equipmentITCompany should be from the development phase to improve safety standards.The default security features to protect operating system and avoid malware into.
(2)The implementation of public key infrastructure and digital certificate
公钥基础设施(PKI)Protection is installed on all sorts of equipment between the client-服务器连接.It USES is used to encrypt the digital certificate to the key data and network interaction between encryption and decryption.
The implementation of public key infrastructure(PKI)And digital certificates by hiding the user secret deal directly input the website text information to protect the user during.
(3)密码保护
Enable password protection on possessions networking equipment.A strong password at least12个字符,Made from a mix of case Numbers and special characters.
Always USES unique password for each device and account.此外,Don't set can guess passwords,For example, the pet name、出生日期、街道地址、Favorite food store, etc.
(4)Set the physical protection
Threat participants can steal equipment and crack them to manipulate the circuit、Port and chip.有时,With the default password stickers will paste within the equipment enclosure,So that they can easily damage the system.
Enterprise can through the device of equipment in the shell of locking to physical protection,You must use the measures to cover their port,Because they are most likely to be Internet attack gateway.
(5)Strengthen the network andAPI安全性
Using anti-malware、防病毒软件、Firewalls and other security software can implement network security.Enterprises should disable port forwarding and ensure that when not in use close port.
应用程序编程接口或APISecurity also can protect the iot devices and the data exchanged between the back-end systems.It only allows the grantee to access it.
结语
The safety of the device can't ignore the Internet of things to people,Because hackers can use them to try different types of network crime,Such as malware attacks、密码泄露、DDoS攻击等.
As more and more companies rely on intelligence technology,Network attack opportunity a rise in the number of.And by implementing strong iot security protocols and preventive measures,Can better protect the enterprise、员工、供应商和客户.
边栏推荐
- golang刷leetcode 经典(2)拓扑排序
- ffmpeg cannot find libx264 after compilation
- 开源一夏 |【云原生】DevOps(五):集成Harbor
- Security First: Tools You Need to Know to Implement DevSecOps Best Practices
- MySQL命令(命令行方式,而非图形界面方式)
- Smart Microelectronics Releases Low-Power MM32L0130 Series MCU Products
- golang刷leetcode 字符串(4)逆波兰式
- DevOps之代码检查
- 攻防世界-favorite_number
- Go编译原理系列6(类型检查)
猜你喜欢
字节面试官狂问我:你没有高并发、性能调优经验,为什么录取你?
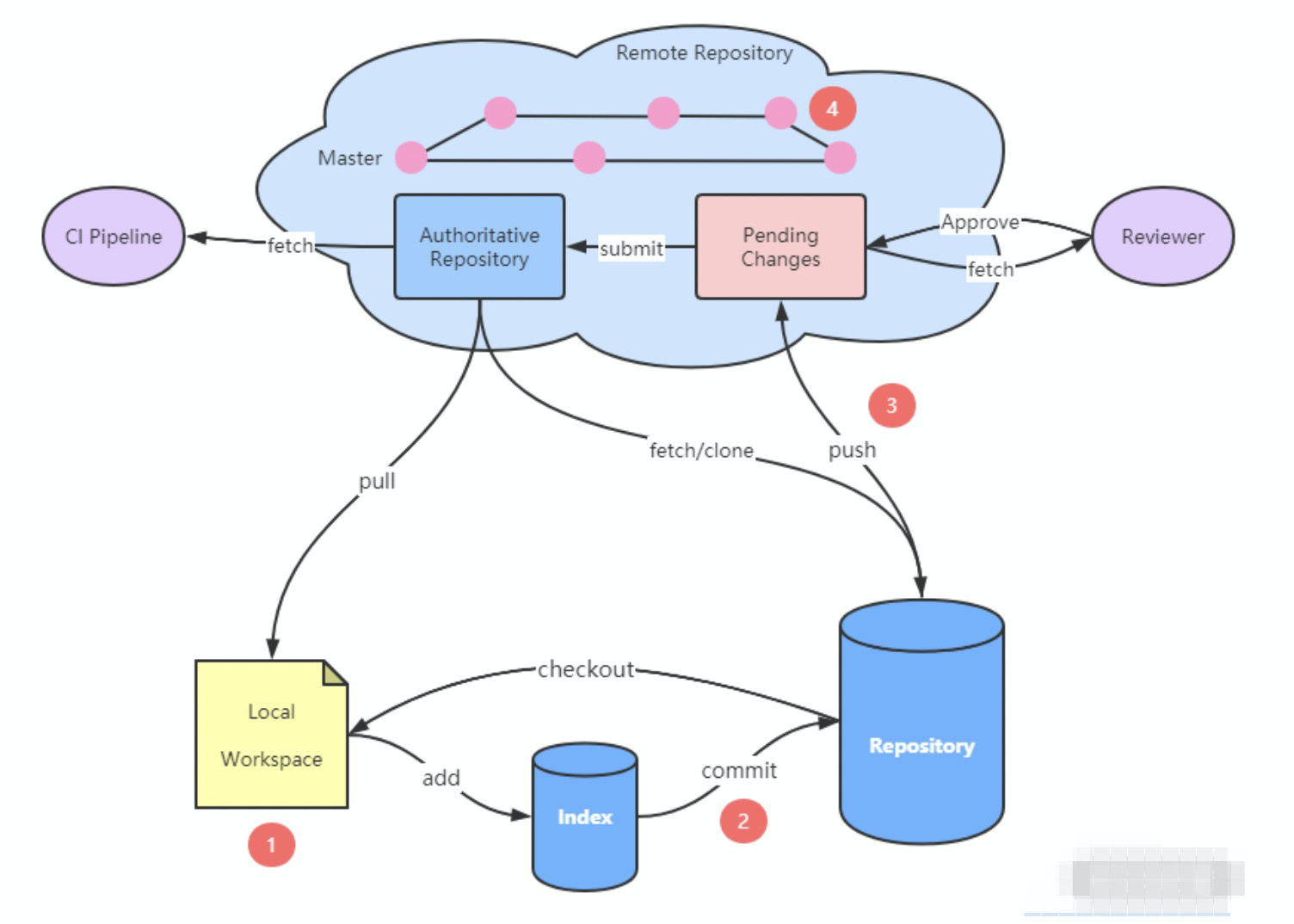
Code Inspection for DevOps
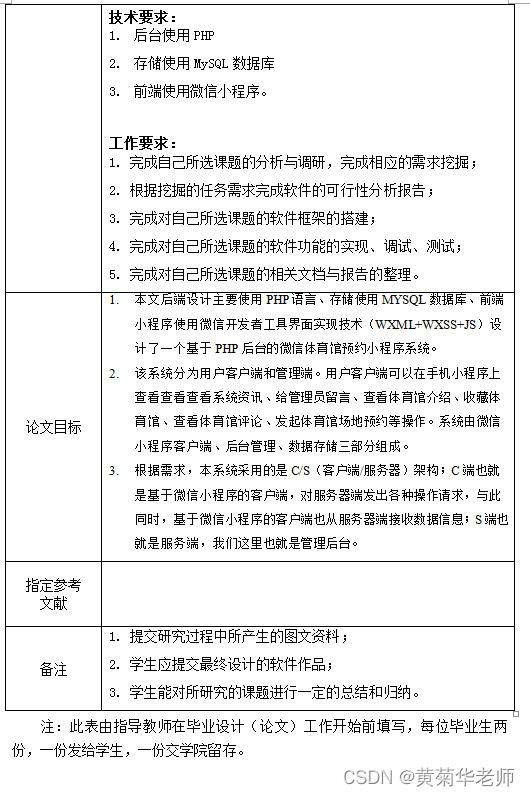
Wechat Gymnasium Appointment Mini Program Graduation Design Finished Work (5) Task Book

What is the difference between erp system and wms system
Flink Learning 9: Configure the idea to develop the flink-Scala program environment

魔豹联盟:佛萨奇2.0dapp系统开发模式详情

erp系统和wms系统有什么区别
Go 语言快速入门指南: 介绍及安装
HDF驱动框架的API(1)
mysql四种隔离级别
随机推荐
golang源码分析(33)pollFD
Playing in the cloud | The key technology of Tianyi cloud object storage ZOS high availability is revealed
POE交换机全方位解读(中)
Flink学习9:配置idea开发flink-Scala程序环境
Code Inspection for DevOps
9月起中国给予多哥等16国98%税目产品零关税待遇
数据治理:数据集成和应用模式的演进
HDF驱动框架的API(1)
The days of patching are more difficult than the days of writing code
如何减轻企业账户被劫持的攻击?
记一次 .NET 某工控自动化控制系统 卡死分析
golang学习之七:并发编程基础(goroutine、channel、select)
What is the difference between erp system and wms system
企业云成本管控,你真的做对了吗?
二叉查找树的查找
MySQL索引
织梦提示信息提示框美化
docker安装Oracle之后常用的一些命令
mui中使用多级选择器实现省市区联动
golang刷leetcode 经典(4) 实现跳表