当前位置:网站首页>Implementing reflexive ACL in Cisco packet tracker
Implementing reflexive ACL in Cisco packet tracker
2022-06-12 18:18:00 【Confused dream butterfly】
Catalog
experiment 1: Use ACL Control link connectivity
experiment 2: In Cisco Simulator Cisco Packet Tracer Reflexive realization ACL
Step one : Give the router 2911 Turn on securityk9 Pattern
Step three : Verify connectivity
One 、 Preface
Recently passed Cisco Packet Tracer Simulator learning ACL when , A little bit of a problem ,ACL Divided into standard ACL Access control lists and extended access control lists , But when a router is configured with an access control list , Although it is to realize the prohibition of the regulation control list , But not from the opposite end PING Come back . The specific phenomena are as follows :
Two 、 experiment
experiment 1: Use ACL Control link connectivity
Experimental Topology

Test connectivity

To configure ACL
Give the router 0 2911 To configure ACL( Here is just a simple use of the standard ACL)
tsy(config)#access-list 11 deny 192.168.10.0 0.0.0.255 // prohibit 192.168.10.0 The network segment is routed through
tsy(config)#access-list 11 permit any // Be careful : This line is the most important , stay cisco Inside, as long as the access control list is created ( Last article ), Other network segments are also disabled by default , Only writing this line can access the default prohibition
tsy(config)#int g0/1
tsy(config-if)#ip access-group 11 out // Reference to interface G0/1
tsy(config-if)#exit
tsy(config)#exitView access control list
tsy#show ip ac
tsy#show ip access-lists
Standard IP access list 11
10 deny 192.168.10.0 0.0.0.255
20 permit any
tsy#Test connectivity again


Why? PC1 Go to PingPC0 no , It doesn't just limit PC0 Go to PC1 Your route ?!!!
because Ping Implementation process of , Between two terminals Mutual inquiry and confirmation The process of :

experiment 2: In Cisco Simulator Cisco Packet Tracer Reflexive realization ACL
How do we achieve one-way Ping through , The opposite end cannot Ping How about yourself ? I found something in Du Niang's knowledge treasure house , Referring to Baidu's experience :https://jingyan.baidu.com/article/948f5924a79294d80ef5f95c.html
Step one : Give the router 2911 Turn on securityk9 Pattern
tsy#conf terminal // Enter configuration mode
tsy(config)#license boot module c2900 technology-package securityk9 // Turn on securityk9 Pattern
// Omit here
ACCEPT? [yes/no]: Y // confirm
tsy#write
Building configuration...
[OK]
tsy#reload // Restart
// Omit here
tsy>en
tsy#show lic
tsy#show license fe
tsy#show license feature // Check the license file after restart ,securityk9 Enabled
Feature name Enforcement Evaluation Subscription Enabled RightToUse
ipbasek9 no no no yes no
securityk9 yes yes no yes yes
datak9 yes no no no yes
uck9 yes yes no no yes
tsy#conf terminal
Enter configuration commands, one per line. End with CNTL/Z.
tsy(config)#Step two : To configure ACL
tsy#conf terminal // Enter configuration mode
tsy(config)#ip access-list extended TSY // Add extended access control list TSY
tsy(config-ext-nacl)#deny ip any any // Prohibit all network segments from passing through
tsy(config-ext-nacl)#exit
tsy(config)#int G0/1 // At the interface G0/1 Application in
tsy(config-if)#ip access-group TSY in // Access control list TSY Applied to the interface G0/1 Access to
tsy(config-if)#exit
tsy(config)#ip inspect name Tong http audit-trail on // This sentence I understand is to allow http Round trip message execution , Mark is Tong Of
tsy(config)#ip inspect name Tong icmp audit-trail on // allow icmp Round trip message execution , Mark is Tong Of
tsy(config)#int G0/1 // At the interface G0/1 Application in
tsy(config-if)#ip inspect Tong out // Access control list TONG Applied to the interface G0/1 The output channel of
tsy(config-if)#exit
tsy(config)#exitI don't know if I understand right here , I hope you can correct me !
View access control list
tsy#show ip access-lists
Extended IP access list TSY
10 deny ip any any (4 match(es))
Step three : Verify connectivity

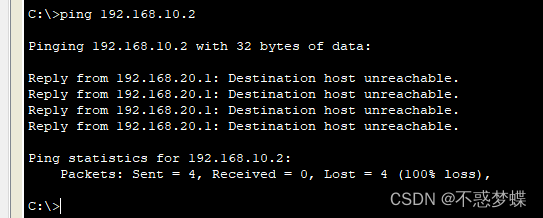
3、 ... and 、 summary
there introspect ACL, It's just Cisco Simulator This is how to use , however Correct reflexivity ACL It's not like that !!!
边栏推荐
- 1.5 what is an architect (serialization)
- MySQL learning notes
- Leetcode 718 longest common substring
- Typescript common types (I)
- leetcode 300. 最长递增子序列
- 在同花顺开户证券安全吗
- JS dichotomy
- leetcode 718 最长公共子串
- Solution to the problem that the anaconda navigator card logo cannot be opened and the card will flash back - replace the alicloud image source
- Explanation of core interrupt of Godson processor
猜你喜欢

迄今微软不同时期发布的SQL Server各版本之间的大致区别,供参考查阅

Schedule update | 2022 Microsoft and Intel hacker song competition is in hot registration

When openharmony meets openeuler

VirtualLab basic experiment tutorial -6 Blazed grating

Schéma de cristallisation différentielle active et différence entre LV - PECL, LVDS et hcsl

PHP implementation of infinite classification tree (recursion and Optimization)

MYSQL:Expression #4 of SELECT list is not in GROUP BY clause and contains nonaggregated column

VirtualLab基础实验教程-4.单缝衍射

The server time zone value ‘� й ��� ʱ ��‘ is unrecognized or represents more than one time zone. ......

Global lock, table lock, row lock
随机推荐
This shift, I still have to go
js求斐波那契数列
Overall flow chart of kernel interrupt
Lambda - 1
小程序和App同时拥有?两者兼得的一种技术方案
es7不使用父子和嵌套关系来实现一对多功能
Summary of static memory allocation and dynamic memory allocation
Gd32f4xx controls dgus variable display
Title 54: take 4 ~ 7 bits of an integer a from the right end.
Changes in the third generation dri
有源差分晶振原理图以及LV-PECL、LVDS、HCSL区别
JS dichotomy
Make good use of IDE, speed up R & D efficiency by 100%
USB to serial port - maximum peak serial port baud rate vs maximum continuous communication baud rate
Random talk about redis source code 91
网盘和对象云存储管理之磁盘映射工具比较
Schematic diagram of active differential crystal oscillator and differences among lv-pecl, LVDS and HCSL
VirtualLab basic experiment tutorial -6 Blazed grating
General differences between SQL server versions released by Microsoft in different periods so far, for reference
Esp32-c3 esp-idf configuring smartconfig and SNTP to obtain network time