当前位置:网站首页>GDB locates the main address of the program after strip
GDB locates the main address of the program after strip
2022-07-25 21:08:00 【xiaozhiwise】
The program after removing the symbol , How to find it in reverse main, as follows :
/*
* intel(64) main address
*/
1.readelf -h find Entry point address Address
(gdb) x/20i 0x555555555080
0x555555555080: endbr64
0x555555555084: xor %ebp,%ebp
0x555555555086: mov %rdx,%r9
0x555555555089: pop %rsi
0x55555555508a: mov %rsp,%rdx
0x55555555508d: and $0xfffffffffffffff0,%rsp
0x555555555091: push %rax
0x555555555092: push %rsp
0x555555555093: lea 0x9e6(%rip),%r8 # 0x555555555a80
0x55555555509a: lea 0x96f(%rip),%rcx # 0x555555555a10
=> 0x5555555550a1: lea 0x910(%rip),%rdi # 0x5555555559b8
0x5555555550a8: callq *0x2f32(%rip) # 0x555555557fe0
0x5555555550ae: hlt
0x5555555550af: nop
0x5555555550b0: lea 0x2f59(%rip),%rdi # 0x555555558010
0x5555555550b7: lea 0x2f52(%rip),%rax # 0x555555558010
0x5555555550be: cmp %rdi,%rax
0x5555555550c1: je 0x5555555550d8
0x5555555550c3: mov 0x2f0e(%rip),%rax # 0x555555557fd8
0x5555555550ca: test %rax,%rax
2.rip Take down the address of an instruction , Add the constant of the breakpoint instruction
0x5555555550a8 + 0x910 = 0x5555555559b8 // main address
/*
* intel(32) main address
*/
1.readelf -h find Entry point address Address
(gdb) x/20i 0x80483c0
80483c0: 31 ed xor %ebp,%ebp
80483c2: 5e pop %esi
80483c3: 89 e1 mov %esp,%ecx
80483c5: 83 e4 f0 and $0xfffffff0,%esp
80483c8: 50 push %eax
80483c9: 54 push %esp
80483ca: 52 push %edx
80483cb: 68 20 8b 04 08 push $0x8048b20
80483d0: 68 b0 8a 04 08 push $0x8048ab0
80483d5: 51 push %ecx
80483d6: 56 push %esi
80483d7: 68 77 8a 04 08 push $0x8048a77
80483dc: e8 cf ff ff ff call 80483b0 <[email protected]>
80483e1: f4 hlt
80483e2: 66 90 xchg %ax,%ax
80483e4: 66 90 xchg %ax,%ax
80483e6: 66 90 xchg %ax,%ax
80483e8: 66 90 xchg %ax,%ax
80483ea: 66 90 xchg %ax,%ax
80483ec: 66 90 xchg %ax,%ax
80483ee: 66 90 xchg %ax,%ax
2. Find the last one push That's ok
80483d7: 68 77 8a 04 08 push $0x8048a77 // main address
/*
* arm(64) main address
*/
1.readelf -h find Entry point address Address
(gdb) x/20i 0x400500
400500: d280001d mov x29, #0x0 // #0
400504: d280001e mov x30, #0x0 // #0
400508: aa0003e5 mov x5, x0
40050c: f94003e1 ldr x1, [sp]
400510: 910023e2 add x2, sp, #0x8
400514: 910003e6 mov x6, sp
400518: 580000c0 ldr x0, 400530 <[email protected]+0x40>
40051c: 580000e3 ldr x3, 400538 <[email protected]+0x48>
400520: 58000104 ldr x4, 400540 <[email protected]+0x50>
400524: 97ffffe7 bl 4004c0 <[email protected]>
400528: 97ffffee bl 4004e0 <[email protected]>
40052c: 00000000 .inst 0x00000000 ; undefined
400530: 00400c48 .inst 0x00400c48 ; undefined
400534: 00000000 .inst 0x00000000 ; undefined
400538: 00400c80 .inst 0x00400c80 ; undefined
40053c: 00000000 .inst 0x00000000 ; undefined
400540: 00400d00 .inst 0x00400d00 ; undefined
400544: 00000000 .inst 0x00000000 ; undefined
2. Find the second variable definition line
400530: 00400c48 .word 0x00400c48 // main address
/*
* arm(32) main address
*/
arm 32bit The program strip Post assembly instructions are completely different , Although the address is not strip It can be matched before , But the instructions have all flown . It seems that when such a program needs to be reversed , Looking for a main It is difficult to .
边栏推荐
- Niuke-top101-bm37
- Compilation and operation of program
- Based on pexels image material API, sort out the material resource library
- ES6---4个强大运算符(??、??=、?.、?:)
- Too many passwords, don't know how to record? Why don't you write a password box applet yourself
- Golang language quickly get started to comprehensive practical notes (go language, beego framework, high concurrency chat room, crawler)
- 一道golang中关于接口和实现的面试题
- 基于腾讯地图实现精准定位,实现微信小程序考勤打卡功能
- An interview question about recover in golang
- Success factors of software R & D effectiveness measurement
猜你喜欢

结构体,枚举类型与联合体
Has baozi ever played in the multi merchant system?

Airtest解决“自动装包”过程中需要输入密码的问题(同适用于随机弹框处理)

Product principles of non-financial decentralized application

Basic knowledge of Marine Geology

Pycharm跑程序时自动进入测试模式

Yolov7 training error indexerror: list index out of range

How to realize reliable transmission with UDP?

Jmeter分布式压测
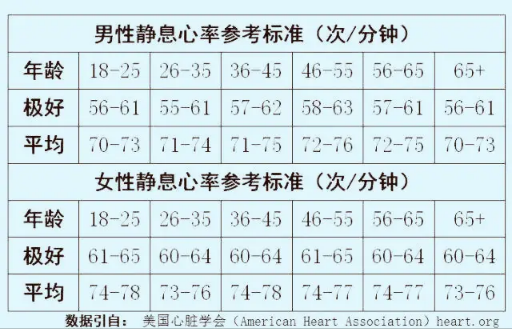
Programmer's Guide to health quenching 5: introduction to sports Basics
随机推荐
PayPal PHP product trial period "recommended collection"
Explain the principle of MySQL master-slave replication in detail
cv图像翻转,EmguCV图像旋转「建议收藏」
CV image flipping, emgucv image rotation "recommended collection"
Huatai Securities account opening process, is it safe to open an account on your mobile phone
Leetcode-155: minimum stack
Leetcode-6125: equal row and column pairs
NPM module removal_ [solved] after NPM uninstalls the module, the module is not removed from package.json [easy to understand]
租房二三事
Matlab---eeglab check EEG signal
leetcode-919:完全二叉树插入器
Leetcode-146: LRU cache
Leetcode-6130: designing digital container systems
What's special about Huawei's innovative solutions to consolidate the foundation of ERP for small and medium-sized enterprises?
Pychart automatically enters the test mode when running the program
A detailed explanation of SCP command
Leetcode skimming -- guess the size of numbers II 375 medium
"Shallow in and shallow out" MySQL and InnoDB [it is recommended to collect and share]
leetcode-146:LRU 缓存
黑盒(功能)测试基本方法